In our Q1 2017 Tactics and Techniques report, we mentioned that the Locky ransomware had mysteriously vanished. Indeed, for a while, it completely disappeared and allowed for Cerber to take the number one spot as the most distributed piece of ransomware (and malware for that matter).
However, the group controlling the Necurs botnet has just opened the spam floodgates again and is pumping out fake documents that deliver the nasty Locky ransomware right before going into the weekend.
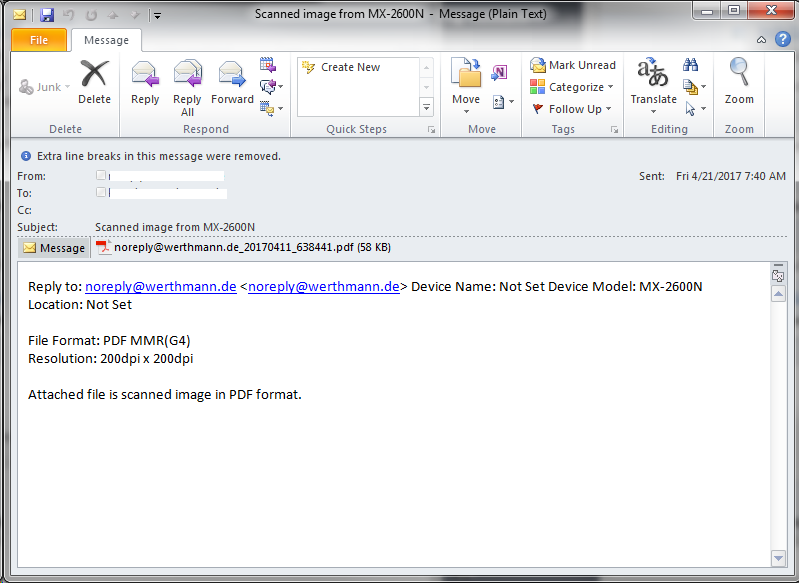
PDF to Word Macro
The ransomware is dropped following a distribution method we have been seeing more of recently with Dridex which involves embedding a Word document within a PDF file.
While this may seem like an unnecessary extra step, it actually allows to bypass sandboxes. Once the user clicks the OK button, the rogue Word document is displayed:
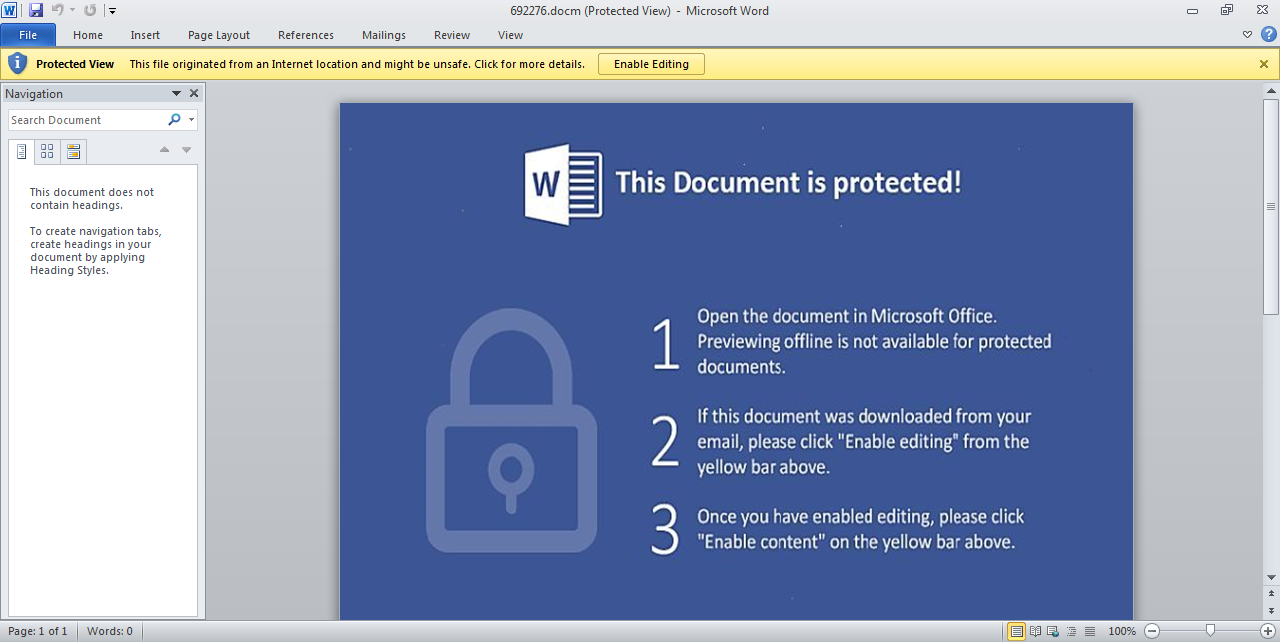
This last step requires a bit of social engineering to execute a malicious macro that will download the actual Locky ransomware.
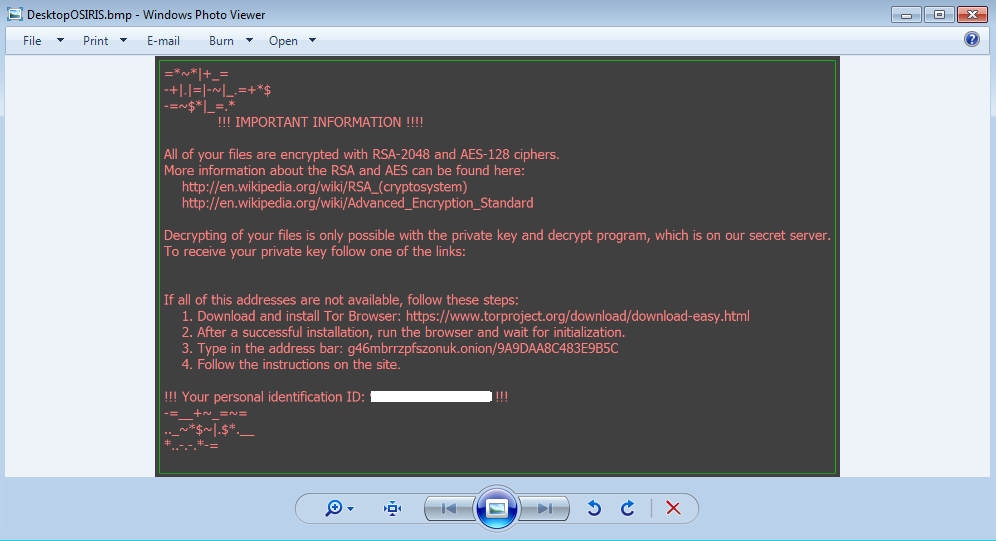
Personal files are encrypted with the .osiris extension and the crooks are asking 0.5 Bitcoin ($623 at the time of writing) to recover them.
Protection
The attack relies on users opening up malicious attachments that will appear legitimate. Many studies have shown that users are often the weakest link in an attack chain and criminals know that too well.
Malwarebytes protects against this attack at various layers including macro and ransomware mitigation, and neither of those required any signature update.