Mozilla released version 102.0 of the Firefox browser to Release channel users on June 28, 2022.
The new version fixes 20 security vulnerabilities, five of which are classified as “High”. The new version also comes with a new privacy feature that strips parameters from URLs that track you around the web.
Vulnerabilities
Publicly disclosed computer security flaws are listed in the Common Vulnerabilities and Exposures (CVE) database. Its goal is to make it easier to share data across separate vulnerability capabilities (tools, databases, and services). These are the CVEs we think you should know:
High
CVE-2022-34479: A malicious website that could create a popup could have resized the popup to overlay the address bar with its own content, resulting in potential user confusion or spoofing attacks. This bug only affects Firefox for Linux. It does not apply to other operating systems.
CVE-2022-34470: Use-after-free in nsSHistory. Use after free (UAF) is a vulnerability caused by incorrect use of dynamic memory during a program’s operation. If after freeing a memory location, a program does not clear the pointer to that memory, an attacker can use the error to manipulate the program. Navigations between XML documents may have led to a use-after-free and potentially exploitable crash.
CVE-2022-34468: CSP sandbox header without ‘allow-scripts’ can be bypassed via retargeted javascript: URI. An iframe that was not permitted to run scripts could do so if the user clicked on a javascript: link.
CVE-2022-34484: Memory safety bugs fixed in Firefox 102 and Firefox ESR 91.11. Some of these bugs showed evidence of JavaScript prototype or memory corruption, and with enough effort some of these could have been exploited to run arbitrary code.
Moderate
CVE-2022-34482 and CVE-2022-34483: Two separate issues with the same effect. Drag and drop of malicious image could have led to malicious executable and potential code execution. An attacker who could have convinced a user to drag and drop an image to a filesystem could have manipulated the resulting filename to contain an executable extension.
CVE-2022-34478: The ms-msdt, search, and search-ms protocols deliver content to Microsoft applications, bypassing the browser when a user accepts a prompt. These applications have had known vulnerabilities, exploited in the wild, so in this release Firefox has blocked these protocols from prompting the user to open them.
New privacy feature
Many companies involved in advertising use custom URL query parameters that enable them to track clicks on links. The most well-known example is probably the ?fbclid= parameter that Facebook adds to outbound links.
With the release of Firefox 102, Mozilla has added the new “Query Parameter Stripping” feature that automatically strips some of these query parameters. It does not matter whether you clicked on a link or pasted the URL into the address bar.
To enable Query Parameter Stripping, go into the Firefox Settings, click on Privacy & Security, and then change Enhanced Tracking Protection to Strict.
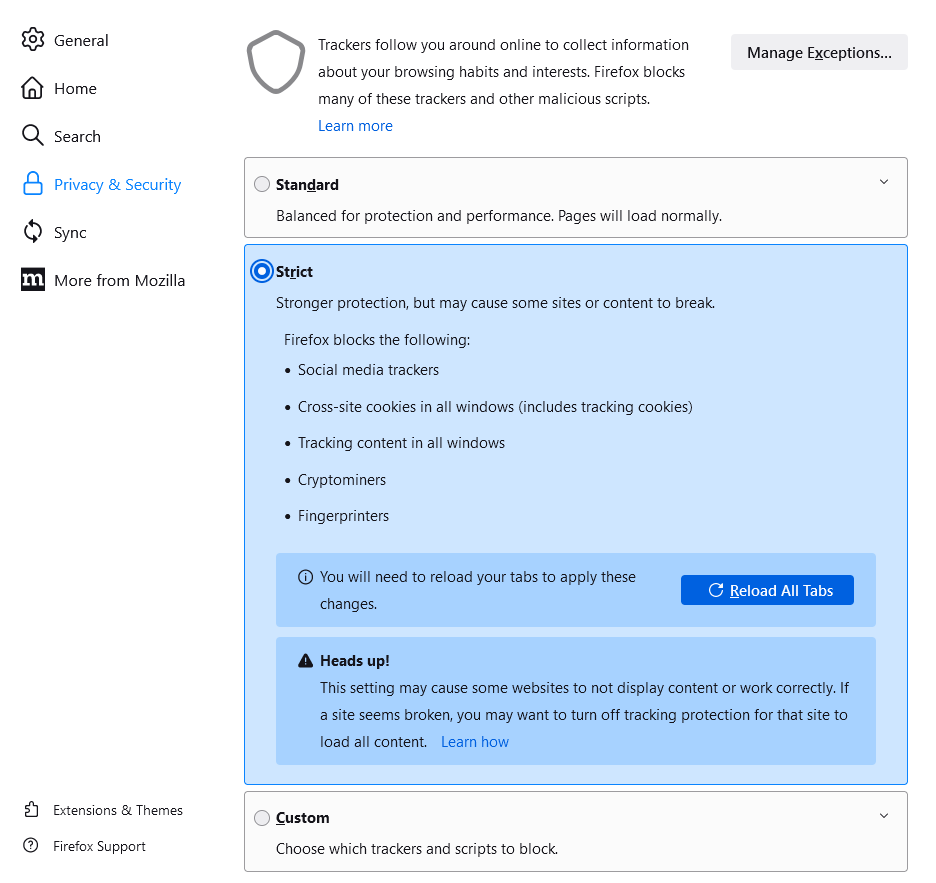
You will need to click Reload All Tabs to apply the changes. If you find that setting Enhanced Tracking Protection to Strict could causes issues with certain sites, you can use the Manage Exceptions option to add these websites, or use the “Custom” setting to choose which trackers and scripts to block.
Updating
Under normal circumstances, updates will be applied without user intervention. You can check for the version number in the products’ menu under Help > About

Should you not be using the latest version for some reason, e.g. automatic updates are disabled, then this screen will inform you that a new version is available and will start downloading it.
When it’s done, you’ll see a prompt to restart the browser. This will apply the update.
Stay safe, everyone!











