A new phishing campaign targeting PayPal users aims to get extensive data from potential victims. The data it’s after includes government documents like passport, as well as selfie photos. In a nutshell, it’s an extensive form of information theft, the likes of which could result in someone’s identity being fully stolen and their financial and other online accounts being taken over.
PayPal phishing sites are a dime a dozen due to the number of people and companies using it as another form of payment method. However, what’s notable about this campaign is that all the phishing pages are hosted on legitimate WordPress sites.
Hundreds—if not thousands—of WordPress sites remain vulnerable and easily exploited by scammers because of their poor security and the use of weak passwords. This was evident after Akamai found an attacker had planted a phishing kit on its WordPress honeypot.
After successfully brute-forcing their way into the WordPress site using a list of common credentials, the attackers then installed a file manager plugin that let them upload the phishing kit to the compromised site.
To avoid detection, the phishing kit cross-referenced IP addresses to domains belonging to companies it wants to avoid. Naturally, some of these domains include those belonging to cybersecurity organizations.
Blending into the background
Akamai researchers also noticed how the scammers made an effort to make their phishing page as indistinguishable as possible from the legitimate one. For one thing, the actors used .htaccess (short for hypertext access), a file that allows an admin to modify how a URL destination appears on the address bar.
In this case, the scammers wanted their phishing URL to make it look like it wasn’t a PHP file, so they edited out the “.php” bit of the URL. This makes sense because PayPal’s sign-in page doesn’t have an extension.
Oddly enough, the phish starts off asking users to type in the alphanumeric string they see on the “Security Challenge” page, under the guise of a means to verify that the user isn’t a bot.
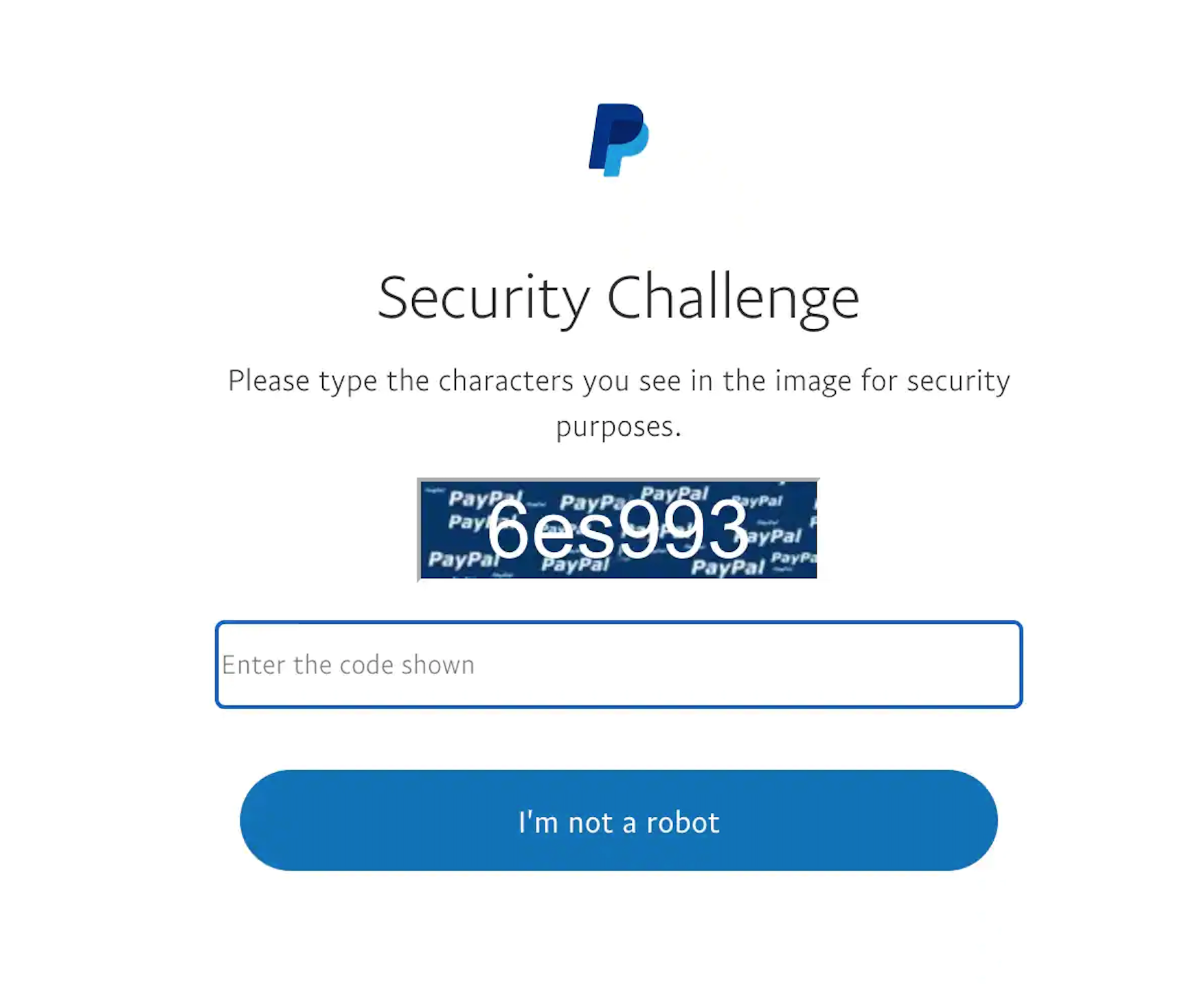
The next page then asks for the user’s PayPal credentials. Normally, phishing kits would stop here, and the scammers would leave content with the PayPal credentials they can then misuse and abuse.
But not here. In this case they want more. This is just the start of a sophisticated work-up to get users to provide such sensitive information without them realizing it.
After users provide their PayPal credentials, they are then presented with a notice of “unusual activity” in the next screen.
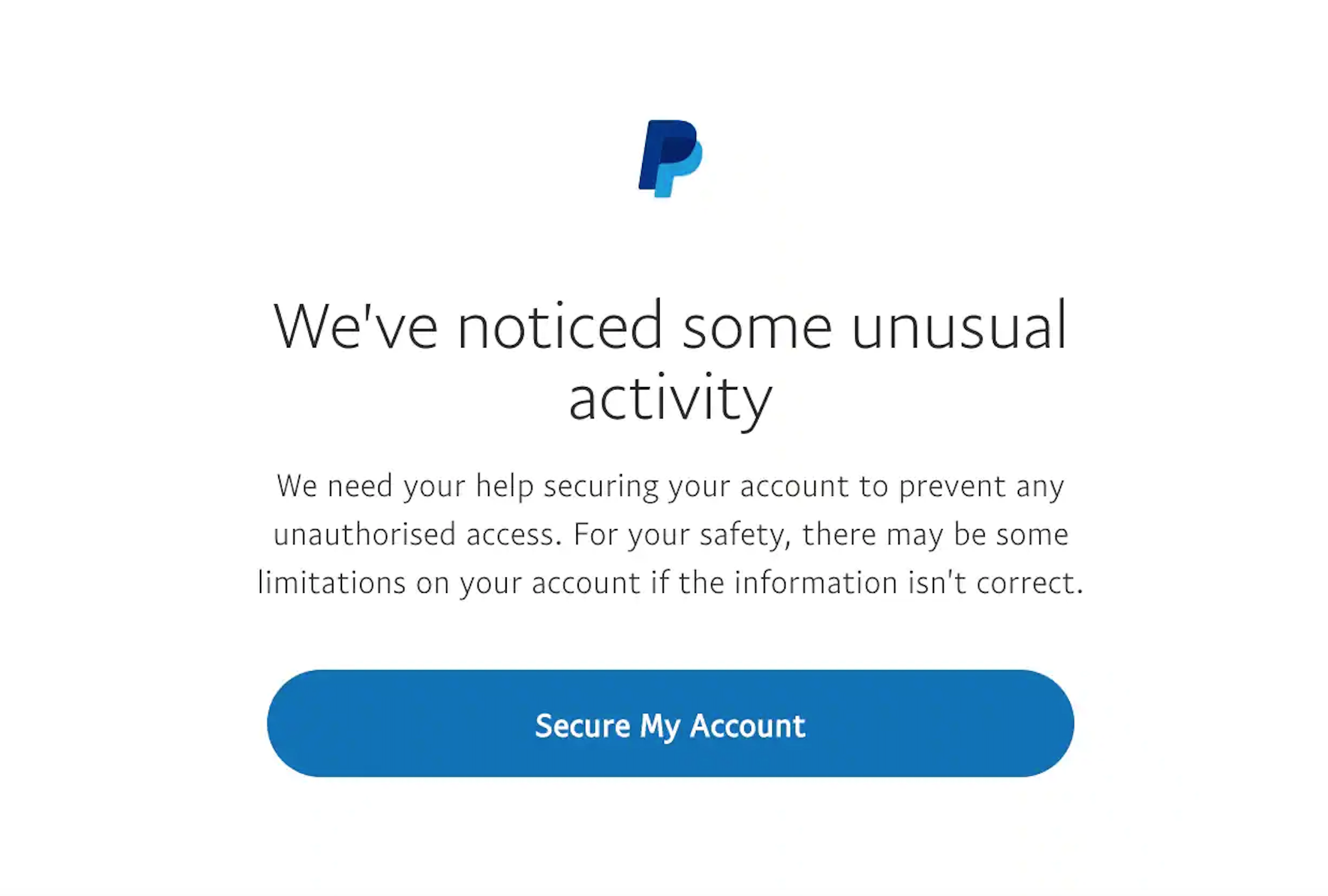
Once users click the “Secure My Account” button, they are then directed to a page telling them to confirm all their card details. Here, Akamai noted that a ZIP code and CVV are normally sufficient.
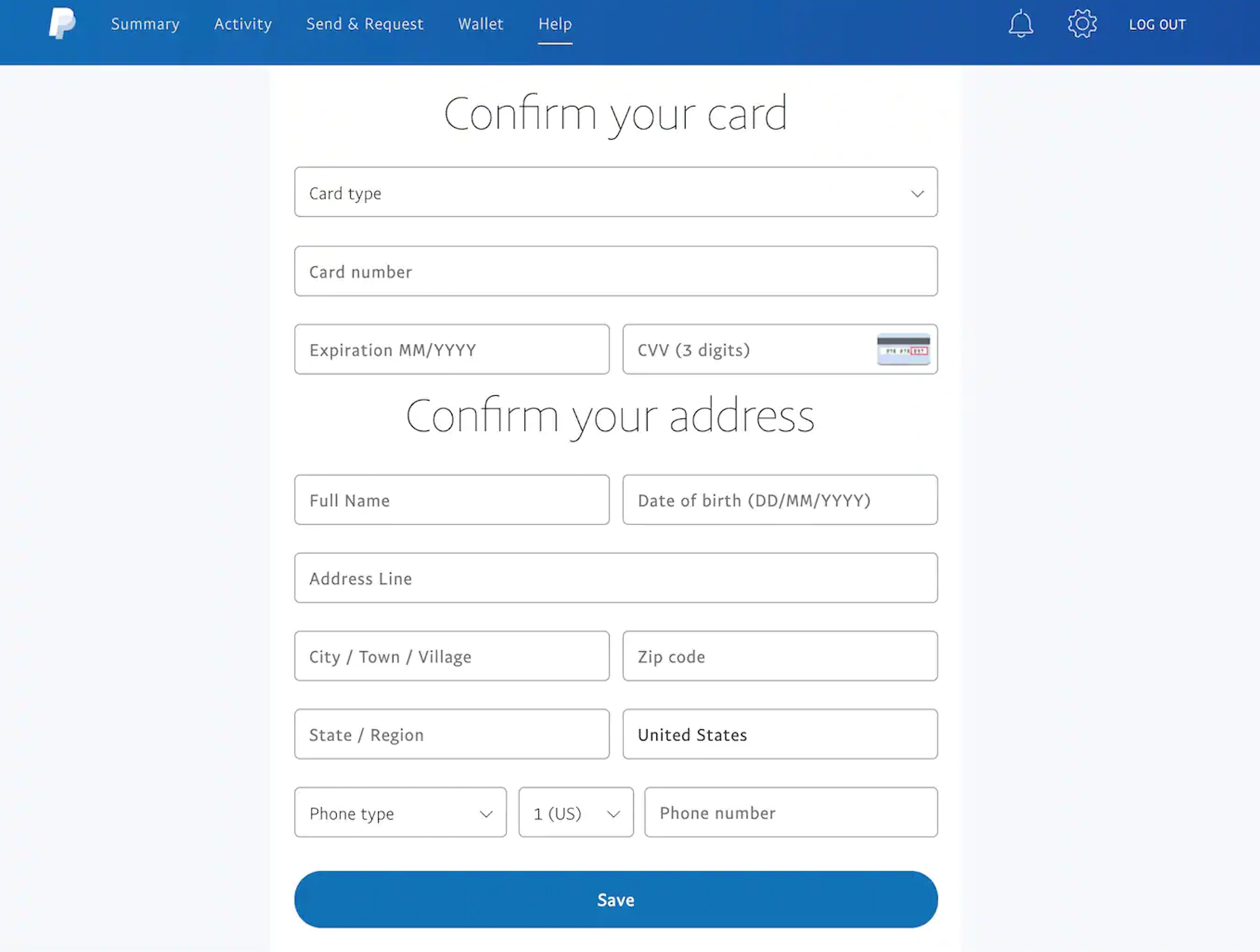
Next, the scammers then ask users for yet more information, specifically their ATM PIN, social security number (SSN), and their mother’s maiden name—a bit of detail that could bypass an additional security layer for an account.

The PayPal phishing site then encourages users to link an email address to their PayPal account, giving the attackers a token, and therefore access, to that email account. It also encourages victims to upload official government documents, such as a passport, driver’s license, or national ID, to secure the account.
Uploading government documents and taking a selfie to verify them is a bigger ballgame for a victim than just losing credit card information — it could be used to create cryptocurrency trading accounts under the victim’s name. These could then be used to launder money, evade taxes, or provide anonymity for other cybercrimes.
~ Akamai Security Research, Akamai
For a verification process for an account showing unusual activity, the amount of information being asked from users is ridiculous and overkill. However, Akamai researchers believe that socially engineering PayPal users to let them keep giving away their data is what makes this phishing kit successful.
“People judge brands and companies on their security measures these days,” said Akamai in the report. “Not only is it commonplace to verify your identity in a multitude of ways, but it’s also an expectation when logging in to sites with ultrasensitive information, such as financial or healthcare companies.”
Phishing, in general, has come a long way. Attackers have been learning from their mistakes thanks to our growing understanding of their tactics and social engineering techniques.
As users of online services, we, too, have an obligation over our own online security and privacy. And the only way one can tell apart two seemingly identical websites is to look at your browser’s address bar.
To rephrase a line: to err is human, to scrutinize URLs is divine.
Stay safe!