Researchers at Netlab have discovered a new botnet that re-uses the Mirai framework to pull vulnerable Android devices into DDoS attacks.
The new botnet, which is called Matryosh, is named after the Russian nesting dolls because the encryption algorithm it uses, and the process of obtaining command and control (C2) are nested in layers. The botnet supports DDoS attacks using tcpraw, icmpecho, and udpplain attacks.
How does Matryosh spread?
Like other botnets before it, Matryosh propagates via Android Debug Bridge (ADB), a diagnostic and debugging interface that uses port 5555. While ADB has a genuine use for developers, an internet-facing ADB also opens the way for remote attacks.
Unfortunately, some vendors are shipping Android devices with port 5555 open. This allows developers to communicate with devices remotely in order to control a device and execute commands, which is generally used for diagnostic and debugging purposes. But it also creates a backdoor for any other attackers that connect to this port.
Android Debug Bridge
ADB is a versatile command-line tool that lets you communicate with an Android device and facilitates a variety of device actions, such as installing and debugging apps. It also provides access to a shell that you can use to run a variety of commands on a device.
Although Android is commonly known as a popular operating system for phones, it is also used as an operating system for any number of internet-connected “Things”, such as exercise bikes and television sets.
To make the potential disaster complete, ADB does not require authentication, meaning anybody can connect to a device running ADB to execute commands. In short, with ADB enabled, anybody can remotely connect to the device as root.
How does Matryosh work?
Matryosh is special in that it uses the encrypted Tor network to mask its malicious traffic. When Matryosh runs on an infected device, it decrypts a remote hostname and uses DNS TXT requests to obtain the Tor C2 server and proxy details. After that, Matryosh uses those details to establish a connection with C2 server, via the Tor proxy, to get its commands.
To perform the DDoS attacks the botnet supports tcpraw, icmpecho, and udpplain attacks. This means it is able to launch DDoS attacks via protocols like TCP, ICMP, and UDP.
How to disable ADB
Although ADB is turned off by default on most Android smartphones and tablets, some vendors do ship their devices with ADB enabled.
- Android users: It is hard to provide clear instructions that work for every device, but generally speaking you need to disable the “Developer options” of the device. In the Malwarebytes for Android client there is a Security audit feature that indicates if Developer mode is enabled, where ADB is located, but does not specifically point out that ADB is on or off. If Developer mode is enabled the audit will point that out and a user can access Developer mode by tapping on Development mode in the audit results, which will be displayed in yellow. When Developer mode is disabled, ADB should be disabled as well.
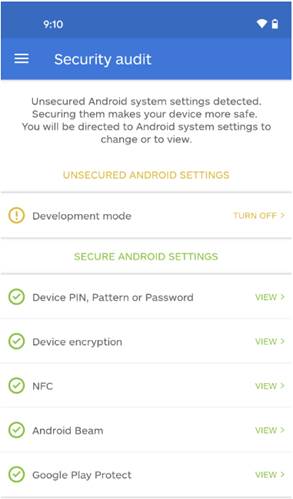
- Enterprises should scan their internal and external networks for port 5555 to see if any devices are listening on that port, which could be an indication that devices are open to receive ADB commands. It also wouldn’t hurt to read our blogpost DDoS attacks are growing: What can businesses do?
- Vendors need to stop shipping products with Android Debug Bridge enabled over a network, especially of those devices are designed to be connected to the internet.
Keep your devices out of the botnets!











