“Hey you. Someone from HR has invited you to a meeting on Thursday. Would you like me to add the appointment to the calendar?”
Receiving an email notification when someone has invited you to a meeting is a feature that many professionals would not like to miss. Being able to log in at certain sites with your Facebook profile might be less indispensable, but nevertheless, it’s a heavily-used functionality. What do these two functions have in common? They both require an integration between different apps, and this opens up some security and privacy risks.
Some practical problems
Recently, we were reminded that the Google Calendar notifications in Gmail provided scammers with the option to spam users with phishing links to sites that are out to steal user credentials. Basically, scammers were able to craft the links in the invitation so that they included a malicious link. Since this is a relatively unknown method, most people wouldn’t think twice before clicking.
Logging into sites with social media profiles more than doubles the privacy risks you run into by using either app separately. We say this because the data used by either app can easily be combined with those of the other app—therefore cybercriminals can come away with double the payday.
You may have seen these login options for Twitter, Google, and Facebook. And Facebook combines these risks with yet another problem. Many people that canceled their Facebook accounts (or thought they did) have found that coming back to a site where they used to log in with their Facebook account revives said Facebook profile and opens it up for the world to see again.

And we haven’t even touched upon the apps that grab the permission to post on these social media sites on your behalf.
Underlying problems
Before we can start to look for effective countermeasures, we need to understand the real foundation behind these security risks. The most common and well-known problems include:
- Apps that refuse to work without permissions. They shouldn’t require integration.
- Apps that grant other apps access to their data and settings.
- Apps that are downloaded and installed by impulse. We tend to forget about them after we’ve stopped using them, but the data sharing goes on.
- Jailbreaking, rooting, and sideloading apps. Apps outside the Google Play or App Store are not as secure. However, popular games like Fortnite were not available in Google Play, basically forcing their fans to compromise their safety to install the game.
- Lack of awareness of the implications of granting permissions. Even when the permissions are clearly communicated (the app will be able to post to your Twitter account, for example), users have the inclination to think it will be all right to allow “trusted apps” full permissions.
Even though not every app in the Play Store is 100 percent trustworthy, you can be assured that at least some security checks have been performed. Google does require developers to limit their device permission requests to what’s really necessary for the app. And they do block many apps from the Play Store because they may be harmful, but there are always those that manage to slither through.
These are just the measures taken against apps that are potentially harmful. We shouldn’t forget those that invade or risk your privacy. What’s important to remember here is that when you are installing apps from other unknown sources, they most likely didn’t have to pass any scrutiny at all—and are a likely security or privacy risk.
A regular check of your list of apps may result in some good device-cleaning, which not only reduces your attack surface, but also might improve your device’s performance and speed. While you’re at it, check the permissions on some of the apps that you decide to keep. They may not need all of them to do what you want or expect the app to do for you.
When an app asks for permissions, carefully read what it is asking for and let that sink in before you allow it. I know that these requests always seem to come at an inconvenient moment. You are in a hurry and you want that notification out of your way so you can carry on and use the app.
But consider why a gaming app is asking for access to GPS location. Or how come that financial app wants access to all of your contacts. Is the app really worth turning over that private information? Also note that these requests are not limited to the install process. They may come after an update or when you are trying a new feature.null
Partial solutions
Right now, without more user awareness of the security risks of integration, and without the applications, software programs, or social media platforms narrowing down their permissions requests to only what’s necessary to make the program work, there are only partial solutions for those looking for convenient installation or login processes. However, these solutions do improve your overall security posture without sacrificing too many benefits.
When it comes to integrations, there are a few tips we are happy to share.
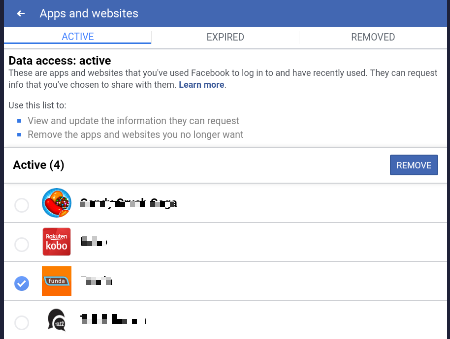
If you decide to unpair your apps and websites from Facebook, follow the directions below:
- Under the Facebook menu, go to Settings.
- Under Security, select Apps and websites then click on the “Logged in with Facebook” section.
- Select to remove all the entries that you will no longer be using. You can also see what information each app was able to retrieve from your Facebook profile. Quite an eye-opener.
Google has an informative page in their Help Center about giving third-party apps access to your Google account. It reads:
“Depending on how you use Google products, some of the information in your account may be extra sensitive. When you give access to third-parties, they may be able to read, edit, delete, or share this private information.”
The integration between Gmail and Google calendar can be rendered less automated (and thus less of a security risk) by turning off the automatic calendar invitations feature. Here are the directions:
- Go to the Event Setting menu in Google Calendar and disable the automatically add invitations option.
- Enable the only show invitations to which I’ve responded one instead.
- Also, users are advised to make sure that the Show declined events in the “View Options” section is also left unchecked.
Twitter has a similar page as Google called About third-party applications and log in sessions which warns:
“You should be cautious before giving third-party applications access to use your account.”
The page also provides information on how to remove access for sites and apps. Have a look and check for any unexpected guests.
Cooperating apps
I realize that cooperating apps are designed to make our life easier. After all, it’s frustrating if the left hand doesn’t know what the right hand is doing. And when everything works seamlessly together, our online life has a natural flow. I’m just asking you to give it some thought before you blindly allow integrations and permissions.
It looks as though users have shifted mindsets from “I have nothing to hide” to “They already know everything anyway.” But in both cases, it is true that you don’t have to hand your personal data to “them” on a silver platter, no matter who they are. Your personal information is too valuable to just give away. After all, that’s why cybercriminals (and legitimate organizations) are after it to begin with.
Stay safe out there!











