Short bio
Point-of-sale (POS) malware is software specifically created to steal customer data, particularly from electronic payment cards like debit and credit cards and from POS machines in retail stores. It does this by scraping the temporarily unencrypted card data from the POS’s memory (RAM), writing it to a text file, and then either sending it to an off-site server at a later date or retrieving it remotely. It is believed that criminals behind the proliferation of this type of malware are mainly after data they can sell, not for their own personal use. Although deemed as less sophisticated than your average PC banking Trojan, POS malware can still greatly affect not just card users but also merchants that unknowingly use affected terminals, as they may find themselves caught in a legal mess that could damage their reputation.
POS malware may come in three types: keyloggers, memory dumpers, and network sniffers.
History
The first known POS memory scraper is RawPOS, which was found sometime in 2008. It is said to be technically simple, but can still affect modern-day card processing terminals. In April 2015, a variant of this malware surfaced, targeting devices in casinos and resort hotels in the United States, Canada, Europe, the Middle East, and Latin America.
While the industry currently detects more than 15 kinds of POS malware, no two are alike. Several of these are predecessors to new known POS malware variants. For example, Alina (aka Track), which surfaced in late 2012, is succeeded by JackPOS, which surfaced in early 2014. The Dexter variant the industry found after Alina surfaced has been succeeded by Soraya and LusyPOS. Modern-day memory scraping malware is found to be more sophisticated compared to their predecessors. Using the previous examples, Soraya is found to have the capabilities of a known banking Trojan called Zeus, while LusyPOS can communicate back to its command and control (C&C) server using Tor, a popular anonymity tool.
2014 was dubbed by industry experts as the “Year of the Largest Retail Hacks” thanks to POS malware.
Common infection method
There are two typical ways POS malware can be installed in machines capable of reading card data. First, it could be an inside job. This means that someone working in the store who has active knowledge of how the payment processing is set up can manually install the malware to target machines. Data scraped by variants that are not hooked up to a network are retrieved or accessed remotely.
Second, POS malware can be installed via social engineering or phishing lures, especially for targeted attack campaigns. It has been noted that tactics employing these come with files bearing misleading names, such as java.exe and adobeflash.exe. Such malware is known to be highly customized to fit or blend in with files associated with the target organization. Once installed, affected machines are connected to a POS botnet that reports back to a centralized C&C server.
Associated families
Here are some of the POS malware families we know of to date:
- Alina
- Backoff
- BlackPOS
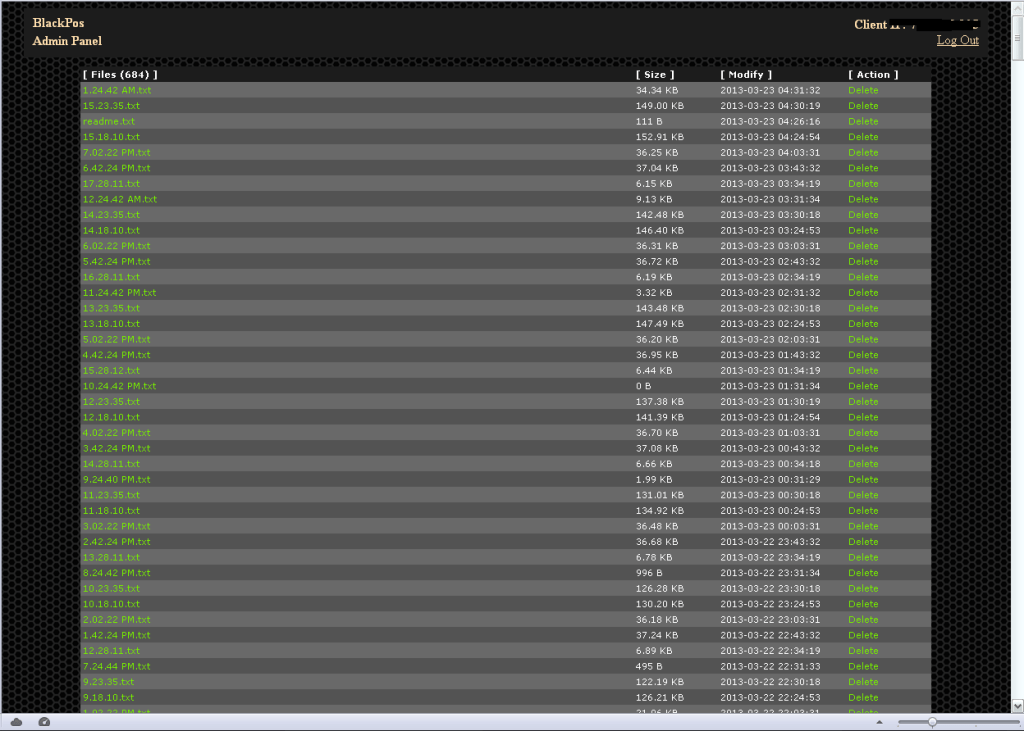
- BlackPOS version 2
- BrutPOS
- ChewBacca
- Citadel
- Decebal
- Dexter
- Dump Memory Grabber
- GetMyPass
- JackPOS
- LogPOS
- LusyPOS
- NewPoSThings
- POSCardStealer
- PwnPOS
- Rdasrv
- Soraya
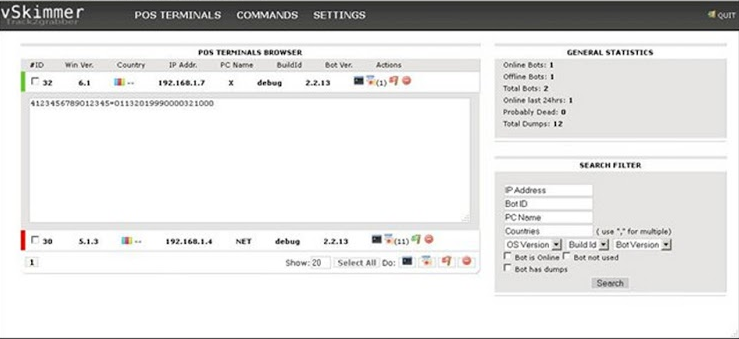
- VSkimmer
Remediation
Businesses that are unknowingly using affected POS machines must first of all contain the infection by disconnecting from the network and then conduct an audit to determine which terminals are infected and which ones are not. Affected POS systems are to be isolated and cleaned using anti-malware software. Once cleaned, businesses must identify the root cause of the infection and create compliance rules to prevent such an occurrence in the future. Staff hiring based on integrity plus properly training staff on fraud tactics can be beneficial for businesses.
Aftermath
Big and small merchants that process debit and credit card transactions may find themselves in a pinch—worse, in court—if consumers have identified that their POS systems may be infected with malware and the merchants didn’t have ample security measures in place.
Avoidance
POS malware can be avoided if businesses have properly trained their staff to spot and correctly address social engineering lures that may allow such files to enter the business’ payment system. Introducing third-party devices to terminals and installing programs on systems connected to the network, such as browsers and games, must also be strictly prohibited.
Screenshots