February has been a relatively busy month in the world of Mac malware, and now it has gotten busier with the appearance of the second piece of ransomware ever to affect macOS. Fortunately, this is quite poor ransomware that will only bite those who are doing something wrong in the first place. Nonetheless, it’s good enough to cause your day to go bad in a very big way if you get infected.
This malware, which an update to Apple’s XProtect signatures calls Findzip, was found and described by ESET. According to their report, Findzip has been found on piracy sites masquerading as cracks for Adobe Premier Pro and Microsoft Office, although ESET was careful to point out that there may be other such files out there.
These apps are signed, but with a certificate not issued by Apple, which is unusual. Fortunately, they won’t open by default on a Mac as a result of this.

Unfortunately, this requires that the app be “quarantined.” A properly quarantine-aware app, such as any of the major web browsers, will download files in such a way that the “quarantine” flag is set. Whenever an app or any other kind of executable file is opened, if it has the quarantine flag set, the system will prevent it from opening if it is known malware or isn’t properly signed.
However, torrent clients typically do not do the right thing, in this case, and will often leave the quarantine flag unset on files they download. So the very people who are likely to be downloading this malware are also the people who will be most vulnerable to it. They will not be prevented from opening the malicious app simply because it isn’t properly signed.
When opened, the malware displays a rather goofy-looking mostly-transparent window:
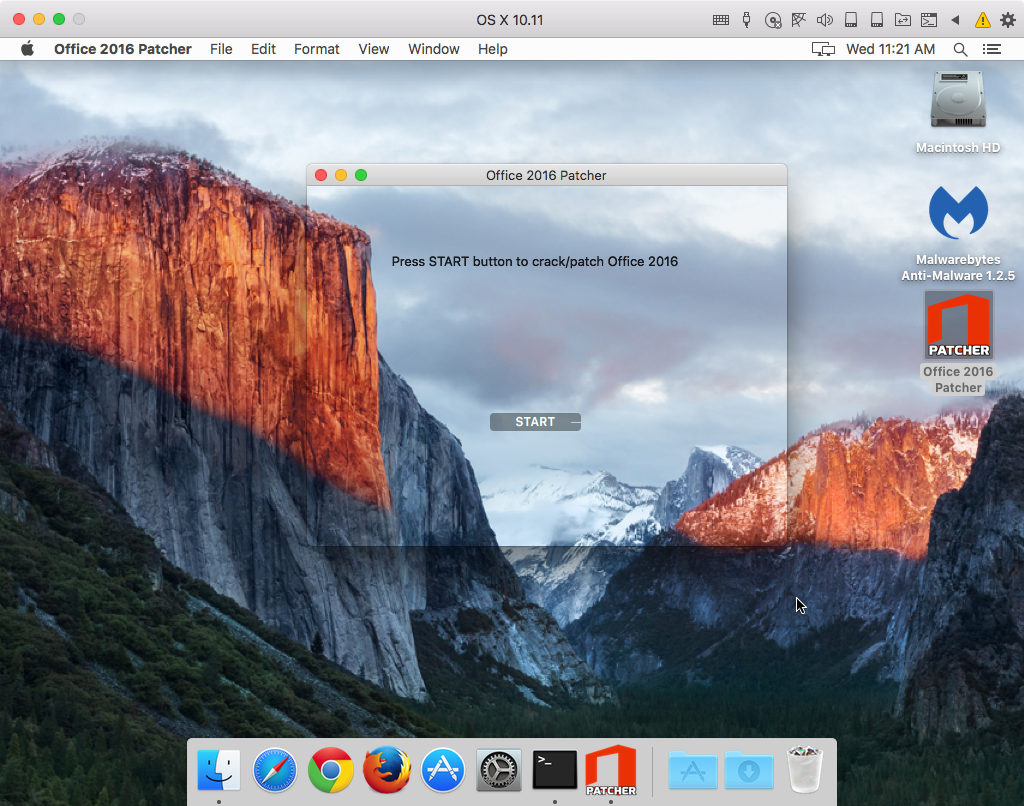
At this point, nothing will happen unless you click the “start” button. You can feel free to quit the app again at this point without suffering any consequences.
If you make the mistake of clicking the “start” button, the malware will begin encrypting the files in your home folder, showing a message indicating that it is patching the app (Adobe Premier Pro or Microsoft Office) and that the process may take up to 10 minutes. Letting the process go quickly made a big mess of my desktop, which should cause even the most clueless pirate some concerns.
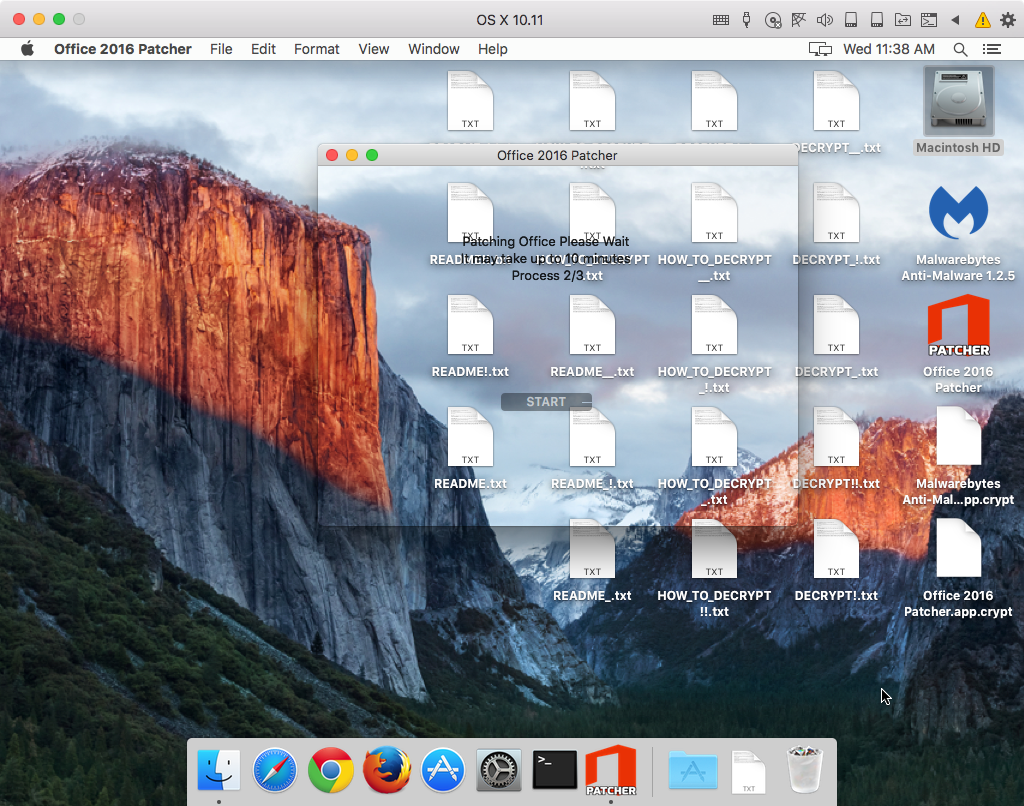
The numerous README, DECRYPT, and HOW_TO_DECRYPT files all contain the same instructions:
NOT YOUR LANGUAGE? USE https://translate.google.comWhat happened to your files ? All of your files were protected by a strong encryption method.
What do I do ?
So , there are two ways you can choose: wait for a miracle or start obtaining BITCOIN NOW! , and restore YOUR DATA the easy way If You have really valuable DATA, you better NOT WASTE YOUR TIME, because there is NO other way to get your files, except make a PAYMENT
FOLLOW THESE STEPS: 1) learn how to buy bitcoin https://en.bitcoin.it/wiki/Buying_Bitcoins_(the_newbie_version) 2)send 0.25 BTC to 1EZrvz1kL7SqfemkH3P1VMtomYZbfhznkb 3)send your btc address and your ip (you can get your ip here https://www.whatismyip.com) via mail to rihofoj@mailinator.com 4)leave your computer on and connected to the internet for the next 24 hours after payment, your files will be unlocked. (If you can not wait 24 hours make a payment of 0.45 BTC your files will be unlocked in max 10 minutes)
KEEP IN MIND THAT YOUR DECRYPTION KEY WILL NOT BE STORED ON MY SERVER FOR MORE THAN 1 WEEK SINCE YOUR FILE GET CRYPTED,THEN THERE WON'T BE ANY METHOD TO RECOVER YOUR FILES, DON'T WASTE YOUR TIME!
The encrypted files, having filenames ending in .crypt, are created using the zip command in the shell to create encrypted .zip files. These files are all given the same passcode, a randomly-generated 25-character string. Interestingly, .crypt files are created for folders, but don’t appear to contain the folders’ contents. Instead, there are more .crypt files inside the original folders. Only files actually get encrypted, and subsequently deleted.
Amusingly, this even applies to the malware itself! After it runs once, if it was run from somewhere in the user folder (like the Downloads folder or the desktop), it’ll never run again.
Unfortunately for affected users, this ransomware is broken as far as “customer service” is concerned. The key used to encrypt the files is never uploaded to a command & control server anywhere, so that hacker would have no way to help you decrypt your files if you paid him. This is a perfect example of the dangers of paying the ransom… there’s never any guarantee that your payment will get you your files back. It certainly won’t in this case. Once encrypted, only a backup can save your data.
There has been some speculation about whether ransomware can or cannot affect a Time Machine backup. ESET reports that it will try to encrypt files found on all connected external or network volumes, so naturally I wondered if Time Machine backups might be included.
I let it loose on a dummy backup, made from my test system, and let it run for 45 minutes. Although it definitely was accessing the external drive, the backups were never damaged in any way. I was still able to restore files from the backup at the end of the test. Of course, a different kind of backup that is connected at the time the malware runs could be affected.
In all, this is not a serious threat to most people. Only those who are engaging in software piracy will encounter it, and even then there are plenty of red flags before they get to the point of actually clicking the “start” button. Unfortunately, if you do run the gauntlet and end up getting your data encrypted, and you don’t have a good backup, this malware will really ruin your day.
Malwarebytes detects this as OSX.Findzip.
Update (Feb. 28, 2017): Malwarebytes has found a method for decrypting the encrypted files created by Findzip. For more information, see Decrypting after a Findzip ransomware infection.










