Short bio
A computer worm is a type of Trojan that is capable of propagating or replicating itself from one system to another. It can do this in a number of ways. Unlike viruses, worms don’t need a host file to latch onto. After arriving and executing on a target system, it can do a number of malicious tasks, such as dropping other malware, copying itself onto devices physically attached to the affected system, deleting files, and consuming bandwidth.
History
Robert Tappan Morris, a computer science student from Cornell University, created the first known worm and unleashed it in November 1988. Now known as the Morris worm, it was initially designed to count the number of computers connected to a network. However, the worm exhibited unwanted side effects.
The term “worm” actually originated from a fictional novel entitled The Shockwave Rider, which was written by John Brunner in 1975. In the novel, this worm is capable of gathering data, suggesting that it’s acting more like an information stealer than a self-replicating program.
Common infection method
Worms can spread themselves in a number of ways:
- Via software vulnerabilities. Some worm variants look for security holes on systems via installed unpatched software. Once a hole is detected, it infiltrates that system, and then it performs its malicious duties.
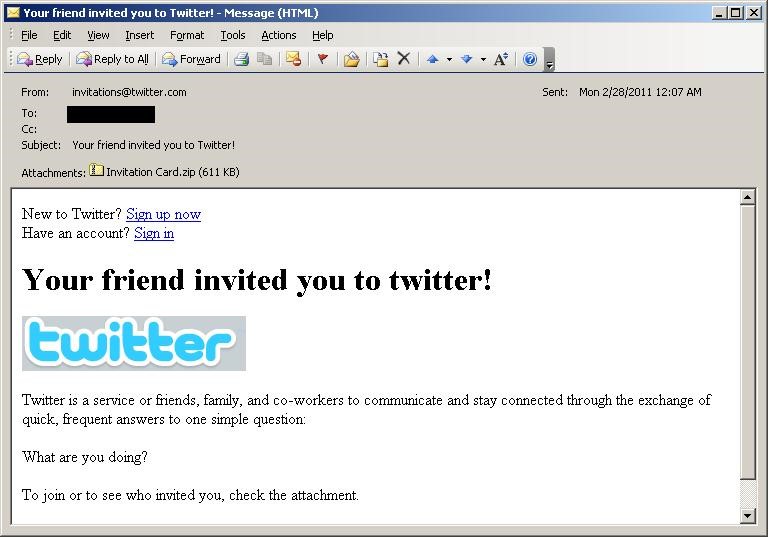
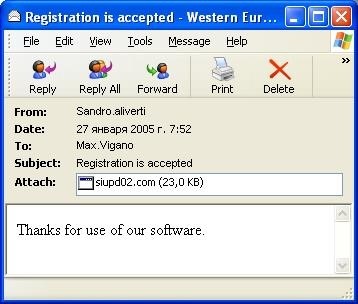
- Via email. Some worm variants can drop other malware, such as backdoors. This payload transforms the affected system into a zombie/bot machine and connects it to a botnet. These machines are capable of spamming messages to random or targeted recipients, with the worm file as its attachment. Spam mail sent usually involve some social engineering tactics for greater chances of infection.
- Via external devices. Some worm variants can copy themselves onto devices, such as USB sticks and external hard drives, which are attached to an already affected system. This way, systems where these devices can be connected to will be affected as well.
- Via peer-to-peer (P2P) file sharing networks. Some Internet users have been known to use P2P applications like eMule and Kazaa to share files with friends and family. However, such an activity is exploited by worms. Worms in P2P file networks have been difficult to detect.
- Via social networks. Some worm variants have propagated within known social sites. For example, MySpace has been affected by an XSS-type worm.
- Via compromised sites. Compromised sites may harbor certain variants of worms that are capable of looking for security holes.
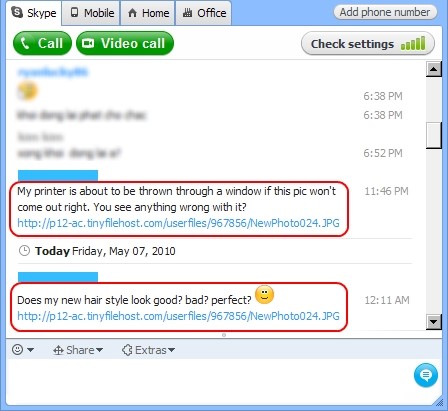
- Via instant messengers (IMs) networks. This is another popular method used by worms. Not only can it spread copies of itself via text messages, IMs can also be used to spread this malware via its P2P sharing capabilities. This method tend to spread worms a lot quicker.
Associated families
From the late 20th century to the early 21st century, worms have been one of the most notorious pieces of software that is found in user systems. Although this type of malware is not as prominent a threat on the Internet as it was before, it remains one of the most dangerous. Below is a short list of reputable and prolific worm families that have caused havoc and is now part of computing history:
- Bagle (aka Beagle, Mitglieder, Lodeight)
- Blaster (aka MSBlast, Lovesan, Lovsan)
- Conficker (aka Downup, Downadup, Kido)
- Duqu
- Flame
- ILOVEYOU (aka Love Letter)
- Mydoom (aka W32.MyDoom@mm, Novarg, Mimail.R, Shimgapi
- Netsky
- Nimda
- Samy
- Sasser
- SQL Slammer
- Storm
- Stration (aka Stratio, Warezov)
- Stuxnet
Remediation
Running antivirus and/or anti-malware software usually cleans up affected systems automatically. It is also advisable to call legitimate computer technical support services should one encounter complications or the worm is highly sophisticated and needs additional steps to cleaning the system.
Aftermath
The aftermath of a worm infection is dependent of the variant itself and its payload(s). Here are just some notable side effects observed on affected systems:
- Further infection from other malware types
- Affected system may become part of a botnet due to other malware infection, such as backdoors
- Some highly sophisticated worm variants are capable of stopping or crashing the affected systems. This happened to the nuclear centrifuges at Iran before the Stuxnet worm was discovered.
- Systems slow down.
- Defenses on the system are disabled, including Safe Mode.
- Files are missing from the affected system, causing it to not operate or function normally.
- Systems are compromised, opening them for spying by bad actors and other malicious activities.
Avoidance
Prevention is best when it comes to dealing with malware like worms. Here are practical ways one can avoid getting affected by worms:
- Download and install an antivirus or anti-malware software, if you haven’t already. The majority of worms are detected by these software.
- Keep you OS and other software installed on your system updated.
- Make sure that all firewalls on your system and router(s) are always enabled. Also, configure your firewall to make it more secure.
- Restrict access to computer users also helps by not giving administrator access to every user of a computer device.
- Disable JavaScript (JS) on your browser(s).
- Exercise basic computer security 101 protocols. For example, not clicking links or opening attachments on emails without verifying from the senders that they legitimately sent those messages.
Screenshots
Previous