Last week, we discussed a particularly serious vulnerability, dubbed “iamroot,” in macOS 10.13 (High Sierra). To sum up, the vulnerability allows an attacker to gain access to the ultra-powerful root user on any Mac running macOS 10.13.0 or 10.13.1. Worse, the vulnerability can be exploited remotely if screen sharing is turned on.
Security Update 2017-001
In response to this, Apple quickly pushed a fix out the door in the form of Security Update 2017-001. Confusingly, Apple has already released a Security Update 2017-001 several times. It released two back in March, for macOS 10.9 and 10.10 (Yosemite and El Capitan). It released another in October for macOS 10.11 (Sierra). Yes, you read that right…Apple’s using the same name for unrelated security fixes for different versions of the system.
Okay, back to the fix. Security Update 2017-001—the one for High Sierra—was released to fix the “iamroot” bug, and it was released for both macOS 10.13.0 and 10.13.1. Because of the severity of the problem, this update was pushed out automatically. In other words, if you don’t install it right away, it will be installed automatically after a fairly short interval. It’s a quick install and doesn’t require a reboot.
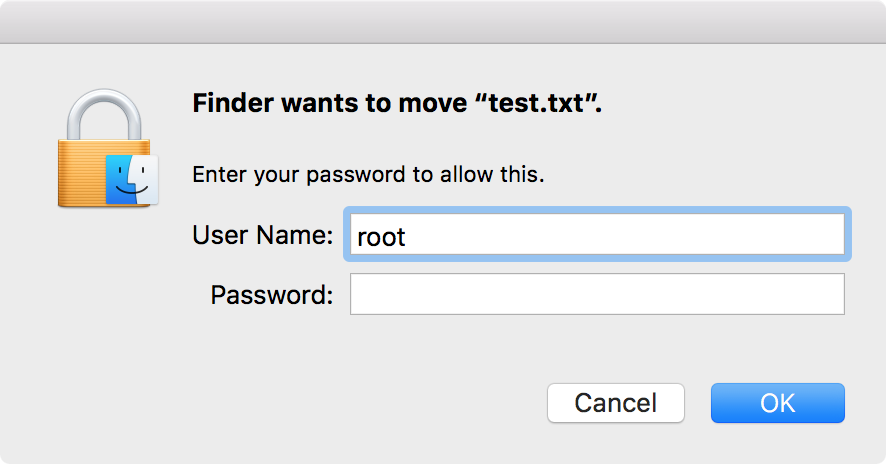
Great, the bug is fixed. We can all go home now! Wait, what’s that you say, Bob? Something’s wrong with file sharing?
Apparently, Apple’s first attempt at fixing the bug had a problem. Specifically, it made file sharing stop working. So if you relied on being able to use file sharing to move files from one Mac to another, this update wreaked havoc with your workflow.
Security Update 2017-001 2.0
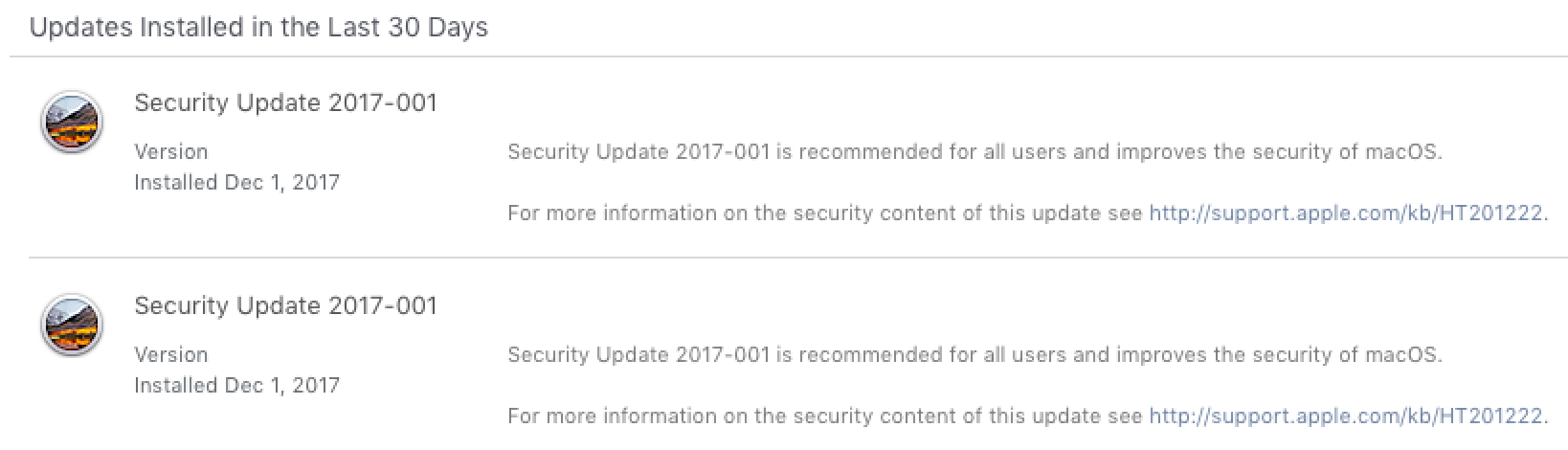
Apple quickly released a technical note about the file sharing problem, and how to fix it, and then re-issued Security Update 2017-001. Yup, that’s a second Security Update 2017-001, not Security Update 2017-002. Thus, people who had already installed Security Update 2017-001 found themselves wondering why they had to install it again. Fortunately, again, the update was automatic. So if you didn’t do it manually, your confusion wasn’t going to keep you from getting the update.
Great, now everything’s fixed. Time to go home for real. Sorry, Bob. You’re going to have to go back to your desk in IT. You’ve got another problem to deal with now. Take note of the fact that this second update increments the build number of macOS to 17B1003. This will be important later.
Remember how we said that Security Update 2017-001 could be applied to both macOS 10.13.0 and 10.13.1? What happens if you install the update on 10.13.0, then update later to 10.13.1? Turns out, it’s bad.
If you install Security Update 2017-001 on 10.13.0, then update to 10.13.1, the bug will re-emerge. The process of installing the 10.13.1 undoes the fix that was applied by Security Update 2017-001, making the machine vulnerable to the “iamroot” bug again.
Of course, Security Update 2017-001 exists for 10.13.1 as well, and will be automatically re-applied sometime after the 10.13.1 update. Crisis averted, right? Bob, you’re really going to have to stop jumping out of your chair every couple paragraphs. I know you want to go home, but unfortunately, there’s still a problem.
You’ve upgraded from 10.13.0 to 10.13.1. You’ve installed Security Update 2017-001. And you’ve verified that you’re running macOS 10.13.1 build 17B1003 (which you can do by choosing About This Mac from the Apple menu and clicking the version number in the window that opens). Unfortunately, you are still vulnerable!
How to fix the problem
So, to sum up, what we’ve described above involves the following steps:
- Install Security Update 2017-001 on macOS 10.13.0
- Update to macOS 10.13.1
- Install Security Update 2017-001 again
- Verify that you’re running macOS 10.13.1 build 17B1003
After doing this, you should be safe from “iamroot.” However, in reality, an attacker would still be able to trigger the original vulnerability and gain root access.
It turns out that restarting the computer will fix the problem, with no further changes needed. This begs the question, though: Why is this necessary? After all, Security Update 2017-001 doesn’t normally require a restart. Why is one required in this specific case?
Since the update doesn’t require a restart, and since many Mac users can be rather averse to restarting, this means that people upgrading from 10.13.0 to 10.13.1 could easily end up being vulnerable to this bug for weeks or months, until they next decide to restart. Keep in mind that nearly all 10.13.0 users have probably already had Security Update 2017-001 installed automatically at this point, putting them into a pipeline heading straight for this issue.
Over the weekend, Apple released a fix and added a mention of the problem to their notes on Security Update 2017-001. Rather than releasing yet another iteration of Security Update 2017-001, Apple added a fix to the MRT application. MRT, which stands for Malware Removal Tool, is not something Apple talks about, and little is known about exactly how it works. It is known, though, that MRT is designed to remove malware that has already infected the system.
If you’re wondering why Apple would release a fix for this bug in MRT, that’s an excellent question. It doesn’t seem to make much sense and feels a bit like a hack to me. My guess is that MRT was something that could be easily and quietly updated, so that’s what they did.
A series of unfortunate events
Now, to be fair, Apple reacted to the original vulnerability quickly, and any rushed fix has a risk of problems. However, this isn’t an isolated incident, and it has Apple fans worried.
In October, there was a problem with certain authentication dialogs revealing the password in the place of the password hint. That has been followed up with the “iamroot” bug and an embarrassing series of buggy responses, which prompted Apple to issue a rare public apology. Now, the latest response to the bugs in the “iamroot” fixes feels more like a hack meant to go unnoticed than anything else.
On top of all that, this weekend, Apple released iOS 11.2 on a Saturday (which is unusual), apparently to address a problem that caused many iOS devices to start crashing on December 2 after 12:15 am. This suggests that the iOS 11.2 release was probably rushed, and time will tell whether there are any issues with the update as a result.
This has many worried about what’s going on at Apple these days. I’ve been using Apple products since 1984, and I’ll be honest: I’m worried about the future of the Mac. Admittedly, I’m not as worried as I was back in the 90s, when Apple was floundering and looked like it could go out of business. However, I do hope that Apple is able to put some of its vast resources to the task of improving the quality assurance process and reverse the worrying trend of increasing bugginess of macOS releases.










