Houzz is an online platform dedicated to home renovation and design. Today (February 1, 2019), they notified their customers about a data breach that reportedly happened in December 2018.
Data breaches unfortunately have become a common event. In fact, we dubbed 2018 the year of the data breach tsunami. Also Houzz is not a giant corporation with millions of customers. So why are we writing about this, you may ask? Mainly because we feel there are some giant corporations out there who can learn from this event as an example on how to handle a data breach properly.
Turnaround
Discovering and informing your customers about a breach that happened less than two months ago is a lot better than what we have seen recently. They did not wait until the investigation on how the breach happened was finished. As soon as they knew what was stolen, they decided to inform those concerned. Of course it is imperative that you get this information into your customers’ hands as soon as possible. Which is probably why the investigation is being conducted by a leading forensics firm. Law enforcement has been notified as well.
Informing customers
Houzz informed their customers directly by email, as well as on their website, about the breach. They said:
Houzz recently learned that a file containing some of our user data was obtained by an unauthorized third party.
The mail starts with this disclosure, goes on to explain what happened, and which information was stolen. It also contains a link to their website, where you can find more information.
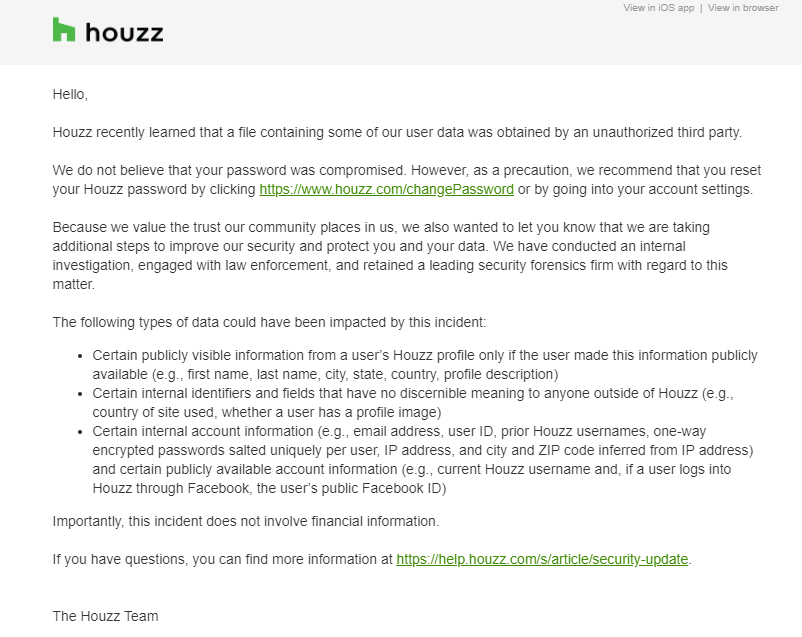
The information given is concise and precise—not just some general remark that no financial information was stolen, which thankfully wasn’t indeed. Houzz included a list of information that was stolen.
The following types of information could have been impacted by this incident:
Importantly, this incident does not involve Social Security numbers or payment card, bank account, or other financial information.
- Certain publicly visible information from a user’s Houzz profile only if the user made this information publicly available (e.g., first name, last name, city, state, country, profile description)
- Certain internal identifiers and fields that have no discernible meaning to anyone outside of Houzz (e.g. country of site used, whether a user has a profile image)
- Certain internal account information (e.g., user ID, prior Houzz usernames, one-way encrypted passwords salted uniquely per user, IP address, and city and ZIP code inferred from IP address) and certain publicly available account information (e.g., current Houzz username and if a user logs into Houzz through Facebook, the user’s public Facebook ID)
On the website, customers can find detailed information on how to change their password. And, like we have done in the past, they advise their customers to use a unique password for each service, which does not need to be as big a hassle as you might expect.
Improvements
Houzz announced security improvements without going into detail. While customers might find this vague, it makes sense to withhold the specifics, as the investigation is ongoing, and they wouldn’t want to make threat actors any wiser. Seeing that they were already using one-way encrypted passwords salted uniquely per user was certainly encouraging.
Dealing with data breaches
Data breaches happen all the time. It happens to the best of companies. It’s the way those organizations deal with them that can save face. What other businesses can take away from this example:
- Inform customers as soon as it makes sense and be precise about the stolen information.
- Approach your customers directly. Don’t let them read about it in the papers or social media.
- Engage law enforcement and a firm specialized in forensic investigations.
- Learn from what went wrong and improve on that.
Stay safe, everyone!











