This blog post was authored by Jérôme Segura
In recent years, tech support scammers have become very familiar with the mechanics of malvertising to generate large amounts of traffic towards their landing pages. Interestingly, over time a sort of desensitization related to these campaigns appears to have taken place, in particular among publishers and ad networks. Yet, these scams are far more dangerous than they once were as the rogue tech support agents no longer simply push bogus support service for a fee but are actively hacking into their victims’ bank accounts.
A few days ago, we received a tip from a computer technician working at a local shop who told us they saw a new tech support scam hosted on Amazon’s AWS. Upon investigating, we realized this was part of a big typosquatting campaign that started roughly a month ago. People often make mistakes when typing a website name and that can result in some unfortunate consequences.
In this blog we share the technical details behind this latest wave of malvertising and tech support scams.
Typosquatting 101
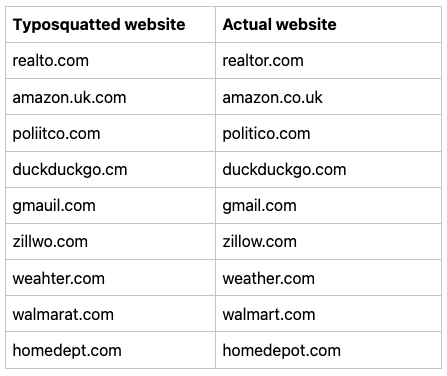
Typosquatting is an old technique where unscrupulous individuals register websites that are lexically close to legitimate ones, preying on victims to make a typo and land on them. Sometimes typosquatting is used for phishing purposes but most usually what we see is malvertising. The victim is bounced through a series of redirects eventually leading to malicious advertisements.
Here are some real examples of website names that were mistyped and subsequently hijacked:
This is how it works in practice:
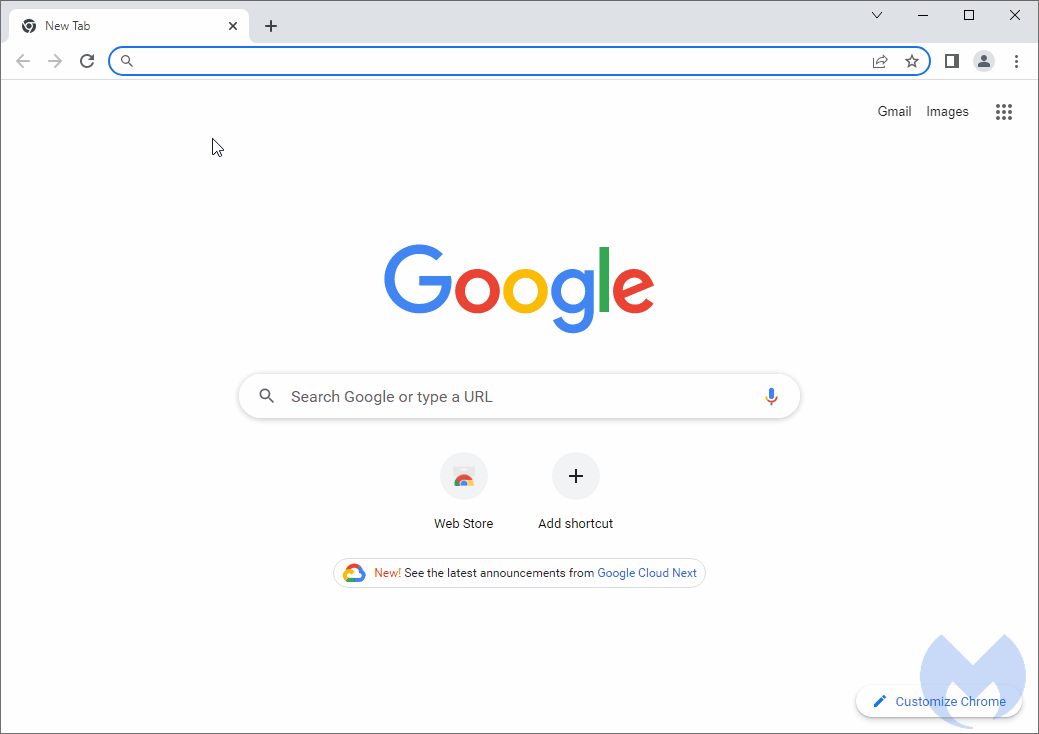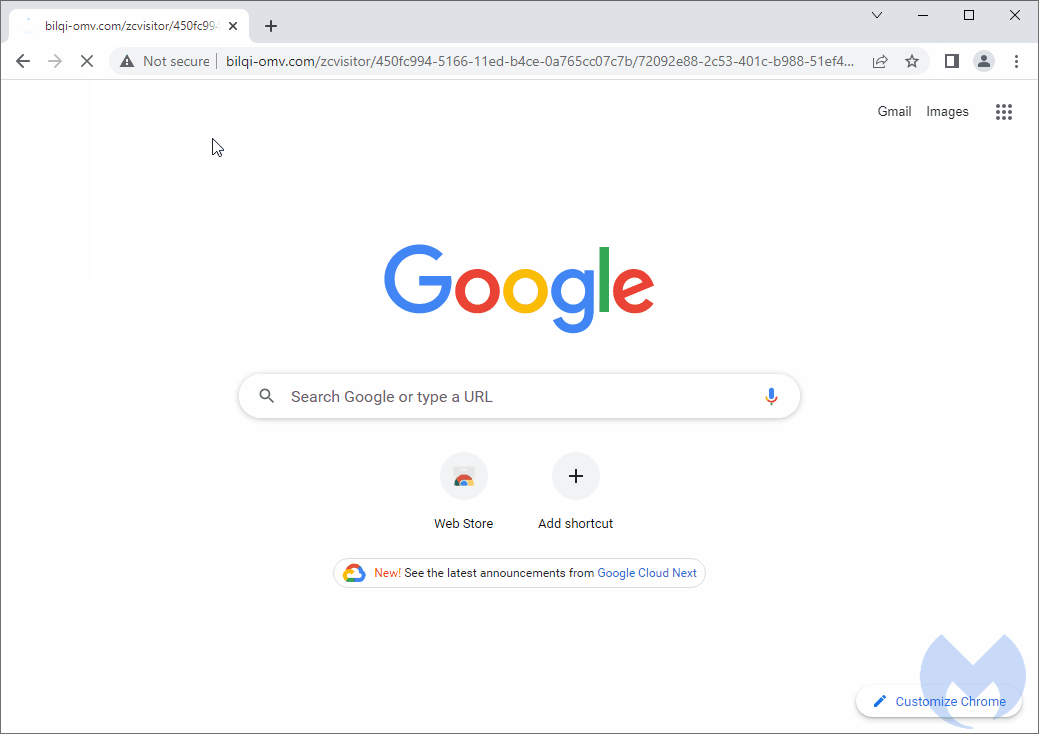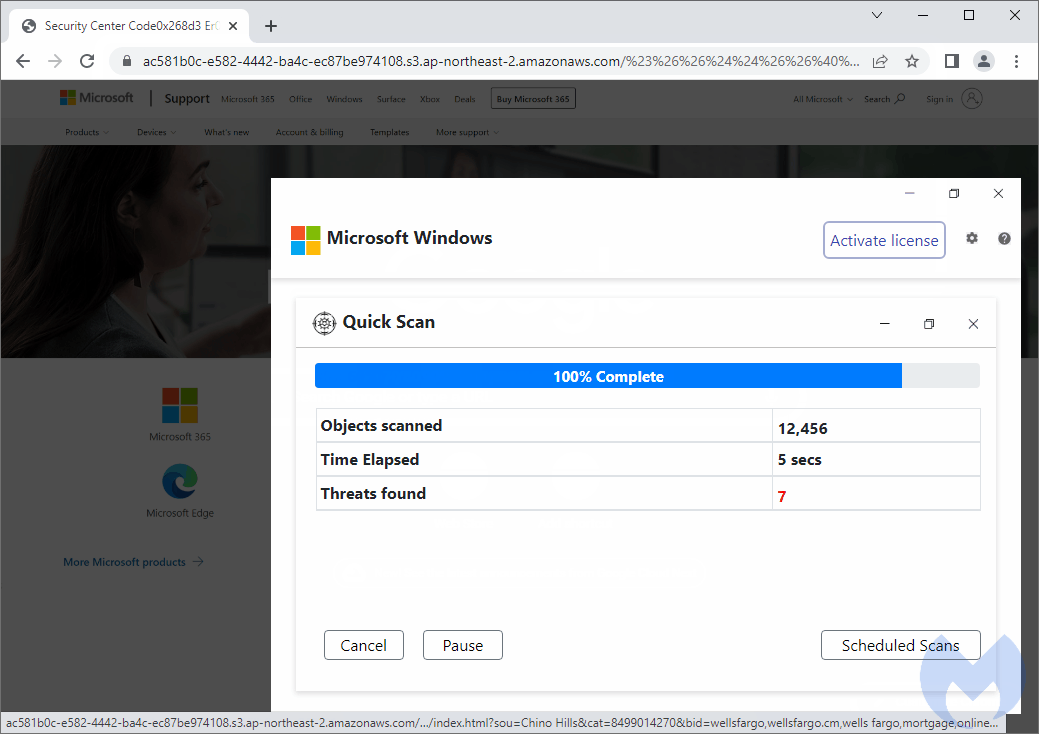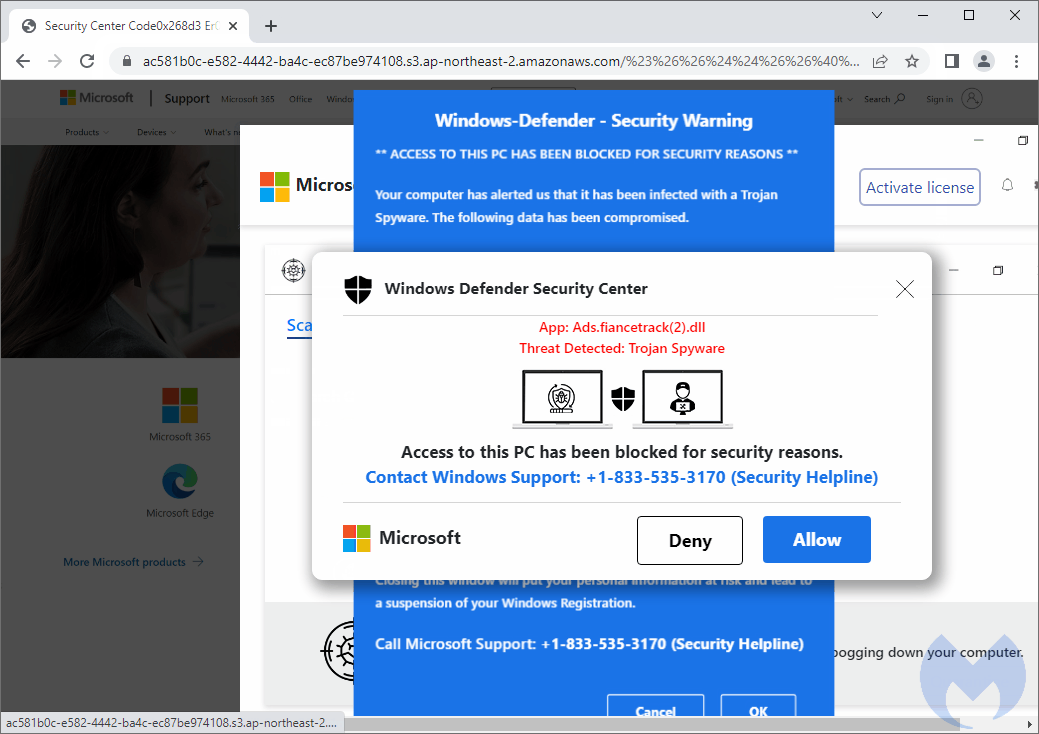
Some brands proactively register domain names that are close in order to prevent this kind of abuse, but there are too many possible variations to account for them all. A copycat page may be parked and contain ads or may be set up in a way that redirects traffic according to the victim’s profile via a series of affiliate networks.
Redirection infrastructure
This particular campaign is only targeting the US and has specific patterns that make it easily identifiable:
- It starts when someone makes a mistake in typing the website they want to visit
- A number of ad networks then process the traffic according to a number of parameters
- A malicious actor is bidding on certain queries, in this case typos for popular brands
- The ad network redirects the visitor to the domain controlled by the malicious actor (malvertising)
- Further profiling is applied to ignore bots, VPNs, unwanted geolocation
- The victim is sent to a temporary (and disposable) webpage on Amazon’s AWS showing a fake alert
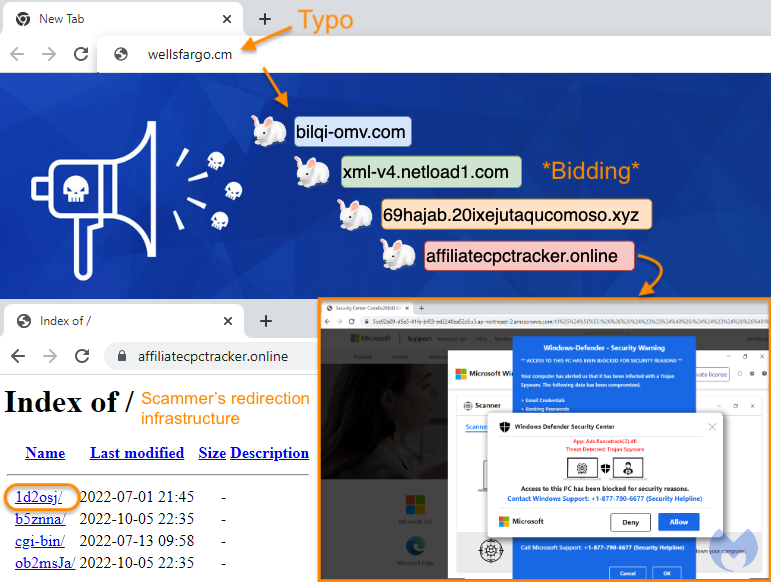
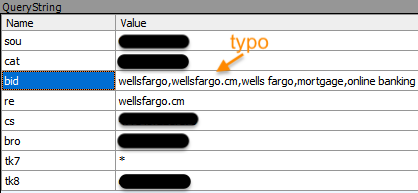
Here’s more detailed information about the bidding and in particular we see a keyword for the user’s typo (wellsfargo.cm):
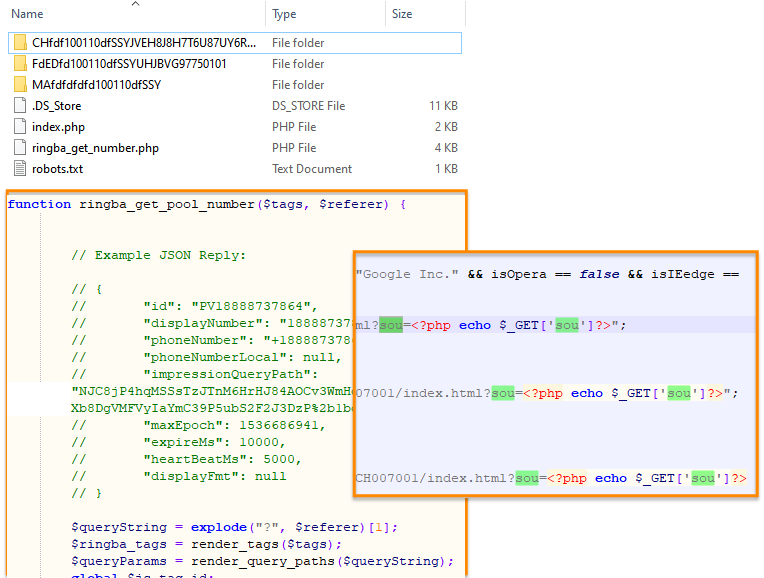
The hosting server for affiliatecpctracker[.]online (162.241.114.43) has a lot of historical data associated with it and shows previous scam pages going as far back as 3 years ago. We were able to find numerous artifacts related to the browser locker pages such as HTML source code and some backend PHP scripts that are used to generate the phone numbers.
Avoiding typo scams
Obviously, it is a human behavior to make typos and that is not something we can really avoid. However, here are some tips:
- bookmark the sites you frequently visit so you don’t have to type them
- use some kind of browser and ad protection tool (i.e. the free Malwarebytes Browser Guard extension)
- don’t panic: that scary popup will not harm your computer, you can safely close it
Scammers love malvertising and will continue to abuse anything that they can to get more and more victims to call their toll-free numbers. The end game is to defraud innocent people and sometimes hacking into their bank account to wire large amounts of money. As famous Youtuber @scammerpayback would say, “don’t get scammed!”.










