Fake advertising infrastructure
Because this is a long running campaign, the infrastructure is fairly large but tends to reuse the same naming convention for domains. The graph below only shows the domains created to abuse the TrafficJunky ad platform. It does not include domains used for the browlock itself.
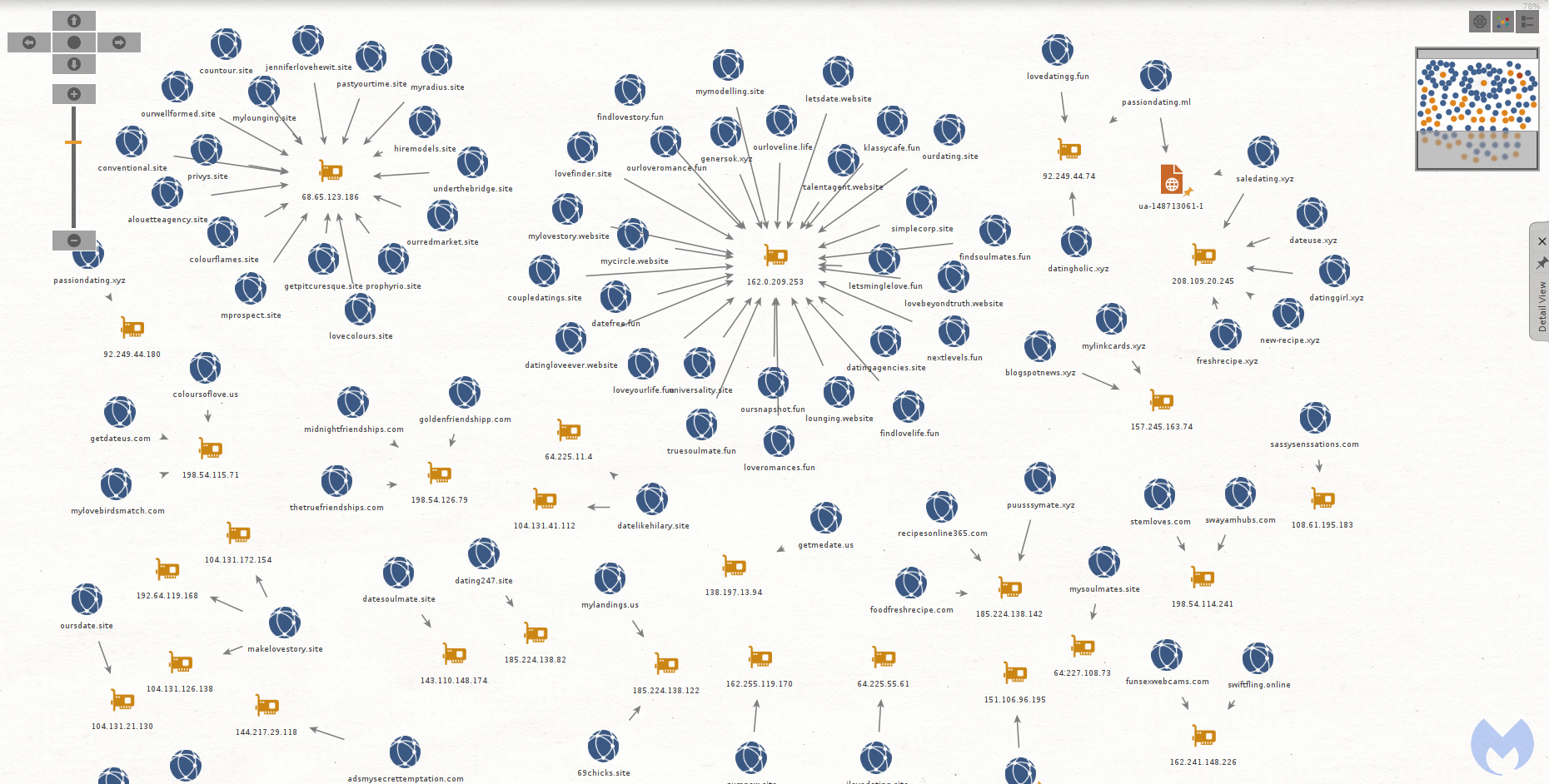
There was a domain (recipesonline365[.]com) whose naming convention differed from the other dating sites. In fact it is the only one with a non-adult theme.
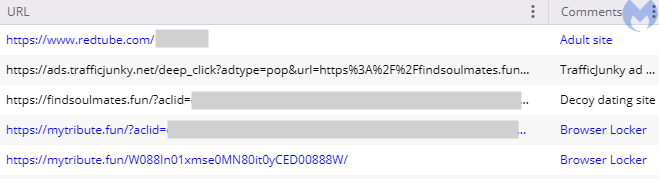
(1) youporn[.]com/_xa/ads?zone_id=[removed] (2) ads.trafficjunky[.]net/deep_click?adtype=pop&url=https%3A%2F%2Frecipesonline365[.]com (3) recipesonline365[.]com/?aclid=[removed] (4) oopi3.azurewebsites[.]net/Winhelpxcode161616winHelpSecurity0nlineCH007
Back in June 2019, we had identified an ad campaign targeting recipe keywords. The threat actor was using decoy recipe and food sites to lure victims via web searches. Those sites performed the same redirect mechanism as the decoy dating sites, and most of the time lead to a browlock hosted on Azure as well.
There are a number of other parallels between that campaign and the adult one such as the predominant use of NameCheap hosting and a large volume of decoy sites. For this reason we believe this is likely the same threat actor.
Protection
Browser lockers are not dangerous in and out of themselves. They are simply a fake warning which may be disrupting and annoying but one that does not indicate a computer problem.
In recent years they have become very common and affect all browsers, even mobile ones. In the past, we have seen browser lockers that were effectively giving the impression the machine was locked due to how they abused the user interface. As of know, most of them can be closed normally without requiring the use of special commands.
Malwarebytes users were already protected against this campaign. Our Browser Guard extension can detect and stop browser lockers using heuristic techniques that do not require to use a blacklist of known domain names or IP addresses.
Indicators of Compromise
The list of IOCs can be downloaded from our GitHub here.
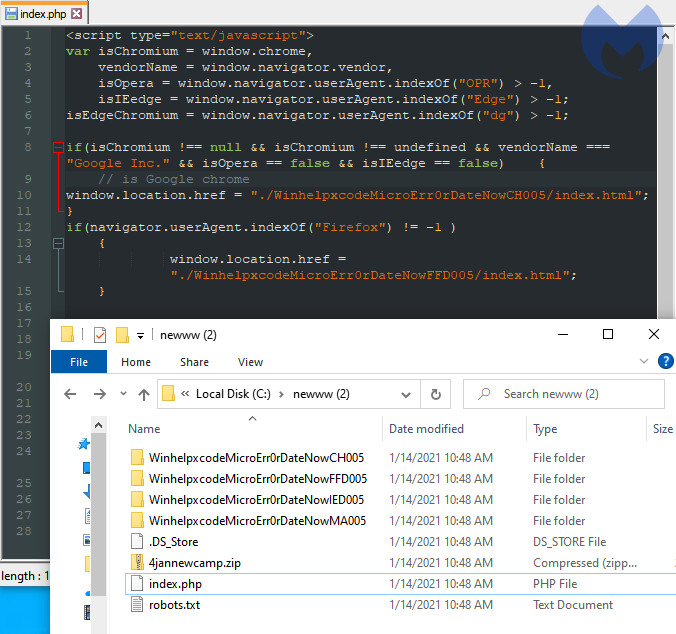
While browsing one of the many decoy sites, we found the HTML source code in an exposed directory showing a few additional variations of the browser locker:

Fake advertising infrastructure
Because this is a long running campaign, the infrastructure is fairly large but tends to reuse the same naming convention for domains. The graph below only shows the domains created to abuse the TrafficJunky ad platform. It does not include domains used for the browlock itself.

There was a domain (recipesonline365[.]com) whose naming convention differed from the other dating sites. In fact it is the only one with a non-adult theme.
(1) youporn[.]com/_xa/ads?zone_id=[removed] (2) ads.trafficjunky[.]net/deep_click?adtype=pop&url=https%3A%2F%2Frecipesonline365[.]com (3) recipesonline365[.]com/?aclid=[removed] (4) oopi3.azurewebsites[.]net/Winhelpxcode161616winHelpSecurity0nlineCH007
Back in June 2019, we had identified an ad campaign targeting recipe keywords. The threat actor was using decoy recipe and food sites to lure victims via web searches. Those sites performed the same redirect mechanism as the decoy dating sites, and most of the time lead to a browlock hosted on Azure as well.
There are a number of other parallels between that campaign and the adult one such as the predominant use of NameCheap hosting and a large volume of decoy sites. For this reason we believe this is likely the same threat actor.
Protection
Browser lockers are not dangerous in and out of themselves. They are simply a fake warning which may be disrupting and annoying but one that does not indicate a computer problem.
In recent years they have become very common and affect all browsers, even mobile ones. In the past, we have seen browser lockers that were effectively giving the impression the machine was locked due to how they abused the user interface. As of know, most of them can be closed normally without requiring the use of special commands.
Malwarebytes users were already protected against this campaign. Our Browser Guard extension can detect and stop browser lockers using heuristic techniques that do not require to use a blacklist of known domain names or IP addresses.
Indicators of Compromise
The list of IOCs can be downloaded from our GitHub here.

While browsing one of the many decoy sites, we found the HTML source code in an exposed directory showing a few additional variations of the browser locker:

Fake advertising infrastructure
Because this is a long running campaign, the infrastructure is fairly large but tends to reuse the same naming convention for domains. The graph below only shows the domains created to abuse the TrafficJunky ad platform. It does not include domains used for the browlock itself.

There was a domain (recipesonline365[.]com) whose naming convention differed from the other dating sites. In fact it is the only one with a non-adult theme.
(1) youporn[.]com/_xa/ads?zone_id=[removed] (2) ads.trafficjunky[.]net/deep_click?adtype=pop&url=https%3A%2F%2Frecipesonline365[.]com (3) recipesonline365[.]com/?aclid=[removed] (4) oopi3.azurewebsites[.]net/Winhelpxcode161616winHelpSecurity0nlineCH007
Back in June 2019, we had identified an ad campaign targeting recipe keywords. The threat actor was using decoy recipe and food sites to lure victims via web searches. Those sites performed the same redirect mechanism as the decoy dating sites, and most of the time lead to a browlock hosted on Azure as well.
There are a number of other parallels between that campaign and the adult one such as the predominant use of NameCheap hosting and a large volume of decoy sites. For this reason we believe this is likely the same threat actor.
Protection
Browser lockers are not dangerous in and out of themselves. They are simply a fake warning which may be disrupting and annoying but one that does not indicate a computer problem.
In recent years they have become very common and affect all browsers, even mobile ones. In the past, we have seen browser lockers that were effectively giving the impression the machine was locked due to how they abused the user interface. As of know, most of them can be closed normally without requiring the use of special commands.
Malwarebytes users were already protected against this campaign. Our Browser Guard extension can detect and stop browser lockers using heuristic techniques that do not require to use a blacklist of known domain names or IP addresses.
Indicators of Compromise
The list of IOCs can be downloaded from our GitHub here.
If you were to visit one those sites directly, you may not see anything else of interest, at least nothing malicious in nature. However, the fraudulent advertiser can easily redirect traffic based on factors such as IP geolocation, referer and other artifacts.
In all, we detected close to 100 decoy domain names set up as “advertising landing pages” used to redirect victims to browser locker scams. Even though the templates are half finished, the threat actor is spending time creating a large inventory they can cycle through in their redirects towards browser lockers.
Browser locker
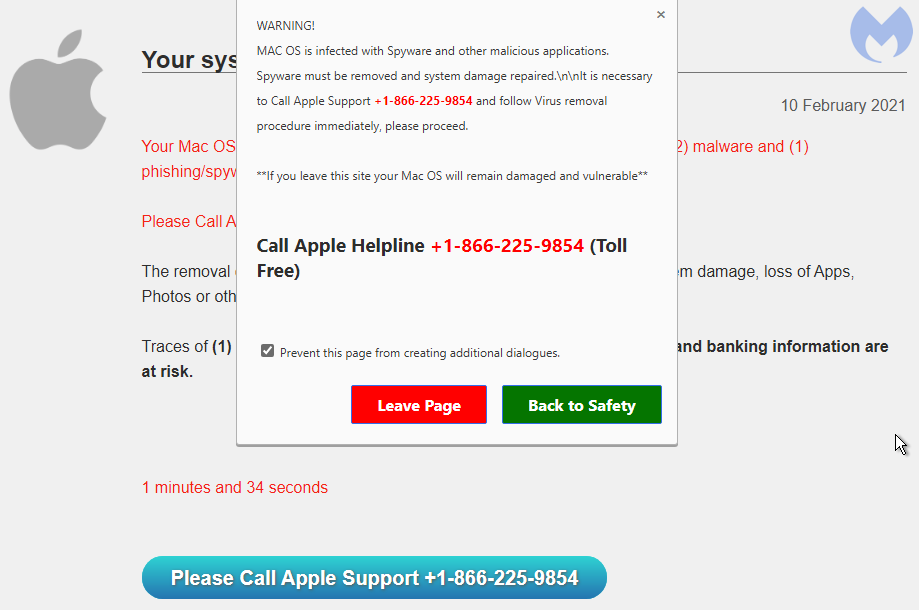
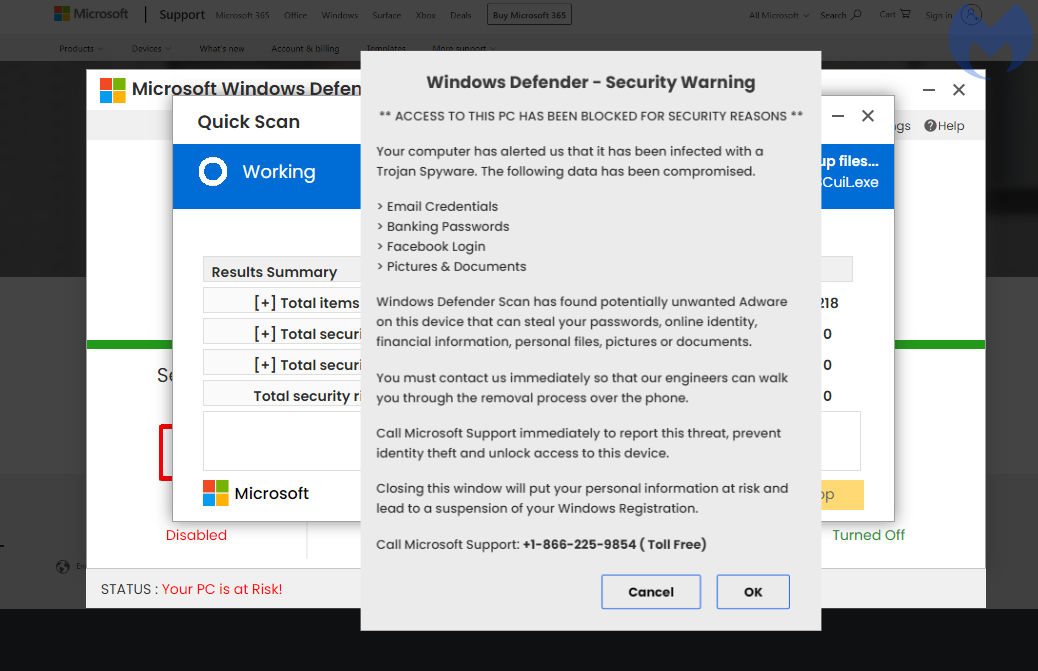
The browser locker is using a common theme of a fake Microsoft Windows Defender scanner. There is some browser profiling to serve the right template based on whether the user is on Windows or Mac.


While browsing one of the many decoy sites, we found the HTML source code in an exposed directory showing a few additional variations of the browser locker:

Fake advertising infrastructure
Because this is a long running campaign, the infrastructure is fairly large but tends to reuse the same naming convention for domains. The graph below only shows the domains created to abuse the TrafficJunky ad platform. It does not include domains used for the browlock itself.

There was a domain (recipesonline365[.]com) whose naming convention differed from the other dating sites. In fact it is the only one with a non-adult theme.
(1) youporn[.]com/_xa/ads?zone_id=[removed] (2) ads.trafficjunky[.]net/deep_click?adtype=pop&url=https%3A%2F%2Frecipesonline365[.]com (3) recipesonline365[.]com/?aclid=[removed] (4) oopi3.azurewebsites[.]net/Winhelpxcode161616winHelpSecurity0nlineCH007
Back in June 2019, we had identified an ad campaign targeting recipe keywords. The threat actor was using decoy recipe and food sites to lure victims via web searches. Those sites performed the same redirect mechanism as the decoy dating sites, and most of the time lead to a browlock hosted on Azure as well.
There are a number of other parallels between that campaign and the adult one such as the predominant use of NameCheap hosting and a large volume of decoy sites. For this reason we believe this is likely the same threat actor.
Protection
Browser lockers are not dangerous in and out of themselves. They are simply a fake warning which may be disrupting and annoying but one that does not indicate a computer problem.
In recent years they have become very common and affect all browsers, even mobile ones. In the past, we have seen browser lockers that were effectively giving the impression the machine was locked due to how they abused the user interface. As of know, most of them can be closed normally without requiring the use of special commands.
Malwarebytes users were already protected against this campaign. Our Browser Guard extension can detect and stop browser lockers using heuristic techniques that do not require to use a blacklist of known domain names or IP addresses.
Indicators of Compromise
The list of IOCs can be downloaded from our GitHub here.
What was clever is that the threat actor didn’t seem to set up an actual site for that fake domain, but instead redirected all traffic to the real one if the visitor did not match the parameters from their malvertising campaign.
However, the malvertising chain shows that they leveraged that domain to perform conditional redirects, such as the one seen below:
(1) pornhub[.]com/_xa/ads?zone_id=[removed] (2) ads.trafficjunky[.]net/click?url=https%3A%2F%2Fsassysenssations[.]com% (3) sassysenssations[.]com/track.php?CampaignID=[removed]&Sitename=Pornhub (4) errorhelpline24x7msofficialsoftwareerrorcodex12[.]monster
Later on, it appears the threat actor started diversifying their scheme by creating a number of fake dating sites to use as redirects in addition to using the sassysenssations identity.
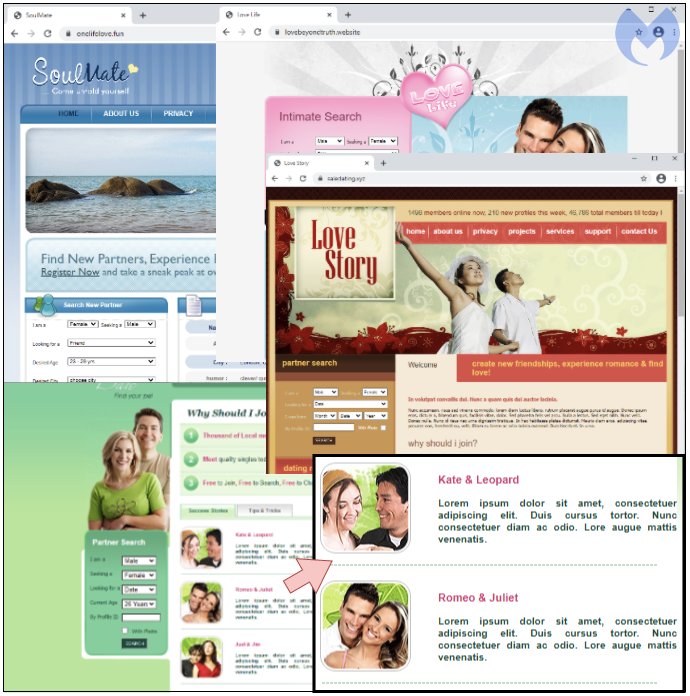
Fake dating sites
The malicious advertiser is using a model that has been tried before and consists of setting up fake identities in order to gain access to the ad platform. In this instance, we cataloged dating and romance sites. However, the majority of them did not look authentic or functional and even still had the ‘Lorem ipsum’ text filler.

If you were to visit one those sites directly, you may not see anything else of interest, at least nothing malicious in nature. However, the fraudulent advertiser can easily redirect traffic based on factors such as IP geolocation, referer and other artifacts.
In all, we detected close to 100 decoy domain names set up as “advertising landing pages” used to redirect victims to browser locker scams. Even though the templates are half finished, the threat actor is spending time creating a large inventory they can cycle through in their redirects towards browser lockers.
Browser locker
The browser locker is using a common theme of a fake Microsoft Windows Defender scanner. There is some browser profiling to serve the right template based on whether the user is on Windows or Mac.


While browsing one of the many decoy sites, we found the HTML source code in an exposed directory showing a few additional variations of the browser locker:

Fake advertising infrastructure
Because this is a long running campaign, the infrastructure is fairly large but tends to reuse the same naming convention for domains. The graph below only shows the domains created to abuse the TrafficJunky ad platform. It does not include domains used for the browlock itself.

There was a domain (recipesonline365[.]com) whose naming convention differed from the other dating sites. In fact it is the only one with a non-adult theme.
(1) youporn[.]com/_xa/ads?zone_id=[removed] (2) ads.trafficjunky[.]net/deep_click?adtype=pop&url=https%3A%2F%2Frecipesonline365[.]com (3) recipesonline365[.]com/?aclid=[removed] (4) oopi3.azurewebsites[.]net/Winhelpxcode161616winHelpSecurity0nlineCH007
Back in June 2019, we had identified an ad campaign targeting recipe keywords. The threat actor was using decoy recipe and food sites to lure victims via web searches. Those sites performed the same redirect mechanism as the decoy dating sites, and most of the time lead to a browlock hosted on Azure as well.
There are a number of other parallels between that campaign and the adult one such as the predominant use of NameCheap hosting and a large volume of decoy sites. For this reason we believe this is likely the same threat actor.
Protection
Browser lockers are not dangerous in and out of themselves. They are simply a fake warning which may be disrupting and annoying but one that does not indicate a computer problem.
In recent years they have become very common and affect all browsers, even mobile ones. In the past, we have seen browser lockers that were effectively giving the impression the machine was locked due to how they abused the user interface. As of know, most of them can be closed normally without requiring the use of special commands.
Malwarebytes users were already protected against this campaign. Our Browser Guard extension can detect and stop browser lockers using heuristic techniques that do not require to use a blacklist of known domain names or IP addresses.
Indicators of Compromise
The list of IOCs can be downloaded from our GitHub here.
A key part of this malvertising chain is the use of many different fake dating portals that are hiding the redirection mechanism for the browser locker.
Beginnings
This browser locker campaign started well before showing up on PornHub[.]com and went undetected for a long time perhaps due to a clever typosquatting trick. In fact, we were fooled ourselves for a while before seeing what is obvious in hindsight.
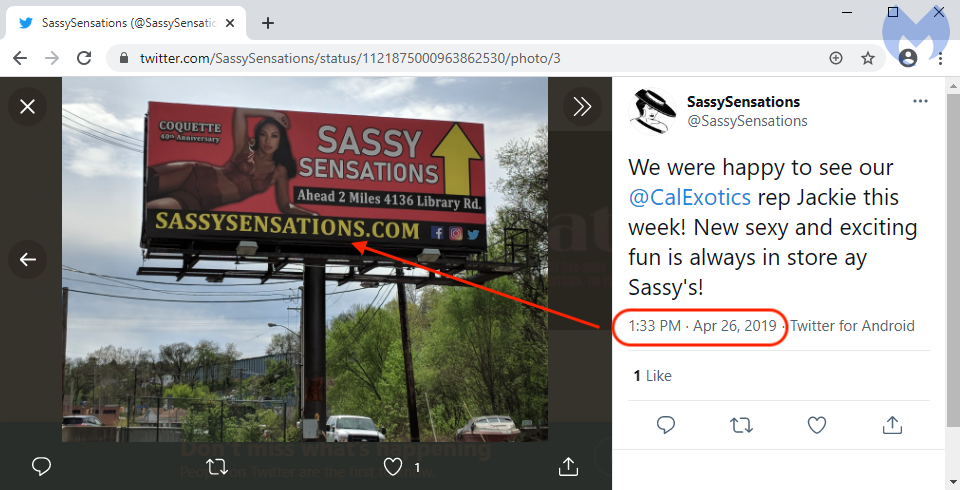
On May 21 2020, the threat actor registered the domain name sassysenssations[.]com which contains a voluntary typo (two ‘s’) to mimic sassysensations[.]com which belongs to a legitimate business.
The real domain was registered in 2014 and we even found a billboard advertisement for it tweeted out on April 26 2019, long before the scammers had registered their copycat domain.

What was clever is that the threat actor didn’t seem to set up an actual site for that fake domain, but instead redirected all traffic to the real one if the visitor did not match the parameters from their malvertising campaign.
However, the malvertising chain shows that they leveraged that domain to perform conditional redirects, such as the one seen below:
(1) pornhub[.]com/_xa/ads?zone_id=[removed] (2) ads.trafficjunky[.]net/click?url=https%3A%2F%2Fsassysenssations[.]com% (3) sassysenssations[.]com/track.php?CampaignID=[removed]&Sitename=Pornhub (4) errorhelpline24x7msofficialsoftwareerrorcodex12[.]monster
Later on, it appears the threat actor started diversifying their scheme by creating a number of fake dating sites to use as redirects in addition to using the sassysenssations identity.
Fake dating sites
The malicious advertiser is using a model that has been tried before and consists of setting up fake identities in order to gain access to the ad platform. In this instance, we cataloged dating and romance sites. However, the majority of them did not look authentic or functional and even still had the ‘Lorem ipsum’ text filler.

If you were to visit one those sites directly, you may not see anything else of interest, at least nothing malicious in nature. However, the fraudulent advertiser can easily redirect traffic based on factors such as IP geolocation, referer and other artifacts.
In all, we detected close to 100 decoy domain names set up as “advertising landing pages” used to redirect victims to browser locker scams. Even though the templates are half finished, the threat actor is spending time creating a large inventory they can cycle through in their redirects towards browser lockers.
Browser locker
The browser locker is using a common theme of a fake Microsoft Windows Defender scanner. There is some browser profiling to serve the right template based on whether the user is on Windows or Mac.


While browsing one of the many decoy sites, we found the HTML source code in an exposed directory showing a few additional variations of the browser locker:

Fake advertising infrastructure
Because this is a long running campaign, the infrastructure is fairly large but tends to reuse the same naming convention for domains. The graph below only shows the domains created to abuse the TrafficJunky ad platform. It does not include domains used for the browlock itself.

There was a domain (recipesonline365[.]com) whose naming convention differed from the other dating sites. In fact it is the only one with a non-adult theme.
(1) youporn[.]com/_xa/ads?zone_id=[removed] (2) ads.trafficjunky[.]net/deep_click?adtype=pop&url=https%3A%2F%2Frecipesonline365[.]com (3) recipesonline365[.]com/?aclid=[removed] (4) oopi3.azurewebsites[.]net/Winhelpxcode161616winHelpSecurity0nlineCH007
Back in June 2019, we had identified an ad campaign targeting recipe keywords. The threat actor was using decoy recipe and food sites to lure victims via web searches. Those sites performed the same redirect mechanism as the decoy dating sites, and most of the time lead to a browlock hosted on Azure as well.
There are a number of other parallels between that campaign and the adult one such as the predominant use of NameCheap hosting and a large volume of decoy sites. For this reason we believe this is likely the same threat actor.
Protection
Browser lockers are not dangerous in and out of themselves. They are simply a fake warning which may be disrupting and annoying but one that does not indicate a computer problem.
In recent years they have become very common and affect all browsers, even mobile ones. In the past, we have seen browser lockers that were effectively giving the impression the machine was locked due to how they abused the user interface. As of know, most of them can be closed normally without requiring the use of special commands.
Malwarebytes users were already protected against this campaign. Our Browser Guard extension can detect and stop browser lockers using heuristic techniques that do not require to use a blacklist of known domain names or IP addresses.
Indicators of Compromise
The list of IOCs can be downloaded from our GitHub here.
This sequence of events can be summarized in the traffic capture below:

A key part of this malvertising chain is the use of many different fake dating portals that are hiding the redirection mechanism for the browser locker.
Beginnings
This browser locker campaign started well before showing up on PornHub[.]com and went undetected for a long time perhaps due to a clever typosquatting trick. In fact, we were fooled ourselves for a while before seeing what is obvious in hindsight.
On May 21 2020, the threat actor registered the domain name sassysenssations[.]com which contains a voluntary typo (two ‘s’) to mimic sassysensations[.]com which belongs to a legitimate business.
The real domain was registered in 2014 and we even found a billboard advertisement for it tweeted out on April 26 2019, long before the scammers had registered their copycat domain.

What was clever is that the threat actor didn’t seem to set up an actual site for that fake domain, but instead redirected all traffic to the real one if the visitor did not match the parameters from their malvertising campaign.
However, the malvertising chain shows that they leveraged that domain to perform conditional redirects, such as the one seen below:
(1) pornhub[.]com/_xa/ads?zone_id=[removed] (2) ads.trafficjunky[.]net/click?url=https%3A%2F%2Fsassysenssations[.]com% (3) sassysenssations[.]com/track.php?CampaignID=[removed]&Sitename=Pornhub (4) errorhelpline24x7msofficialsoftwareerrorcodex12[.]monster
Later on, it appears the threat actor started diversifying their scheme by creating a number of fake dating sites to use as redirects in addition to using the sassysenssations identity.
Fake dating sites
The malicious advertiser is using a model that has been tried before and consists of setting up fake identities in order to gain access to the ad platform. In this instance, we cataloged dating and romance sites. However, the majority of them did not look authentic or functional and even still had the ‘Lorem ipsum’ text filler.

If you were to visit one those sites directly, you may not see anything else of interest, at least nothing malicious in nature. However, the fraudulent advertiser can easily redirect traffic based on factors such as IP geolocation, referer and other artifacts.
In all, we detected close to 100 decoy domain names set up as “advertising landing pages” used to redirect victims to browser locker scams. Even though the templates are half finished, the threat actor is spending time creating a large inventory they can cycle through in their redirects towards browser lockers.
Browser locker
The browser locker is using a common theme of a fake Microsoft Windows Defender scanner. There is some browser profiling to serve the right template based on whether the user is on Windows or Mac.


While browsing one of the many decoy sites, we found the HTML source code in an exposed directory showing a few additional variations of the browser locker:

Fake advertising infrastructure
Because this is a long running campaign, the infrastructure is fairly large but tends to reuse the same naming convention for domains. The graph below only shows the domains created to abuse the TrafficJunky ad platform. It does not include domains used for the browlock itself.

There was a domain (recipesonline365[.]com) whose naming convention differed from the other dating sites. In fact it is the only one with a non-adult theme.
(1) youporn[.]com/_xa/ads?zone_id=[removed] (2) ads.trafficjunky[.]net/deep_click?adtype=pop&url=https%3A%2F%2Frecipesonline365[.]com (3) recipesonline365[.]com/?aclid=[removed] (4) oopi3.azurewebsites[.]net/Winhelpxcode161616winHelpSecurity0nlineCH007
Back in June 2019, we had identified an ad campaign targeting recipe keywords. The threat actor was using decoy recipe and food sites to lure victims via web searches. Those sites performed the same redirect mechanism as the decoy dating sites, and most of the time lead to a browlock hosted on Azure as well.
There are a number of other parallels between that campaign and the adult one such as the predominant use of NameCheap hosting and a large volume of decoy sites. For this reason we believe this is likely the same threat actor.
Protection
Browser lockers are not dangerous in and out of themselves. They are simply a fake warning which may be disrupting and annoying but one that does not indicate a computer problem.
In recent years they have become very common and affect all browsers, even mobile ones. In the past, we have seen browser lockers that were effectively giving the impression the machine was locked due to how they abused the user interface. As of know, most of them can be closed normally without requiring the use of special commands.
Malwarebytes users were already protected against this campaign. Our Browser Guard extension can detect and stop browser lockers using heuristic techniques that do not require to use a blacklist of known domain names or IP addresses.
Indicators of Compromise
The list of IOCs can be downloaded from our GitHub here.
Threat actors involved in tech support scams have been running a browser locker campaign from November 2020 until February 2021 on the world’s largest adult platforms including PornHub.
The same group behind this campaign has been active for much longer and we believe is tied to previous schemes we’ve identified before, making it one of the most prolific tech support scam operations to date.
In late January, we heard several complaints of fake Microsoft alerts and started to investigate them. We discovered a number of decoy dating sites used by fraudulent advertisers on TrafficJunky, the advertising company for brands such as PornHub, RedTube and YouPorn owned by MindGeek.
The scammers created those fake identities to redirect traffic away from the adult platforms onto pages showing bogus alerts claiming users were infected with pornographic spyware. This well-known scheme attempts to scare victims into calling so-called technicians for assistance but in fact defrauds them for hundreds of dollars.
We reported our findings to MindGeek and continue to track and share new incidents as they arise. We believe this threat actor will keep on tricking new victims until fully exposed and individuals apprehended by law enforcement.
Redirection chain
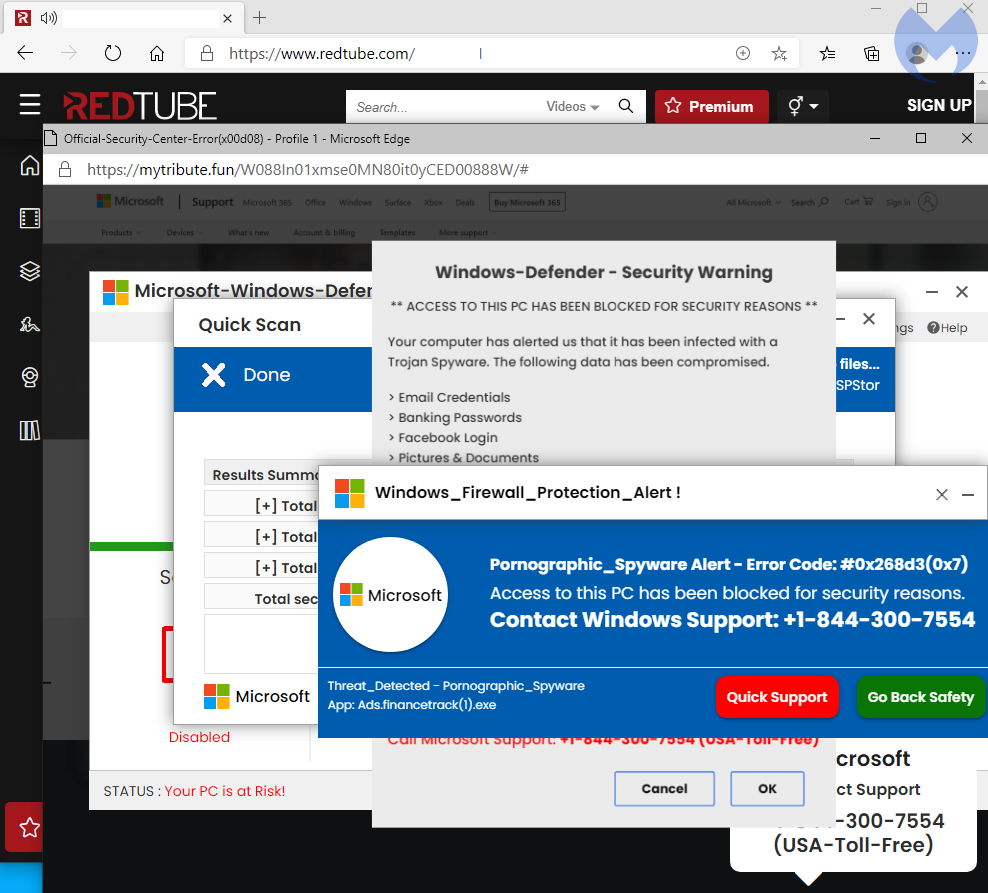
We were able to capture the malvertising redirection chain several times and the flow is almost identical. We know from our telemetry that the malicious advertiser is targeting victims from the U.S. and the U.K.
- User clicks to play a video
- A new browser window opens
- A request is sent to the TrafficJunky ad platform
- An ad is served and makes a request to a decoy dating site
- A redirect immediately loads the browser locker

This sequence of events can be summarized in the traffic capture below:

A key part of this malvertising chain is the use of many different fake dating portals that are hiding the redirection mechanism for the browser locker.
Beginnings
This browser locker campaign started well before showing up on PornHub[.]com and went undetected for a long time perhaps due to a clever typosquatting trick. In fact, we were fooled ourselves for a while before seeing what is obvious in hindsight.
On May 21 2020, the threat actor registered the domain name sassysenssations[.]com which contains a voluntary typo (two ‘s’) to mimic sassysensations[.]com which belongs to a legitimate business.
The real domain was registered in 2014 and we even found a billboard advertisement for it tweeted out on April 26 2019, long before the scammers had registered their copycat domain.

What was clever is that the threat actor didn’t seem to set up an actual site for that fake domain, but instead redirected all traffic to the real one if the visitor did not match the parameters from their malvertising campaign.
However, the malvertising chain shows that they leveraged that domain to perform conditional redirects, such as the one seen below:
(1) pornhub[.]com/_xa/ads?zone_id=[removed] (2) ads.trafficjunky[.]net/click?url=https%3A%2F%2Fsassysenssations[.]com% (3) sassysenssations[.]com/track.php?CampaignID=[removed]&Sitename=Pornhub (4) errorhelpline24x7msofficialsoftwareerrorcodex12[.]monster
Later on, it appears the threat actor started diversifying their scheme by creating a number of fake dating sites to use as redirects in addition to using the sassysenssations identity.
Fake dating sites
The malicious advertiser is using a model that has been tried before and consists of setting up fake identities in order to gain access to the ad platform. In this instance, we cataloged dating and romance sites. However, the majority of them did not look authentic or functional and even still had the ‘Lorem ipsum’ text filler.

If you were to visit one those sites directly, you may not see anything else of interest, at least nothing malicious in nature. However, the fraudulent advertiser can easily redirect traffic based on factors such as IP geolocation, referer and other artifacts.
In all, we detected close to 100 decoy domain names set up as “advertising landing pages” used to redirect victims to browser locker scams. Even though the templates are half finished, the threat actor is spending time creating a large inventory they can cycle through in their redirects towards browser lockers.
Browser locker
The browser locker is using a common theme of a fake Microsoft Windows Defender scanner. There is some browser profiling to serve the right template based on whether the user is on Windows or Mac.


While browsing one of the many decoy sites, we found the HTML source code in an exposed directory showing a few additional variations of the browser locker:

Fake advertising infrastructure
Because this is a long running campaign, the infrastructure is fairly large but tends to reuse the same naming convention for domains. The graph below only shows the domains created to abuse the TrafficJunky ad platform. It does not include domains used for the browlock itself.

There was a domain (recipesonline365[.]com) whose naming convention differed from the other dating sites. In fact it is the only one with a non-adult theme.
(1) youporn[.]com/_xa/ads?zone_id=[removed] (2) ads.trafficjunky[.]net/deep_click?adtype=pop&url=https%3A%2F%2Frecipesonline365[.]com (3) recipesonline365[.]com/?aclid=[removed] (4) oopi3.azurewebsites[.]net/Winhelpxcode161616winHelpSecurity0nlineCH007
Back in June 2019, we had identified an ad campaign targeting recipe keywords. The threat actor was using decoy recipe and food sites to lure victims via web searches. Those sites performed the same redirect mechanism as the decoy dating sites, and most of the time lead to a browlock hosted on Azure as well.
There are a number of other parallels between that campaign and the adult one such as the predominant use of NameCheap hosting and a large volume of decoy sites. For this reason we believe this is likely the same threat actor.
Protection
Browser lockers are not dangerous in and out of themselves. They are simply a fake warning which may be disrupting and annoying but one that does not indicate a computer problem.
In recent years they have become very common and affect all browsers, even mobile ones. In the past, we have seen browser lockers that were effectively giving the impression the machine was locked due to how they abused the user interface. As of know, most of them can be closed normally without requiring the use of special commands.
Malwarebytes users were already protected against this campaign. Our Browser Guard extension can detect and stop browser lockers using heuristic techniques that do not require to use a blacklist of known domain names or IP addresses.
Indicators of Compromise
The list of IOCs can be downloaded from our GitHub here.










