On February 12, a patron of the Malwarebytes Forum alerted us of an issue with ad redirects that seemed to come out of nowhere. An outcry from other commenters filled the forum thread, all experiencing the same redirects to the same exact websites. Our web protection team traced the offending websites back to the culprit—the adware known as BatMobi.
What is BatMobi?
BatMobi is an Advertisement Software Development Kit (Ad SDK), which is essentially a software library that connects applications to ad networks. Developers insert Ad SDKs into their apps’ code to gain revenue through ads. Thus, they can offer their apps for free and still make money. Most variants of BatMobi were clean and safe to use—until recently.
Based on a Reddit post about the sudden web redirects on January 21, it appears these “clean” versions of BatMobi turned into mobile adware around mid January. Adware is a subcategory of Potentially Unwanted Programs (PUPs), which means it hangs around the fringes of bad behavior and often results in poor user experiences. Furthermore, BatMobi has always had a slightly more aggressive version we consider low-level adware. We detect this as Android/Adware.BatMobi.
Triggered by Google Play
An interesting component of this newly seen BatMobi variant is the location in which it was popping up ads—Google Play. Forum patrons verified the ads were popping up whenever an app was updating or installing in Google Play. BatMobi is using Chrome Custom Tabs within its code to open websites in Google Play whenever it was triggered by these events. Although the websites being redirected to are relatively safe sites, they are an unwanted nuisance for the user—exactly what we consider adware.
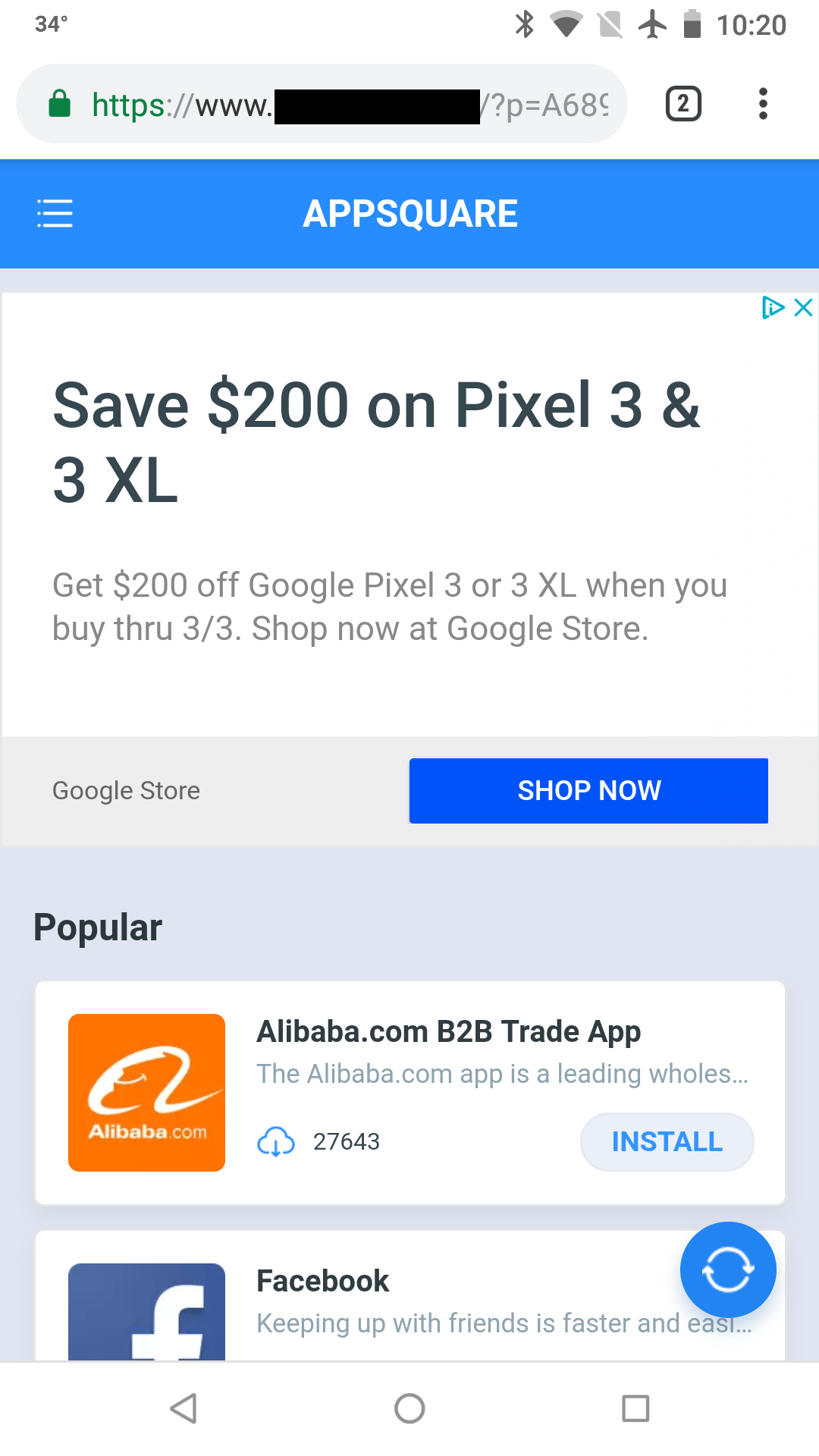
Tracking down the beast
Usually, pinpointing the source of an adware app on a customer’s device is simple, especially when knowing the adware variant, as in this case. Thanks to all the great Malwarebytes forum participants, I had a large set of data to work with in the form of what we call Apps Reports.
This is a list of apps along with data about their MD5, package name, and other components to assist tracking down infections. Even with all the data, finding BatMobi was a nightmare: It hides deep within an app’s code, in different apps on each user’s device, and no other mobile anti-malware vendors detect it. Nevertheless, I was able to make some headway and find a couple of patterns of infection. Here were my findings.
Uptodown
The search started with the third-party app store Uptodown. More specifically, apps that download videos from YouTube, such as Videoder, Video Downloader, Snaptube, and TubeMate were delivering ads to users the most. These apps all come with hidden versions of BatMobi. Removing these apps solved the issue for many, but still it persisted for others.
Mi Mobile
Another component that further complicates detecting and removing BatMobi is that we found it on apps pre-installed on Mi Mobile devices—specifically, the Xiaomi Redmi Note 5. The infected apps are as listed:
Package name: com.mi.android.globalpersonalassistant App name: App vault
Package name: com.android.providers.downloads.ui App name: Downloads
Please note that not all versions of these apps have BatMobi nor do all Xiaomi Redmi Note 5 devices—only a select few. Detections are in place in Malwarebytes for Android to alert users of its presence.
If you are having issues with adware on pre-installed apps, you can follow our removal instructions for disabling or uninstalling.
Warning: Make sure to read Restoring apps onto the device (without factory reset) in the rare case you need to revert/restore apps.
Use this/these command(s) during step 7 under Uninstalling Adups via ADB command line to remove:
adb shell pm uninstall -k –user 0 com.mi.android.globalpersonalassistant adb shell pm uninstall -k –user 0 com.android.providers.downloads.ui
Still unknowns
Even after finding two dominant sources of the Batmobi infection, there are still cases left unsolved. You see, as suddenly as the ads appeared, they abruptly stopped in early March. Without active cases to see if removing apps will remediate or not, finding these deeply hidden BatMobi variants has become nearly impossible. I’m confident that there are versions still on Google Play, but finding them now is searching for a needle in millions of haystacks.
The scary reality of Ad SDKs
Technically, since these hidden BatMobi variants no longer trigger ads inappropriately, they are no longer considered adware. I suppose that’s the good news. My assumption is that BatMobi made a change on their servers without warning, thus triggering the ads in January. But we don’t know why there was an abrupt stop in March. What happened? Maybe an overwhelming amount of complaints to BatMobi caused a change of heart?
This all leaves us with an uneasy feeling about Ad SDKs. It highlights their power to switch from clean and safe to adware overnight. It’s a scary reality to have code lay dormant in legitimate apps that can turn malicious so quickly. I reiterate that yes, these website redirects were to relatively safe sites, but the potential for worse is present.
Developers beware
The last thing a developer wants is for their app to be on an anti-malware scanner’s adware list without warning. In the past, we have seen ad companies clearly move from legitimate to serving adware, becoming overly aggressive with data collection and/or aggressively pushing ad content, as in the case above. However, in those cases it was easy to make a clear cut distinction of the cause of infection. This time, its much more unclear which components were causing the issue, and so much is still left unknown.
Unfortunately, finding an Ad SDK that developers can trust is an ongoing challenge. All we can say is do your research and choose wisely. If an Ad SDK has any variants that are considered adware, as with BatMobi, it’s a wise decision to stay clear.
We don’t just report on phone security—we provide it
Cybersecurity risks should never spread beyond a headline. Keep threats off your mobile devices by downloading Malwarebytes for iOS, and Malwarebytes for Android today.










