Reports against the Bitcoin address, 1KE1EqyKLPzLWQ3BhRz2g1MHh5nws2TRk, started pouring in to Bitcoin abuse sites in late August just last week. As of this writing, this address has received a total of more or less 2,500 USD worth of Bitcoins.
After a quiet period following a surge in late 2018 to early 2019, the online blackmail scheme known as sextortion scams are back on the radar and on the uptick.
According to a report from Digital Shadows, a leading UK-based cybersecurity company that monitors potential threats against businesses, there are several resources available to embolden novice criminals to a life of extortion. These resources include: access to credentials leaked from past breaches, tools and technologies that aid in creating campaigns, training from online extortionists, and a trove of DIY extortion guides that exist on the dark web.
The report also finds that these fledgling extortionists and accomplices are incentivized with high salaries if they are able to hook high-earning targets, such as doctors, lawyers, or company executives—information that can be gleaned by scouring LinkedIn profiles or other social media accounts.
With a number of creative ways to wring money out of Internet users, the high potential of a hefty payout, and many helping hands from professional criminals, we shouldn’t expect online sextortion scams to stop (permanently) any time soon. Just ask the Nigerian Prince how well his retirement is going.
To look at what motivates threat actors to adopt sextortion scams as part of their criminal repertoire, we did what all good detectives do when trying to break open a case: We followed the money. Find out what we discovered on the trail begun by a single sextortion campaign.
The spam
We were able to determine several Bitcoin sextortion schemes being implemented in the wild, but for this post, we looked at its most common distribution form: email spam.
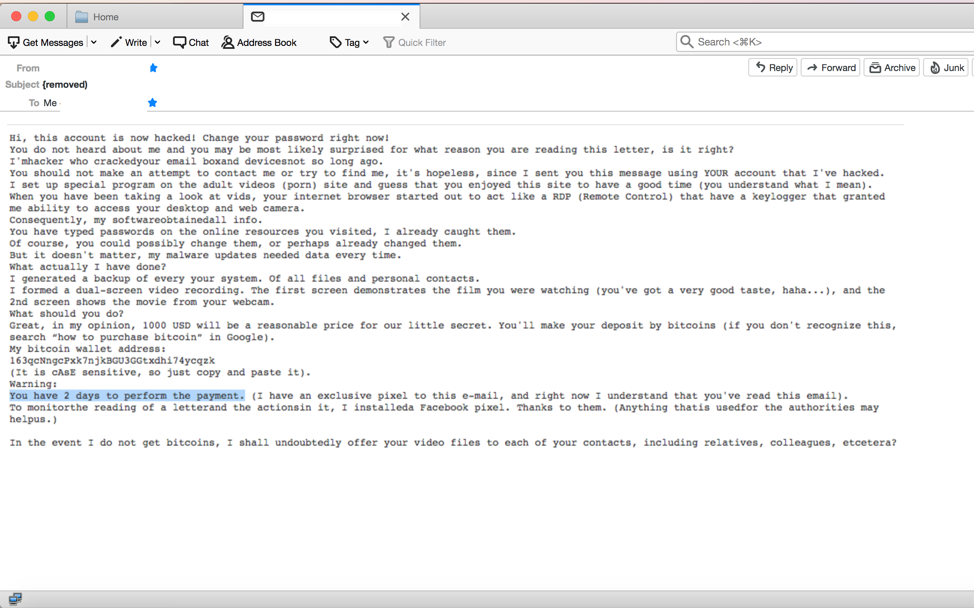
The full text of this email reads:
Hi, this account is now hacked! Change your password right now!
You do not heard about me and you may not be most likely surprised for what reason you are reading this letter, is it right?
I’mhacker who crackedyour email boxand devicesnot so long ago.
You should not make an attempt to contact me or try to find me, it’s hopeless, since I sent you this message using YOUR account that I’ve hacked.
I set up special program on the adult videos (porn) site and guess that you enjoyed this site to have a good time (you understand what I mean).
When you have been taking a look at vids, your internet browser started out to act like a RDP (Remote Control) that have a keylogger that granted me ability to access your desktop and web camera.
Consequently, my softwareobtainedall info.
You have typed passwords on the online resources you visited, I already caught them.
Of course, you could possibly change them, or perhaps already changed them.
But it doesn’t matter, my malware updates needed data every time.
What actually I have done?
I generated a backup of your every system. Of all files and personal contacts.
I formed a dual-screen video recording. The first screen demonstrates the film you were watching (you’ve got a very good taste, haha…), and the 2nd screen shows the movie from your webcam.
What should you do?
Great, in my opinion, 1000 USD will be a reasonable price for your little secret. You’ll make your deposit by bitcoins (if you don’t recognize this, search “how to purchase bitcoin” in Google).
My bitcoin wallet address:
163qcNngcPxk7njkBGU3GGtxdhi74ycqzk
(It is cAsE sensitive, so just copy and paste it).
Warning:
You have 2 days to perform the payment. (I have an exclusive pixel to this e-mail, and right now I understand that you’ve read this email).
To monitorthe reading of a letterhead the actionsin it, I installeda Facebook pixel. Thanks to them. (Anything thatis usedfor the authorities may helpus.)
In the event I do not get bitcoins, I shall undoubtedly offer your video files to each of your contacts, including relatives, colleagues, etcetera?
There are many variations of this spam content, but they all follow a similar template: We’ve hacked your account, we have video proof of you visiting porn sites and watching sexual content, and we now demand payment or we’ll release the video of you to the public. In fact, Cisco’s Talos Security Intelligence & Research Group was able to retrieve an email spam template, which they said the extortionists mistakenly sent out to their targets.
The Electronic Frontier Foundation (EFF) also keeps an updated record of variants of Bitcoin sextortion messages that you can look up in this blog post.
As we followed the money in this investigation, the only relevant piece of information we needed from the sextortion email was the Bitcoin address, which in this case is 163qcNngcPxk7njkBGU3GGtxdhi74ycqzk. This is our starting point.
The investigation
To better understand the next steps in our investigation, readers should first grasp the basics of how cryptocurrency and the blockchain work.
Paper money and coins are to the real, material world as digital currency is to the online, electronic world.
Bitcoin is one of thousands of digital currencies available online to date. Specifically, it is a virtual currency—because it is controlled by its creators and used and embraced by a virtual community—and at the same time a cryptocurrency—because it uses strong encryption algorithms and cryptographic schemes to ensure its resistant to forgery and cryptanalysis.
The blockchain, as the name suggests, is a collection of data blocks that are linked together to form a chain. This system, commonly likened to a ledger, is used by several cryptocurrencies—Bitcoin is one of them. Each block in a chain contains information on multiple transactions. And each transaction has a transaction ID, or TXID. Because of the way cryptocurrency wallets and sites record Bitcoin inputs to addresses, a single TXID may contain multiple entries in its record.
While real-world ledgers are private and exclusive only to organizations and individuals that keep financial records, the blockchain Bitcoin operates in is not. This makes it easy for anyone, including security researchers, to look up cryptocurrency transactions online using publicly available tools, such as a block explorer.
In a Bitcoin block, transaction information includes the sender and receiver—all identified by Bitcoin addresses—and the amount paid in Bitcoin.
Keep these concepts in mind as we go back to the sextortion campaign at hand and navigate the trenches of Bitcoin transactions.
Going with the (Bitcoin through the blockchain) flow
The Bitcoin address in our sextortion email, 163qcNngcPxk7njkBGU3GGtxdhi74ycqzk, actually has a small transaction history.
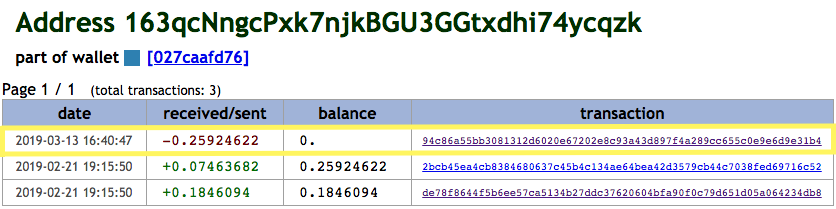
However, we were able to take a closer look at these transactions and uncover additional addresses, giving us further insight into this particular campaign.
According to TXID 94c86a55bb3081312d6020e67202e8c93a43d897f4a289cc655c0e9e6d9e31b4, the balance of 0.25924622 BTC was sent to another Bitcoin address, 3HXdb3HAw1wVzU9b7ZSigvGaStd8KoZ3zJ on March 13, 2019. During that time, this BTC value was worth approximately US$1,000, which is the amount demanded in the ransom email.
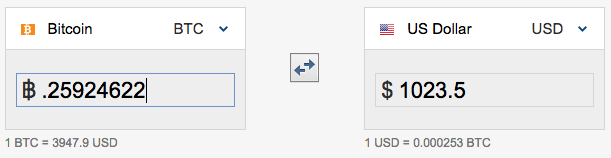
This TXID also contains 23 additional inputs from other Bitcoin addresses, which are likely also under the control of the same actor(s) behind the sextortion campaign, to 3HXdb3HAw1wVzU9b7ZSigvGaStd8KoZ3zJ. Naturally, all BTC values from these inputs were combined, totaling 4.16039634 BTC (approximately US$16,100 at time of investigation).
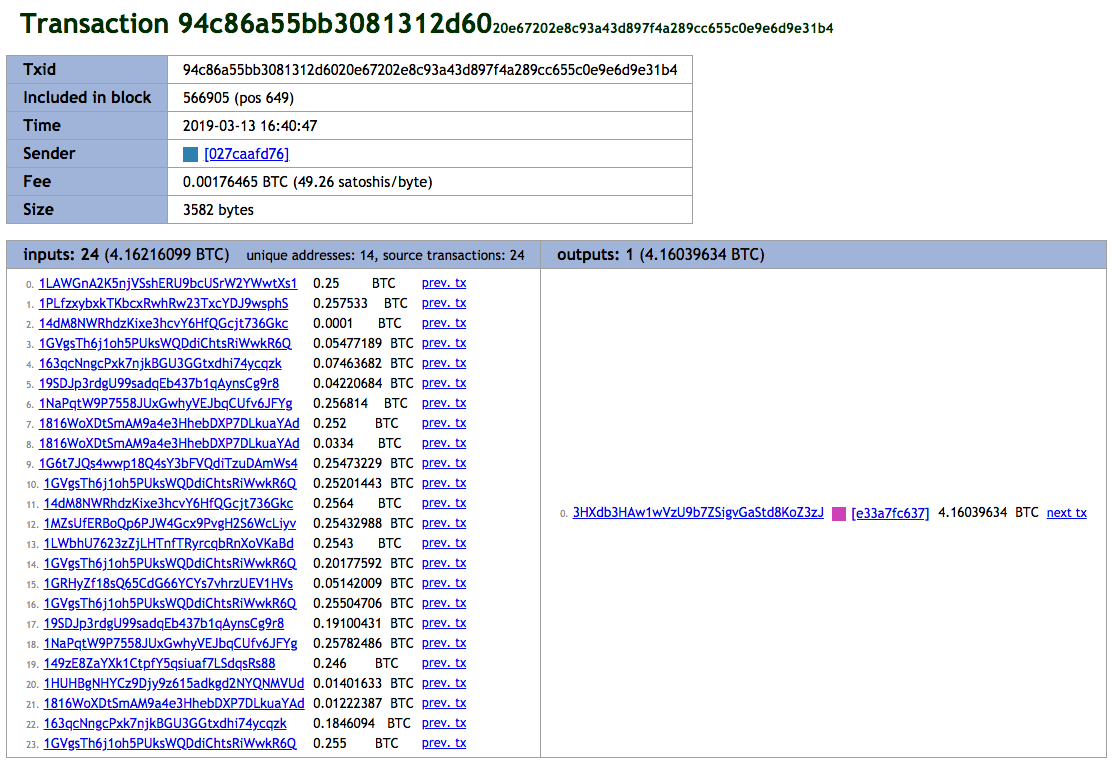
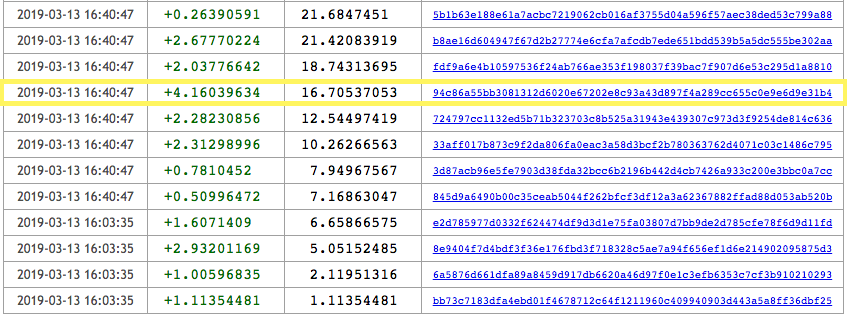
Looking closely at 3HXdb3HAw1wVzU9b7ZSigvGaStd8KoZ3zJ, we found it has 11 other transactions that follow a similar pattern to from the transaction we just reviewed.
We can confirm that that each of these transactions contains extorted funds. Take, for example, TXID b8ae16d604947f67d2b27774e6cfa7afcdb7ede651bdd539b5a5dc555be302aa:
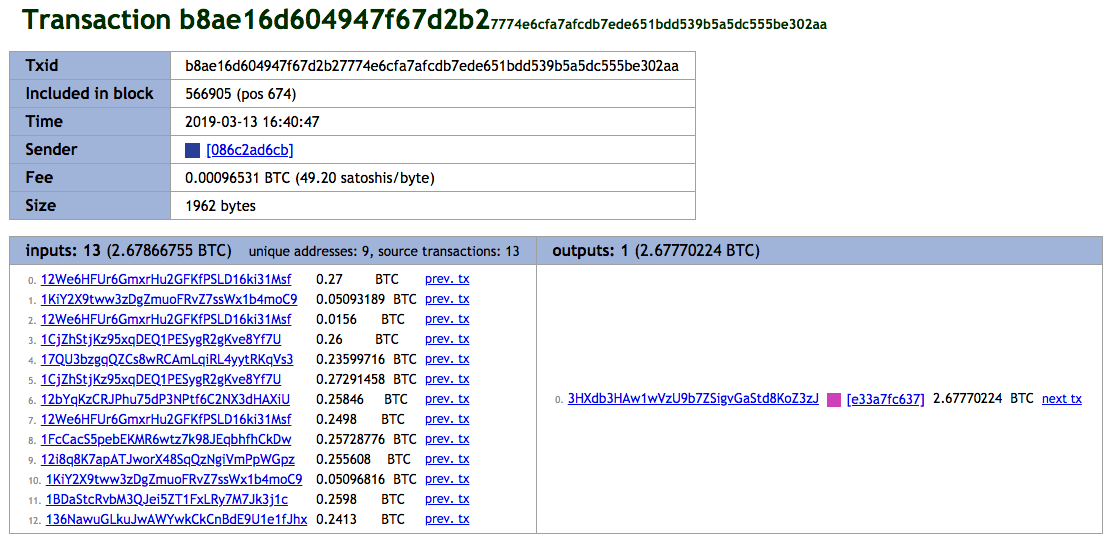
All Bitcoin addresses in this TXID have been reported as associated with criminal activity on Bitcoin-Spam, a public database of crypto-addresses used by hackers and criminals. Here are links to their respective scam reports and the amount of money they received based on the Bitcoin price as of this writing:
- 12We6HFUr6GmxrHu2GFKfPSLD16ki31Msf (made three inputs): received a total of US$5,297.32
- 1KiY2X9tww3zDgZmuoFRvZ7ssWx1b4moC9 (made two inputs): received a total of US$993.54
- 1CjZhStjKz95xqDEQ1PESygR2gKve8Yf7U (made two inputs): received a total of 7,748.92 USD
- 17QU3bzgqQZCs8wRCAmLqiRL4yytRKqVs3: received a total of US$4,672.65
- 12bYqKzCRJPhu75dP3NPtf6C2NX3dHAXiU: received a total of US$2,516.05
- 1FcCacS5pebEKMR6wtz7k98JEqbhfhCkDw: received a total of US$3,752.34
- 12i8q8K7apATJworX48SqQzNgiVmPpWGpz: received a total of US$2,490.25
- 1BDaStcRvbM3QJei5ZT1FxLRy7M7Jk3j1c: received a total of US$2,531.09
- 136NawuGLkuJwAWYwkCkCnBdE9U1e1fJhx: received a total of US$2,343.33
Further analysis past the consolidation address becomes difficult as the thieves begin a laundering process to hide their illicit gains by splitting and mixing the stolen funds.
This particular scam campaign appears to have been most active between February 1, 2019 until March 13, 2019, collecting a total of 21.6847451 BTC, which is a little over US$220,000 at current exchange rates.
Money, money, money
When it comes to email sextortion scams, suffice to say, business is unfortunately incredibly good. While the simplicity and profitability of the scam may serve an invitation for would-be criminals, the more users become aware of the scheme, the less we’ll be lining the bad guys’ pockets with our cryptocash.
But more importantly, this should be a wake-up call for users. A lot of people, even those who consider themselves Internet-savvy, are falling for or are rattled by the extortion messaging, especially those emails that make use of old passwords to scare innocent people into parting with their money.
If you or someone you know may have received sextortion emails, know that it’s highly likely they’re not watching you. What threat actors describe in their emails is not actually taking place.
Furthermore, don’t panic. Do your due diligence and secure accounts that have been affected by massive breaches in the past (if you haven’t already). And lastly, if you want to do as little hoop-jumping as possible, just delete the email and file them away in your mind as harmless spam.
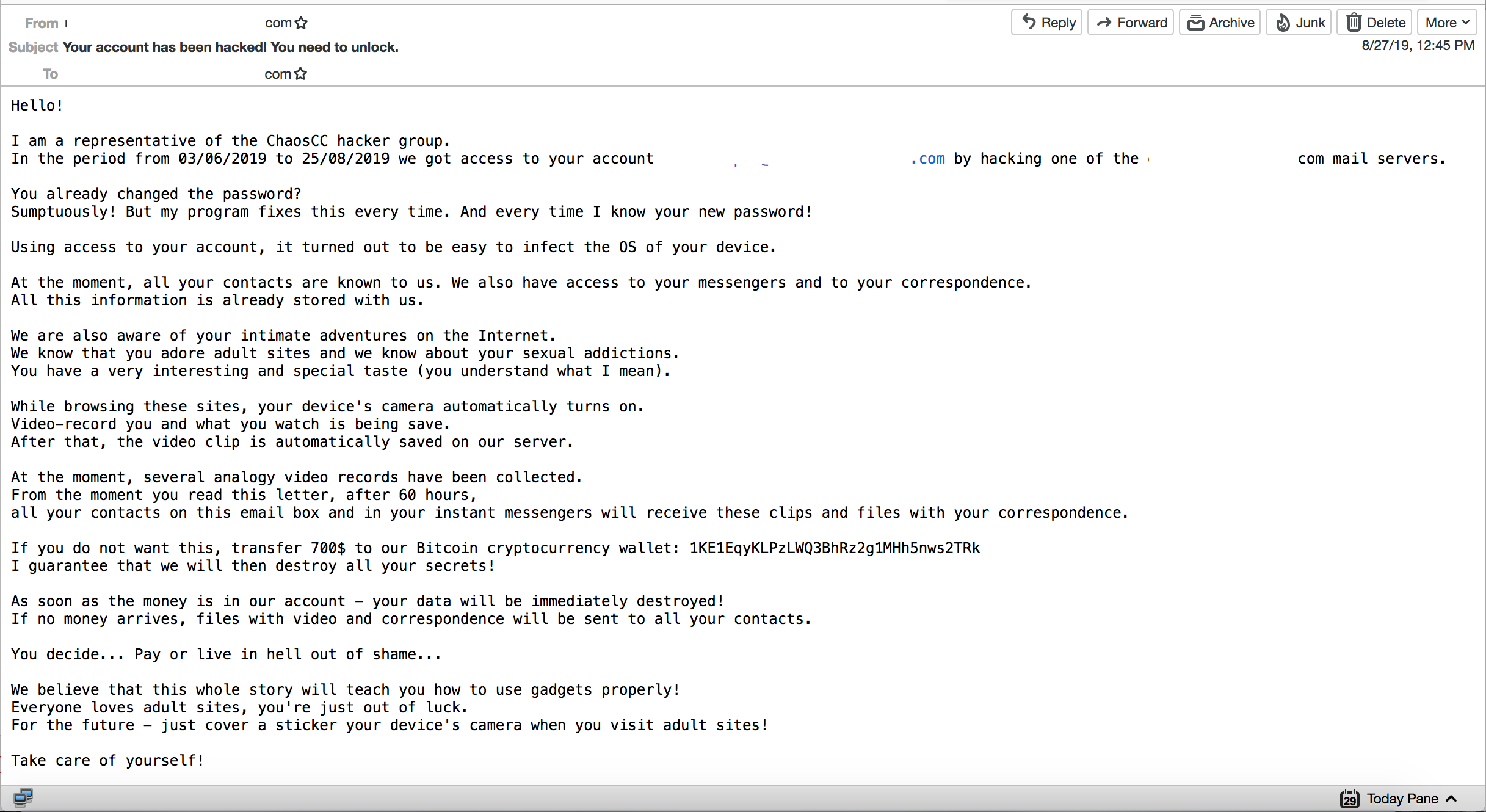
Update (2019-09-04): A new wave of sextortion emails purporting to have originated from a group of hackers called ChaosCC—a play on the legitimate European white hat hacking community, Chaos Computer Club (CCC)—has recently caught the attention of the security world. Below is a sample email we captured in our honeypot.

Reports against the Bitcoin address, 1KE1EqyKLPzLWQ3BhRz2g1MHh5nws2TRk, started pouring in to Bitcoin abuse sites in late August just last week. As of this writing, this address has received a total of more or less 2,500 USD worth of Bitcoins.
After a quiet period following a surge in late 2018 to early 2019, the online blackmail scheme known as sextortion scams are back on the radar and on the uptick.
According to a report from Digital Shadows, a leading UK-based cybersecurity company that monitors potential threats against businesses, there are several resources available to embolden novice criminals to a life of extortion. These resources include: access to credentials leaked from past breaches, tools and technologies that aid in creating campaigns, training from online extortionists, and a trove of DIY extortion guides that exist on the dark web.
The report also finds that these fledgling extortionists and accomplices are incentivized with high salaries if they are able to hook high-earning targets, such as doctors, lawyers, or company executives—information that can be gleaned by scouring LinkedIn profiles or other social media accounts.
With a number of creative ways to wring money out of Internet users, the high potential of a hefty payout, and many helping hands from professional criminals, we shouldn’t expect online sextortion scams to stop (permanently) any time soon. Just ask the Nigerian Prince how well his retirement is going.
To look at what motivates threat actors to adopt sextortion scams as part of their criminal repertoire, we did what all good detectives do when trying to break open a case: We followed the money. Find out what we discovered on the trail begun by a single sextortion campaign.
The spam
We were able to determine several Bitcoin sextortion schemes being implemented in the wild, but for this post, we looked at its most common distribution form: email spam.

The full text of this email reads:
Hi, this account is now hacked! Change your password right now!
You do not heard about me and you may not be most likely surprised for what reason you are reading this letter, is it right?
I’mhacker who crackedyour email boxand devicesnot so long ago.
You should not make an attempt to contact me or try to find me, it’s hopeless, since I sent you this message using YOUR account that I’ve hacked.
I set up special program on the adult videos (porn) site and guess that you enjoyed this site to have a good time (you understand what I mean).
When you have been taking a look at vids, your internet browser started out to act like a RDP (Remote Control) that have a keylogger that granted me ability to access your desktop and web camera.
Consequently, my softwareobtainedall info.
You have typed passwords on the online resources you visited, I already caught them.
Of course, you could possibly change them, or perhaps already changed them.
But it doesn’t matter, my malware updates needed data every time.
What actually I have done?
I generated a backup of your every system. Of all files and personal contacts.
I formed a dual-screen video recording. The first screen demonstrates the film you were watching (you’ve got a very good taste, haha…), and the 2nd screen shows the movie from your webcam.
What should you do?
Great, in my opinion, 1000 USD will be a reasonable price for your little secret. You’ll make your deposit by bitcoins (if you don’t recognize this, search “how to purchase bitcoin” in Google).
My bitcoin wallet address:
163qcNngcPxk7njkBGU3GGtxdhi74ycqzk
(It is cAsE sensitive, so just copy and paste it).
Warning:
You have 2 days to perform the payment. (I have an exclusive pixel to this e-mail, and right now I understand that you’ve read this email).
To monitorthe reading of a letterhead the actionsin it, I installeda Facebook pixel. Thanks to them. (Anything thatis usedfor the authorities may helpus.)
In the event I do not get bitcoins, I shall undoubtedly offer your video files to each of your contacts, including relatives, colleagues, etcetera?
There are many variations of this spam content, but they all follow a similar template: We’ve hacked your account, we have video proof of you visiting porn sites and watching sexual content, and we now demand payment or we’ll release the video of you to the public. In fact, Cisco’s Talos Security Intelligence & Research Group was able to retrieve an email spam template, which they said the extortionists mistakenly sent out to their targets.
The Electronic Frontier Foundation (EFF) also keeps an updated record of variants of Bitcoin sextortion messages that you can look up in this blog post.
As we followed the money in this investigation, the only relevant piece of information we needed from the sextortion email was the Bitcoin address, which in this case is 163qcNngcPxk7njkBGU3GGtxdhi74ycqzk. This is our starting point.
The investigation
To better understand the next steps in our investigation, readers should first grasp the basics of how cryptocurrency and the blockchain work.
Paper money and coins are to the real, material world as digital currency is to the online, electronic world.
Bitcoin is one of thousands of digital currencies available online to date. Specifically, it is a virtual currency—because it is controlled by its creators and used and embraced by a virtual community—and at the same time a cryptocurrency—because it uses strong encryption algorithms and cryptographic schemes to ensure its resistant to forgery and cryptanalysis.
The blockchain, as the name suggests, is a collection of data blocks that are linked together to form a chain. This system, commonly likened to a ledger, is used by several cryptocurrencies—Bitcoin is one of them. Each block in a chain contains information on multiple transactions. And each transaction has a transaction ID, or TXID. Because of the way cryptocurrency wallets and sites record Bitcoin inputs to addresses, a single TXID may contain multiple entries in its record.
While real-world ledgers are private and exclusive only to organizations and individuals that keep financial records, the blockchain Bitcoin operates in is not. This makes it easy for anyone, including security researchers, to look up cryptocurrency transactions online using publicly available tools, such as a block explorer.
In a Bitcoin block, transaction information includes the sender and receiver—all identified by Bitcoin addresses—and the amount paid in Bitcoin.
Keep these concepts in mind as we go back to the sextortion campaign at hand and navigate the trenches of Bitcoin transactions.
Going with the (Bitcoin through the blockchain) flow
The Bitcoin address in our sextortion email, 163qcNngcPxk7njkBGU3GGtxdhi74ycqzk, actually has a small transaction history.

However, we were able to take a closer look at these transactions and uncover additional addresses, giving us further insight into this particular campaign.
According to TXID 94c86a55bb3081312d6020e67202e8c93a43d897f4a289cc655c0e9e6d9e31b4, the balance of 0.25924622 BTC was sent to another Bitcoin address, 3HXdb3HAw1wVzU9b7ZSigvGaStd8KoZ3zJ on March 13, 2019. During that time, this BTC value was worth approximately US$1,000, which is the amount demanded in the ransom email.

This TXID also contains 23 additional inputs from other Bitcoin addresses, which are likely also under the control of the same actor(s) behind the sextortion campaign, to 3HXdb3HAw1wVzU9b7ZSigvGaStd8KoZ3zJ. Naturally, all BTC values from these inputs were combined, totaling 4.16039634 BTC (approximately US$16,100 at time of investigation).

Looking closely at 3HXdb3HAw1wVzU9b7ZSigvGaStd8KoZ3zJ, we found it has 11 other transactions that follow a similar pattern to from the transaction we just reviewed.

We can confirm that that each of these transactions contains extorted funds. Take, for example, TXID b8ae16d604947f67d2b27774e6cfa7afcdb7ede651bdd539b5a5dc555be302aa:

All Bitcoin addresses in this TXID have been reported as associated with criminal activity on Bitcoin-Spam, a public database of crypto-addresses used by hackers and criminals. Here are links to their respective scam reports and the amount of money they received based on the Bitcoin price as of this writing:
- 12We6HFUr6GmxrHu2GFKfPSLD16ki31Msf (made three inputs): received a total of US$5,297.32
- 1KiY2X9tww3zDgZmuoFRvZ7ssWx1b4moC9 (made two inputs): received a total of US$993.54
- 1CjZhStjKz95xqDEQ1PESygR2gKve8Yf7U (made two inputs): received a total of 7,748.92 USD
- 17QU3bzgqQZCs8wRCAmLqiRL4yytRKqVs3: received a total of US$4,672.65
- 12bYqKzCRJPhu75dP3NPtf6C2NX3dHAXiU: received a total of US$2,516.05
- 1FcCacS5pebEKMR6wtz7k98JEqbhfhCkDw: received a total of US$3,752.34
- 12i8q8K7apATJworX48SqQzNgiVmPpWGpz: received a total of US$2,490.25
- 1BDaStcRvbM3QJei5ZT1FxLRy7M7Jk3j1c: received a total of US$2,531.09
- 136NawuGLkuJwAWYwkCkCnBdE9U1e1fJhx: received a total of US$2,343.33
Further analysis past the consolidation address becomes difficult as the thieves begin a laundering process to hide their illicit gains by splitting and mixing the stolen funds.
This particular scam campaign appears to have been most active between February 1, 2019 until March 13, 2019, collecting a total of 21.6847451 BTC, which is a little over US$220,000 at current exchange rates.
Money, money, money
When it comes to email sextortion scams, suffice to say, business is unfortunately incredibly good. While the simplicity and profitability of the scam may serve an invitation for would-be criminals, the more users become aware of the scheme, the less we’ll be lining the bad guys’ pockets with our cryptocash.
But more importantly, this should be a wake-up call for users. A lot of people, even those who consider themselves Internet-savvy, are falling for or are rattled by the extortion messaging, especially those emails that make use of old passwords to scare innocent people into parting with their money.
If you or someone you know may have received sextortion emails, know that it’s highly likely they’re not watching you. What threat actors describe in their emails is not actually taking place.
Furthermore, don’t panic. Do your due diligence and secure accounts that have been affected by massive breaches in the past (if you haven’t already). And lastly, if you want to do as little hoop-jumping as possible, just delete the email and file them away in your mind as harmless spam.










