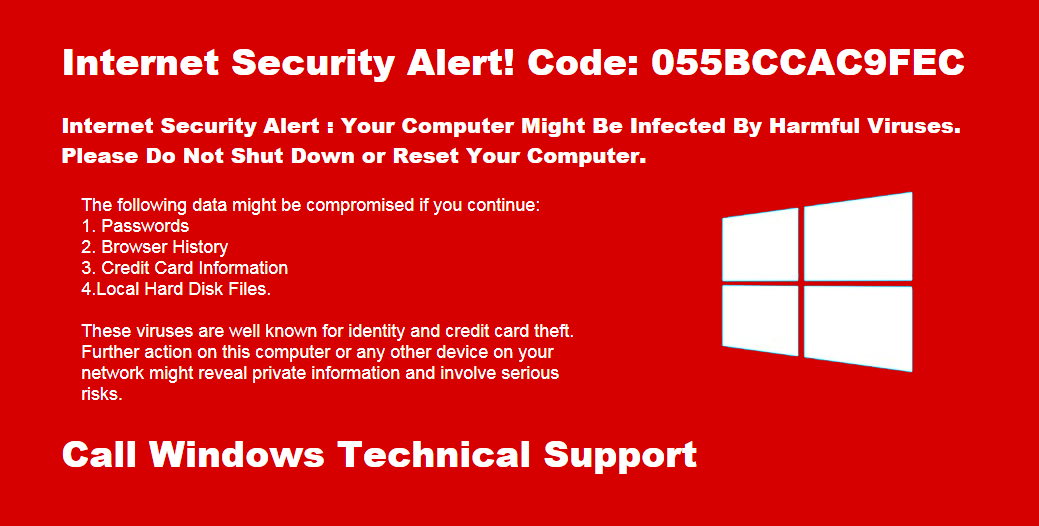
Tech support scammers have been relying on fraudulent pop-ups for many years in order to scare potential victims into calling for remote assistance. These so-called browser lockers (or browlocks) typically originate from malicious ads (malvertising) that can appear on any website, including trusted online portals.
The purpose of browser lockers is not only to scare but also to create the illusion that the computer has been locked, which is not quite true. What’s happened is simply that the browser is stuck in between a flurry of alert dialogs that won’t seem to go away, no matter how many times they are clicked on.
Google Chrome is often the most-targeted browser because of its dominant market share, but pop-ups come in as many different flavors as browser types, with landing pages specific to those browsers. For example, a particularly vicious technique abused the history.pushState HTML5 API to literally freeze machines while displaying the fake pop-up.
Historically, browser makers have let users down by not being to handle those tricks cleanly. However, they appear to have taken note, fixing many of the issues that have to do with poor user experience, while also suggesting other ways for (legitimate) webmasters to send notifications, for example via the proper Notifications API.
Unfortunately, crooks are adapting as well. Despite browser developers’ best intentions, browlocks are still the best bet to scam innocent folks. The following shows a browser locker that went into full screen mode after the user clicked somewhere on the page. Pressing the Escape key to exit full screen (as instructed by the browser) triggered a malicious loop in the code that prevented closing the fraudulent pop-up (without resorting to Task Manager):
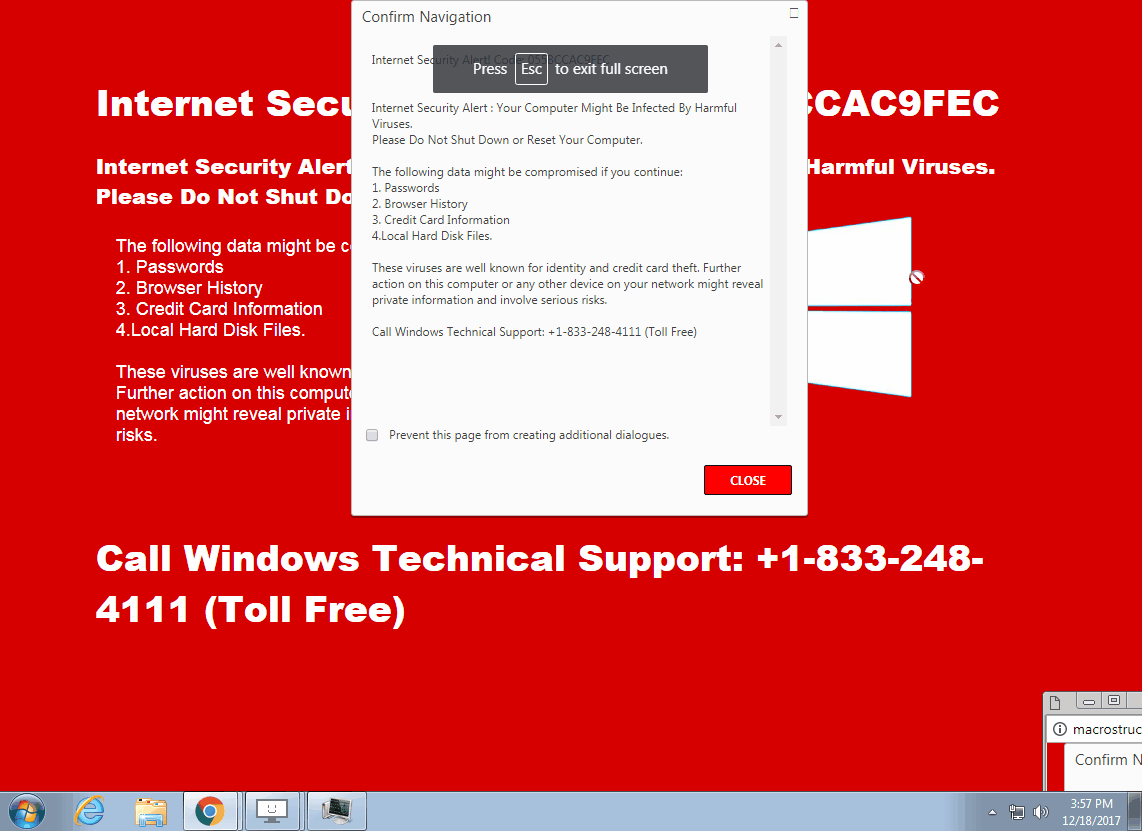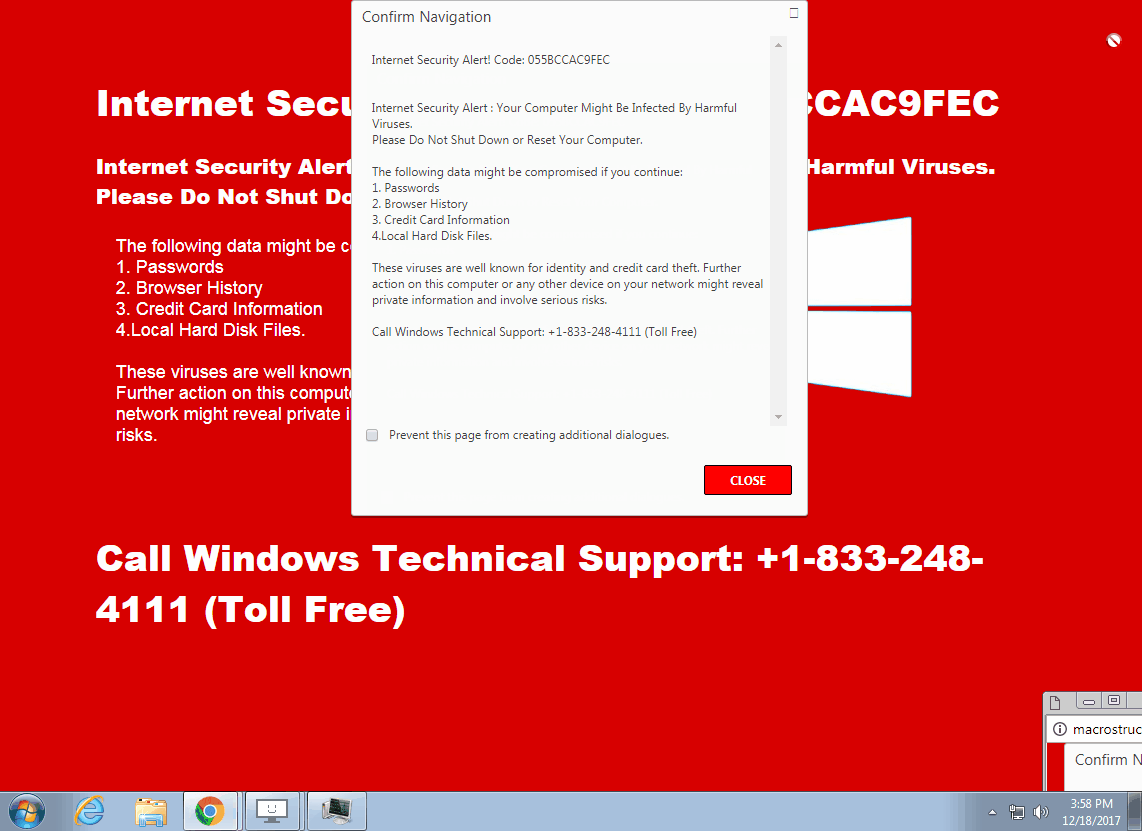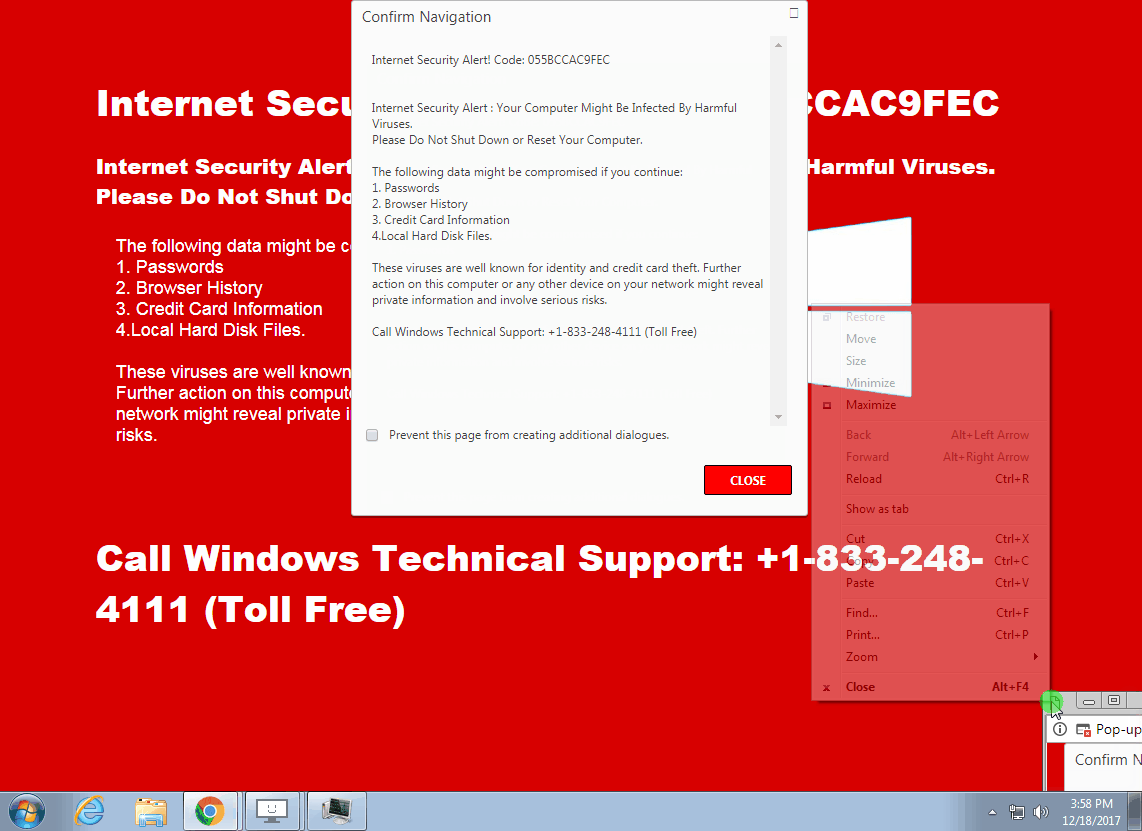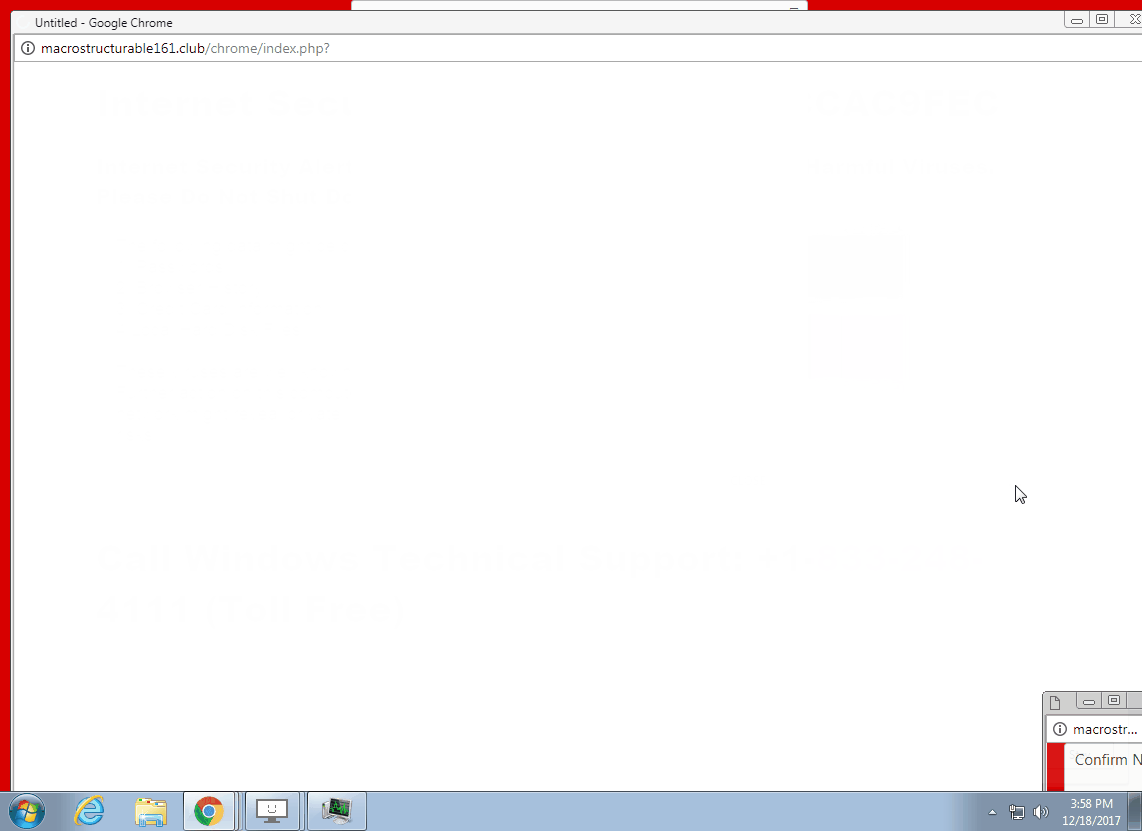
This is a similar technique to what we reported on recently with persistent drive-by mining attacks in that it uses a pop-under as a “helper.” There are actually three different layers in play to make this work:
- a background window in full screen mode
- another window that is superimposed (triggered on click or Escape key)
- the pop-under (triggered on click)
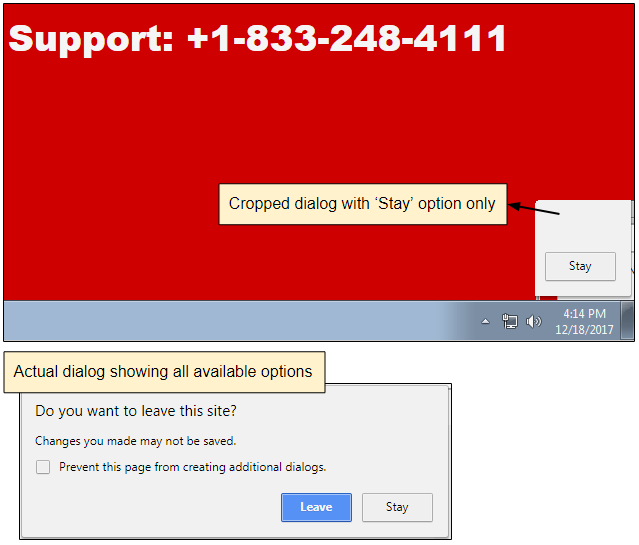
The crooks have positioned and sized the pop-under in such a way that it only displays the “Stay” part of the “Leave” or “Stay” dialog window, leaving users very little choice.
Keep in mind that at the same time the user is trying to close the page, a constant reminder is being played on the computer speakers, to add to the victim’s distress:
From a technical stand point, browser lockers are on the low side of the scale compared to malware such as ransomware. However, they benefit from great distribution channels via malvertising, guaranteeing that millions of people are affected by them. Consider that scammers charge an average of $400 per victim, and you soon realize that this is a highly-profitable business.
On this blog, we have long said that awareness is critical in order to avoid falling for tech support scams, but we also recognize that browsers have a big role to play in how they handle and block such annoying alerts. Unfortunately, scammers try to trick people by abusing regular warnings and creating fake buttons. In the case mentioned above, it would have been possible to close the page from the beginning by clicking on the top window’s X before it went into full screen mode. But if a user can be enticed to perform a certain action, they essentially lock themselves out.
The rule of thumb here is to avoid panicking and simply close the browser via the Task Manager (if all else fails). Remember that the pop-ups themselves are usually harmless. You are safe as long as you haven’t dialed the toll-free number that is being advertised.