On September 25, 2017, Deloitte announced that they detected a breach of the firm’s global email server via a poorly secured admin email in March of this year. Further, the attackers most likely had control of the server since November of 2016.
Deloitte’s initial statement indicated that only six of their consultancy clients were impacted by the breach, but insider sources later disclosed to the media that the attack most likely compromised every admin account at the firm. The startling severity of the breach has brought attention to Deloitte’s other cybersecurity practices, which, as we can see here with a likely Active Directory server, are not ideal. (There are valid applications for self-signed certificates, but the larger problem here is that the server is exposed to the outside internet at all, running unnecessary services.) 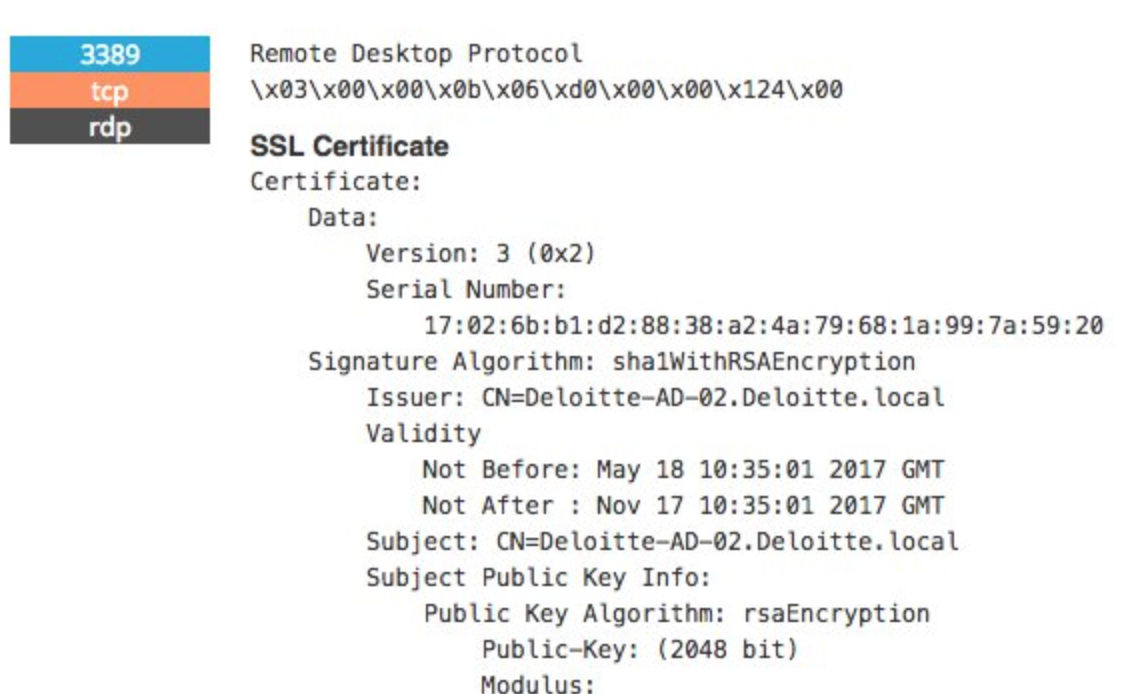
An admin account subversion is not very shocking, given that a significant number of Deloitte email accounts can be found on paste sites, most of a low complexity suggesting the firm has minimal password policies, and lack of a threat intelligence capacity to identify and recover leaked PII. A quick scan of pastebin.com showed a significant amount of Deloitte data from various locations, going back five years. A portion of those pastes were email credentials—the primary breach vector—as shown below.
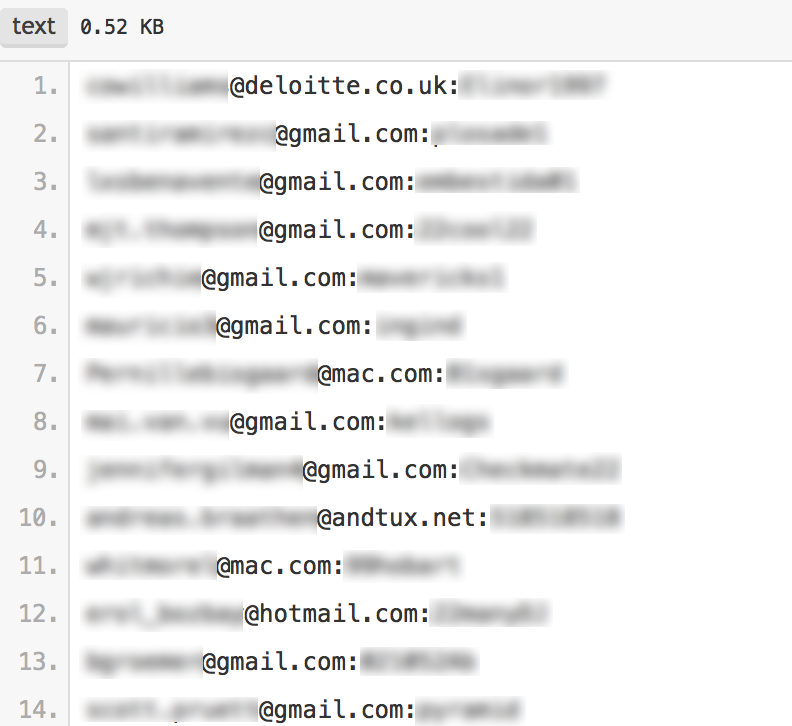
What you should do if you’re a Deloitte cybersecurity client
- First and foremost, take a quick inventory of your own corporate email accounts that have corresponded with the company. Accounts with normal network privileges could benefit from a password reset. Those with elevated privileges should be reviewed for accesses and unusual activity. It’s not unheard of for attackers to breach an ancillary services firm in furtherance of an attack on the main target.
- Do Deloitte consultants have accounts on your network? You can review outbound traffic on these hosts to make sure it matches with their work role.
- Maintain your own threat intelligence capacity to identify work product that might be leaked on paste sites. Enormous breaches like this one are quickly monetized on the dark web, with data eventually filtering out for public use. You can’t prevent third party access to your data, but you can find it in a timely manner, and serve a takedown request accordingly.
- Don’t repeat their mistakes. Best practices for enterprise security are widely written about and publically available. While security is generally seen as a cost center, it would be more accurate to describe it as an investment in public trust. And without trust, how profitable could your enterprise possibly be?










