Tech support scams continue to be one of the top consumer threats in 2018, despite actions from security vendors and law enforcement. Scammers are constantly looking for new ways to reel in more victims, going beyond cold calls impersonating Microsoft to rogue tech support ads using the good name of legitimate brands, and of course, malicious pop-ups.
We have been monitoring a particular tech support scam campaign for some time which, like several others, relies on malvertising to redirect users to the well-known browser lockers (browlocks) pages. While it is common for crooks in this industry to reuse design templates, we were still able to isolate incidents pertaining to this group which we have been tracking under the name Partnerstroka.
However we caught up with the same campaign again recently and noticed that the fake alert pages contained what seemed to be a new browlock technique designed specifically for Google Chrome. In this blog post, we share some of our findings on this group and their latest techniques.
Identification
The browser locker is typical of those we normally see, but the crooks have ensured that most browsers and operating systems are covered with their own landing page. This is determined by looking at the user-agent string when the client requests the page to the malicious server. It is further customized via JavaScript functions that perform the “locking” part of the scam.
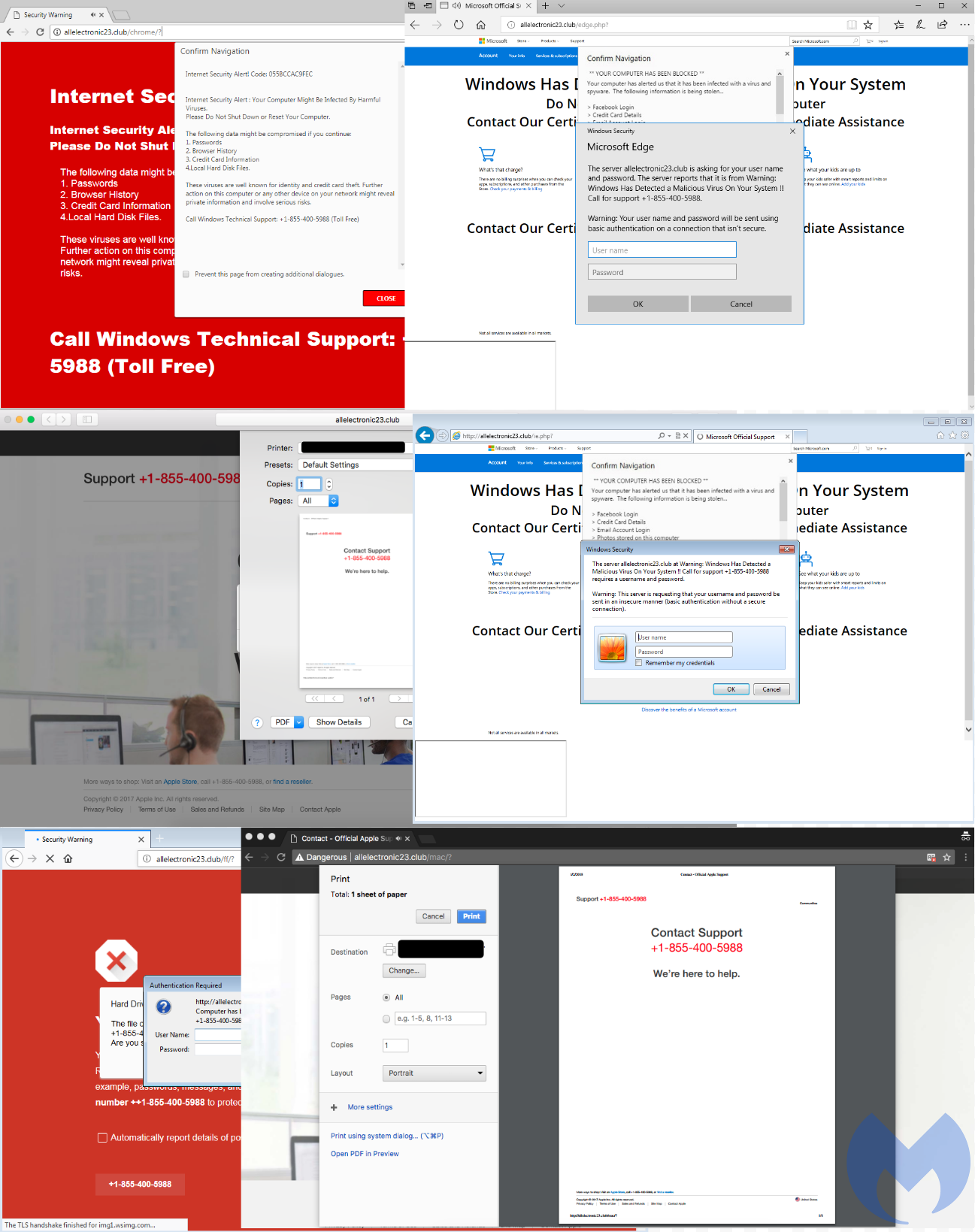
Different templates for the same browlock domain
The name we track this campaign under is inspired by the string “stroka” found within the HTML source code. That same string (and similar code) was also present in previous JavaScript-based “Police Browlocks” that required users to pay a fine with vouchers. However, because code reuse is common among scammers, it is likely to be an entirely different group.
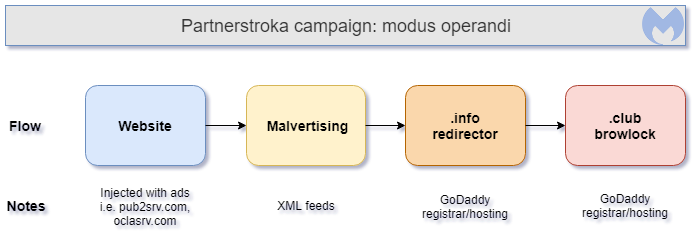
Campaign identification via redirects, TLD and registrar
The threat actors use dozens of Gmail accounts following a somewhat predictable pattern.
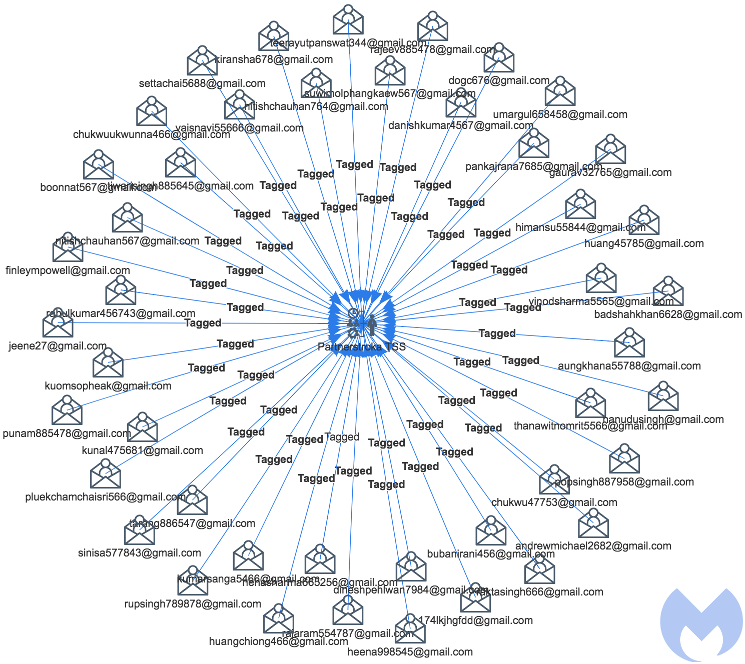
Registrants emails tied to the Partnerstroka campaign
Each email address is tied to anywhere from a few to several hundred .club (gTLD) browlock domains abusing the GoDaddy registrar/hosting platform, with whom we have shared our investigation.
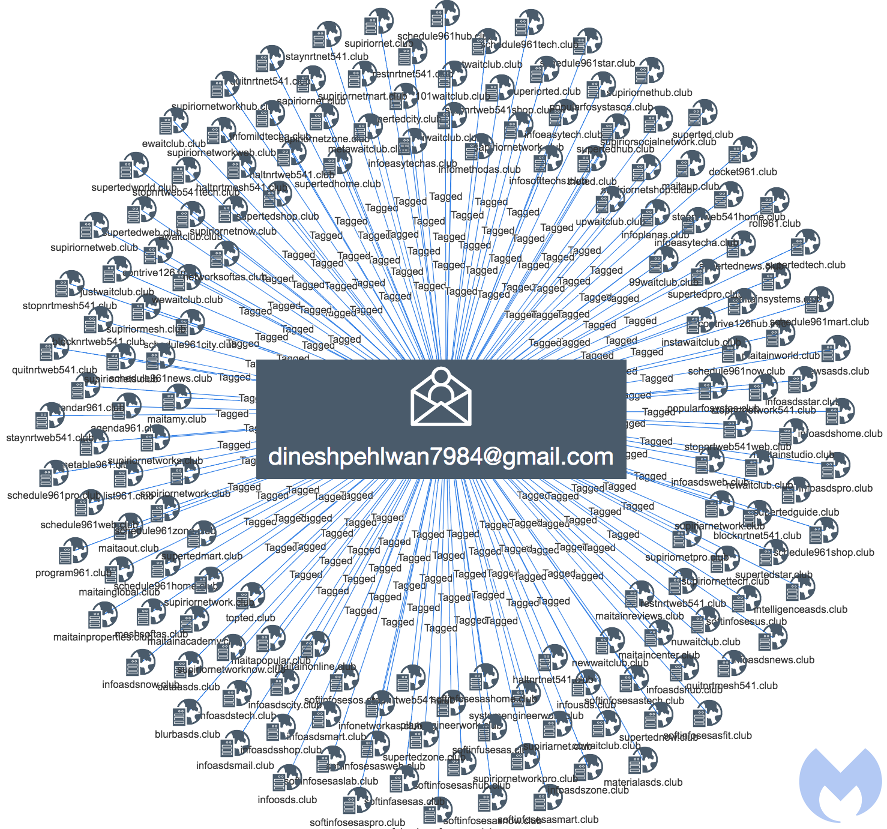
A view of the domains belonging to one email address
We were able to extract over 16,000 malicious domains during a period of several months, but we believe the actual number is much higher. Indeed, our visibility into the depth of this campaign was partly tied to the email addresses we had cataloged and unfortunately, the new privacy laws around whois records hindered our research.
Traffic distribution
We observed different techniques to redirect unsuspecting users to the browlock pages, although malvertising was almost always an element in the chain. The likelihood of getting redirected to one of these browlocks is higher when visiting websites that have less than optimal advertising practices.
BlackTDS
BlackTDS is a Traffic Distribution System (TDS) used by crooks to deliver web threats and avoid unwanted traffic (i.e. not real humans). The kind of traffic that comes out of it ranges from social engineering attacks to infections via exploit kits.
The Partnerstroka group used various ad networks to drive visitors to the browlock page, sometimes directly but often times via the intermediary of an .info gate.
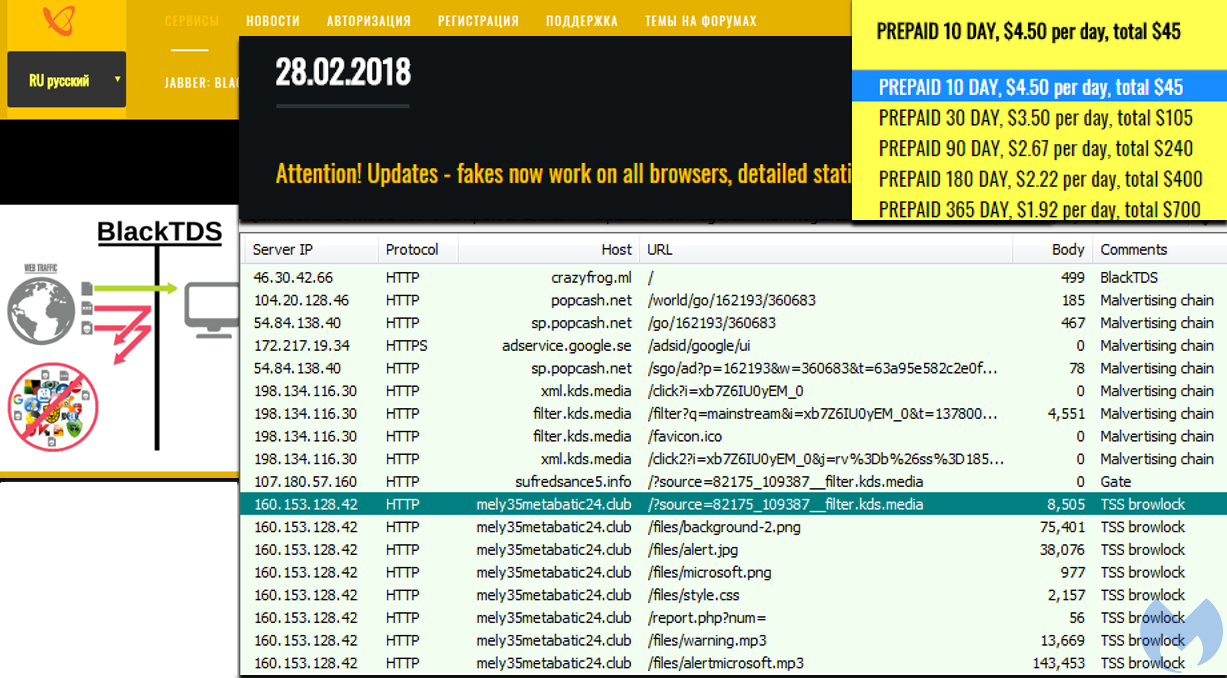
BlackTDS traffic, malvertising, .info gate, and .club browlock
Decoy sites
Another technique the threat actors leveraged was redirects via decoy portals performing what we call “cloaking,” a trick used to only serve malicious content to certain kinds of users and redirect others (non targets) to a benign-looking page instead.
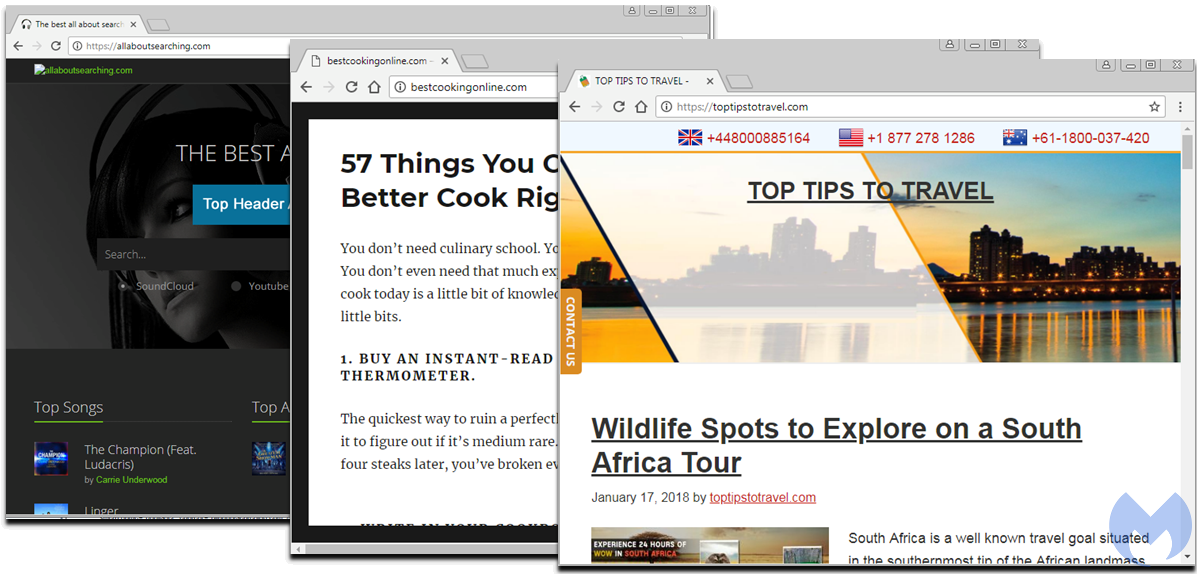
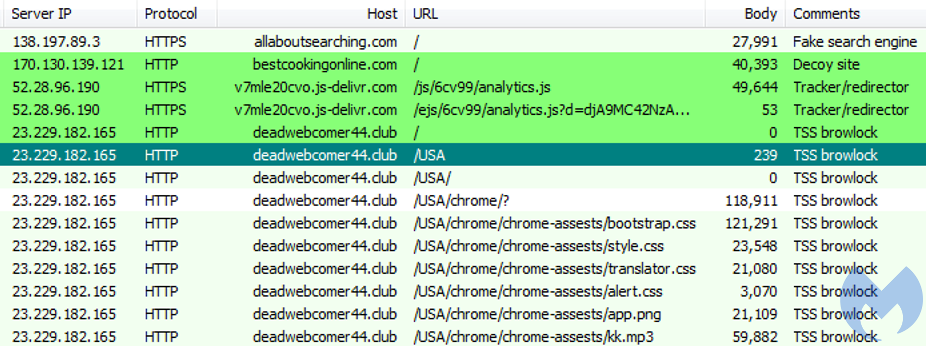
Traffic from decoy sites leading to .club browlock
Blogspot redirects
We also came across a number of blogs hosted on Blogger (now owned by Google). These were either empty or only showed limited content, and again, their purpose was to perform redirects to the browlock pages.
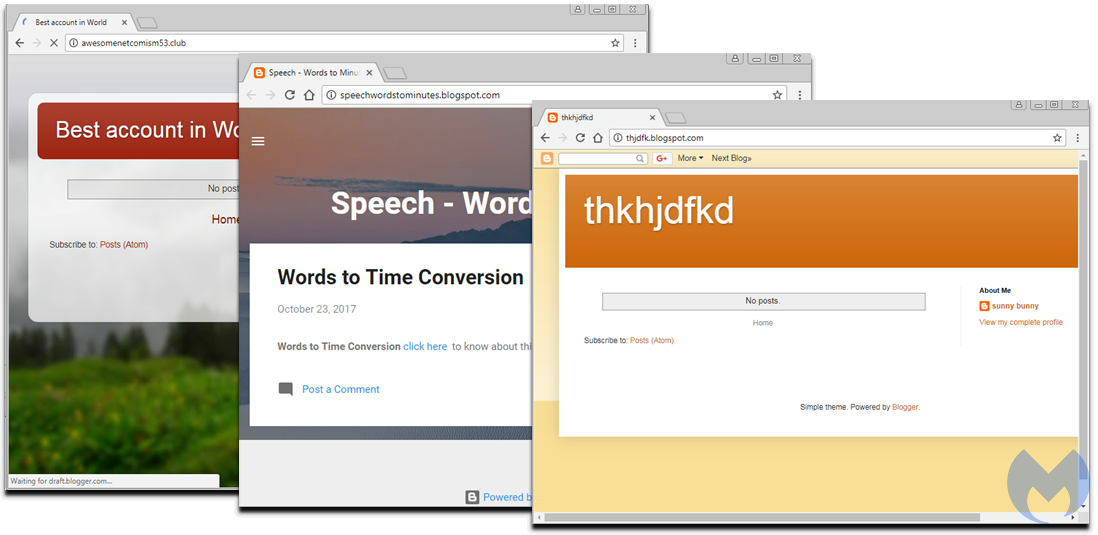
Rogue Blogspot pages used for redirects
Studying their redirection chain more closely, we found something interesting in how the browlock domain was being called. They used a marketing platform in between that would respond with the latest registered browlock domain:
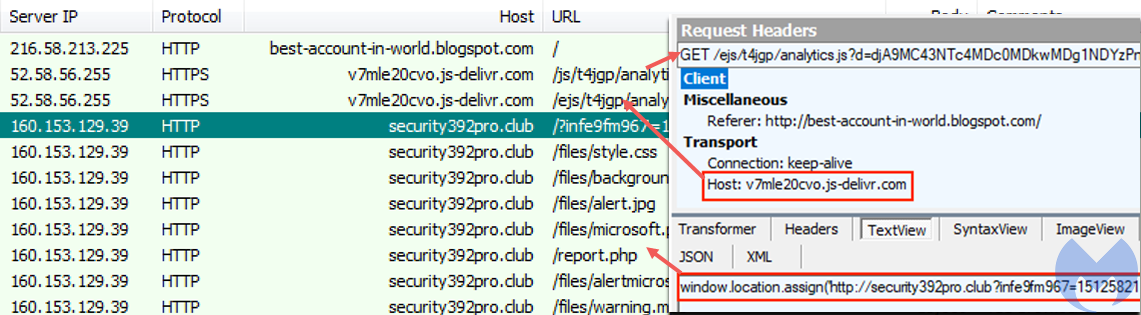
Redirect from Blogspot to the browlock
Malvertising via injected sites
The majority of activity we are observing lately comes from websites that have been injected with ad code. While some website owners do this purposely to monetize their traffic, it becomes a lot more suspicious when we find matching ad campaign identifiers across domains that have seemingly nothing in common. Thanks to @baberpervez2 for providing recent malvertising chains.
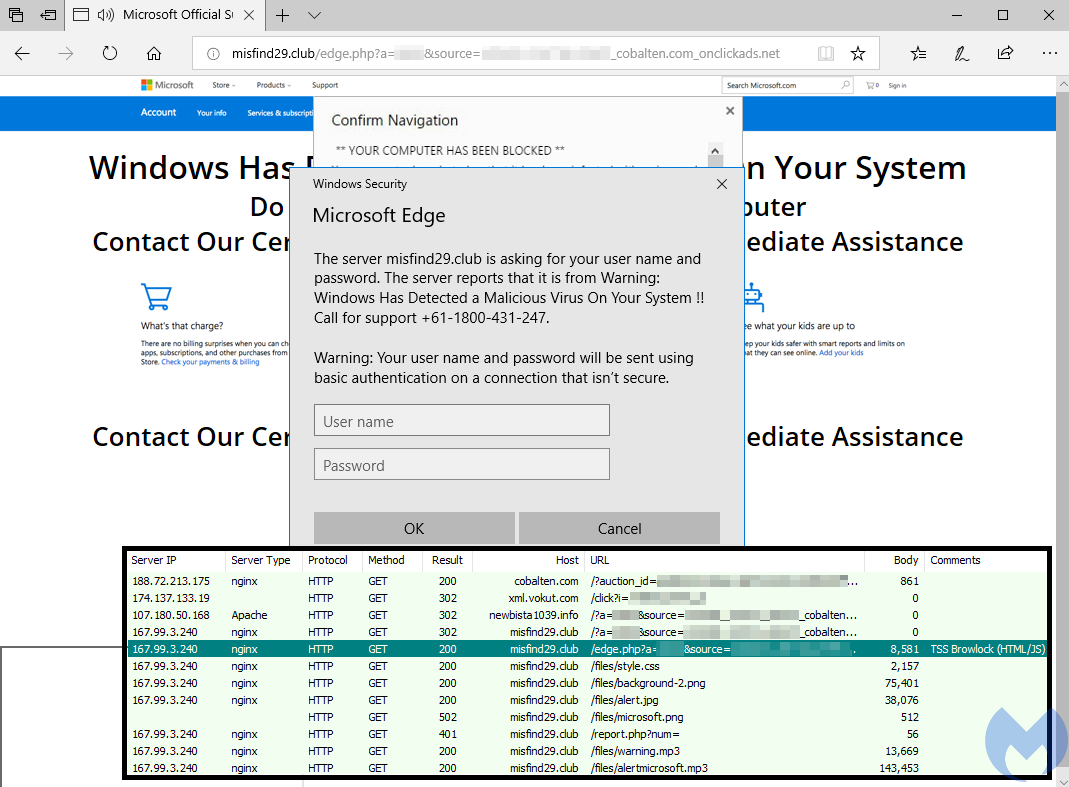
Browser locker for Edge on Windows 10 from a malvertising chain
The evil cursor
There are many different documented techniques that can be used to prevent users from closing a tab or browser window, and often times those are specific to each browser. For instance, Edge and Firefox users will often get the authentication required prompt in a loop, while Chrome users are served with more nasty stuff, such as actual attempts to freeze the browser or trigger thousands of downloads.
In early September, we came across the Partnerstroka group again and noticed that they had incorporated a browser locker technique that was working against the latest version of Google Chrome (69.0.3497.81). Similar to other tricks, it effectively prevented from closing the offending page because the mouse cursor had been hijacked.
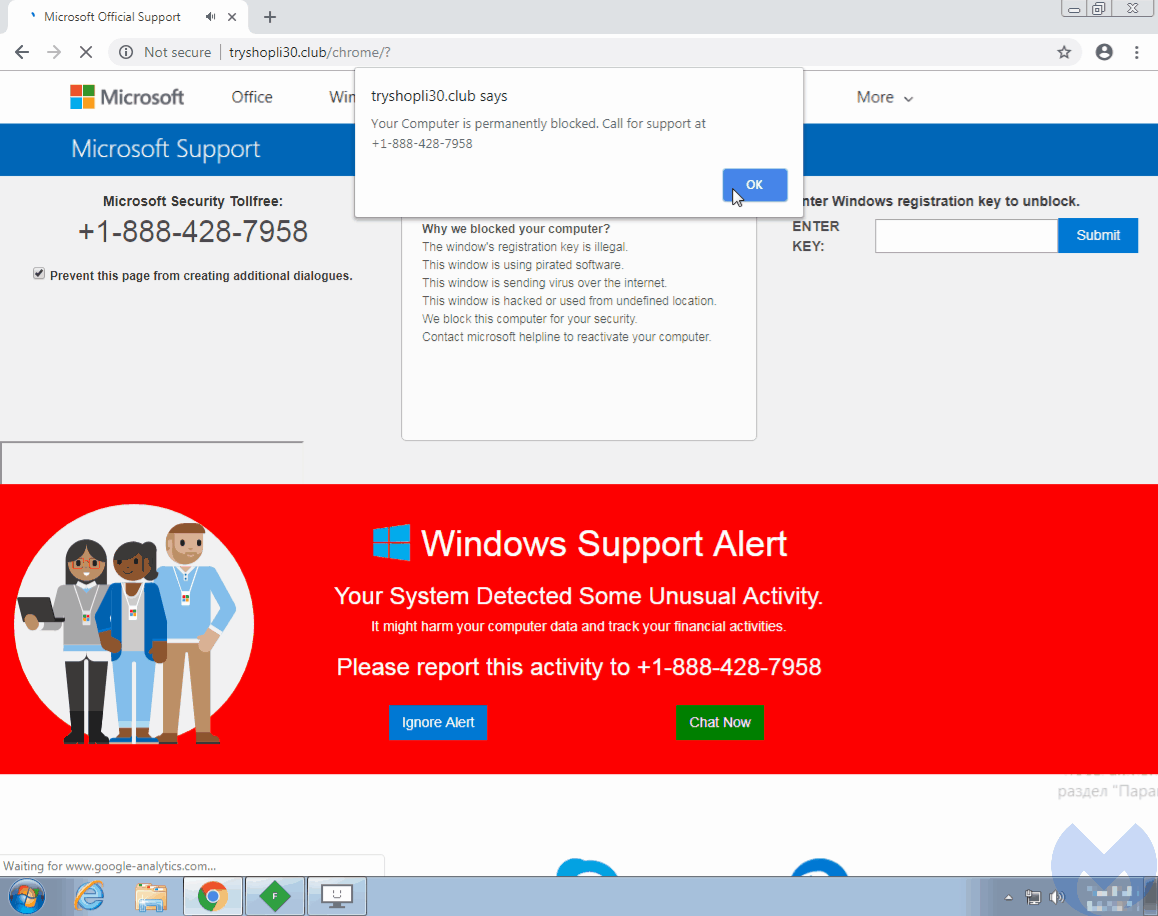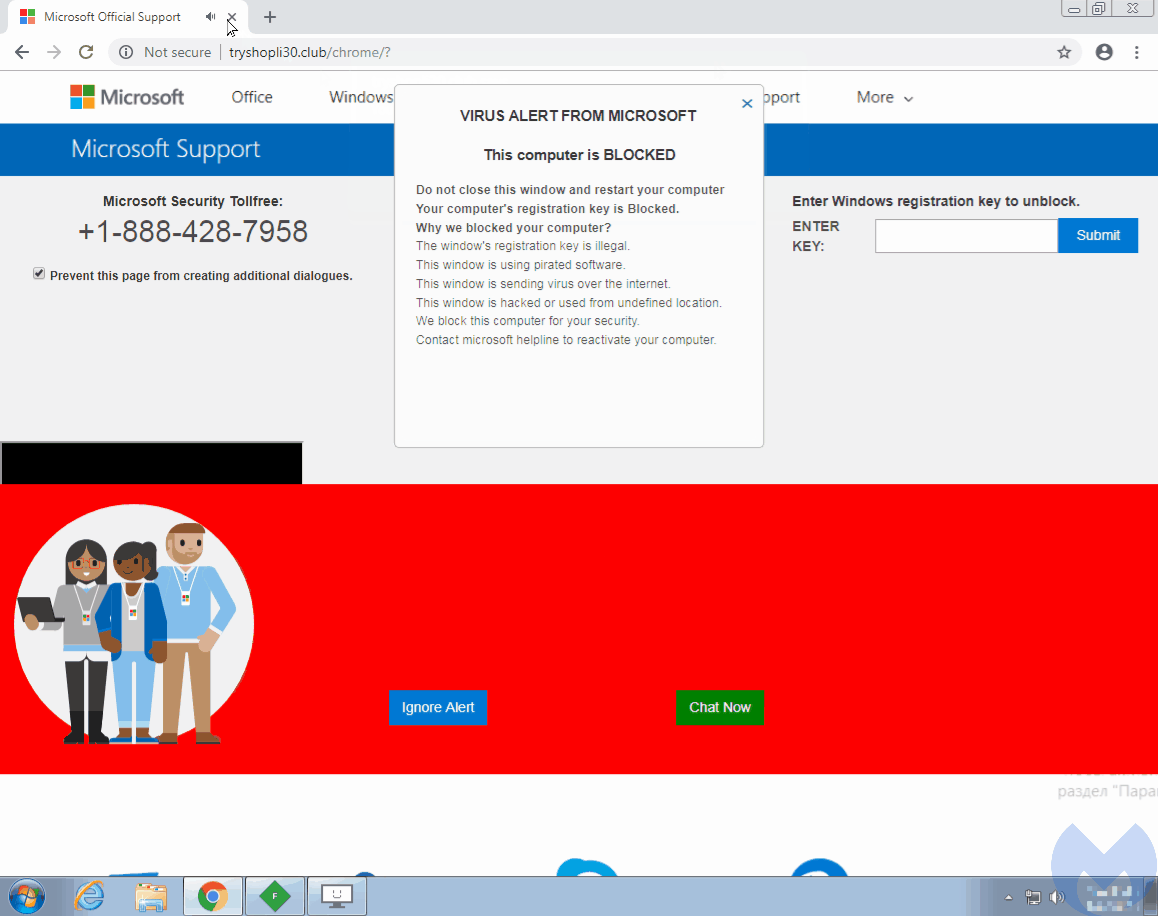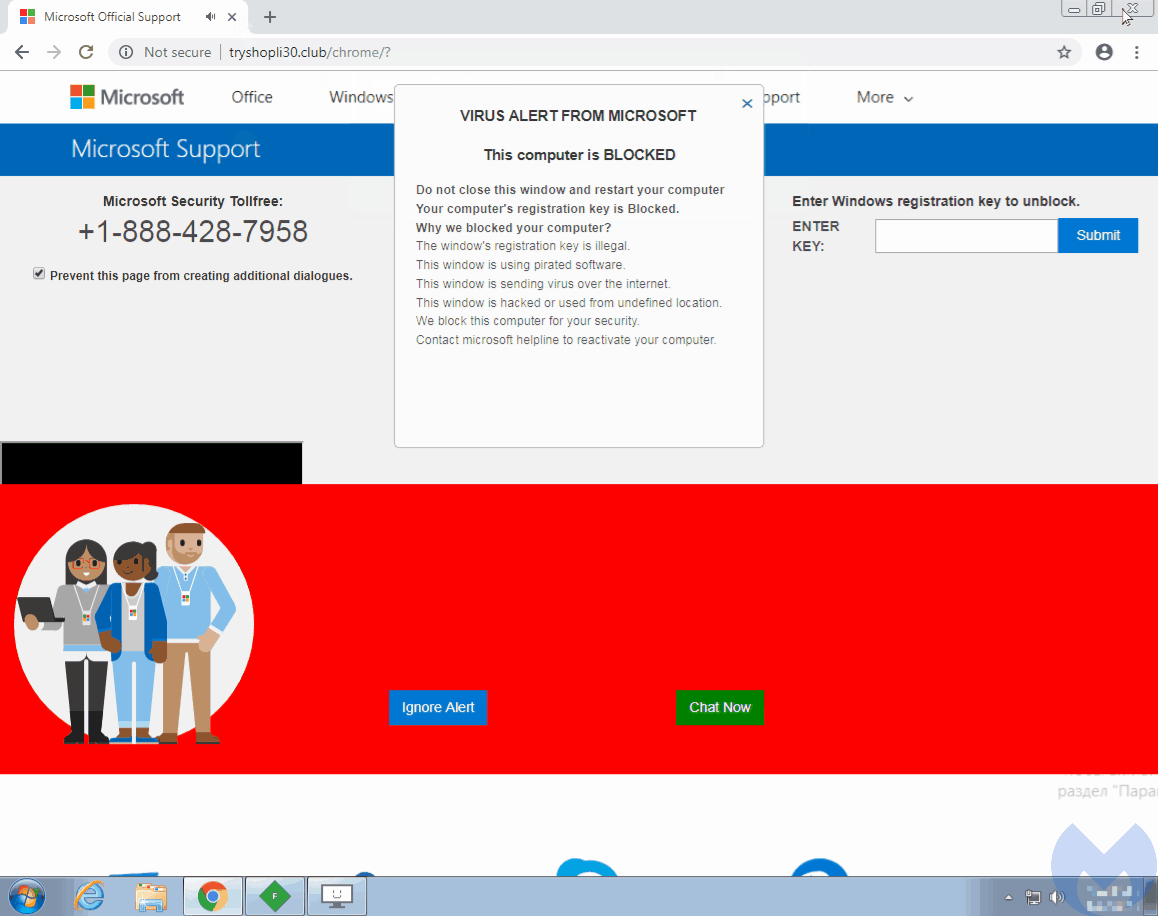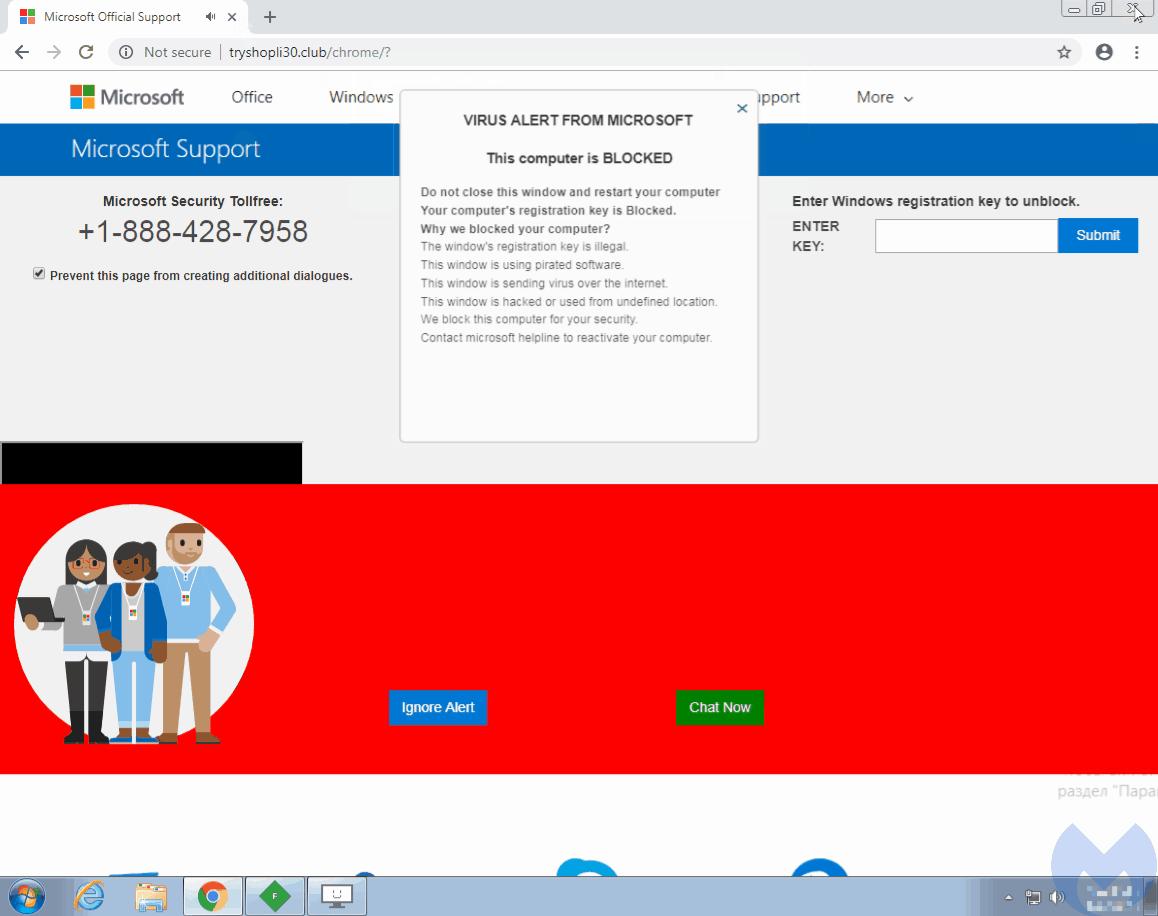
As can be seen in the animation above, the red dot represents what the user actually clicks on, even though the cursor itself seems to be way off. The code responsible for this unwanted behavior can be found within the HTML body tag:
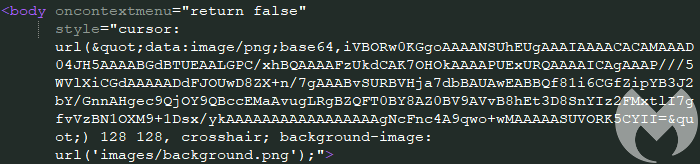
A few lines of code to alter the mouse cursor
The Base64 blurb decodes to a simple image of a low-resolution mouse cursor, but the important bit is the 128×128 transparent pixel, which essentially turns your cursor into a large box. We reported this issue via the Chromium bug tracker portal, and the first person who replied showed what that custom “evil” cursor looks like:
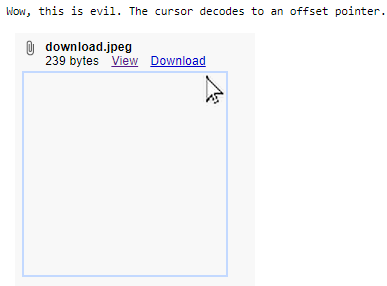
This is one example of many such tricks that can be used against modern browsers. Often times, features that are either well-documented or more obscure turn into attack vectors used to further fool end users, causing them to dial up the scammers for assistance. Indeed, the sound of an alert and a browser that appears to be completely locked up triggers panic for many people. These are essentially the same scare tactics that have been used for ages and still work well.
Similar campaigns
We have noted an increase in tech support scams abusing the NameCheap registrar. While we cannot positively identify that this is also the Partnerstroka group (landing page reuse among scammers is a thing), they definitely share some common traits.
Domain Name: ukxhdp[.]club Registrar URL: http://www.namecheap.com Creation Date: 2018-08-21T15:06:23Z
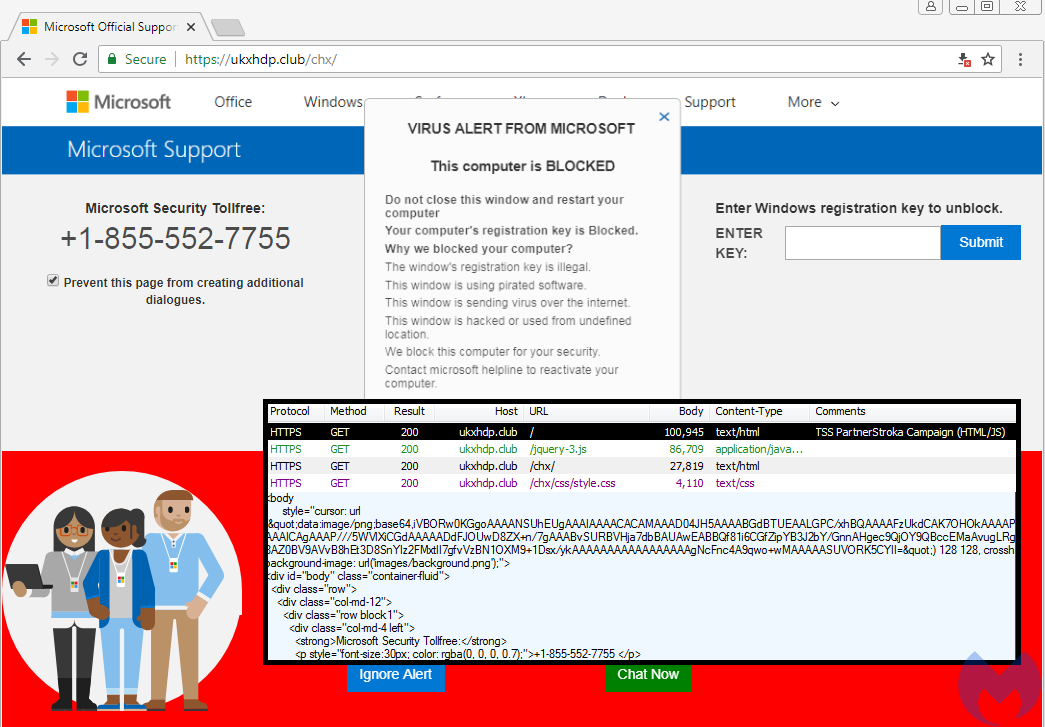
Browlock using the same cursor trick with a domain registered via Namecheap
Domain Name: descorservicesavailoffer[.]club Registrar URL: http://www.namecheap.com Creation Date: 2018-08-22T12:16:07Z
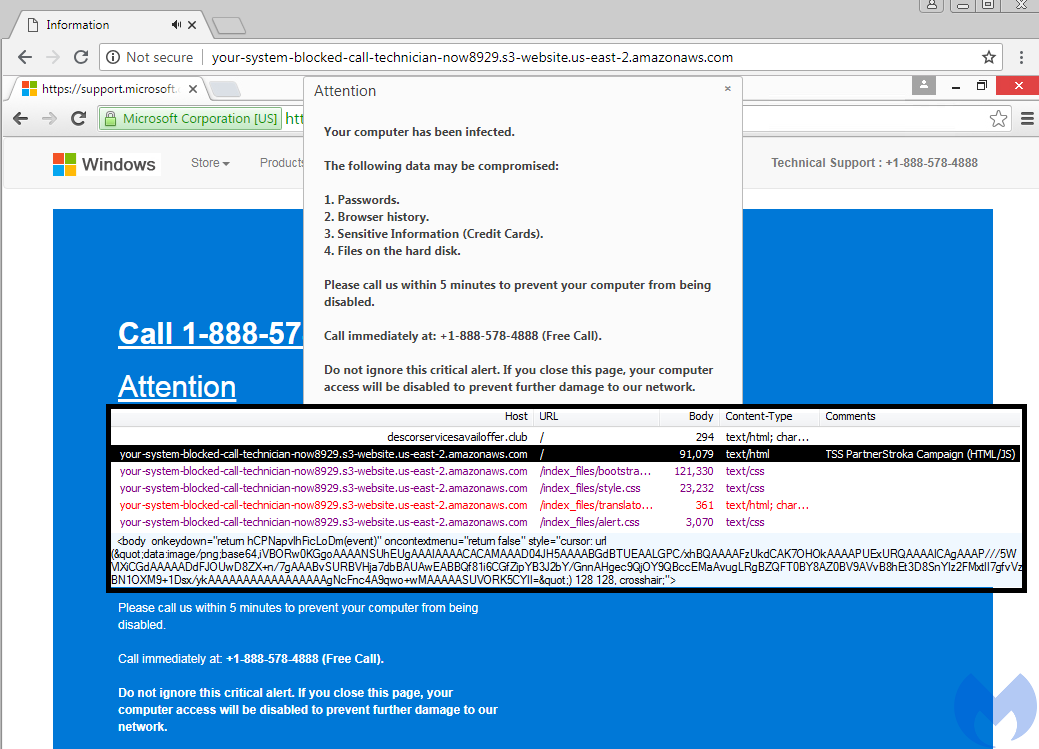
Browlock hosted on AWS S3 bucket
Mitigations
Due to the size and ever-changing nature of the infrastructure between different browser locker campaigns, applying a domain/IP database approach against them is not an effective solution. Although it does offer some coverage, scammers are always a step ahead because of their ability to register new (yet to be detected) domain names.
Here at Malwarebytes, we tackle this issue using both blacklist and, more importantly, heuristics techniques. Our browser extension (Beta) can detect and prevent browlocks:
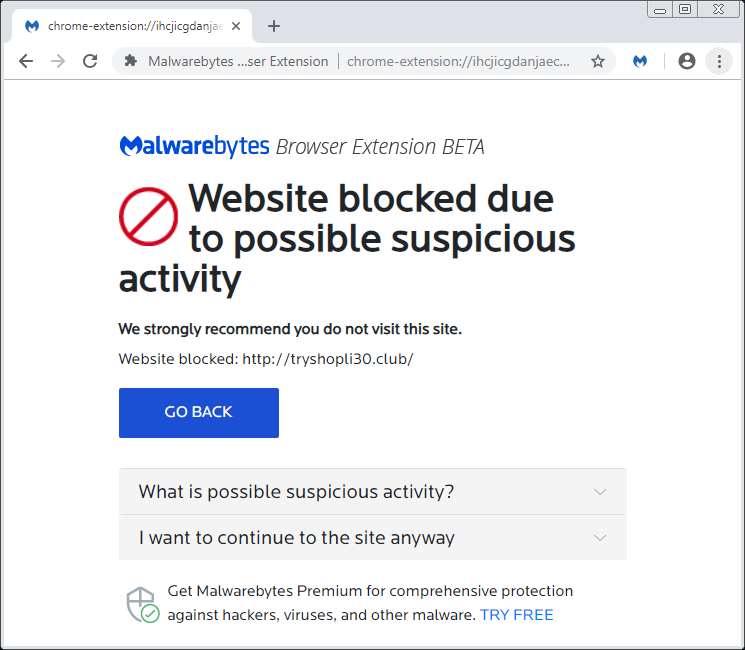
Browlock stopped via the Malwarebytes extension
Tech support scams have been going on for some time and followed various trends over the years. While social engineering is their main leverage, they often incorporate techniques that help with that effort. We can expect crooks to keep coming up with clever ways to disrupt the browsing experience and abuse advertising, registration, and hosting platforms along the way.
As defenders, we must also face new challenges in tracking threat actors that benefit from changes brought up by privacy protection laws. As we adapt to these new realities, sharing threat intelligence with involved parties becomes more important than ever to tackle the problem at a larger scale.
Indicators of Compromise
Recent .info redirectors
getshopea7[.]info meshopea4[.]info bestshopec97[.]info
Recent .club browlocks
ourtabta133[.]club xtabtec134[.]club doebase1089[.]club digivinta137[.]club 99shopez16[.]club
Decoy sites
allaboutsearching[.]com bestcookingonline[.]com best10traveltips[.]com thronetheater[.]com bestporngifs[.]org bestshockers[.]com toptipstotravel[.]com hddfilms[.]com
Blogger redirects
part-added-to-a-book-document[.]blogspot.com best-account-in-world.blogspot[.]com thjdfk.blogspot[.]com webanalysesteam.blogspot[.]com latestdeliverystatusesofallyours[.]blogspot.com speechwordstominutes.blogspot[.]com templateanditwillalwaysservethe.blogspot[.]com themeswritingpadandcustomise.blogspot[.]com










