A great number of attack techniques these days are using Microsoft Office documents to distribute malware. In recent years, there has been serious development on document exploit kit builders, not to mention the myriad of tricks that red-teamers have come up with to bypass security solutions.
In contrast to drive-by downloads that require no user interaction, document-based attacks usually incorporate some kind of social engineering component. From being lured into opening up an attachment to enabling the infamous macros, attackers are using all sorts of themes and spear phishing techniques to infect their victims.
While Microsoft Office gets all of the attention, other productivity software suites have been exploited before. We recall the Hangul Office Suite, which is popular in South Korea and was used by threat groups in targeted attacks.
Today we look at a vulnerability in LibreOffice, the free and open-source office suite, and OpenOffice (now Apache OpenOffice) available for Windows, Mac, and Linux. The bug (CVE-2018-16858) was discovered by Alex Inführ, who responsibly disclosed it and then published the results with an accompanying proof of concept on his blog.
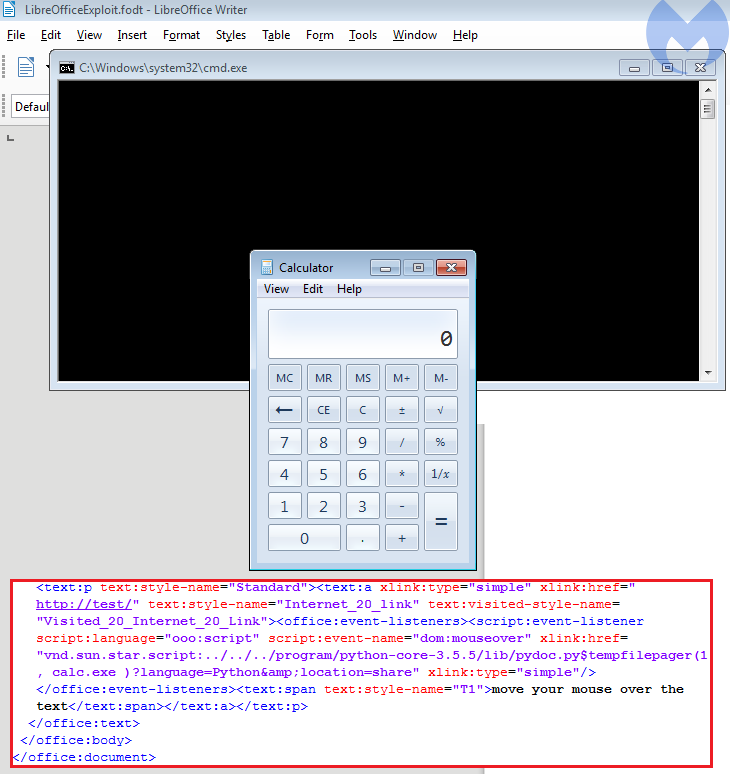
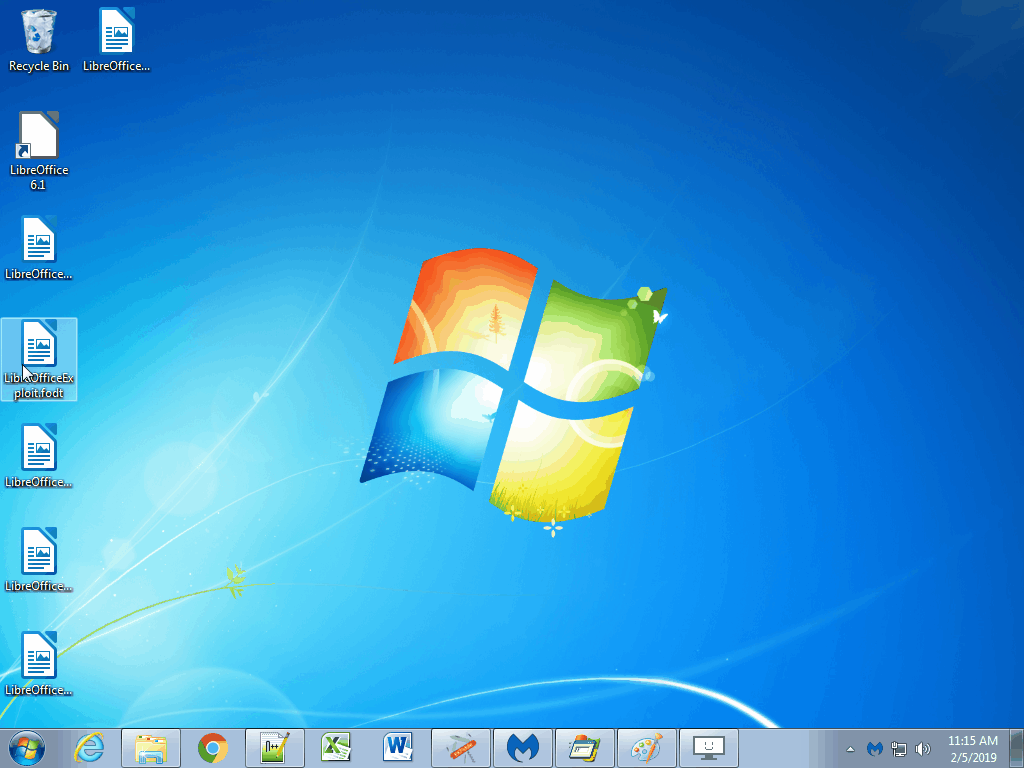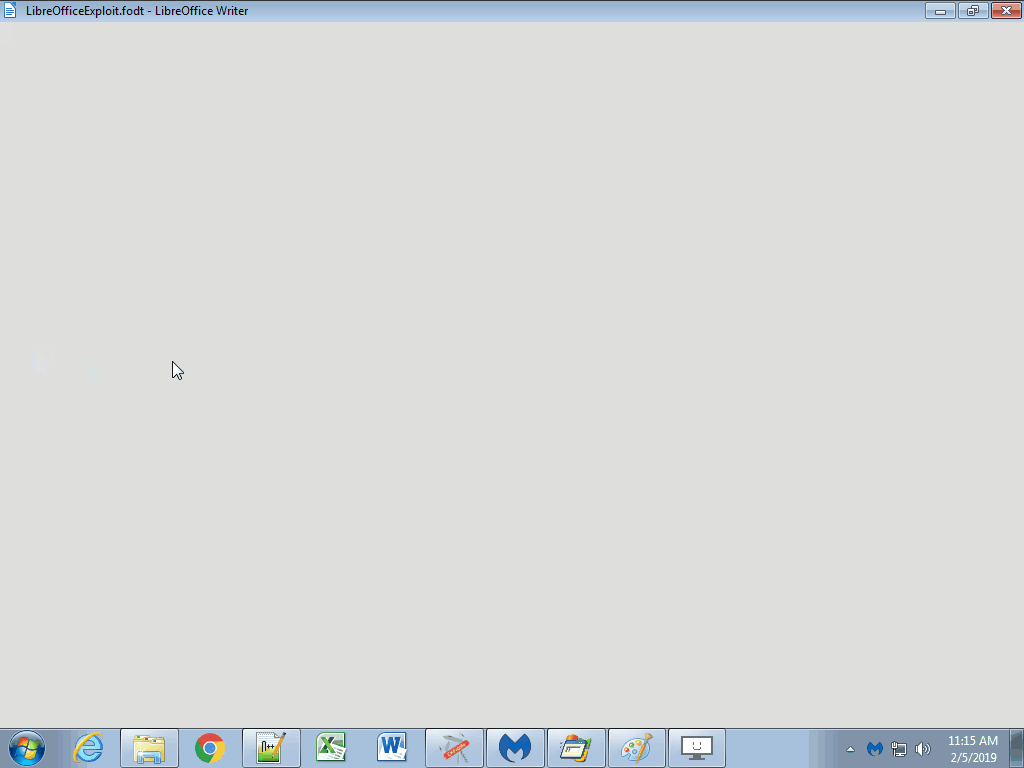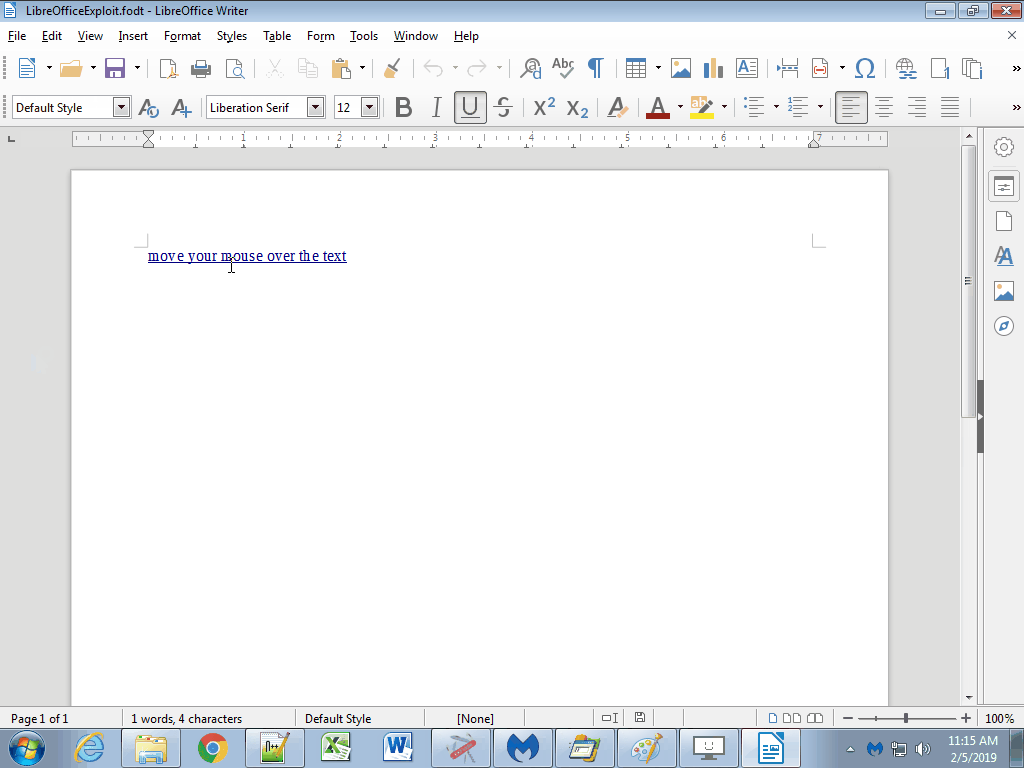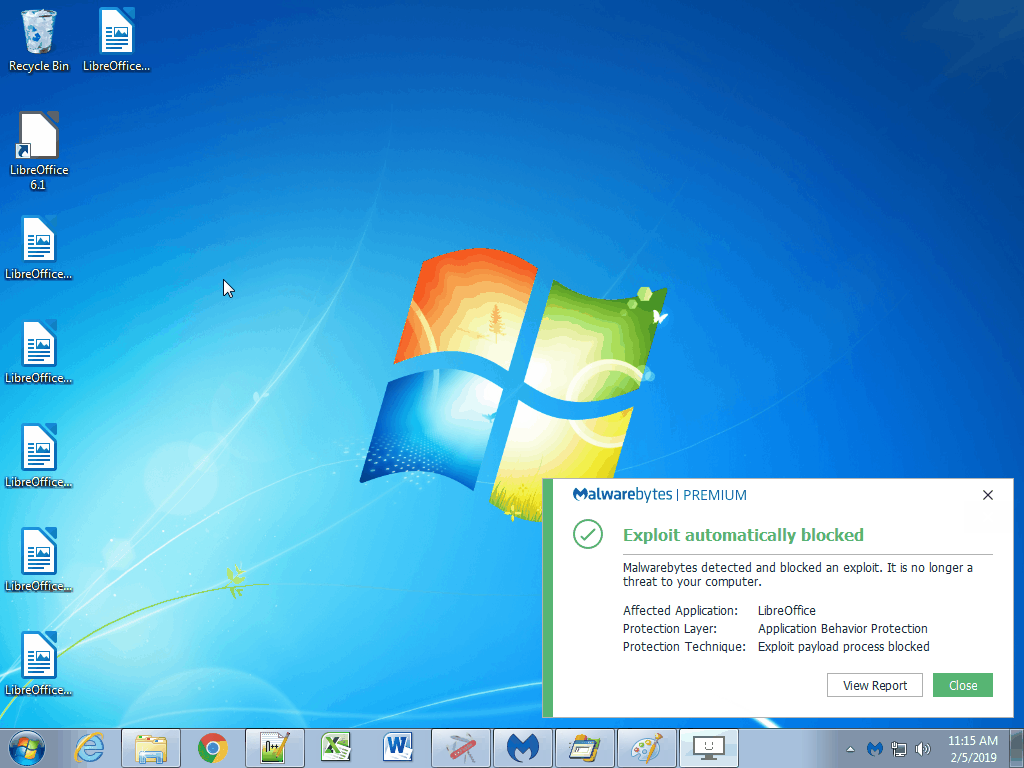
Proof of concept code exploiting the vulnerability and launching the calculator
An attacker could take advantage of this bug to execute remote code, which could lead to compromising the system. The flaw uses a mouseover event, which means the user would have to be tricked into placing their mouse over a link within the document. This triggers execution of a Python file (installed with LibreOffice) and allows parameters to be passed and executed.
We tested several proof of concepts shared by John Lambert. The process flow typically goes like this: soffice.exe -> soffice.bin -> cmd.exe -> calc.exe
The vulnerability has been patched in LibreOffice but not in Apache OpenOffice—yet. Malwarebytes users were already protected against it without the need for a detection update.
Time will tell if this vulnerability ends up being used in the wild. It’s worth noting that not everyone uses Microsoft Office, and threat actors could consider it for targeting specific victims they know may be using open-source productivity software.