Short bio
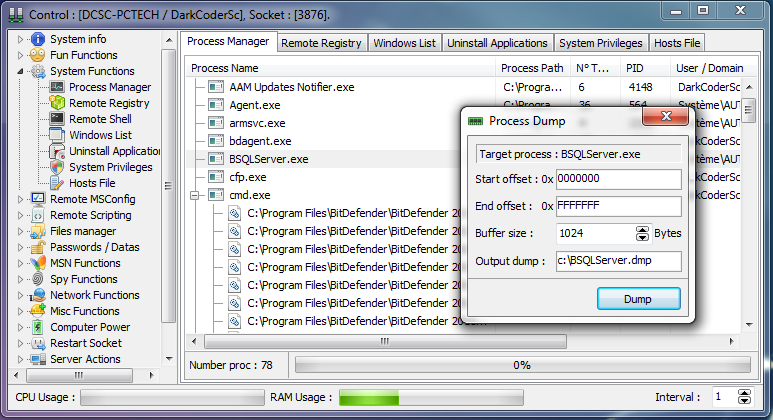
Remote Access Trojans are programs that provide the capability to allow covert surveillance or the ability to gain unauthorized access to a victim PC. Remote Access Trojans often mimic similar behaviors of keylogger applications by allowing the automated collection of keystrokes, usernames, passwords, screenshots, browser history, emails, chat lots, etc. Remote Access Trojans differ from keyloggers in that they provide the capability for an attacker to gain unauthorized remote access to the victim machine via specially configured communication protocols which are set up upon initial infection of the victim computer. This backdoor into the victim machine can allow an attacker unfettered access, including the ability to monitor user behavior, change computer settings, browse and copy files, utilize the bandwidth (Internet connection) for possible criminal activity, access connected systems, and more.
History
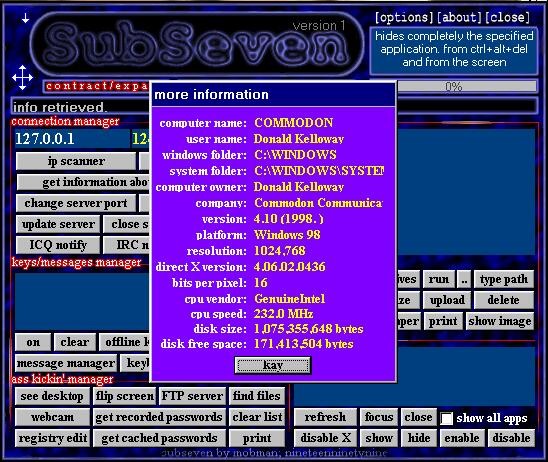
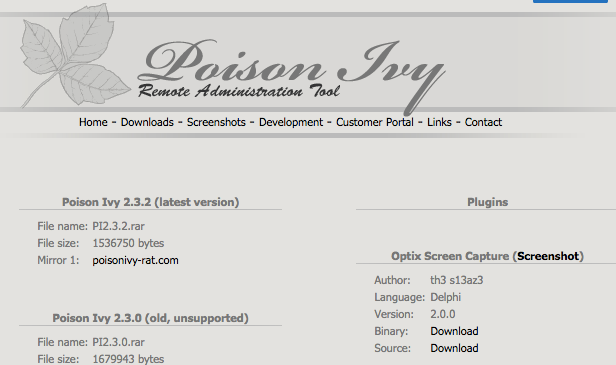
While the full history of Remote Access Trojans is unknown, these applications have been in use for a number of years to help attackers establish a foothold onto a victim PC. Well-known and long established Remote Access Trojans include the SubSeven, Back Orifice, and Poison-Ivy applications. These programs date to the mid to late 1990s and can still be seen in use to this day.
The successful utilization of such applications led to a number of different applications being produced in the subsequent decades. As security companies become aware of the tactics being utilized by Remote Access Trojans, malware authors are continually evolving their products to try and thwart the newest detection mechanisms.
Common infection method
Remote Access Trojans can be installed in a number of methods or techniques, and will be similar to other malware infection vectors. Specially crafted email attachments, web-links, download packages, or .torrent files could be used as a mechanism for installation of the software. Targeted attacks by a motivated attacker may deceive desired targets into installing such software via social engineering tactics, or even via temporary physical access of the desired computer.
Associated families
There are a large number of Remote Access Trojans. Some are more well-known than others. SubSeven, Back Orifice, ProRat, Turkojan, and Poison-Ivy are established programs. Others, such as CyberGate, DarkComet, Optix, Shark, and VorteX Rat have a smaller distribution and utilization. This is just a small number of known Remote Access Trojans, and a full list would be quite extensive, and would be continually growing.
Remediation
Remote Access Trojans are covert by nature and may utilize a randomized filename/path structure to try to prevent identification of the software. Installing and running Malwarebytes Anti-Malware and Malwarebytes Anti-Exploit will help mitigate any potential infection by removing associated files and registry modifications, and/or preventing the initial infection vector from allowing the system to be compromised.
Aftermath
Remote Access Trojans have the potential to collect vast amounts of information against users of an infected machine. If Remote Access Trojan programs are found on a system, it should be assumed that any personal information (which has been accessed on the infected machine) has been compromised. Users should immediately update all usernames and passwords from a clean computer, and notify the appropriate administrator of the system of the potential compromise. Monitor credit reports and bank statements carefully over the following months to spot any suspicious activity to financial accounts.
Avoidance
As in all cases, never click email or website links from unknown locations or install software at the urging of unknown parties. Using a reputable antivirus and anti-malware solution will help to ensure Remote Access Trojans are unable to properly function, and will assist in mitigating any collection of data. Always lock public computers when not in use, and be wary of emails or telephone calls asking to install an application.
Screenshots
Previous