Interestingly, this Smoke Loader instance also downloads Raccoon Stealer and ZLoader.
Malsmoke is probably the most persistent malvertising campaigns we have seen this year. Unlike other threat actors, this group has shown that it can rapidly switch ad networks to keep their business uninterrupted.
Still using Internet Explorer?
Threat actors still leveraging exploit kits to deliver malware is one thing, but end users browsing with Internet Explorer is another. Despite recommendations from Microsoft and security professionals, we can only witness that there are still a number of users (consumer and enterprise) worldwide that have yet to migrate to a modern and fully supported browser.
As a result, exploit kit authors are squeezing the last bit of juice from vulnerabilities in Internet Explorer and Flash Player (due to retire for good next year).
Malwarebytes customers have long been protected from malvertising and exploit kits. We continue to track and report the campaigns we run into to help do our part in keeping the Internet safer.
Indicators of compromise
Gates used in malvertising campaign pushing Raccoon Stealer
intica-deco[.]com
websolvent[.]me
Raccoon Stealer
b289155154642ba8e9b032490a20c4a2c09b925e5b85dda11fc85d377baa6a6c
f319264b36cdf0daeb6174a43aaf4a6684775e6f0fb69aaf2d7dc051a593de93
Raccoon Stealer C2s
34.105.147[.]92/gate/log.php
chinadevmonster[.]top/gate/log.php
Smoke Loader
23bef893e3af7cb49dc5ae0a14452ed781f841db7397dc3ebb689291fd701b6b
Smoke Loader C2s
dkajsdjiqwdwnfj[.]info
2831ujedkdajsdj[.]info
928eijdksasnfss[.]info
dkajsdjiqwdwnfj[.]info
2831ujedkdajsdj[.]info
928eijdksasnfss[.]info
Gates used in the malsmoke campaign
einlegesohle[.]com/indexx.php
adexhangetomatto[.]space
encelava[.]com/coexo.php
encelava[.]com/caac
uneaskie[.]com/ukexo.php
bumblizz[.]com/auexo.php
bumblizz[.]com/auflexexo.php
bumblizz[.]com/caexo.php
bumblizz[.]com/caflexexo.php
bumblizz[.]com/usexo.php
bumblizz[.]com/usflexexo.php
canadaversaliska[.]info/coflexexo.php
canadaversaliska[.]info/coflexo.php
canadaversaliska[.]info/ukflexexo.php
canadaversaliska[.]info/ukflexo.php
canadaversaliska[.]info/usflexexo.php
canadaversaliska[.]info/usflexo.php
krostaur[.]com/jpexo.php
krostaur[.]com/jpflexexo.php
krostaur[.]com/jpflexo.php
leiomity[.]com/ukexo.php
leiomity[.]com/ukflexexo.php
leiomity[.]com/usexo.php
leiomity[.]com/usflexexo.php
surdised[.]com/coexo.php
surdised[.]com/usexo.php
Tweets referencing the malsmoke campaign
https://twitter[.]com/MBThreatIntel/status/1245791188281462784 https://twitter[.]com/FaLconIntel/status/1232475345023987713 https://twitter[.]com/nao_sec/status/1231149711517634560 https://twitter[.]com/tkanalyst/status/1229794466816389120 https://twitter[.]com/nao_sec/status/1209090544711815169
The redirection mechanism is more sophisticated than those used in other malvertising campaigns. There is some client-side fingerprinting and connectivity checks to avoid VPNs and proxies, only targeting legitimate IP addresses.

Interestingly, this Smoke Loader instance also downloads Raccoon Stealer and ZLoader.
Malsmoke is probably the most persistent malvertising campaigns we have seen this year. Unlike other threat actors, this group has shown that it can rapidly switch ad networks to keep their business uninterrupted.

Still using Internet Explorer?
Threat actors still leveraging exploit kits to deliver malware is one thing, but end users browsing with Internet Explorer is another. Despite recommendations from Microsoft and security professionals, we can only witness that there are still a number of users (consumer and enterprise) worldwide that have yet to migrate to a modern and fully supported browser.
As a result, exploit kit authors are squeezing the last bit of juice from vulnerabilities in Internet Explorer and Flash Player (due to retire for good next year).
Malwarebytes customers have long been protected from malvertising and exploit kits. We continue to track and report the campaigns we run into to help do our part in keeping the Internet safer.
Indicators of compromise
Gates used in malvertising campaign pushing Raccoon Stealer
intica-deco[.]com
websolvent[.]me
Raccoon Stealer
b289155154642ba8e9b032490a20c4a2c09b925e5b85dda11fc85d377baa6a6c
f319264b36cdf0daeb6174a43aaf4a6684775e6f0fb69aaf2d7dc051a593de93
Raccoon Stealer C2s
34.105.147[.]92/gate/log.php
chinadevmonster[.]top/gate/log.php
Smoke Loader
23bef893e3af7cb49dc5ae0a14452ed781f841db7397dc3ebb689291fd701b6b
Smoke Loader C2s
dkajsdjiqwdwnfj[.]info
2831ujedkdajsdj[.]info
928eijdksasnfss[.]info
dkajsdjiqwdwnfj[.]info
2831ujedkdajsdj[.]info
928eijdksasnfss[.]info
Gates used in the malsmoke campaign
einlegesohle[.]com/indexx.php
adexhangetomatto[.]space
encelava[.]com/coexo.php
encelava[.]com/caac
uneaskie[.]com/ukexo.php
bumblizz[.]com/auexo.php
bumblizz[.]com/auflexexo.php
bumblizz[.]com/caexo.php
bumblizz[.]com/caflexexo.php
bumblizz[.]com/usexo.php
bumblizz[.]com/usflexexo.php
canadaversaliska[.]info/coflexexo.php
canadaversaliska[.]info/coflexo.php
canadaversaliska[.]info/ukflexexo.php
canadaversaliska[.]info/ukflexo.php
canadaversaliska[.]info/usflexexo.php
canadaversaliska[.]info/usflexo.php
krostaur[.]com/jpexo.php
krostaur[.]com/jpflexexo.php
krostaur[.]com/jpflexo.php
leiomity[.]com/ukexo.php
leiomity[.]com/ukflexexo.php
leiomity[.]com/usexo.php
leiomity[.]com/usflexexo.php
surdised[.]com/coexo.php
surdised[.]com/usexo.php
Tweets referencing the malsmoke campaign
https://twitter[.]com/MBThreatIntel/status/1245791188281462784 https://twitter[.]com/FaLconIntel/status/1232475345023987713 https://twitter[.]com/nao_sec/status/1231149711517634560 https://twitter[.]com/tkanalyst/status/1229794466816389120 https://twitter[.]com/nao_sec/status/1209090544711815169
Malvertising on top adult site gets maximum reach
The second malvertiser (‘malsmoke’) is one that we have tracked diligently over the past several months and whose end payload is often the Smoke Loader malware. It is by far the most daring and successful one in that it goes after larger publishers and a variety of ad networks. However, up until now we had only seen them on publishers from the adult industry that are still relatively small in scale.
In this instance, the threat actor was able to abuse the Traffic Stars ad network and place their malicious ad on xhamster[.]com, a site with just over 1.06 billion monthly visits according to SimilarWeb.com.
The gates used by this group also use a decoy site and over time they have registered domains mocking ad networks and cloud providers.

The redirection mechanism is more sophisticated than those used in other malvertising campaigns. There is some client-side fingerprinting and connectivity checks to avoid VPNs and proxies, only targeting legitimate IP addresses.

Interestingly, this Smoke Loader instance also downloads Raccoon Stealer and ZLoader.
Malsmoke is probably the most persistent malvertising campaigns we have seen this year. Unlike other threat actors, this group has shown that it can rapidly switch ad networks to keep their business uninterrupted.

Still using Internet Explorer?
Threat actors still leveraging exploit kits to deliver malware is one thing, but end users browsing with Internet Explorer is another. Despite recommendations from Microsoft and security professionals, we can only witness that there are still a number of users (consumer and enterprise) worldwide that have yet to migrate to a modern and fully supported browser.
As a result, exploit kit authors are squeezing the last bit of juice from vulnerabilities in Internet Explorer and Flash Player (due to retire for good next year).
Malwarebytes customers have long been protected from malvertising and exploit kits. We continue to track and report the campaigns we run into to help do our part in keeping the Internet safer.
Indicators of compromise
Gates used in malvertising campaign pushing Raccoon Stealer
intica-deco[.]com
websolvent[.]me
Raccoon Stealer
b289155154642ba8e9b032490a20c4a2c09b925e5b85dda11fc85d377baa6a6c
f319264b36cdf0daeb6174a43aaf4a6684775e6f0fb69aaf2d7dc051a593de93
Raccoon Stealer C2s
34.105.147[.]92/gate/log.php
chinadevmonster[.]top/gate/log.php
Smoke Loader
23bef893e3af7cb49dc5ae0a14452ed781f841db7397dc3ebb689291fd701b6b
Smoke Loader C2s
dkajsdjiqwdwnfj[.]info
2831ujedkdajsdj[.]info
928eijdksasnfss[.]info
dkajsdjiqwdwnfj[.]info
2831ujedkdajsdj[.]info
928eijdksasnfss[.]info
Gates used in the malsmoke campaign
einlegesohle[.]com/indexx.php
adexhangetomatto[.]space
encelava[.]com/coexo.php
encelava[.]com/caac
uneaskie[.]com/ukexo.php
bumblizz[.]com/auexo.php
bumblizz[.]com/auflexexo.php
bumblizz[.]com/caexo.php
bumblizz[.]com/caflexexo.php
bumblizz[.]com/usexo.php
bumblizz[.]com/usflexexo.php
canadaversaliska[.]info/coflexexo.php
canadaversaliska[.]info/coflexo.php
canadaversaliska[.]info/ukflexexo.php
canadaversaliska[.]info/ukflexo.php
canadaversaliska[.]info/usflexexo.php
canadaversaliska[.]info/usflexo.php
krostaur[.]com/jpexo.php
krostaur[.]com/jpflexexo.php
krostaur[.]com/jpflexo.php
leiomity[.]com/ukexo.php
leiomity[.]com/ukflexexo.php
leiomity[.]com/usexo.php
leiomity[.]com/usflexexo.php
surdised[.]com/coexo.php
surdised[.]com/usexo.php
Tweets referencing the malsmoke campaign
https://twitter[.]com/MBThreatIntel/status/1245791188281462784 https://twitter[.]com/FaLconIntel/status/1232475345023987713 https://twitter[.]com/nao_sec/status/1231149711517634560 https://twitter[.]com/tkanalyst/status/1229794466816389120 https://twitter[.]com/nao_sec/status/1209090544711815169
Beyond a common payload, those two domains are also related. A RiskIQ crawl confirms a relationship between these 2 domains where the parent host was caught doing a meta refresh redirect to the child:

Malvertising on top adult site gets maximum reach
The second malvertiser (‘malsmoke’) is one that we have tracked diligently over the past several months and whose end payload is often the Smoke Loader malware. It is by far the most daring and successful one in that it goes after larger publishers and a variety of ad networks. However, up until now we had only seen them on publishers from the adult industry that are still relatively small in scale.
In this instance, the threat actor was able to abuse the Traffic Stars ad network and place their malicious ad on xhamster[.]com, a site with just over 1.06 billion monthly visits according to SimilarWeb.com.
The gates used by this group also use a decoy site and over time they have registered domains mocking ad networks and cloud providers.

The redirection mechanism is more sophisticated than those used in other malvertising campaigns. There is some client-side fingerprinting and connectivity checks to avoid VPNs and proxies, only targeting legitimate IP addresses.

Interestingly, this Smoke Loader instance also downloads Raccoon Stealer and ZLoader.
Malsmoke is probably the most persistent malvertising campaigns we have seen this year. Unlike other threat actors, this group has shown that it can rapidly switch ad networks to keep their business uninterrupted.

Still using Internet Explorer?
Threat actors still leveraging exploit kits to deliver malware is one thing, but end users browsing with Internet Explorer is another. Despite recommendations from Microsoft and security professionals, we can only witness that there are still a number of users (consumer and enterprise) worldwide that have yet to migrate to a modern and fully supported browser.
As a result, exploit kit authors are squeezing the last bit of juice from vulnerabilities in Internet Explorer and Flash Player (due to retire for good next year).
Malwarebytes customers have long been protected from malvertising and exploit kits. We continue to track and report the campaigns we run into to help do our part in keeping the Internet safer.
Indicators of compromise
Gates used in malvertising campaign pushing Raccoon Stealer
intica-deco[.]com
websolvent[.]me
Raccoon Stealer
b289155154642ba8e9b032490a20c4a2c09b925e5b85dda11fc85d377baa6a6c
f319264b36cdf0daeb6174a43aaf4a6684775e6f0fb69aaf2d7dc051a593de93
Raccoon Stealer C2s
34.105.147[.]92/gate/log.php
chinadevmonster[.]top/gate/log.php
Smoke Loader
23bef893e3af7cb49dc5ae0a14452ed781f841db7397dc3ebb689291fd701b6b
Smoke Loader C2s
dkajsdjiqwdwnfj[.]info
2831ujedkdajsdj[.]info
928eijdksasnfss[.]info
dkajsdjiqwdwnfj[.]info
2831ujedkdajsdj[.]info
928eijdksasnfss[.]info
Gates used in the malsmoke campaign
einlegesohle[.]com/indexx.php
adexhangetomatto[.]space
encelava[.]com/coexo.php
encelava[.]com/caac
uneaskie[.]com/ukexo.php
bumblizz[.]com/auexo.php
bumblizz[.]com/auflexexo.php
bumblizz[.]com/caexo.php
bumblizz[.]com/caflexexo.php
bumblizz[.]com/usexo.php
bumblizz[.]com/usflexexo.php
canadaversaliska[.]info/coflexexo.php
canadaversaliska[.]info/coflexo.php
canadaversaliska[.]info/ukflexexo.php
canadaversaliska[.]info/ukflexo.php
canadaversaliska[.]info/usflexexo.php
canadaversaliska[.]info/usflexo.php
krostaur[.]com/jpexo.php
krostaur[.]com/jpflexexo.php
krostaur[.]com/jpflexo.php
leiomity[.]com/ukexo.php
leiomity[.]com/ukflexexo.php
leiomity[.]com/usexo.php
leiomity[.]com/usflexexo.php
surdised[.]com/coexo.php
surdised[.]com/usexo.php
Tweets referencing the malsmoke campaign
https://twitter[.]com/MBThreatIntel/status/1245791188281462784 https://twitter[.]com/FaLconIntel/status/1232475345023987713 https://twitter[.]com/nao_sec/status/1231149711517634560 https://twitter[.]com/tkanalyst/status/1229794466816389120 https://twitter[.]com/nao_sec/status/1209090544711815169
About 10 days later, another domain, websolvent[.]me, became active but used a different redirection technique, a 302 redirect, also known as 302 cushioning. This time we see the RIG exploit kit which also delivers Raccoon Stealer.

Beyond a common payload, those two domains are also related. A RiskIQ crawl confirms a relationship between these 2 domains where the parent host was caught doing a meta refresh redirect to the child:

Malvertising on top adult site gets maximum reach
The second malvertiser (‘malsmoke’) is one that we have tracked diligently over the past several months and whose end payload is often the Smoke Loader malware. It is by far the most daring and successful one in that it goes after larger publishers and a variety of ad networks. However, up until now we had only seen them on publishers from the adult industry that are still relatively small in scale.
In this instance, the threat actor was able to abuse the Traffic Stars ad network and place their malicious ad on xhamster[.]com, a site with just over 1.06 billion monthly visits according to SimilarWeb.com.
The gates used by this group also use a decoy site and over time they have registered domains mocking ad networks and cloud providers.

The redirection mechanism is more sophisticated than those used in other malvertising campaigns. There is some client-side fingerprinting and connectivity checks to avoid VPNs and proxies, only targeting legitimate IP addresses.

Interestingly, this Smoke Loader instance also downloads Raccoon Stealer and ZLoader.
Malsmoke is probably the most persistent malvertising campaigns we have seen this year. Unlike other threat actors, this group has shown that it can rapidly switch ad networks to keep their business uninterrupted.

Still using Internet Explorer?
Threat actors still leveraging exploit kits to deliver malware is one thing, but end users browsing with Internet Explorer is another. Despite recommendations from Microsoft and security professionals, we can only witness that there are still a number of users (consumer and enterprise) worldwide that have yet to migrate to a modern and fully supported browser.
As a result, exploit kit authors are squeezing the last bit of juice from vulnerabilities in Internet Explorer and Flash Player (due to retire for good next year).
Malwarebytes customers have long been protected from malvertising and exploit kits. We continue to track and report the campaigns we run into to help do our part in keeping the Internet safer.
Indicators of compromise
Gates used in malvertising campaign pushing Raccoon Stealer
intica-deco[.]com
websolvent[.]me
Raccoon Stealer
b289155154642ba8e9b032490a20c4a2c09b925e5b85dda11fc85d377baa6a6c
f319264b36cdf0daeb6174a43aaf4a6684775e6f0fb69aaf2d7dc051a593de93
Raccoon Stealer C2s
34.105.147[.]92/gate/log.php
chinadevmonster[.]top/gate/log.php
Smoke Loader
23bef893e3af7cb49dc5ae0a14452ed781f841db7397dc3ebb689291fd701b6b
Smoke Loader C2s
dkajsdjiqwdwnfj[.]info
2831ujedkdajsdj[.]info
928eijdksasnfss[.]info
dkajsdjiqwdwnfj[.]info
2831ujedkdajsdj[.]info
928eijdksasnfss[.]info
Gates used in the malsmoke campaign
einlegesohle[.]com/indexx.php
adexhangetomatto[.]space
encelava[.]com/coexo.php
encelava[.]com/caac
uneaskie[.]com/ukexo.php
bumblizz[.]com/auexo.php
bumblizz[.]com/auflexexo.php
bumblizz[.]com/caexo.php
bumblizz[.]com/caflexexo.php
bumblizz[.]com/usexo.php
bumblizz[.]com/usflexexo.php
canadaversaliska[.]info/coflexexo.php
canadaversaliska[.]info/coflexo.php
canadaversaliska[.]info/ukflexexo.php
canadaversaliska[.]info/ukflexo.php
canadaversaliska[.]info/usflexexo.php
canadaversaliska[.]info/usflexo.php
krostaur[.]com/jpexo.php
krostaur[.]com/jpflexexo.php
krostaur[.]com/jpflexo.php
leiomity[.]com/ukexo.php
leiomity[.]com/ukflexexo.php
leiomity[.]com/usexo.php
leiomity[.]com/usflexexo.php
surdised[.]com/coexo.php
surdised[.]com/usexo.php
Tweets referencing the malsmoke campaign
https://twitter[.]com/MBThreatIntel/status/1245791188281462784 https://twitter[.]com/FaLconIntel/status/1232475345023987713 https://twitter[.]com/nao_sec/status/1231149711517634560 https://twitter[.]com/tkanalyst/status/1229794466816389120 https://twitter[.]com/nao_sec/status/1209090544711815169
Simple server-side cloaking performs the redirect to a Fallout exploit kit landing page which attempts to exploit CVE-2019-0752 (Internet Explorer) and CVE-2018-15982 (Flash Player) before dropping the Raccoon Stealer.

About 10 days later, another domain, websolvent[.]me, became active but used a different redirection technique, a 302 redirect, also known as 302 cushioning. This time we see the RIG exploit kit which also delivers Raccoon Stealer.

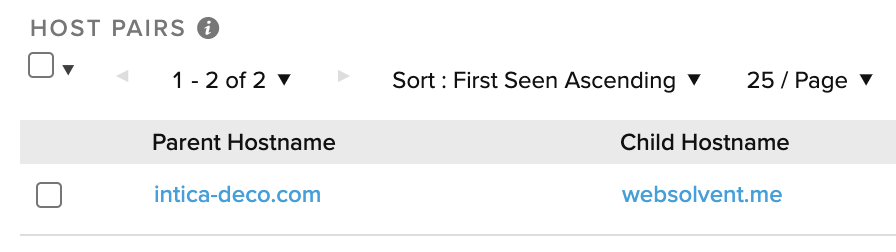
Beyond a common payload, those two domains are also related. A RiskIQ crawl confirms a relationship between these 2 domains where the parent host was caught doing a meta refresh redirect to the child:

Malvertising on top adult site gets maximum reach
The second malvertiser (‘malsmoke’) is one that we have tracked diligently over the past several months and whose end payload is often the Smoke Loader malware. It is by far the most daring and successful one in that it goes after larger publishers and a variety of ad networks. However, up until now we had only seen them on publishers from the adult industry that are still relatively small in scale.
In this instance, the threat actor was able to abuse the Traffic Stars ad network and place their malicious ad on xhamster[.]com, a site with just over 1.06 billion monthly visits according to SimilarWeb.com.
The gates used by this group also use a decoy site and over time they have registered domains mocking ad networks and cloud providers.

The redirection mechanism is more sophisticated than those used in other malvertising campaigns. There is some client-side fingerprinting and connectivity checks to avoid VPNs and proxies, only targeting legitimate IP addresses.

Interestingly, this Smoke Loader instance also downloads Raccoon Stealer and ZLoader.
Malsmoke is probably the most persistent malvertising campaigns we have seen this year. Unlike other threat actors, this group has shown that it can rapidly switch ad networks to keep their business uninterrupted.

Still using Internet Explorer?
Threat actors still leveraging exploit kits to deliver malware is one thing, but end users browsing with Internet Explorer is another. Despite recommendations from Microsoft and security professionals, we can only witness that there are still a number of users (consumer and enterprise) worldwide that have yet to migrate to a modern and fully supported browser.
As a result, exploit kit authors are squeezing the last bit of juice from vulnerabilities in Internet Explorer and Flash Player (due to retire for good next year).
Malwarebytes customers have long been protected from malvertising and exploit kits. We continue to track and report the campaigns we run into to help do our part in keeping the Internet safer.
Indicators of compromise
Gates used in malvertising campaign pushing Raccoon Stealer
intica-deco[.]com
websolvent[.]me
Raccoon Stealer
b289155154642ba8e9b032490a20c4a2c09b925e5b85dda11fc85d377baa6a6c
f319264b36cdf0daeb6174a43aaf4a6684775e6f0fb69aaf2d7dc051a593de93
Raccoon Stealer C2s
34.105.147[.]92/gate/log.php
chinadevmonster[.]top/gate/log.php
Smoke Loader
23bef893e3af7cb49dc5ae0a14452ed781f841db7397dc3ebb689291fd701b6b
Smoke Loader C2s
dkajsdjiqwdwnfj[.]info
2831ujedkdajsdj[.]info
928eijdksasnfss[.]info
dkajsdjiqwdwnfj[.]info
2831ujedkdajsdj[.]info
928eijdksasnfss[.]info
Gates used in the malsmoke campaign
einlegesohle[.]com/indexx.php
adexhangetomatto[.]space
encelava[.]com/coexo.php
encelava[.]com/caac
uneaskie[.]com/ukexo.php
bumblizz[.]com/auexo.php
bumblizz[.]com/auflexexo.php
bumblizz[.]com/caexo.php
bumblizz[.]com/caflexexo.php
bumblizz[.]com/usexo.php
bumblizz[.]com/usflexexo.php
canadaversaliska[.]info/coflexexo.php
canadaversaliska[.]info/coflexo.php
canadaversaliska[.]info/ukflexexo.php
canadaversaliska[.]info/ukflexo.php
canadaversaliska[.]info/usflexexo.php
canadaversaliska[.]info/usflexo.php
krostaur[.]com/jpexo.php
krostaur[.]com/jpflexexo.php
krostaur[.]com/jpflexo.php
leiomity[.]com/ukexo.php
leiomity[.]com/ukflexexo.php
leiomity[.]com/usexo.php
leiomity[.]com/usflexexo.php
surdised[.]com/coexo.php
surdised[.]com/usexo.php
Tweets referencing the malsmoke campaign
https://twitter[.]com/MBThreatIntel/status/1245791188281462784 https://twitter[.]com/FaLconIntel/status/1232475345023987713 https://twitter[.]com/nao_sec/status/1231149711517634560 https://twitter[.]com/tkanalyst/status/1229794466816389120 https://twitter[.]com/nao_sec/status/1209090544711815169
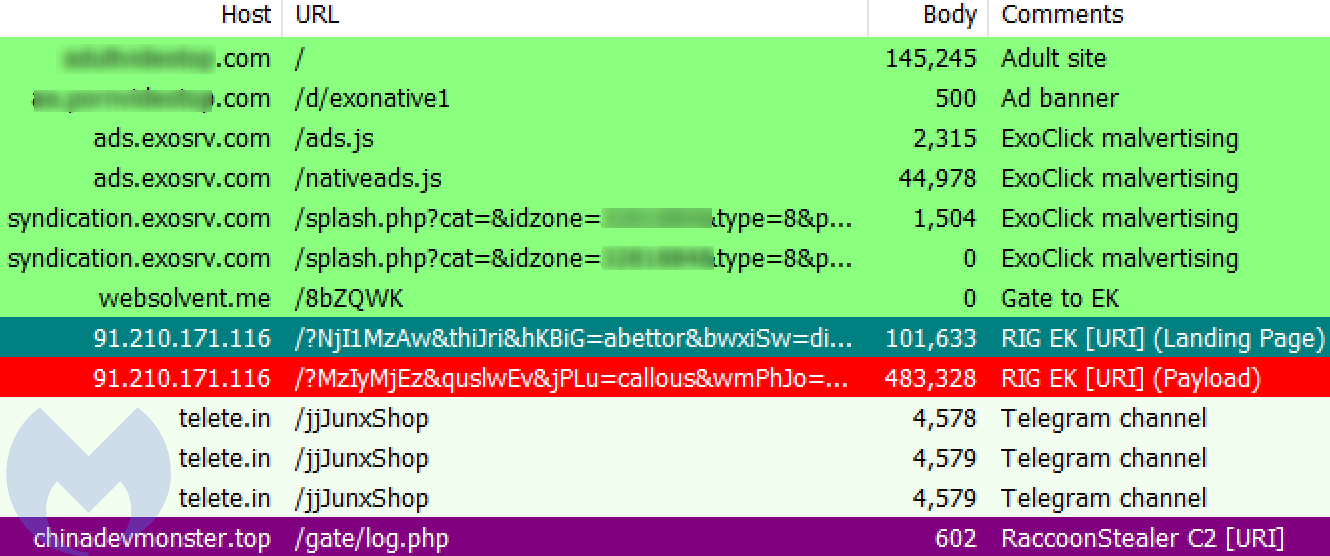
In this campaign, the crooks abused the popular ad network ExoClick by using different redirection pages. However, each time we were able to notify the ad network and get them shut down quickly.
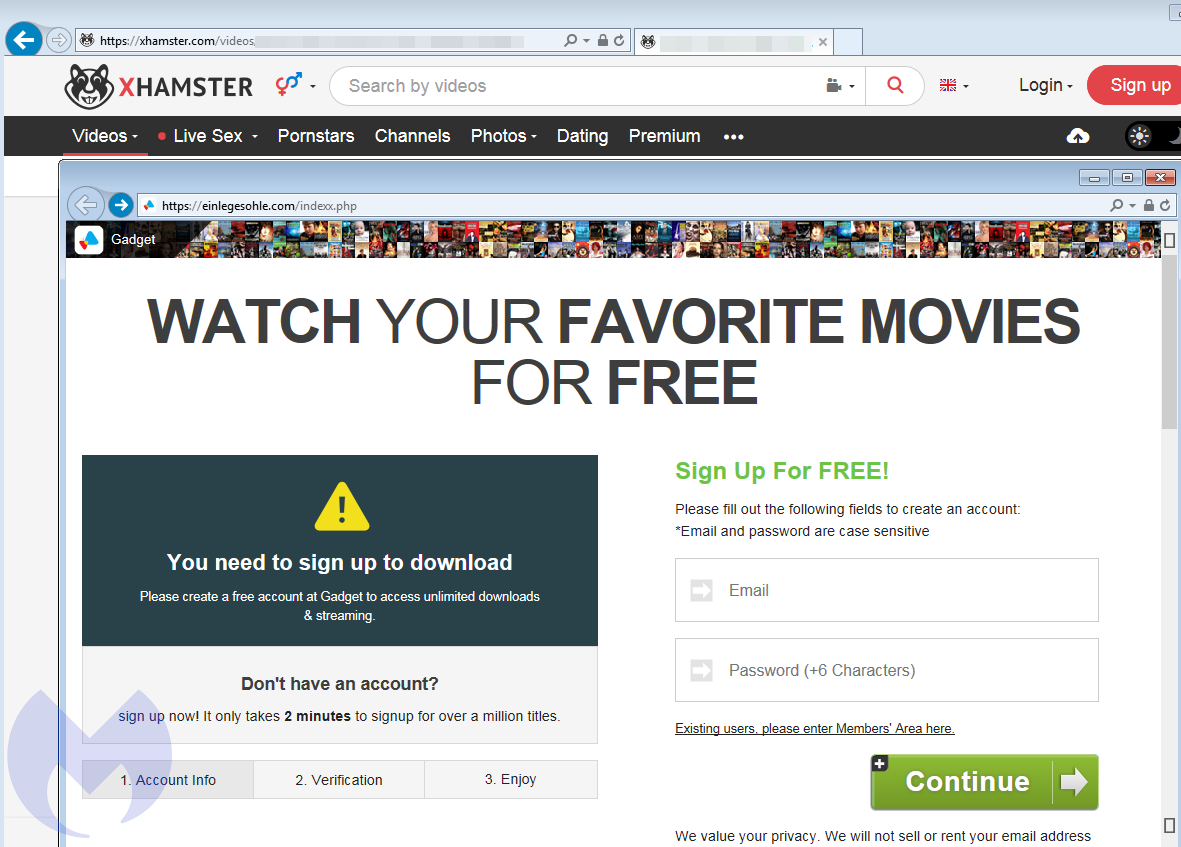
The first domain they used was inteca-deco[.]com, which was setup as a web design agency but visibly a decoy page to the trained eye.

Simple server-side cloaking performs the redirect to a Fallout exploit kit landing page which attempts to exploit CVE-2019-0752 (Internet Explorer) and CVE-2018-15982 (Flash Player) before dropping the Raccoon Stealer.

About 10 days later, another domain, websolvent[.]me, became active but used a different redirection technique, a 302 redirect, also known as 302 cushioning. This time we see the RIG exploit kit which also delivers Raccoon Stealer.

Beyond a common payload, those two domains are also related. A RiskIQ crawl confirms a relationship between these 2 domains where the parent host was caught doing a meta refresh redirect to the child:

Malvertising on top adult site gets maximum reach
The second malvertiser (‘malsmoke’) is one that we have tracked diligently over the past several months and whose end payload is often the Smoke Loader malware. It is by far the most daring and successful one in that it goes after larger publishers and a variety of ad networks. However, up until now we had only seen them on publishers from the adult industry that are still relatively small in scale.
In this instance, the threat actor was able to abuse the Traffic Stars ad network and place their malicious ad on xhamster[.]com, a site with just over 1.06 billion monthly visits according to SimilarWeb.com.
The gates used by this group also use a decoy site and over time they have registered domains mocking ad networks and cloud providers.

The redirection mechanism is more sophisticated than those used in other malvertising campaigns. There is some client-side fingerprinting and connectivity checks to avoid VPNs and proxies, only targeting legitimate IP addresses.

Interestingly, this Smoke Loader instance also downloads Raccoon Stealer and ZLoader.
Malsmoke is probably the most persistent malvertising campaigns we have seen this year. Unlike other threat actors, this group has shown that it can rapidly switch ad networks to keep their business uninterrupted.

Still using Internet Explorer?
Threat actors still leveraging exploit kits to deliver malware is one thing, but end users browsing with Internet Explorer is another. Despite recommendations from Microsoft and security professionals, we can only witness that there are still a number of users (consumer and enterprise) worldwide that have yet to migrate to a modern and fully supported browser.
As a result, exploit kit authors are squeezing the last bit of juice from vulnerabilities in Internet Explorer and Flash Player (due to retire for good next year).
Malwarebytes customers have long been protected from malvertising and exploit kits. We continue to track and report the campaigns we run into to help do our part in keeping the Internet safer.
Indicators of compromise
Gates used in malvertising campaign pushing Raccoon Stealer
intica-deco[.]com
websolvent[.]me
Raccoon Stealer
b289155154642ba8e9b032490a20c4a2c09b925e5b85dda11fc85d377baa6a6c
f319264b36cdf0daeb6174a43aaf4a6684775e6f0fb69aaf2d7dc051a593de93
Raccoon Stealer C2s
34.105.147[.]92/gate/log.php
chinadevmonster[.]top/gate/log.php
Smoke Loader
23bef893e3af7cb49dc5ae0a14452ed781f841db7397dc3ebb689291fd701b6b
Smoke Loader C2s
dkajsdjiqwdwnfj[.]info
2831ujedkdajsdj[.]info
928eijdksasnfss[.]info
dkajsdjiqwdwnfj[.]info
2831ujedkdajsdj[.]info
928eijdksasnfss[.]info
Gates used in the malsmoke campaign
einlegesohle[.]com/indexx.php
adexhangetomatto[.]space
encelava[.]com/coexo.php
encelava[.]com/caac
uneaskie[.]com/ukexo.php
bumblizz[.]com/auexo.php
bumblizz[.]com/auflexexo.php
bumblizz[.]com/caexo.php
bumblizz[.]com/caflexexo.php
bumblizz[.]com/usexo.php
bumblizz[.]com/usflexexo.php
canadaversaliska[.]info/coflexexo.php
canadaversaliska[.]info/coflexo.php
canadaversaliska[.]info/ukflexexo.php
canadaversaliska[.]info/ukflexo.php
canadaversaliska[.]info/usflexexo.php
canadaversaliska[.]info/usflexo.php
krostaur[.]com/jpexo.php
krostaur[.]com/jpflexexo.php
krostaur[.]com/jpflexo.php
leiomity[.]com/ukexo.php
leiomity[.]com/ukflexexo.php
leiomity[.]com/usexo.php
leiomity[.]com/usflexexo.php
surdised[.]com/coexo.php
surdised[.]com/usexo.php
Tweets referencing the malsmoke campaign
https://twitter[.]com/MBThreatIntel/status/1245791188281462784 https://twitter[.]com/FaLconIntel/status/1232475345023987713 https://twitter[.]com/nao_sec/status/1231149711517634560 https://twitter[.]com/tkanalyst/status/1229794466816389120 https://twitter[.]com/nao_sec/status/1209090544711815169
Malvertising campaigns leading to exploit kits are nowhere near as common these days. Indeed, a number of threat actors have moved on to other delivery methods instead of relying on drive-by downloads.
However, occasionally we see spikes in activity that are noticeable enough that they highlight a successful run. In late August, we started seeing a Fallout exploit kit campaign distributing the Raccoon Stealer via high-traffic adult sites. Shortly after we reported it to the ad network, the same threat actor came back again using the RIG exploit kit instead.
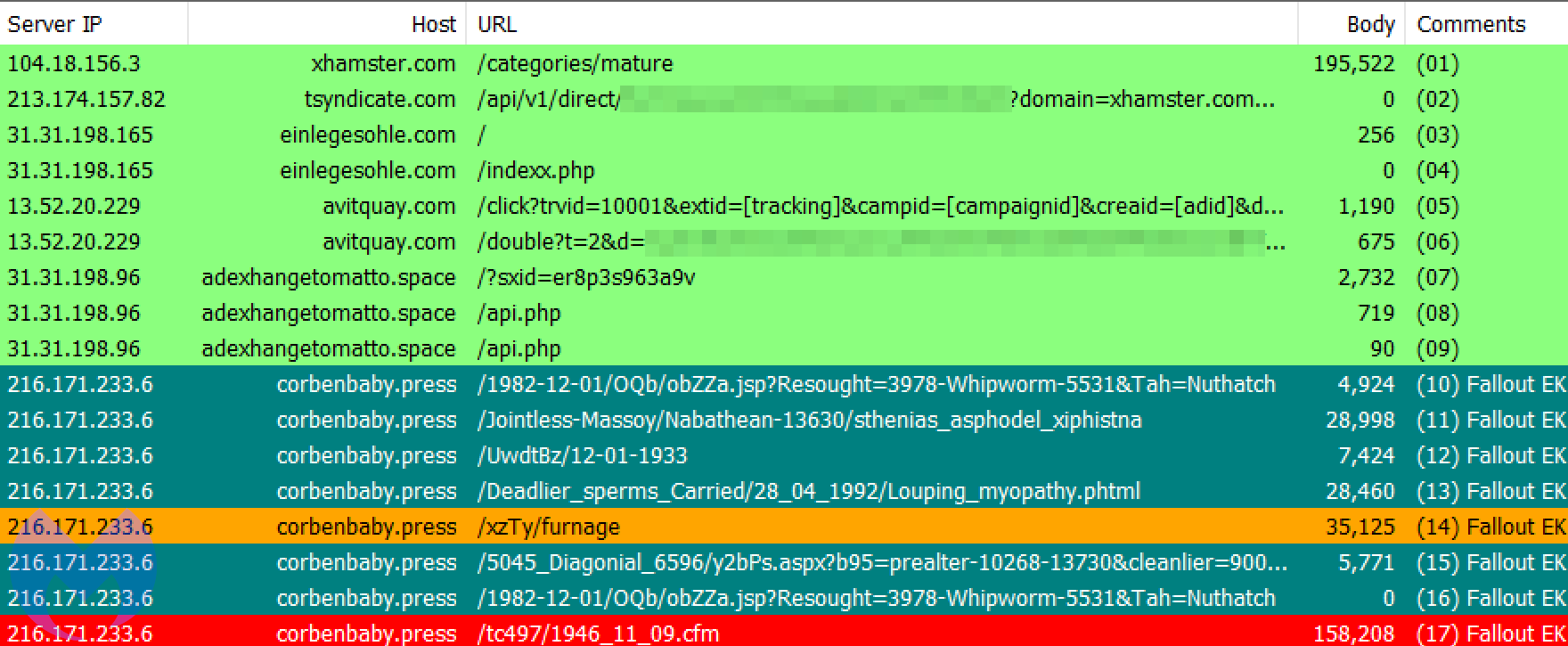
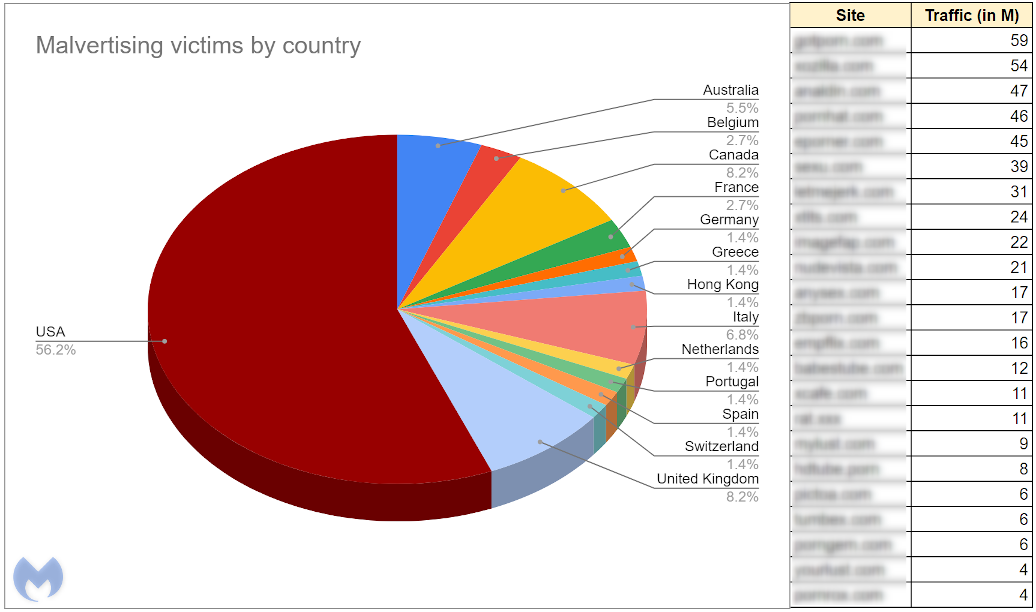
Then we saw possibly the largest campaign to date on top site xhamster[.]com from a malvertiser we have tracked for well over a year. This threat actor has managed to abuse practically all adult ad networks but this may be the first time they hit a top publisher.
Malvertising on popular ad network
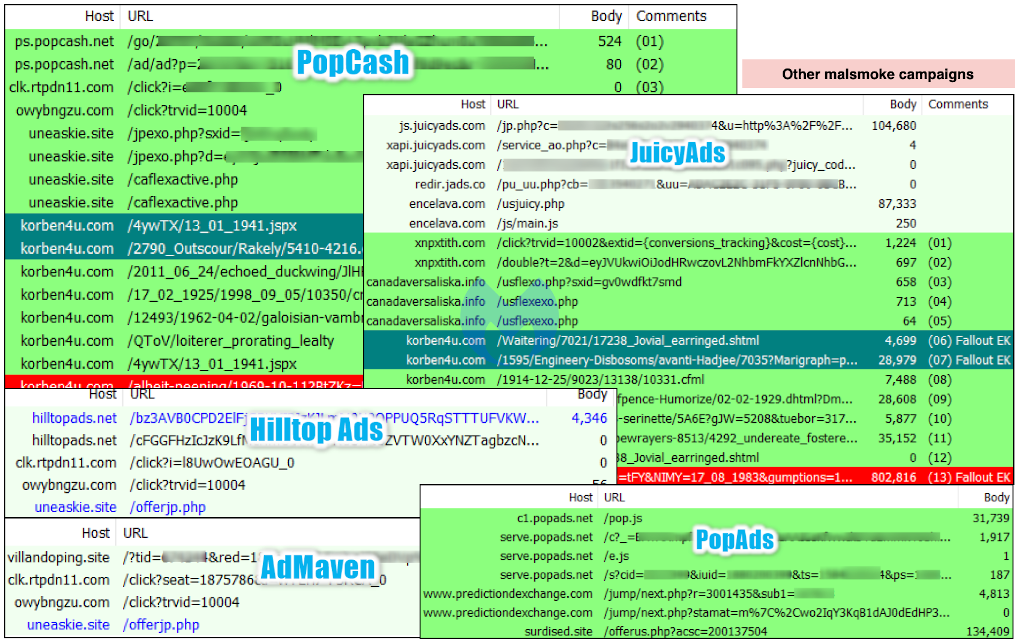
The first malicious advertiser we observed was able to bid for ads on a number of adult sites by targeting users running Internet Explorer without any particular geolocation restriction, although the majority of victims were in the US.

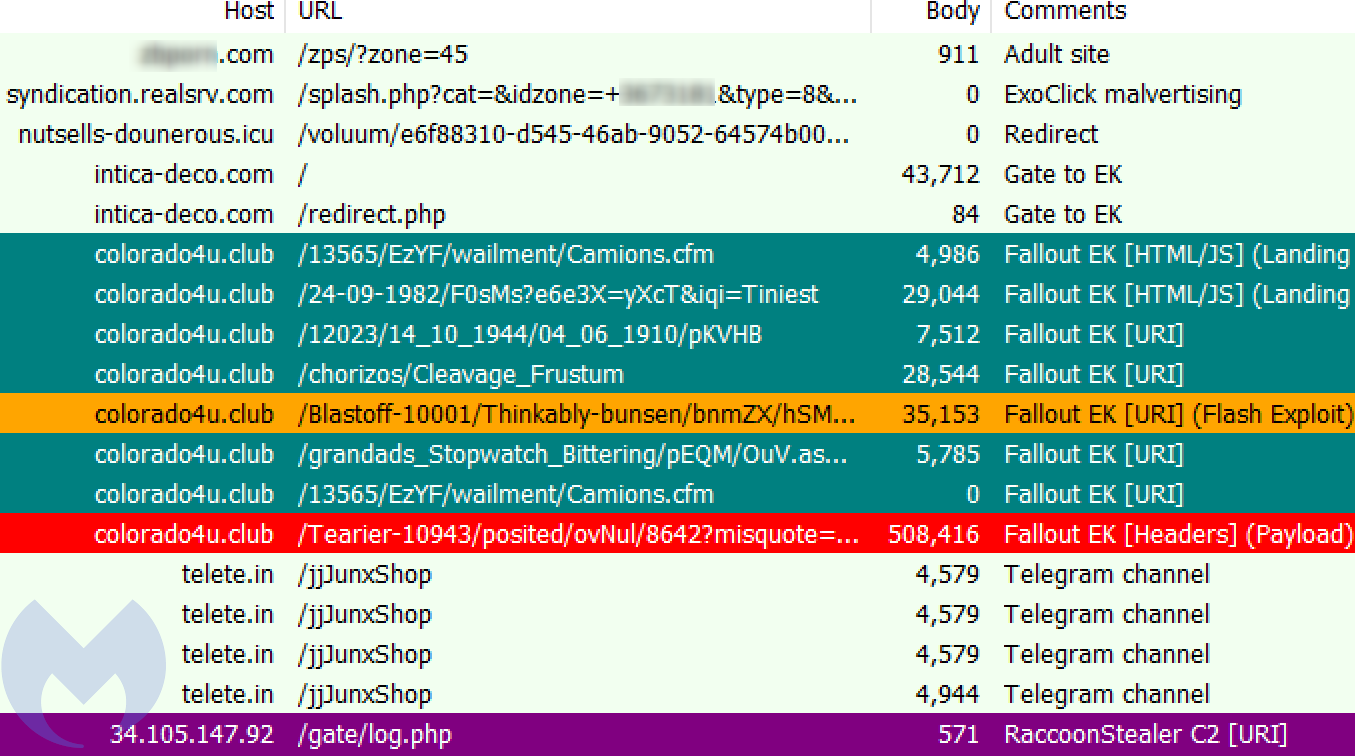
In this campaign, the crooks abused the popular ad network ExoClick by using different redirection pages. However, each time we were able to notify the ad network and get them shut down quickly.
The first domain they used was inteca-deco[.]com, which was setup as a web design agency but visibly a decoy page to the trained eye.

Simple server-side cloaking performs the redirect to a Fallout exploit kit landing page which attempts to exploit CVE-2019-0752 (Internet Explorer) and CVE-2018-15982 (Flash Player) before dropping the Raccoon Stealer.

About 10 days later, another domain, websolvent[.]me, became active but used a different redirection technique, a 302 redirect, also known as 302 cushioning. This time we see the RIG exploit kit which also delivers Raccoon Stealer.

Beyond a common payload, those two domains are also related. A RiskIQ crawl confirms a relationship between these 2 domains where the parent host was caught doing a meta refresh redirect to the child:

Malvertising on top adult site gets maximum reach
The second malvertiser (‘malsmoke’) is one that we have tracked diligently over the past several months and whose end payload is often the Smoke Loader malware. It is by far the most daring and successful one in that it goes after larger publishers and a variety of ad networks. However, up until now we had only seen them on publishers from the adult industry that are still relatively small in scale.
In this instance, the threat actor was able to abuse the Traffic Stars ad network and place their malicious ad on xhamster[.]com, a site with just over 1.06 billion monthly visits according to SimilarWeb.com.
The gates used by this group also use a decoy site and over time they have registered domains mocking ad networks and cloud providers.

The redirection mechanism is more sophisticated than those used in other malvertising campaigns. There is some client-side fingerprinting and connectivity checks to avoid VPNs and proxies, only targeting legitimate IP addresses.

Interestingly, this Smoke Loader instance also downloads Raccoon Stealer and ZLoader.
Malsmoke is probably the most persistent malvertising campaigns we have seen this year. Unlike other threat actors, this group has shown that it can rapidly switch ad networks to keep their business uninterrupted.

Still using Internet Explorer?
Threat actors still leveraging exploit kits to deliver malware is one thing, but end users browsing with Internet Explorer is another. Despite recommendations from Microsoft and security professionals, we can only witness that there are still a number of users (consumer and enterprise) worldwide that have yet to migrate to a modern and fully supported browser.
As a result, exploit kit authors are squeezing the last bit of juice from vulnerabilities in Internet Explorer and Flash Player (due to retire for good next year).
Malwarebytes customers have long been protected from malvertising and exploit kits. We continue to track and report the campaigns we run into to help do our part in keeping the Internet safer.
Indicators of compromise
Gates used in malvertising campaign pushing Raccoon Stealer
intica-deco[.]com
websolvent[.]me
Raccoon Stealer
b289155154642ba8e9b032490a20c4a2c09b925e5b85dda11fc85d377baa6a6c
f319264b36cdf0daeb6174a43aaf4a6684775e6f0fb69aaf2d7dc051a593de93
Raccoon Stealer C2s
34.105.147[.]92/gate/log.php
chinadevmonster[.]top/gate/log.php
Smoke Loader
23bef893e3af7cb49dc5ae0a14452ed781f841db7397dc3ebb689291fd701b6b
Smoke Loader C2s
dkajsdjiqwdwnfj[.]info
2831ujedkdajsdj[.]info
928eijdksasnfss[.]info
dkajsdjiqwdwnfj[.]info
2831ujedkdajsdj[.]info
928eijdksasnfss[.]info
Gates used in the malsmoke campaign
einlegesohle[.]com/indexx.php
adexhangetomatto[.]space
encelava[.]com/coexo.php
encelava[.]com/caac
uneaskie[.]com/ukexo.php
bumblizz[.]com/auexo.php
bumblizz[.]com/auflexexo.php
bumblizz[.]com/caexo.php
bumblizz[.]com/caflexexo.php
bumblizz[.]com/usexo.php
bumblizz[.]com/usflexexo.php
canadaversaliska[.]info/coflexexo.php
canadaversaliska[.]info/coflexo.php
canadaversaliska[.]info/ukflexexo.php
canadaversaliska[.]info/ukflexo.php
canadaversaliska[.]info/usflexexo.php
canadaversaliska[.]info/usflexo.php
krostaur[.]com/jpexo.php
krostaur[.]com/jpflexexo.php
krostaur[.]com/jpflexo.php
leiomity[.]com/ukexo.php
leiomity[.]com/ukflexexo.php
leiomity[.]com/usexo.php
leiomity[.]com/usflexexo.php
surdised[.]com/coexo.php
surdised[.]com/usexo.php
Tweets referencing the malsmoke campaign
https://twitter[.]com/MBThreatIntel/status/1245791188281462784 https://twitter[.]com/FaLconIntel/status/1232475345023987713 https://twitter[.]com/nao_sec/status/1231149711517634560 https://twitter[.]com/tkanalyst/status/1229794466816389120 https://twitter[.]com/nao_sec/status/1209090544711815169










