Recently, one of the more dominant search hijacker families on our radar has started to display some curious behavior. The family in question is delivered by various Chrome extensions and classified as PUP.Optional.QxSearch because of its description in listings of installed extensions, which tells us that “QxSearch configures your default search settings.”
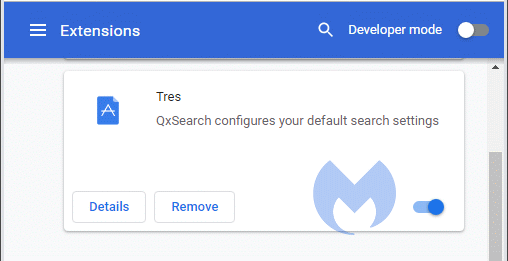
This branch of the search hijacker family is a clear descendant of SearchPrivacyPlus, which is referenced in our removal guide for a Chrome extension called SD App. The Chrome Web Store entries and websites that promote both QxSearch and SearchPrivacyPlus are almost identical. What’s different is that QxSearch tells users that the installation failed or that an extra step is required.
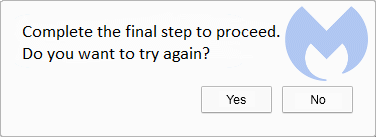
However, despite the message asking users to try again, the extension has already been installed. Curious.
How can we recognize QxSearch extensions?
QxSearch can be found in more than one Chrome extension in the Web Store. We can recognize them by spotting the QxSearch description, which also shows up in the overview section of the store.
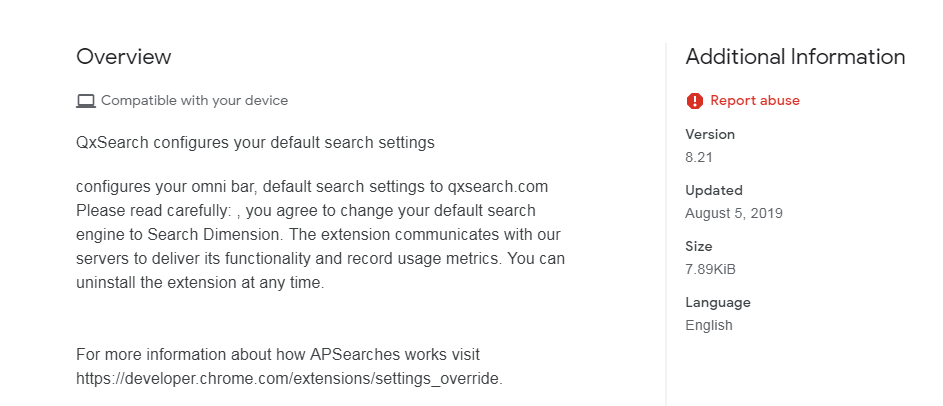
At the moment, these extensions are installed from the Web Store after a redirect from sites that are served up by ad-rotators. The sites all look similar, showing a prompt that tells users, “Flash SD App required to proceed” and a button marked “Browse Safely” that leads to the extension in the Web Store.
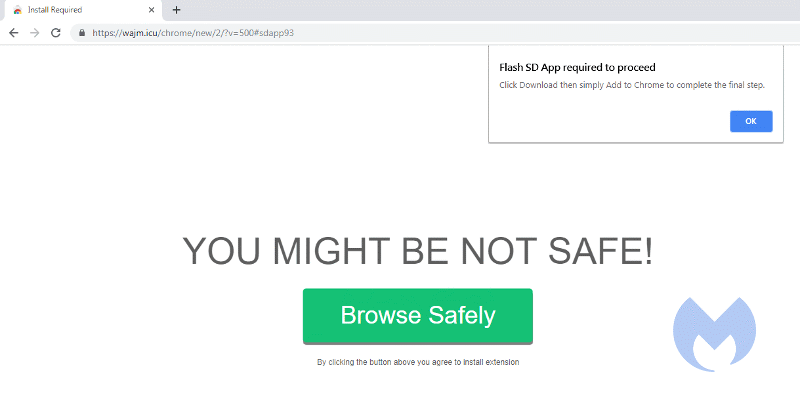
In the Web Store, another common denominator so far has been the “Offered by: AP” subhead.
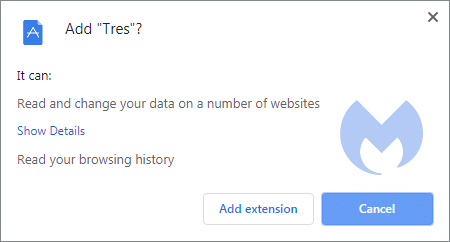
During the installation, the “Permissions prompt” will show that the extension reads and changes your data on a number of websites:
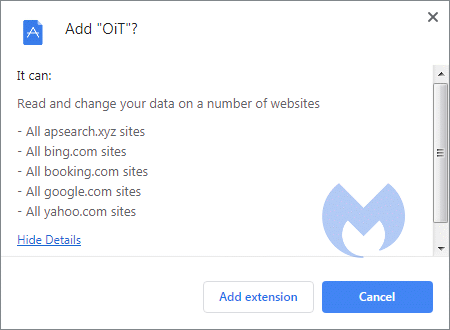
Using the “Show Details” link will show users that the sites they want to read and change belong to some of the most commonly-used search engines, including Google, Bing, and Yahoo.
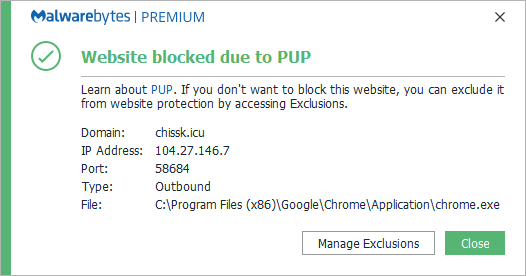
The hijacker intercepts searches performed on these domains and redirects the user to a domain of their own, showing the search results while adding some sponsored results at the top.
We are not sure whether the behavior of showing a failed install notification is by design or just sloppy programming, but given the fact that the “error” hasn’t been corrected after a few weeks, this leads us to believe it might be on purpose.
Looking at the installation process, it looks as if the fail occurs when the extension is due to add an icon to the browser’s menu bar. As a result, these hijackers do not display an icon—a handy way to make them more difficult to remove.
Protection against QxSearch
Malwarebytes removes these extensions and blocks the known sites that promote these extensions.
It is useless to blacklist the extensions, because a new one is pushed out at least once every day. So instead, we’ll show you some typical trademarks that they have in common so you can recognize them—and avoid them.
IOCs of QxSearch
Search result domains:
- qxsearch.com
- bigsrch.xyz
Landing pages:
- chissk.icu
- wajm.icu
- xv11.xyz
- … /chrome/new/2/?v=500#sdapp93
Similar but not the same
Another family of hijackers displays slightly similar behavior by showing an installation failed notification.
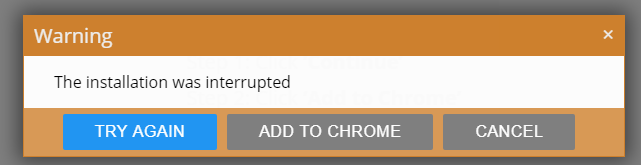
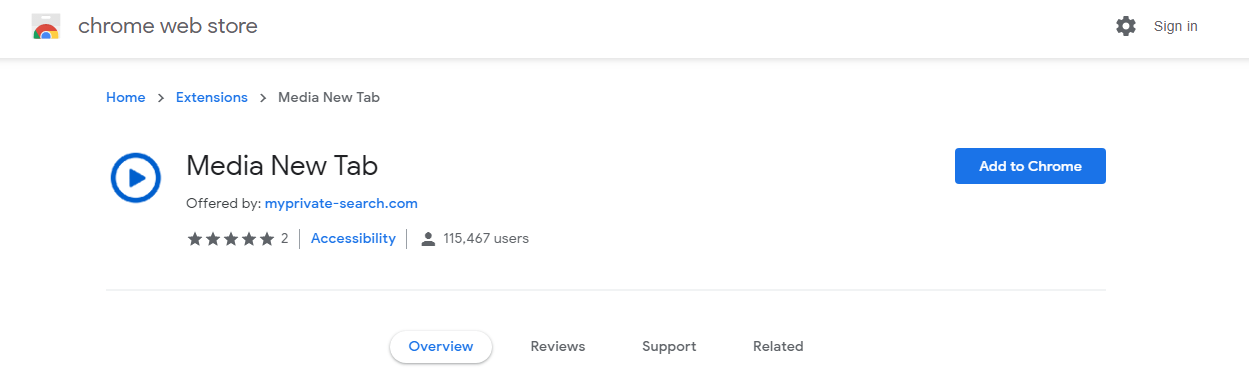
Only in this case the “interrupted installation” refers to the installation of a second extension that the first one tried to trigger. In this family, the first extension is a search hijacker and the second one is a “newtab” hijacker. The search hijackers in this family are detected as PUP.Optional.Safely and the Newtab hijacker is called Media New Tab.
Why would search hijackers do this?
Search hijackers don’t generate large amounts of cash for threat actors, like ransomware or banking Trojans. So, the publishers are always looking for ways to get installed on large numbers of systems and stay installed for as long as possible.
This “installation failed” tactic could have been invented to make users think nothing was installed, so there is no reason to check for or suspect suspicious behavior. This does not explain why they opted to redirect to their own domain rather than simply adding the sponsored results as we have seen in the past.
So, it remains a bit of a mystery and reason enough to keep an eye on this family.
Search hijackers in general
Search hijackers come in different flavors. Basically, they can be divided into three main categories if you look at their methodology:
- The hijacker redirects victims to the best paying search engine.
- The hijacker redirects victims to their own site and show additional sponsored ads.
- The hijacker redirects victims to a popular search engine after inserting or replacing sponsored ads.
By far the most common vehicle are browser extensions, whether they are called extensions, add-ons, or browser helper objects. But you will see different approaches here as well:
- The extension lets the hijacker take over as the default search engine.
- The extension takes over as “newtab” and shows a search field in that tab.
- The extension takes permission to read and change your data on websites. It uses these permissions to alter the outcome of the victim’s searches.
Especially in the case of both lists, it helps the hijacker to be hidden from plain sight as the user might not notice that his search results are “off.” Which seems to be exactly what this branch of the QxSearch family is doing.
A short lesson
The lesson we can take away from these search hijackers is that the sheer notification that an install has failed is not enough reason to assume that nothing was installed. Stay vigilant so that, even if the culprit isn’t readily visible, you’ll know what to do.
Stay safe everyone!











