Tor, The Onion Router
Tor (The Onion Router) is free software used to keep your online communications safe and secure from outside observers. It’s designed to block tracking and eavesdropping, resist fingerprinting (where services tie your browser and device information to an identity), and to hide the location of the people using it.
The network of websites and services that are only accessible using Tor is often referred to as “The Dark Web” or, more correctly, “The Dark Net”. Although the Dark Web has a reputation for being a place where criminal activity takes place there is nothing intrinsically bad or criminal about Tor. In fact, it was originally created to keep US intelligence communications safe. If your primary concern online is to try and stay anonymous, this is something you’d turn to.
How Tor works
Tor uses layers of encryption to keep your traffic secure. (It’s called “onion” routing because it has multiple layers, like an onion.) Traffic passes through random servers (or nodes) kept running by, well, anybody. You won’t know who is responsible for running the nodes, and the nodes don’t know, and can’t see, what traffic is passing through them.
By default, traffic passes through three nodes, called a Circuit, and the nodes in the Circuit are changed every ten minutes. Each node peels back one layer of encryption. The encryption ensures that each node is only aware of the node that came before it and the node that comes after it. Tor uses three nodes in a circuit because it’s the smallest number of nodes that ensures no point in the system can know both where your traffic originated and where it’s eventually going.
Tor can either be used to access services on the regular Internet or services that are also hidden behind Tor. If you use Tor to access the Internet your Circuit of three nodes acts like an anonymous and very secure Virtual Private Network (VPN) that hides your IP address from the things you use. If you use Tor to access other services that are also hidden by Tor then neither side of the communication can see the IP address of the other.
There are numerous ways to use Tor. You can configure your computer so that all of its communications use the Tor network, or you can use individual applications that make use of it, like the Tor Messenger, launched in 2015. Most people’s first, and perhaps only, experience of Tor is via the appropriately named Tor browser though, which is used for secure web browsing both on the regular web and the Dark Web. As a result, that’s what we’ll focus on below.
The Tor browser
The Tor Browser, which began development in 2008, is a web browser with multiple security and privacy options built in by default. A modded Firefox browser, it connects to the Internet using Tor, and comes with the NoScript and HTTPS Everywhere plugins pre-installed. It also has a number of security defaults cranked up to eleven, to prevent things like browser fingerprinting. It can be used for browsing regular websites securely, or for browsing websites on the Dark Web.
As far as the default operations of the Tor Browser go, NoScript allows active content for trusted domains only. In practice, what this means is that (for example) a site you’re visiting for the first time won’t be allowed to run JavaScript until you allow it.
HTTPS Everywhere helps by ensuring that you don’t accidentally connect to websites using the unencrypted HTTP protocol.
The Security Level settings, available via the browser’s preferences, allows users to customise a wealth of security options, or choose a default.
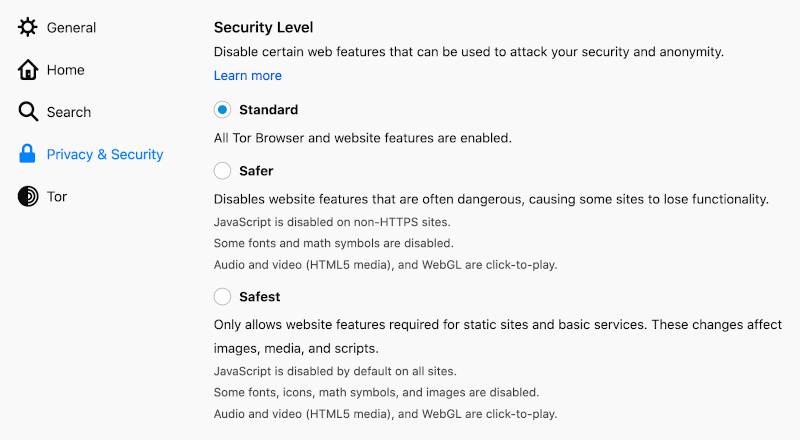
The default Standard option enables all Tor browser and website features. Safer disables a number of common website options, such as JavaScript on non-HTTPs sites. Audio and video are click to play. Safest “only allows website features required for static sites and basic services. These changes affect images, media, and scripts. In other words, it’s as bare bones a web experience as you’re likely to have. Many sites simply will not function. There’s a big trade off in functionality for security here, and casual users probably won’t have much interest in this.
Possible risks of using Tor
The fact that anyone can run a Tor node is a feature, but it’s also a possible threat. There’s no guarantee the person running a node isn’t a rogue entity and the total number of nodes is relatively small: Just a few thousand. Although Tor is designed to be resistant to snooping nodes, the last node in a Circuit (known as an Exit node) can be used for spying on traffic that is leaving Tor and joining the regular Internet.
Rogue / snooping exit nodes are definitely a concern. Law enforcement also definitely takes an interest in this area, so temper your expectations appropriately.
Law enforcement or threat actors that are present on a large number of nodes can also theoretically run “correlation attacks”. These undo Tor users’ anonymity by trying to match up traffic entering the Tor network with traffic leaving the Tor network, based on things like timing. Tor isn’t perfect, but it hugely increases the time and effort an adversary would have to expend to spy on you.
One school of thought commonly seen online suggests using Tor in the interest of anonymity makes you stand out and is akin to firing a large “I AM HERE” flare gun into the sky. While this may be true in some cases, for most people using it this probably isn’t an issue.
By comparison, people using a VPN are probably more interested in privacy than anonymity. A VPN is run by a single organisation, as opposed to bouncing you through lots of random nodes maintained by complete strangers. Because Tor uses more nodes and more encryption than a VPN it is normally slower.
VPNs can also be compromised, and user data put up for grabs. Nothing is 100% guaranteed to be secure, and that holds true here whether using VPNs or Tor. It’s up to users to pick the option most suited to their needs, and account for things potentially going wrong.
That isn’t to dissuade you from using either service; if you’re considering using either, there’s likely a valid need for it. In practical terms a little boost in anonymity and / or privacy can only be a good thing, so get a feel for what options are available and stay safe regardless of your ultimate choice.










