File-hosting company Dropbox revealed on Tuesday that it has suffered a phishing incident. Attackers took 130 code repositories using stolen credentials after gaining access to one of Dropbox’s GitHub accounts.
GitHub notified Dropbox after detecting suspicious activity on October 14, a day after the activity began.
Multiple Dropbox employees were targeted by this campaign which started off as an email posing as a message from CircleCI, a code integration and delivery platform. When one of the employees clicked the email link, they were taken to a phishing page where they entered their GitHub username and password.
Affected employees also used their hardware authentication key to input a One-Time Password (OTP) to the malicious site.
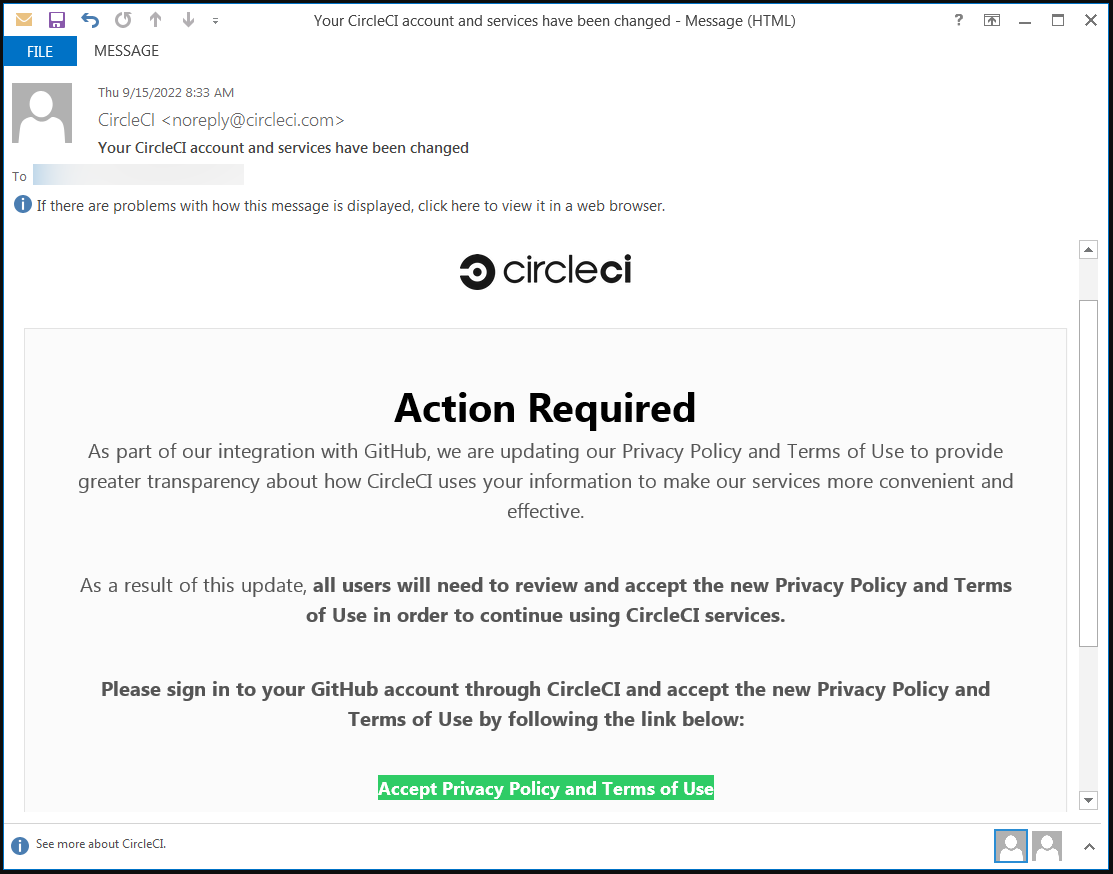
The phishing email was made to look like it came from CircleCI, asking recipients to accept updated Privacy Policy and Terms of Use changes so they can continue to use the company’s services. (Source: BleepingComputer)
In a post about the incident, the Dropbox Security Team said:
“At no point did this threat actor have access to the contents of anyone’s Dropbox account, their password, or their payment information. To date, our investigation has found that the code accessed by this threat actor contained some credentials—primarily, API keys—used by Dropbox developers. The code and the data around it also included a few thousand names and email addresses belonging to Dropbox employees, current and past customers, sales leads, and vendors (for context, Dropbox has more than 700 million registered users).”
Regarding the repositories, Dropbox said the contents included “our own copies of third-party libraries slightly modified for use by Dropbox, internal prototypes, and some tools and configuration files used by the security team.” Code for its core apps or infrastructure was not stored in the repositories, and no content, password, or payment information was accessed.
In response to what happened, Dropbox is said to be going forward with adopting WebAuth, the “gold standard” for a more phishing-resistant multi-factor authentication (MFA), which it was already in the process of doing before the attack.
“Even the most skeptical, vigilant professional can fall prey to a carefully crafted message delivered in the right way at the right time. This is precisely why phishing remains so effective—and why technical controls remain the best protection against these kinds of attacks. As threats grow more sophisticated, the more important these controls become.”
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.










