The healthcare industry is no longer circling the drain, but it’s still in critical condition.
While many organizations in healthcare have aimed at or made positive strides toward a more robust cybersecurity and privacy posture, they still have a long way to go.
In 2018, healthcare had the highest number of breaches recorded compared to other industries. This is according to BakerHostetler’s 2019 Data Security Incident Response Report, which is in its fifth annual iteration this year.
Even today, black hat hackers are continuing to go after patient healthcare data, and as such breaches will only intensify, according to Business Insider. The HIPAA Journal, a website dedicated to covering HIPAA-related news, corroborates this intensity after seeing a steady reporting of at least one breach per day from January through March, 2019.
What’s causing these daily breaches?
Hacking and IT incidents, which include malware attacks, have been consistently topping the list.
Malware in healthcare sectors
Healthcare falls short on a lot of security measures: unpartitioned networks, reliance on legacy infrastructure, non-compliance with HIPAA security rules and NIST CSF controls, unmanaged IoT devices, vulnerable medical management apps, the slow implementation of government-recommended IT and cybersecurity practices over the last four years, and the lack of email authentication and low adoption of always-encrypted sessions. For starters.
More importantly, healthcare systems are massively susceptible to malware infection and hijacking, since there are little-to-no protections in place. And when the threats being lobbed at healthcare are more advanced, all that lagging on security takes its toll.
So which types of malware are targeting healthcare organizations? We have collated and analyzed data from our own product telemetry to determine the top malware aiming to infect systems and networks, exfiltrate patient data, and disrupt operations. Here are our results.
Trojans and riskware are common on healthcare systems
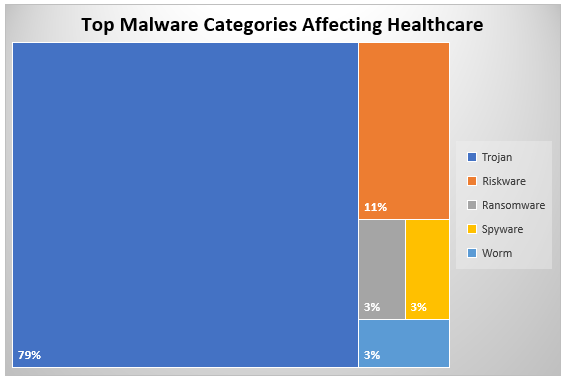
Among the five types of malware we found affecting healthcare systems, more than three-quarters (79 percent) are Trojans. This is followed by riskware (11 percent)—those pieces of software that are not inherently malicious, but could still pose a risk to systems on which they’re installed. Others are ransomware, spyware, and worms—all with an equal share of 3 percent.
We take a deep dive into each.
Trojans
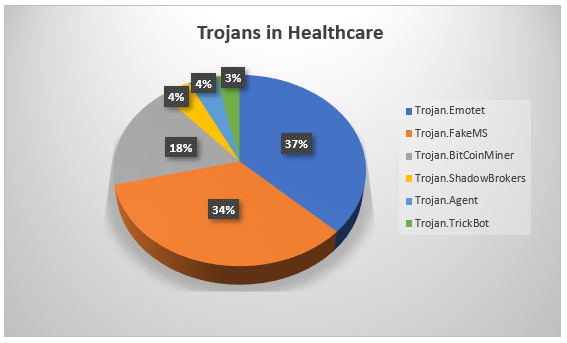
Based on our data, a sizable chunk of information-stealing Trojans and downloaders, as well as files posing as legitimate Microsoft (MS) files are present on healthcare systems. We detect them as Trojan.Emotet (35 percent) and Trojan.FakeMS (33 percent), respectively.
Emotet is an information stealer that can target user credentials stored in browsers and listen to network traffic. Known new versions of Emotet act as downloaders, dropping other banking Trojans, such as TrickBot and Qakbot, ransomware, such as Ryuk, and, at times, cryptominers and cryptowallet stealers.
Emotet has had success in penetrating organizations and spreading because of its simple, yet tried-and-true delivery method—phishing emails—as well as its use of an NSA exploit called EternalBlue, which pushes the infection laterally through networks. In addition, Emotet contains its own malspam module, which churns out additional phishing to continue the cycle.
To add insult to injury, once on networks, Emotet is notoriously difficult to remediate.
Information stealers, in general, are particularly dangerous to have in healthcare systems, as they put electronic health records (EHRs) at risk. Staff credentials can also be swiped and re-used by threat actors to gain access to more information and resources they can use, misuse, or sell to the highest bidders in the dark market.
Emotet has widely affected the health insurance, hospital, pharmaceutical, biotechnology, and medical device sectors. In fact, this threat has been consistently gaining ground on all organizations over the last year, increasing in both persistence and volume to the tune of almost 650 percent from the same time last year.
Trojan.FakeMS, on the other hand, is the detection we use for malware posing as legitimate Microsoft files. Healthcare personnel may or may not have been aware of such files ending up on their work systems. Either way, their presence on machines that staff rely on to processes sensitive records or pull up correct patient data at critical times isn’t ideal.
Meanwhile, cryptominer infections, which we sometimes detect as Trojans, often present machine slowdown as a common symptom, and 17 percent of healthcare systems have been showing this sign.
Cryptomining schemers, who may or may not be part of healthcare staff, can manually download miners, which we generically detect as Trojan.BitCoinMiner, from the Internet and discreetly install them onto machines that are used for record keeping. This resource abuse was the case for the Decatur County General Hospital in Tennessee when their electronic medical records (EMR) server has been hijacked in September 2017 to house a miner.
Riskware
As mentioned earlier, riskware is non-malicious; however, we flag it for a number of reasons, one of which is its ability to block other programs from receiving patches. This leaves the user’s machine open for exploitation by a number of threats, including EternalBlue mentioned above.
RiskWare.MicTray makes up 98 percent of our riskware detections in several healthcare sectors, primarily in health insurance and pharmaceuticals. MicTray is the name of our detection for the keylogger component present in the Conexant audio driver set.
The remaining 2 percent of detections are for Riskware.Tool.HCK, the name we use for tools or applications that may be illegal to use in certain countries. Cracked versions of paid software are examples of this.
Ransomware
Ransom.WannaCrypt, otherwise known as WannaCry, is the ransomware responsible for crippling the UK’s National Health Services (NHS) in 2017, costing them a total of £92 million (approximately $120 million) from cancelled appointments due to unusable systems to remediation and IT system upgrades. It’s also the malware that forced the healthcare industry to take cybersecurity and privacy seriously.
More than a year later, WannaCry is still at large and continues to affect organizations across industries and countries, disrupting normal operations and putting patient lives and data at risk.
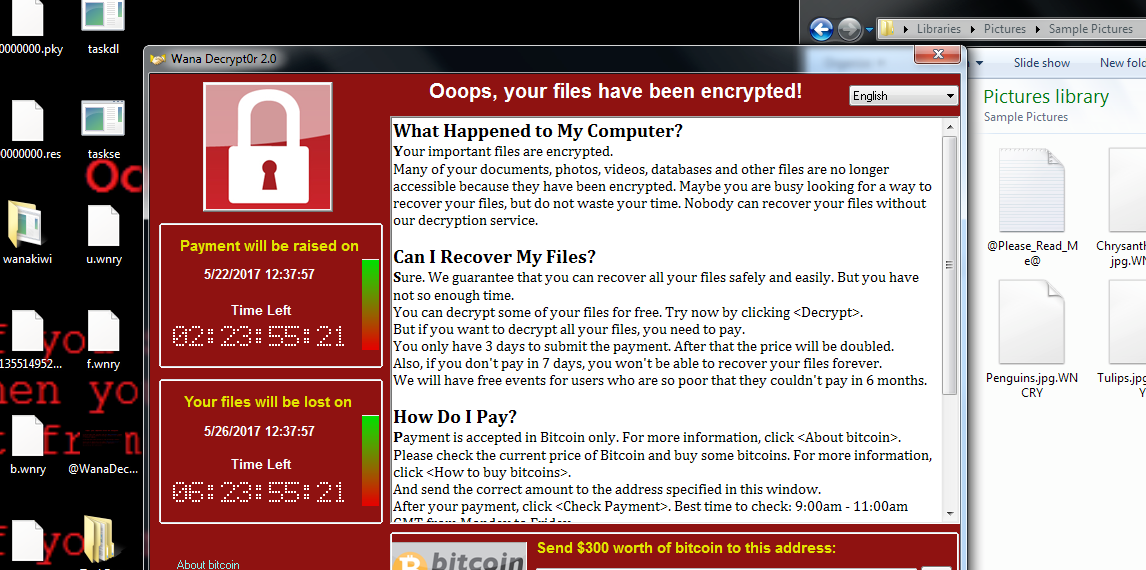
Our data shows that WannaCry is currently in the top five malware families affecting healthcare. This could also mean that a vast number of systems are still open to the EternalBlue vulnerability, waiting to be exploited.
Spyware
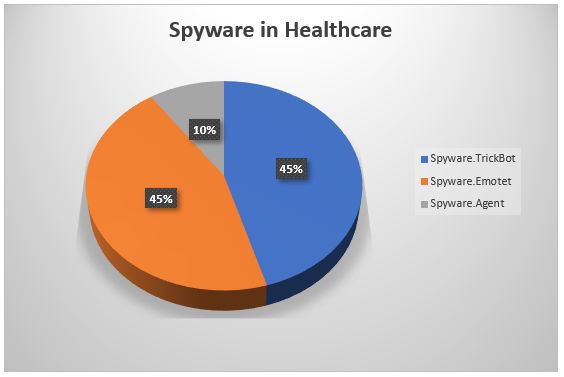
When it comes to spyware in healthcare, Spyware.TrickBot and Spyware.Emotet have dominated the detection count at 45 percent each. Spyware.Agent accounted for 10 percent of our total spyware detections in healthcare.
As secondary infections to Trojan.TrickBot and Trojan.Emotet, it’s no surprise to see TrickBot and Emotet spyware on healthcare systems. Normal users hardly notice how these information stealer modules work in the background; however, network admins may be able to spot odd connections to blacklisted domains as an attempt to reach command-and-control (C&C) servers to upload stolen data.
Worms
Worm.Parite, a detection name we use for a polymorphic file infector targeting executable programs (files ending in .exe) and screensavers (files ending in .scr) on local and shared networked drives, is the only one of its kind affecting systems within the biotech/medical sector.
One thing to note about Parite is that systems it infects may not show any obvious signs of infection—at least at first. Once a user executes an infected file, the virus code attached to it runs, and then passes back the control to the .exe or .scr file so it executes as normal.
If users don’t address a worm or virus infection, the system is at risk of further infection and exploitation from other malware.
Oh, and one more thing: fileless malware
Fileless malware is one of those new schemes that black hat hackers adopted several years ago, and they continue to do so at an ever-increasing pace.
A fileless infection means that traces of actual malware present on the affected system are so minute that it evades regular antivirus detection and makes the work of grabbing samples a challenge to security analysts.
Our telemetry data has revealed that, although nominal, fileless malware are present in healthcare organization systems, among them the health insurance and pharmaceutical sectors.
We are able to detect fileless infections flagged as Rootkit.Fileless.MTGen. They’re our broad detection for fileless malware that use rootkits to hide their presence on affected systems.
Some examples of fileless malware that we’ve seen through the years include the following, which we have rounded up in a list below:
- Fileless infection: an overview
- Fileless malware: getting the lowdown on this insidious threat
- Fileless infections from exploit kit: an overview
No better time to act
The healthcare industry is ripe with opportunity. Despite the cybersecurity and privacy challenges it is working to address, it continues to evolve by embracing innovative technologies—such as blockchain, virtual reality, and artificial intelligence—and adopting new models to better serve patients. Of course, adding new technologies can sometimes make protecting systems more complex than it already is.
However healthcare organizations plan to move forward, there are still two simple objectives they must not lose sight of: the security of systems and devices from malware, zero-day vulnerabilities, and hardware hacks, and the protection of patient healthcare data from thieves and malicious insiders.
In mid-April, researchers from the Ben Gurion University released their study on the malicious tampering of CT scans using deep learning AI. According to their paper, they were able to successfully demonstrate how threat actors can remove or add evidence of medical conditions on scans. They used a man-in-the-middle device, which is another computer loaded with malware to gain access to CT scans and feed medical devices with false information. If such a technology would be used in the wild, people’s medical records and treatment plans would be at risk, jeopardizing their overall health.
Indeed, healthcare organizations have a lot of catching up to do to protect themselves from online threats that continue to grow in sophistication. A lot more is at stake within this sector than virtually any other. It’s not just potential earnings or sensitive data at risk if cybersecurity is breached. Patients’ lives are at stake.
To keep the aforementioned objectives in focus, we recommend healthcare organizations visit these guides to shape up their security posture:
- Physician, protect thyself: An ounce of prevention is worth a pound of cure
- Building an incident response program: creating the framework
- How to create an intentional culture of security
- Who is managing the security of medical management apps?
- How to create a successful cybersecurity policy
- The not-so-definitive guide to cybersecurity and data privacy laws
- 10 easy ways to prevent malware infection
Stay safe!










