Despite advance warnings that a root certificate provided by Let’s Encrypt would expire on September 30, users reported issues with a variety of services and websites once that deadline hit. So what happened?
The problem
A number of high profile tech and security companies noticed their products and services were affected by the certificate expiration, such as cloud computing services for Amazon, Google, and Microsoft, IT and cloud security services for Cisco, as well as sellers that were unable to log in on Shopify.
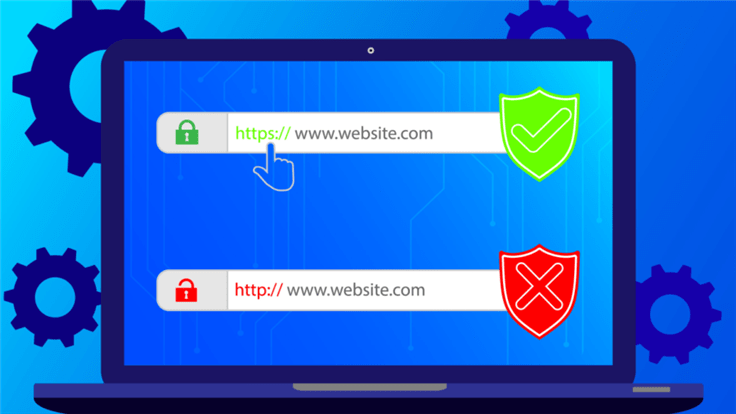
When a user’s browser arrives at your website one of the first things it checks for is the validity of the SSL certificate. An SSL certificate is a digital certificate that authenticates a website’s identity and enables an encrypted connection. SSL certificates are issued by a Certificate Authority (CA). Most browsers will accept certificates issued by hundreds of different CAs. Let’s Encrypt is a CA that provides digital certificates as a free non-profit and millions of websites rely on Let’s Encrypt services.
If the certificate, or the root certificate that signed it, has expired, it issues a warning that the site may not be secure or the connection is not private. At least 2 million people saw an error message on their phones, computers, or smart gadgets due to the certificate issue.
GnuPG
GnuPG free implementation of the OpenPGP standard as defined by RFC4880 (also known as PGP). GnuPG allows you to encrypt and sign your data and communications; it features a versatile key management system, along with access modules for all kinds of public key directories.
GnuPG is a command line tool without any graphical user that is often used as the actual crypto backend of other applications.
Even though many organizations had not forgotten about the certificate expiration, GnuPG did not handle it well. And since many were unaware of the fact they were even using GnuPG, because it functions as the backend of another application, it took some organizations a while to figure out and correct the problem. Without knowing the cause, it’s a difficult problem to identify. For the affected companies, it’s not like everything is down, but they’re certainly having all sorts of service issues.
The update
The new version of GnuPG 2.2.32 (LTS) fixes the problem with Let’s Encrypt certificate chain validation, and this update should restore access to many web resources (e.g. Web Key Directory and key servers). “LTS” is short for long term support, and this series of GnuPG is guaranteed to be maintained at least until the end of 2024.
SSL/TLS certificate management
Digital certificates are the primary vehicle by which people and machines are identified and authenticated. As the number of identities in a company grows, so does the difficulty of managing and protecting certificates at scale. The adoption of BYOD and IoT makes certificate management even more critical than ever.
Like passwords and keys, certificates also go through a cycle. They’re created, provisioned into the infrastructure, and have a finite validity period after which they expire. Certificate Management is usually concerned only with certificates issued by mutually trusted Certificate Authorities. Once the digital certificates have been issued, they must be managed diligently through their entire validity period.
If this incident has shown one thing that is how important it is to keep track of all the digital certificates that your organization relies on.