Short bio
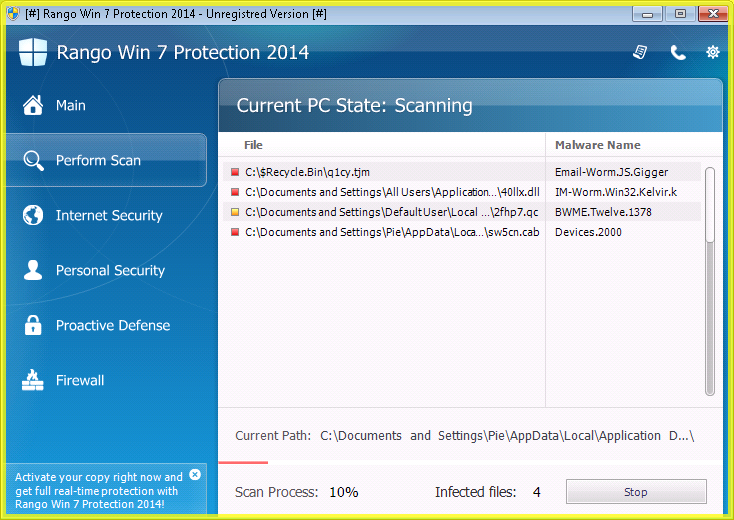
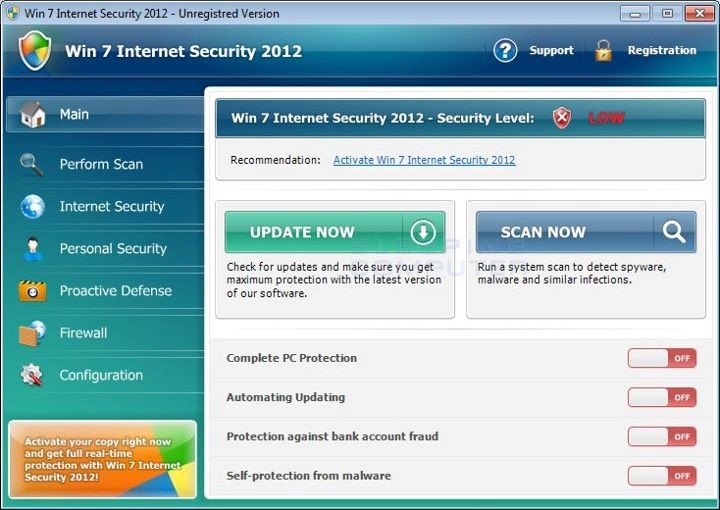
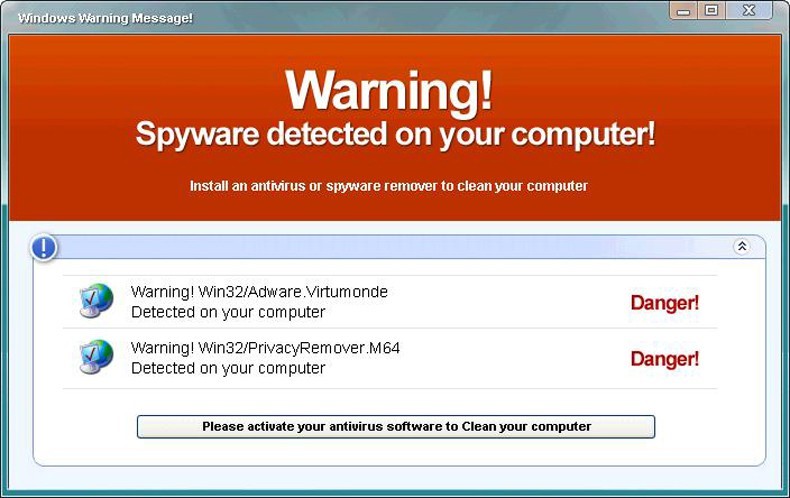
Rogue scanners, also known as fake scanners, fake AV, or rogueware, are pieces of code injected into legitimate sites or housed in fake sites. Their social engineering tactic normally involve displaying fictitious security scan results, threat notices, and other deceptive tactics in an effort to manipulate users into purchasing fake security software or licenses in order to remove potential threats that have supposedly infected their systems. Their warnings were deliberately crafted to closely resemble interfaces of legitimate AV or anti-malware software, further increasing the likelihood that users who see them will fall for the ploy. These malware can target and affect PCs and Mac systems alike. In 2011, known names in the security industry have noted the dramatic decline of rogue scanners, both in detection of new variants and search engine results for their solutions.
Rogueware is one of two main classes of scareware. The other is ransomware. Rogue scanners are not as apparent as they used to be several years ago. It is believed that ransomware has completely replaced rogue scanners altogether.
History
The history of rogue scanners is quite murky; however, the first noted application deemed as fake AV is Spy Wiper, which surfaced in November of 2003. It was deemed a super rogue, as it was capable of modifying some of the affected system’s browser settings, bombarding users with pop-up ads, and tracking computer usage—tactics that may have been occurring less during those time.
The advent of rogue scanners may have also been the budding years of miscreants monetizing on un-savvy end users.
Common infection method
Rogue scanners are often distributed via affiliate networks known to supply other malware types like Trojan kits. Social engineering tactics are then used to get users to download them onto user systems. Online criminals behind such malware campaigns are also known to use three known vectors of infection: Black Hat SEO (BHSEO), malvertising, and spam campaigns.
During a BHSEO campaign, pages housing rogue scanners are promoted to higher ranks in search engine results due to them being full of popular keywords. These keywords are derived from services that display hot topics in near real-time results. Criminals can program PHP scripts to retrieve those keywords and use them in creating infected webpages. Some malicious results can be images.
Legitimate websites that may not be compromised can also be used by criminals to drop their rogue scanners via third-party advertising. In this case, advertisers are compromised to redirect users to rogue scanner downloads once users click ads appearing on these legitimate sites. This is basic malvertising as we know it today.
Lastly, spam campaigns are probably the oldest vector among the three. Rogue scanners can be attached to email or included in the message body as a link, resulting in a drive-by download after user clicks it. Usually when a drive-by download happens, users are unaware that malware is already being introduced to their system. Some known email types that harbor rogue scanners are those that pretend to be regular, daily emails, such as supposed parcel deliveries and tax documents.
Associated families
To date, there are hundreds of rogue scanner variants that have been found and detected during its six-year reign from 2008 to 2014. For the sake of brevity, we have only noted three of the most-prevalent and interesting families that have plagued users:
- WinWebSec: This is a rogue scanner family that uses misleading alerts that mimic logos and interface designs from known companies, particularly Microsoft. Examples of some names are Live Security Platinum, Smart Protection, and Win XP Security System. In 2009, some variants of WinWebSec were found to drop malware that allow affected systems to be part of a botnet.
- Chameleon (FakeRean): This is a rogue scanner family that is found to drop variants of notorious worm families like Bredolab for its payload after successfully infiltrating user systems.
- FakeScanti: This is a sophisticated rogue scanner family that acts like a spyware. It arrives on systems via software vulnerabilities. Sometimes, it’s bundled with Trojan rootkits. Another payload for this family is the displaying of unwanted advertisements.
Remediation
If end users find their systems affected with rogue scanners/fake AV, it is important that they refrain from paying for software advertised or pushed by the malware. Instead, users must retrieve a copy of legitimate AV software from a clean system and introduce it to the affected systems via a USB stick or other third-party means. The AV software can be manually installed and run onto the affected system. As a result, any dropped files and registry modifications made by the malware are removed.
Aftermath
Once a system is infected with a rogue scanner or fake AV, the program may perform the following actions:
- Displaying prompts of either purported system infection or pornography
- Displaying animations of purported system crashes and reboots
- Disabling some features of the affected system in order to prevent the user from uninstalling the malware, to prevent security software from running, to disable certain updates, and to block certain online sites from getting accessed, consequently leaving the affected system open for other possible infection
- Modifying system registries and settings
- Enticing users into purchasing their product and then claiming that a portion of the sales will be given to charity. The Green rogue scanner does this.
- Employing general scareware tactics, offering urgent computer fixes and housekeeping, and popping up security alerts similar to actual system notices in order to scare users
Avoidance
Thankfully, most sites introduced with rogue scanner code are benign once users visit them. As such, users who have discerned the fake prompts can simply close the browser tab of the site they visited. They don’t have to click anything on the affected page.
The criminals behind rogue scanners/fake AV heavily rely on users’ unfamiliarity with legitimate software. As such, it is essential that users acquaint themselves with old and new tactics of rogue malware as well as differentiate between legitimate software and non-legitimate ones.
Screenshots