Organizations know that training employees on cybersecurity and privacy are not only expensive but time-consuming. However, given that current threats are targeting businesses more than consumers, introducing and teaching cybersecurity and privacy best practices in the workplace has undoubtedly become an absolute must.
Creating a successful training program is a massive undertaking. It doesn’t just require one to grab “Cybersecurity 101” material from the Internet, stuff it in a PowerPoint presentation, and expect trainees to understand what’s at stake, let alone change unwanted behaviors. It’s more thoughtful and systematic than this.
Putting together a cybersecurity and privacy training program that is not only effective but sticks requires an incredible amount of time, effort, and thought in finding out employees’ learning needs, planning, creating goals, and identifying where they want to go. Without these, imparting knowledge on cybersecurity and privacy would be ineffective, not to mention costly.
We’re past asking the wrong questions (“Where do I start?”) at this point. But if you’re still weighing your options on whether your organization should do an awareness campaign instead of a full-blown training or education program, we’ll help make it easier for you. Although awareness, training, and education are used interchangeably or compounded together in this field, in reality, these three are entirely different at their core.
Awareness, training, and education
Awareness is in the heart of what we do here at Malwarebytes Labs. We impart learnings by writing about matters related to cybersecurity, which include news, opinion pieces, thought leadership, malware analyses, business and consumer guides, and quarterly threat reports. But for companies aiming to solidify specific security skills that employees need to function, awareness might not be enough.
A security awareness campaign aims to make employees realize that particular actions or responses toward, say, an email of questionable origin could actually be dangerous. The National Institute of Standards and Technology (NIST) defines awareness, training, and education as follows:
- Awareness is not training. The purpose of awareness is simply to focus attention on security. Awareness presentations are intended to allow individuals to recognize IT security concerns and respond accordingly.
- Training strives to produce relevant and needed security skills and competencies.
- Education integrates all of the security skills and competencies of the various functional specialties into a common body of knowledge . . . and strives to produce IT security specialists and professionals capable of vision and pro-active response.
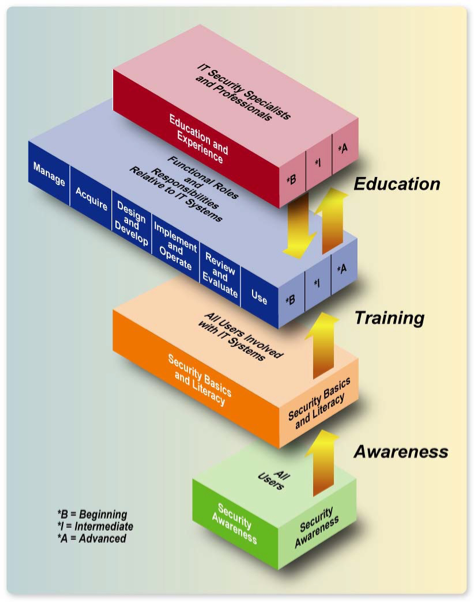
NIST also recognizes that awareness can be the foundation of training. That said, organizations may not have to pick one over the other. They can start with awareness, then training, then education, should they choose to produce specialists. In this blog post, we’ll focus solely on the middle ground: training, from its conception to follow-through.
Why training doesn’t work: Let us count the ways
While training is an excellent approach for building security literacy in an organization, it doesn’t always work out as planned. Reasons why training may be ineffective include (1) trainees didn’t learn much from the program, (2) trainees didn’t change their behavior after the program, and (3) trainee learnings aren’t retained for a long time. Let’s also list down a few additional points to keep in mind before putting together a training program to keep our expectations in check.
Training is done once a year. Traditionally, organizations hold training sessions once per year, but when it comes to cybersecurity, this would have to change dramatically. It’s important to hold regular sessions, especially for new hires, to stay on top of any new tactics cybercriminals are adopting that might affect the business. Also, organizations must keep in mind that cybersecurity best practices shouldn’t be the only discipline they should train employees on. They should also pay particular attention to addressing insider threats and workplace violence.
Training is optional. Organizations who aren’t serious about cybersecurity but want to tick off a box conduct a training session (usually a short one) where employees are merely encouraged to attend but are not required. With breaches happening on a regular basis across industries, an employee base that understands cybersecurity has become a necessity in every organization. Governments recognized this need long before and passed legislation to hold organizations accountable for handling and securing assets. Complying with laws requires training, especially for employees who directly use data assets as part of their work.
Training is only conducted for non-managerial employees. This is another traditional scenario we see in the workplace. Many may not realize this, but a lot of employees in the managerial position are none the wiser when it comes to cybersecurity. Often, they’re unaware of any security measures and policies the organization already has in place. It is then crucial for the organization to include management in the training sessions.
Training is boring/is too long/has too much information to digest. In turn, the supposed learnings that the training is supposed to impart are not adequately delivered and received. Trainees often feel that there is too much for them to digest (especially if this is the first time they hear all this), and the majority of them end up confused or have too many questions. IT directors and educators will recognize that glazed over look.
Keeping training expectations in check
Below is a list of points organizations must always bear in mind to temper their expectations and avoid making decisions that would set themselves up for failure.
- While there is no such thing as perfect security, there is also no such thing as the perfect training program. The closest thing to it would be a program that has been custom-designed to fit the specific organization by individuals with a solid background in cybersecurity.
- Training isn’t the silver bullet that cures all cybersecurity ailments in an organization. Breaches can still happen.
- Training won’t change your workforce overnight. Change is difficult, and often, not welcomed by employees. So, expect a level of resistance, hang in there, and overdose on repetition.
- Training employees doesn’t make them experts. But at the very least, organizations must aim at making every employee competent enough in cybersecurity to do their job well while consistently exercising safe computing habits.
Tips for developing an effective cybersecurity training program
PRE-TRAINING
This is the preparation stage where much of the thinking, brainstorming, and planning takes place. The work here requires a tremendous amount of time, and some organizations may find the wait a hard pill to swallow while breaches are happening left and right. At the end of the day, though, companies will realize that pre-planning is worth the wait.
- Get executive buy-in or sponsorship. In an organization, it’s challenging—if not impossible—for any program to start and achieve momentum if executives don’t support it. So, getting their blessing before doing anything else should be a priority. Furthermore, executives can help direct and shape the future of the company’s overall cybersecurity learning program.
- Create a training task force. Once approved, the organization must then create a task force, ideally comprised of representatives from different departments, including upper management. The task force’s size should be relative to the size of its organization. It’s essential to have an exclusive group responsible for the organization’s cybersecurity learning needs not only to assume accountability but also to adequately address a need and enforce the program. At this stage, the organization can also invite an external third-party as a consultant to be part of the task force.
- Get to know your workforce and the company cultures influencing them. One of the first duties of the task force is to assess their potential trainees—including personnel in the managerial level—and finding out what motivates them, how they learn, and what they need to learn.
- Create a roadmap and include the result they want to aim for. The task force can now use the information they received from their assessment to design the training program and how content can best be presented for maximum learning. It would also be wise to identify bad computing behaviors they have observed from employees and aim to change them. Note: Regardless of how the organization decides to train employees, the training should be based on teaching cybersecurity and privacy best practices and local and international security standards.
- Prioritize. Once the task force has identified bad behaviors that need to change, the team must then determine the top three they want to address. Doing so avoids information overload. For example: Since every employee in an organization handles emails, the team can focus on introducing risks one may find in their inboxes, identifying risk indicators, highlighting the current insecure practices of employees, and then providing changes to these behaviors that, in turn, mitigate the risks.
Read: Insider threats in your work inbox
- Decide on the best training approach or strategies to use for your target trainees. There is no one-size-fits-all approach here. The task force can use the traditional classroom-style method, computer-based training (or e-learning), or a combination of the two—otherwise known as blended learning. As a rule of thumb, e-learning is the ideal method for learnings that may need repetition (especially for new hires). Someone in the task force familiar with adult learning methodologies could significantly contribute to further optimize the learning method. For example, the group can plan on solidifying learning weeks after the initial training by having learners go through simulations. Any failure in the simulations is a new learning opportunity.
- Communicate. This is the part where the task force should socialize the organization’s plans for training the staff, why this is important, what the organization is trying to achieve, and how the training will be conducted. Get buy-in from stakeholders and official sign-off from executives before the first email goes out alerting employees about the upcoming training and having them block off their calendars. The task force can also help employees by sending out regular notices of upcoming training details (or any changes to them) as the date approaches.
- Prep trainees with an online course before training. Should the task force decide to take the blended learning route, the task force may want to consider preparing employees by having them undergo an online course as a primer to the training proper. The course could be an introduction to terms they may likely encounter during the training but not have heard of, such as business email compromise (BEC). This way, trainees would be able to pick up the jargon used in the training without having to look up acronyms in the dictionary.
PERI-TRAINING
Now that organizations have identified which employee behaviors they want to focus on improving, and they know how to effectively impart the training, it’s time to now deliver the training to employees. The work doesn’t stop here.
- Think of the trainer as a facilitator, and not a lecturer. The person presiding over the program should encourage interaction and openness, as employees will better retain knowledge as active participators.
- Make the training environment open and friendly to allow every trainee to speak up without being forced or put on the spot.
- Make training more interactive. In this age, there are more creative ways to present information than clicking through PowerPoint slides. Videos, voiceovers and/or podcasts, articles, and infographics are at an organization’s disposal. They can also participate in live demos, role-playing, and simulations where possible.
- To help trainees retain learnings, use mid-course quizzes, exercises, and post-completion summaries.
- Consider using an online platform for final exams. In this way, companies can also integrate gamification techniques to make exams more fun and less stressful.
As a side note, the task force may want to consider allowing an informal talk or chat among the facilitator and trainees outside the training room and into, say, the company break room or the coffee shop just across the road. This chat could be a further discussion about the topic or learnings of the day’s training or an opportunity for trainees to ask questions.
Read: How to create an intentional culture of cybersecurity
POST-TRAINING
At this point, the task force’s work is almost done—but not yet.
Activities that happen after the training shouldn’t be optional. In fact, the post-training stage is as indispensable as the pre-training stage. Without this, the effectiveness of the training will not be measured, feedback won’t be acted upon, and eventually, the program will stagnate. Note, however, that post-training doesn’t just involve monitoring effectiveness but looks to produce continuous improvement of the program and company-wide promotion of sound cybersecurity and privacy behaviors.
- Implement awareness acknowledgments to foster accountability for all employees. Awarding trainees a completion certificate seems to be a popular end-result of security training programs. But what if, instead of or in addition to the certificate, organizations had trainees sign acknowledgment documents to promote accountability. After investing in and conducting an effective training program, companies should expect their workforce to comply with the new cybersecurity and privacy policies in place. Nothing can solidify this message more than to have them put their names down on paper acknowledging that they should now know better.
- Set up a portal within the intranet that contains training materials for employees to revisit at their own comfort. If possible, allow employees to access these materials on any device, anytime and anywhere, but only with a VPN. The task force can also add more skill-building resources, such as simulations, for employees to practice what they have learned at any given time.
- Consider creating an FAQ page to anticipate the usual questions from employees. Not all questions are raised and answered during or immediately after training. And often, one employee has the same concern as the another. Having an accessible go-to page to address questions about cybersecurity helps trainees get a leg up before the training, and keeps answers to important questions handy long after the program has ended.
- Create visual cues around the workplace to keep the learnings fresh. Posters, emails, newsletters. Basically, the works.
- Make reporting of cybersecurity and privacy incidents readily available to employees. At some point in the future, that proverbial “potentially malicious” email could drop into your employee’s work inbox. Being trained, they would realize that something is off and likely take caution when dealing with it. If a simple reporting system is in place, such as having a dedicated room for cybersecurity and privacy incident reporting in Slack, it would be easier for anyone to raise questions or concerns about suspicious emails. For emails that may have been sent by imposters, a flagging and verification process should be in place for employees to know and properly handle such an incident.
- Update training materials when necessary. Expect this to happen on a regular basis, especially when new and appropriate case studies come up or more effective teaching methods come to light.
Technology and training do go together
All too often, organizations recognize weaknesses in their systems and network, so they focus on putting money on the best software to beef up. And all too often, organizations also recognize flaws in their employees’ online habits due to lack of training or awareness, yet training on matters relating to cybersecurity and privacy doesn’t happen because of budget and resource constraints.
But while it is crucial to address weaknesses in systems that only technology can solve, organizations must realize that, holistically, its security can only be as good as its firewall or AV. Beyond that, we have people who, while lacking awareness, are a threat to security. For employees to transform from liability to last layer of defense, every person in the organization—from the Chief Executive Officer to the receptionist—must undergo at least one general training on cybersecurity and privacy, which only gets more in-depth and tailored for individual departments. Neglecting this could cost organizations more than just money; their reputation as a service provider, competitive advantage, and overall business success are also at stake.
Theodore Roosevelt once said that knowing what’s right doesn’t mean much unless you do what’s right. He’s right. It’s not enough for employees to know what to do. They need to absorb it and apply what they know, changing any bad behaviors and adopting safer online practices. The lessons need to stick. In order to achieve this, organizations must create a highly effective training program that ensures employees know and understand why that training is essential, and guarantees that employees follow requirements by holding them accountable. These are tried-and-tested ways organizations can hold their own in this era of breaches.










