In our last blog, Barcode Scanner app on Google Play infects 10 million users with one update, we wrote about a barcode scanner found on the Google Play store that was infected with Android/Trojan.HiddenAds.AdQR. All initial signs led us to believe that LavaBird LTD was the developer of this malware, but since then, a representative from LavaBird reached out to us. They claimed it was not them who was responsible for uploading malicious versions of Barcode Scanner, package name com.qrcodescanner.barcodescanner, but an account named “The space team.”
Upfront, we must also say that though we attempted to reach “The space team” when writing this story, we received no response.
Here, we will show the evidence of the case presented by LavaBird.
LavaBird pleading its case
Below we have the original message from LavaBird from February 10, 2020. We have provided minor editing to conceal and remove sensitive information:
“Good day.
We have read the article and are outraged no less than you. We were the intermediary between the seller and the buyer in this situation.
And the application was transferred to the account “The space team”
Herewith the following account details:
Here is their official email (as listed in Google Play) – digitalapp@yahoo.com
We have written them a letter so they should remove their Google Play account.
Also, we reported that account and app to Google.
Lavabird LTD develops and sells applications, and sometimes we buy and sell applications.
We have a lot of useful apps on our account, who always complied to all Google Policies – https://play.google.com/store/apps/developer?id=LAVABIRD+LTD
The update that we published from our account was made by the buyer to verify the key and password from the application.
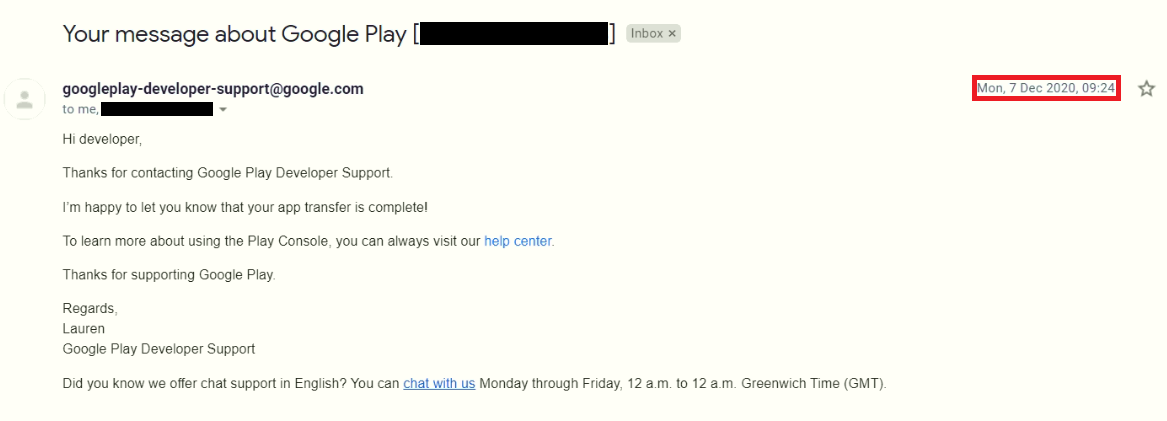
The buyer was given access to the Google Play console of this application and he updated it himself. After that in a week, we transferred an application to buyer Google Play account – it was 7th of December.
We attached a screenshot, from our developer computer the app is visible – probably because he still has got Barcode app on his device. The app is unpublished, probably, since, for people, who do not have the app installed, you can see only “We’re sorry, the requested URL was not found on this server.”
We are very sorry that the application has become a virus, for us it is not only a blow to our reputation.
We hope users will remove the app with a virus from their phones.
We ask you to change the name of the developer to the real “The space team” and attach actual screenshots if needed.
Regards LAVABIRD LTD”
Transferring of ownership
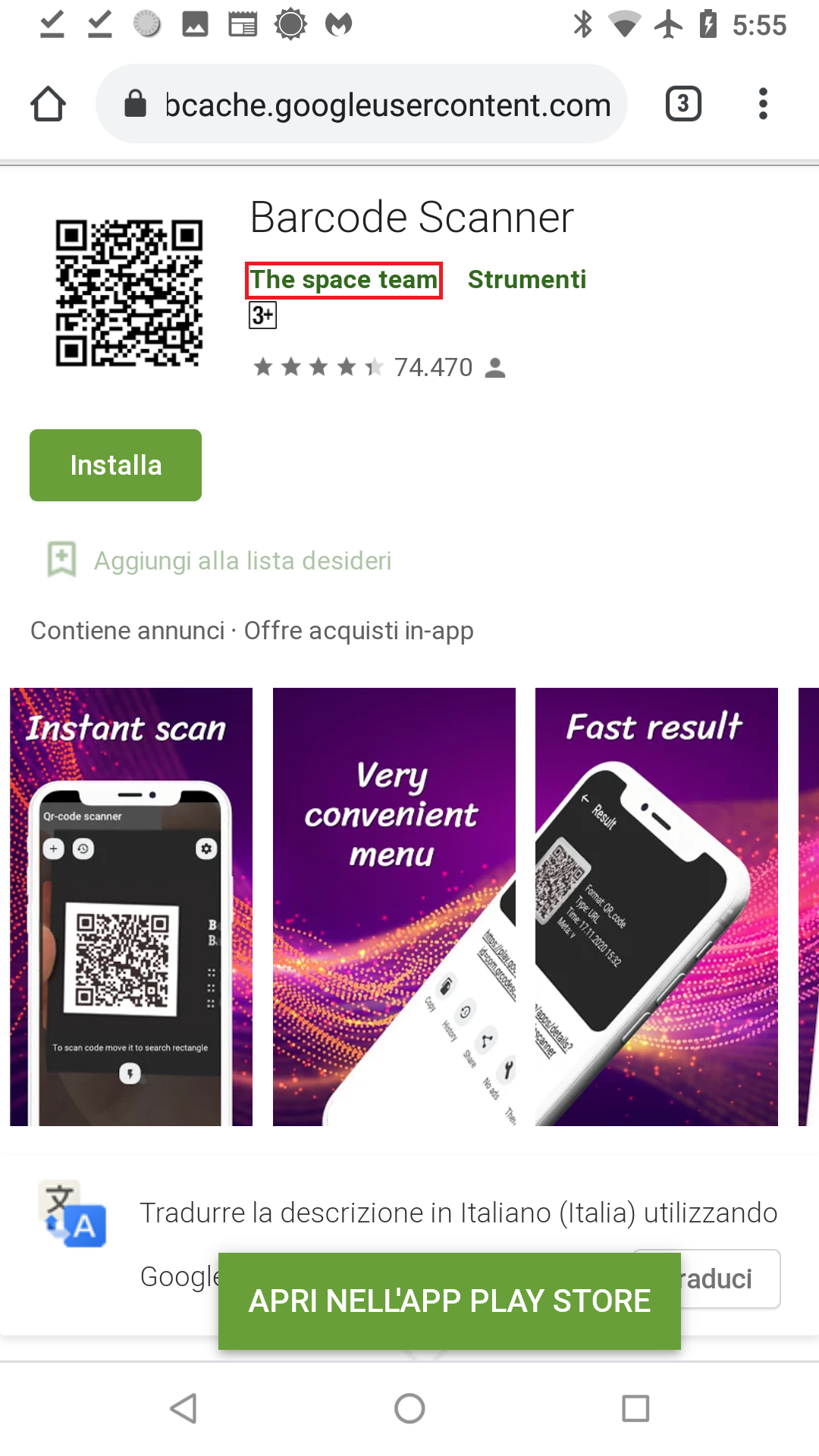
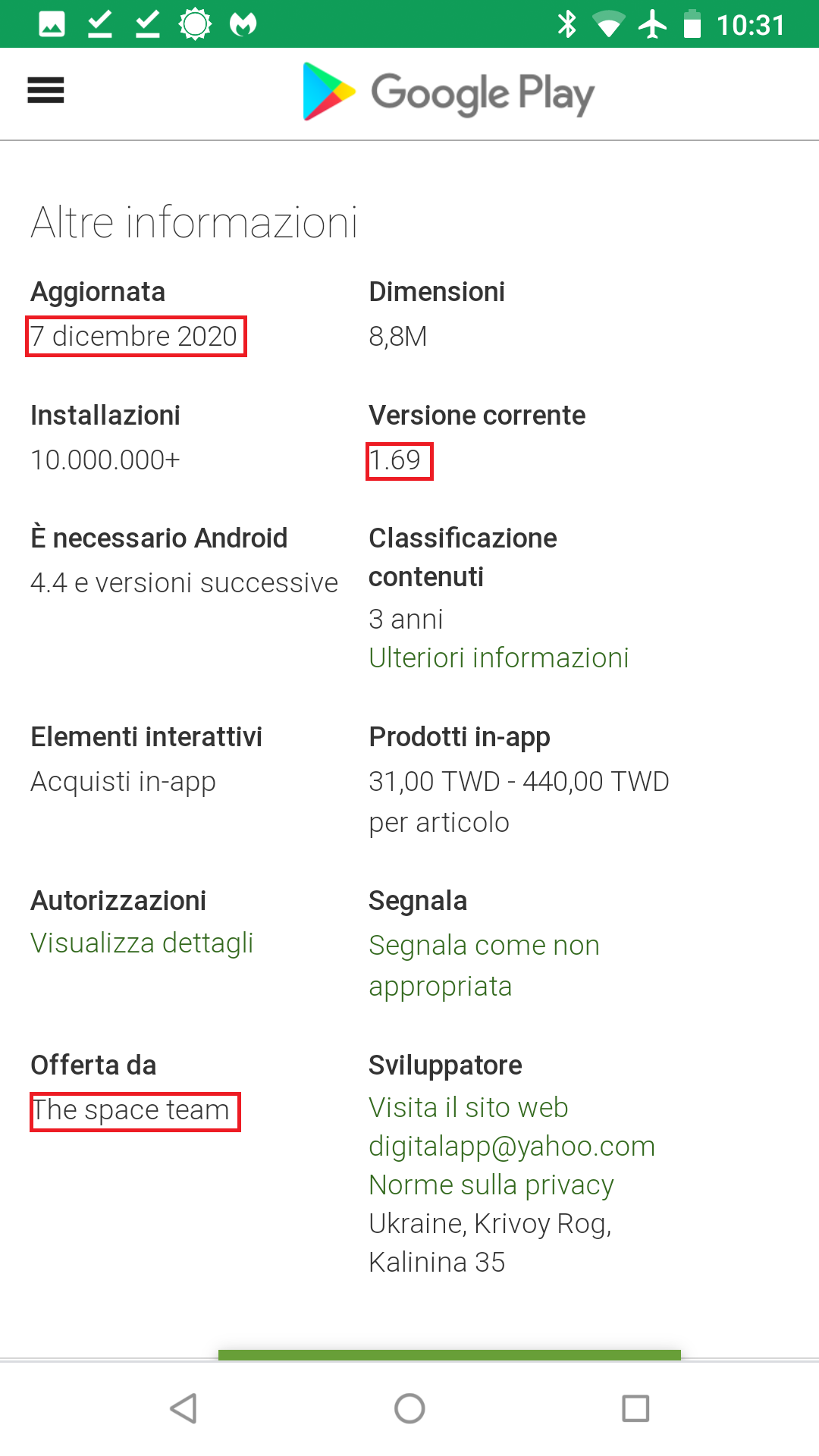
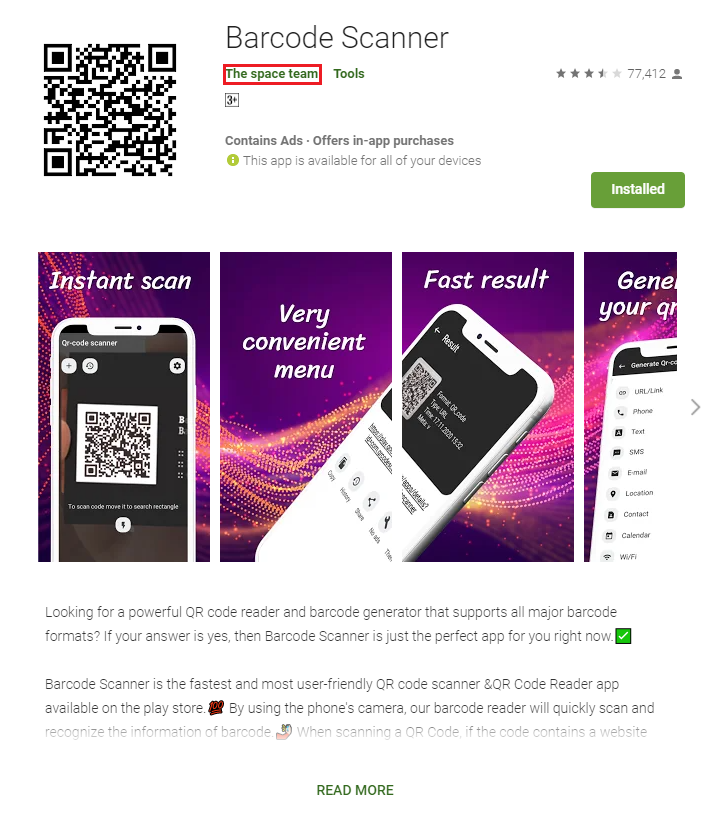
Let’s start with LavaBird’s claim of transferring ownership to The space team on December 7th, 2020. To verify LavaBird’s claims, we search for our own cache Google PLAY webpage of the Barcode Scanner with The space team as owner. Although we’ve included screenshots from the Italian version of the site, here is evidence of ownership to The space team of Barcode Scanner on the date of transfer, December 7, 2020:
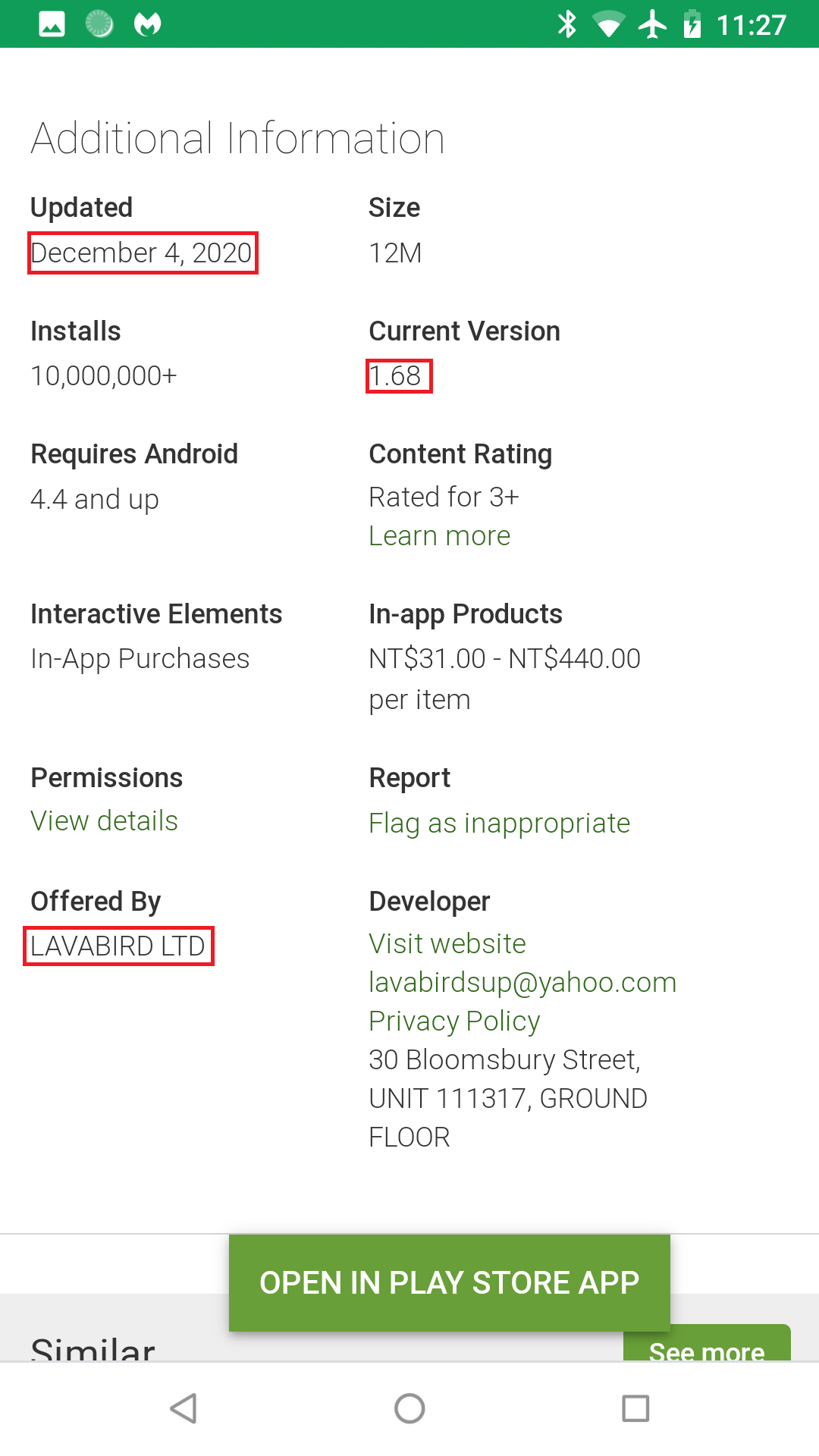
Although this may be true, this raises another question. Why did we find evidence of LavaBird being the owner during our last blog prior to the transfer date? The screenshot from our last blog is December 4, 2020:
Was the malware code really added on December 7, or did it exist before? Did we make a mistake of accusing the wrong developer? Further investigation was needed to verify. Thereupon, we turn to third-party app stores that grab APKs from Google Play the date they upload to Play. Keep in mind these types of app stores do not scan APKs for malware like Google Play does. We assume this is due to them trusting Google Play to do that job in advance. Thus, if malware is later revealed to have gotten onto Google Play, third-party app stores do not remove the APKs from their sites. In other words, use third-party app stores at your own risk. (But for purposes of grabbing old versions of apps, malware versions and all, third-party app stores are great.)
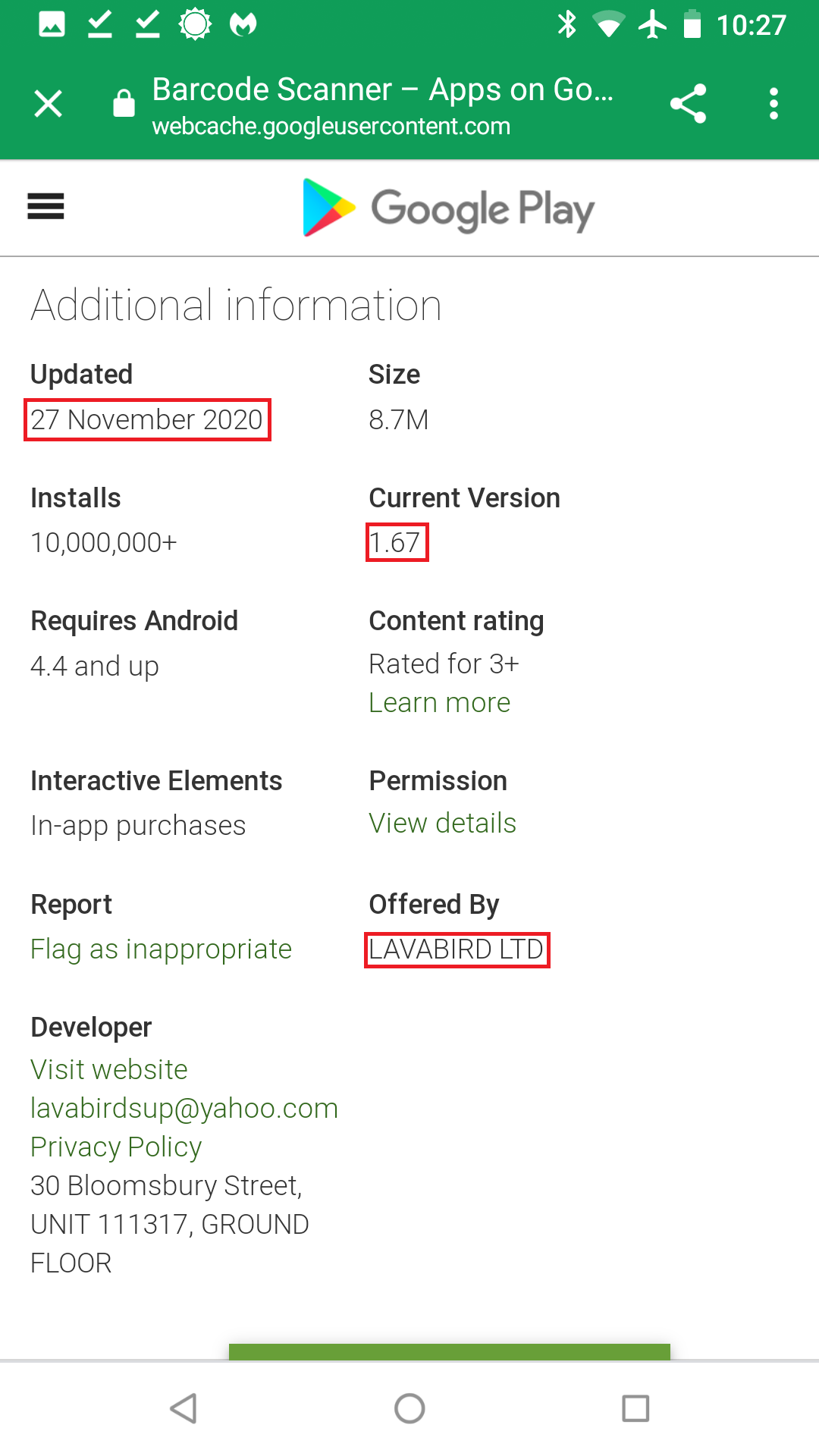
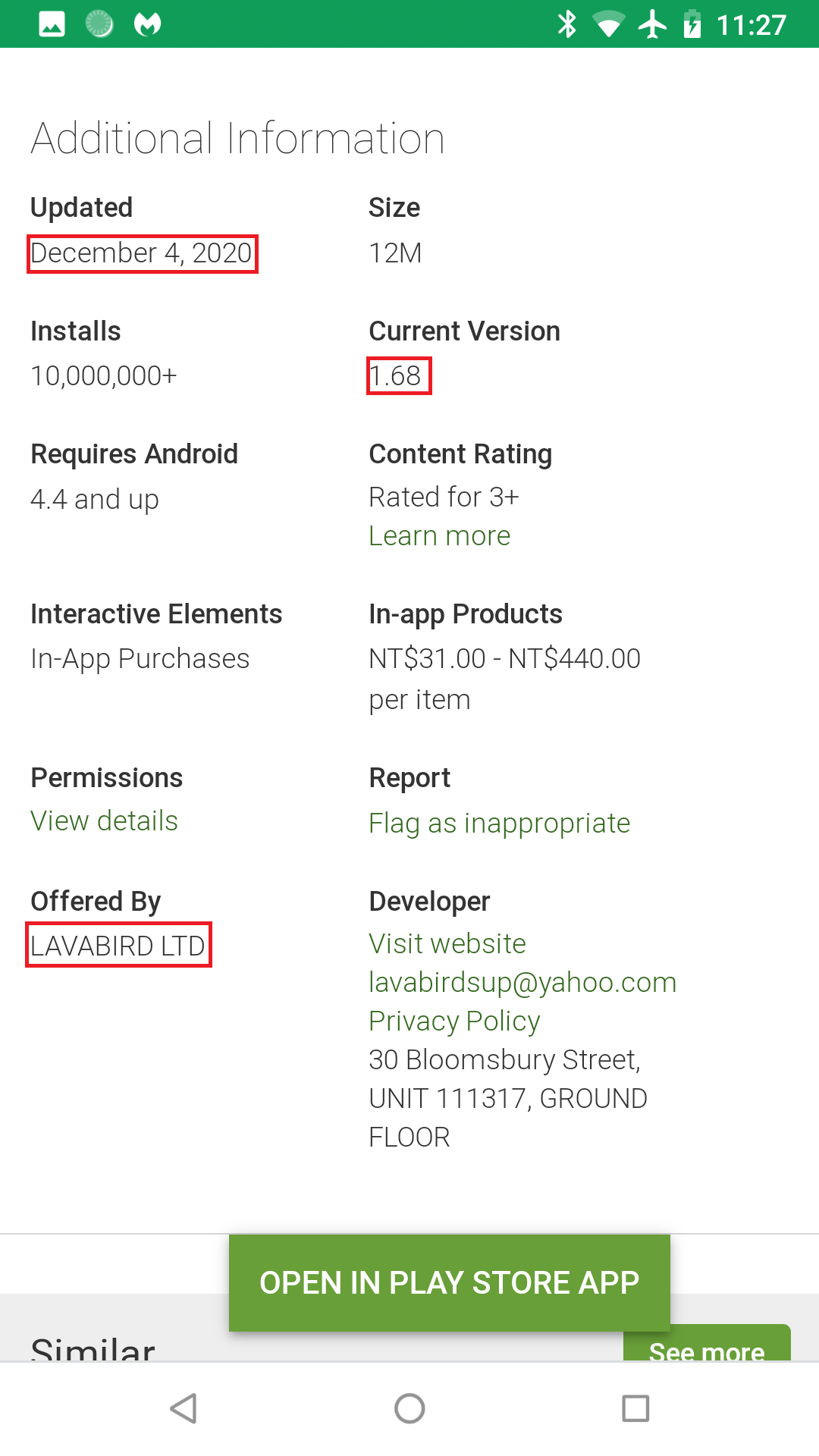
The following shows our findings of analyzing multiple versions of Barcode Scanner, package name com.qrcodescanner.barcodescanner, from third-party app stores. The first version containing malware is Barcode Scanner v1.67. The timestamp is November 28, 2020, before the transfer. Grabbing yet another cache Google Play webpage, we prove that v1.67 ownership belonged to LavaBird LTD at that time:
Furthermore, analyzing Barcode Scanner v1.68, the one in our last blog’s screenshot, we prove it contains malware as well. Hence, our accusation is true. LavaBird is indeed the owner during the time of infection. We then went on to analyze the previous version of Barcode Scanner—v1.62—from August 11, 2020. Lo and behold, this version is clean. This is how we can conclude that the infection starts with Barcode Scanner v1.67.
Clarifications from LavaBird
With many unanswered questions, it was time to reach out to LavaBird. I would like to state upfront that LavaBird was quick to respond to all inquiries and proved very helpful during this process.
The transfer to LavaBird
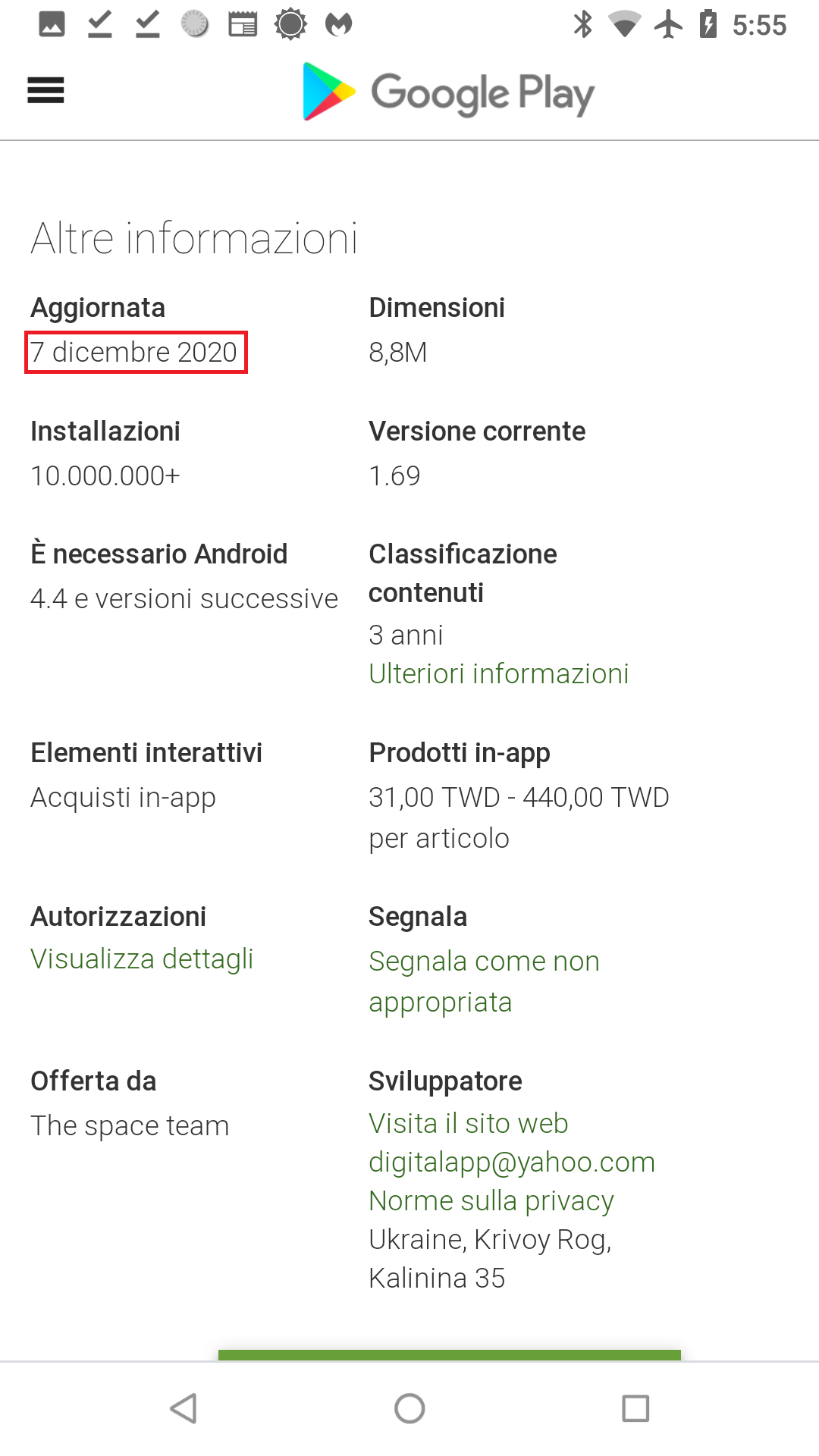
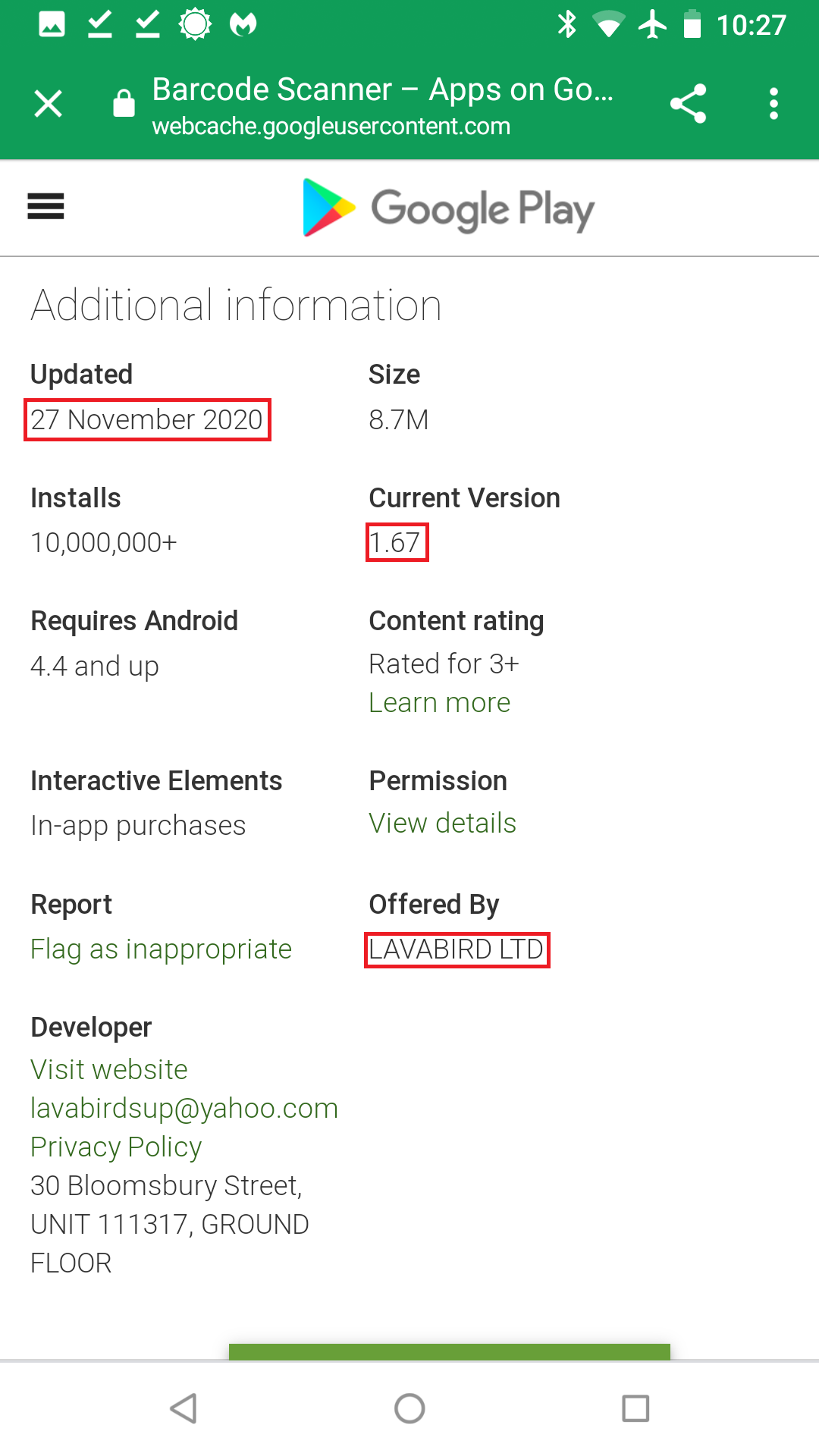
LavaBird stated originally, “We were the intermediary between the seller and the buyer in this situation.” Not being the original developer, LavaBird was transferred ownership of Barcode Scanner on November 23, 2020.
It is important to note that we were unable to find any cache Google Play webpages to find the previous owner but we can verify that previous app versions did exist based off third-party app store data.
Transferring of keys
The big question for LavaBird is this: If “The space team” is the bad actor here, why is the that first version of Barcode Scanner that contains malware, v1.67, lists its ownership to LavaBird?
LavaBird explains:
“To verify the authenticity of the app signing key and password, we gave them (The space team) the option to update the app. As soon as they were convinced of the correctness of the keys, the transaction took place on December 7, the application was transferred to their account.”
The quoted “app signing key” needs some explaining. App signing is setup via Google Play when an app developer first creates an app and wants to upload it onto the digital store. In this process, Google assigns them a keypair. The keypair comes with a public key and a private key.
Every app that is installed from Google Play onto a mobile device is signed with a public key. When an app developer uploads a newer update of the app to Google Play, they sign it with the assigned private key. This is due to the fact that mobile devices will only accept an update of an already installed app when its public key matches the private key. This is done to prevent others from uploading a malicious version of your app to Google Play with a different private key. For this reason, transferring of the app’s signing key when transferring ownership of the app is a legitimate part of process. Therefore, the request by “The space team” to verify that the private key works by uploading an update to Google Play seems plausible.
Updating the analytics
LavaBird went to on to explain:
“We also agreed to update the app with their analytics (according to them it was just analytics) for half of the sum, before transferring the application.
Our agreement included the conditions that they would check the operation of the application with their analytics, as you can see there were 2 updates. One on November 27 and another on December 4. All updates were made by them. We were in the process of selling the application, so we tested the application only manually.”
Now we know the second reason for the updates is for “The space team” to modify the analytics code. Note that every Android app has some type of analytics in the code which gathers simple data points. Nothing unusual there. Looking at the code of Barcode Scanner versions for myself, there certainly is modification to the analytics code. However, during this same time period is when the adding of the malicious code occurred.
Keep in mind that allowing a developer to modify code, even analytics, before transferring is not common practice. When asked why they did not check the code themselves before allowing the update they replied:
“Usually we do not check the code, because the application will go to another publisher and if he makes mistakes, then it will be a minus for him and not for us.”
LavaBird continued, stating, “We are very sorry that this did not arouse suspicion, again, we thought that the application would be on their account soon and it would not affect us … We were very wrong.”
I also went on to ask if there was any research done on “The space team” to verify trust in them. LavaBird responded that “Unfortunately, we did not have such practice, but this lesson will remain with us for life.” LavaBird apparently found The space team as a buyer through word of mouth.
Thereafter, both updates containing malicious code on November 28 and December 4 are shown with LavaBird LTD being the owner:
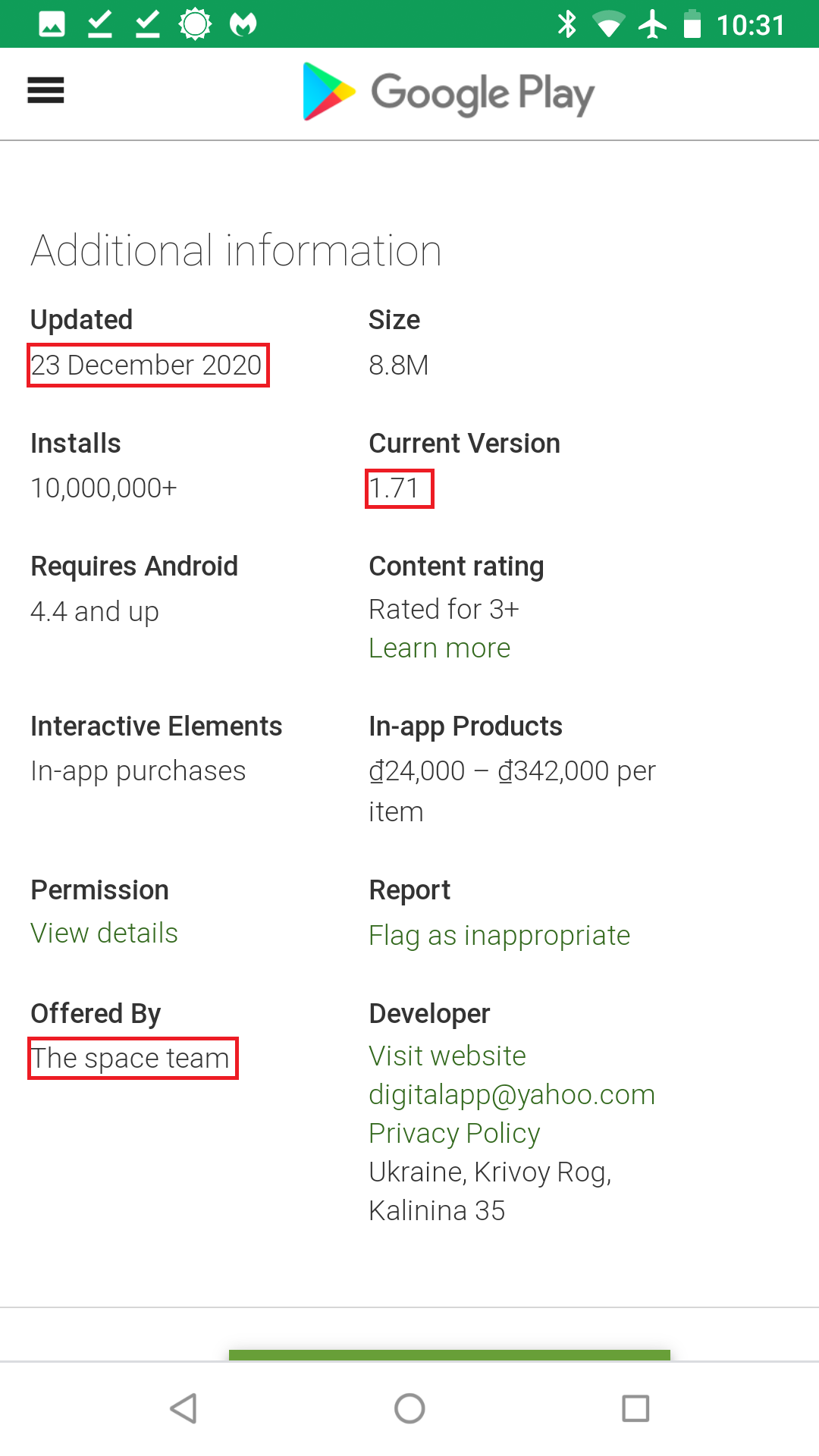
It is not until December 7, the date of the transfer, that the owner shows as “The space team.”
Breaking down the timeline
For simplicity, here is a breakdown of the timeline:
- August 11, 2020: Barcode Scanner v1.62 is uploaded to Google Play and is a clean version from owners prior to LavaBird LTD
- November 23, 2020: LavaBird purchases a clean version of Barcode Scanner
- November 25, 2020: LavaBird enters agreements with “The space team”
- “The space team” claims they need to, according to LavaBird, “verify the authenticity of the app signing key and password” and “update the app with their analytics” which led to updates on Google Play
- November 27, 2020: Barcode Scanner v1.67 is uploaded to Google Play with malicious code added with LavaBird shown as owner
- LavaBird claims this was done by “The space team” prior to purchase, according to their agreement
- December 4, 2020: Barcode Scanner v1.68 is uploaded to Google Play still containing malicious code
- December 7, 2020: LavaBird transfers ownership of Barcode Scanner to “The space team”
- December 7, 2020: Barcode Scanner v1.69 is uploaded to Google Play with “The space team” as the owner and still contains malicious code
Here is the timeline after the transfer to “The space team”:
- December 21, 2020: Malwarebytes forum patrons first report an instance of infected Barcode Scanner
- December 24, 2020: Malwarebytes for Android adds detection originally as Android/Adware.AdQR.FBG
- December23, 2020: Barcode Scanner v1.71 obfuscates malicious code to evade detection
- December31, 2020: Barcode Scanner v1.73 further obfuscates malicious code to evade detection
- December31, 2020: Barcode Scanner v1.75 further obfuscates malicious code to evade detection
- January 5, 2020: Barcode Scanner v1.75 is last known malware-infected version released on Google PLAY
- Somewhere thereafter Google Play must have removed the app from the store
- February 1, 2020: Malwarebytes for Android detection updated with increased severity to Android/Trojan.HiddenAds.AdQR which detects all versions
- February 5, 2020: We publish Barcode Scanner app on Google Play infects 10 million users with one update with a screenshot of a Google Play webpage showing LavaBird as owner of the infected Barcode Scanner
- February 10, 2020: We received the original message from LavaBird
More information about the The space team
Alright, so who is “The space team”? The only evidence of them on Google Play is from the Barcode Scanner mentioned and an app called Alarm Clock – Loud and Accurate Alarm, package name com.alarm.clock.wake.up. This app was only on Google Play briefly in December 2020, and is a legitimate, clean app. No other apps appear to exist under the developer’s name. Because there is only evidence of “The space team” existing from December 2020 to January 2021, we can only assume that the developer account was created in December 2020.
When asking LavaBird of any additional information about “The space team,” they said they “do not have any other information.”
“Also,” LavaBird added, “I think that this is not a company and they can easily create account.”
In effect, this confirmed my assumptions of them creating an account at the time of transfer. For the purpose of being fair, we did attempt to reach out to “The space team” to comment on the allegations set forth by LavaBird. They did not respond.
Here is the only information on the “The space team” that we have:
Publisher:The space team
Email:digitalapp@yahoo.com
Address:Ukraine, Krivoy Rog, Kalinina 35
Final Thoughts
From my analysis, what appears to have happened is a clever social engineering feat in which malware developers purchased an already popular app and exploited it. In doing so, they were able to take an app with 10 million installs and turn it into malware. Even if a fraction of those installs updates the app, that is a lot of infections. And by being able to modify the app’s code before full purchase and transfer, they were able to test if their malware went undetected by Google Play on another company’s account.
There is an important lesson here. To all app sellers, be weary to who you sell. If at all possible, verify their credibility. Furthermore, be skeptical if they are asking unreasonable requests such as modifying code, even analytics, before transfer.
Ultimately, I believe LavaBird’s claims. Unfortunately, LavaBird came in our crosshairs after firing off a blog about this malicious Barcode Scanner. As the evidence shows, we were in right in doing so. Regardless, now knowing the full story we apologize it led to this. We write this in hopes of clearing LavaBrid’s name.