In 2020, we reported on how law enforcement managed to compromise a secure communications system set up by and for criminals.
Now, Europol has published a progress report showing the enormous impact the infiltration of the encrypted communications tool EncroChat made.
EncroChat, a company based in the Netherlands, advertised its services as safer than safe, stating that no messages were saved on its servers, which were located “offshore.” However, Dutch law enforcement figured out the EncroChat servers were located in France and got to work, hoping to catch criminals in the act. And they did.
The EncroChat system was well organized and had gained a lot of trusting users over the years. Criminals felt secure enough to chat freely about everything: Names of customers, drug deliveries, and even assassinations. And their trust was understandable, given what EncroChat promised to offer:
- Phones were dual boot, so users could alternatively start the Android operating system and their phones would look like a normal, old-fashioned model
- The phones had a “wipe all” button that would delete all the stored conversations in case of an arrest or other emergency
- No messages were stored on servers so they could not be seized and decrypted later
- The service used OTR which is a cryptographic protocol that provides both authentication and end-to-end encryption for instant messaging. This protocol ensures that session keys will not be compromised even if the private key of the server is compromised. Even when a server is seized, the conversations cannot be decrypted or lead back to the participants
EncroChat users paid hefty fees for this service— thousands of dollars per year, per device. The exorbitant fees may explain why the majority of the EncroChat clientele could be found on the wrong side of the law. Other parties that might have a vested interest in keeping their chat messages secret include government parties, journalists, security professionals, or lawyers. However, there are cheaper, if somewhat less sophisticated, alternatives for legitimate secret-keeping that law enforcement does not target.
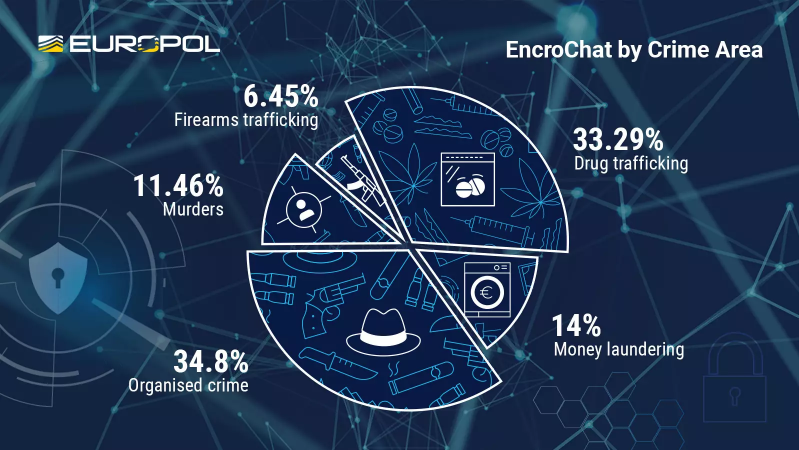
According to Europol, most EncroChat users were either members of organized crime, or performed drug trafficking. The rest engaged in money laundering, assassinations, and firearms trafficking.
Three years later the harvest of the operation stands at:
- 6,558 suspects arrested, including 197 high value targets
- 7,134 years of imprisonment of convicted criminals up to now
- EUR 739.7 million in cash seized
- EUR 154.1 million frozen in assets or bank accounts
- 30.5 million pills of chemical drugs seized
- 103.5 tonnes of cocaine seized
- 163.4 tonnes of cannabis seized
- 3.3 tonnes of heroin seized
- 971 vehicles seized
- 271 estates or homes seized
- 923 weapons seized, as well as 21,750 rounds of ammunition and 68 explosives
- 83 boats and 40 planes seized
All this was possible thanks to the analysis of 115 million conversations between the roughly 60,000 users of the EncroChat platform.
Similar operations like the one against Sky ECC, and a fake secure chat service set up by the Federal Bureau of Investigation (FBI) and the Australian Federal Police (AFP) called AN0M, have shown that despite being unable to break secure encryption, law enforcement agencies have found ways to eavesdrop on the criminals that feel safe using them.
We don’t just report on encryption—we offer you the option to use it.
Privacy risks should never spread beyond a headline. Keep your online privacy yours by using Malwarebytes Privacy VPN.











