Adware.Elex
Short bio
Adware.Elex is Malwarebytes’ generic detection name for a large family of Windows-oriented adwareof Chinese origin.
Symptoms
Once executed, Adware.Elex displays ads by injecting them into visited sites and pops up browser windows.
Type and source of infection
Adware.Elex arrives on a system as a file downloaded from the Internet. Sometimes it disguises itself as a tool that can detect and remove adware. At times, it hides under the guise of an Adobe Flash or Java update. Adware.Elex can also be dropped by Trojan.Elexwhich has been known to use rootkits.
Protection
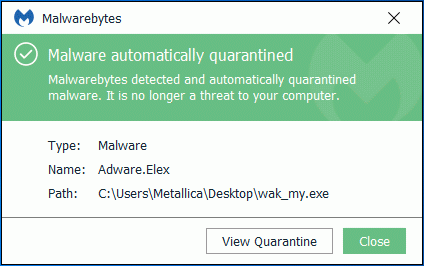
Malwarebytes blocks Adware.Elex
Home remediation
Malwarebytes can detect and remove Adware.Elex without further user interaction.
- Please download Malwarebytesto your desktop.
- Double-click MBSetup.exeand follow the prompts to install the program.
- When your Malwarebytes for Windowsinstallation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantineto remove the found threats.
- Reboot the system if prompted to complete the removal process.
Business remediation
How to remove Adware.Elex with the Malwarebytes Nebula console
You can use the Malwarebytes Anti-Malware Nebula console to scan endpoints.

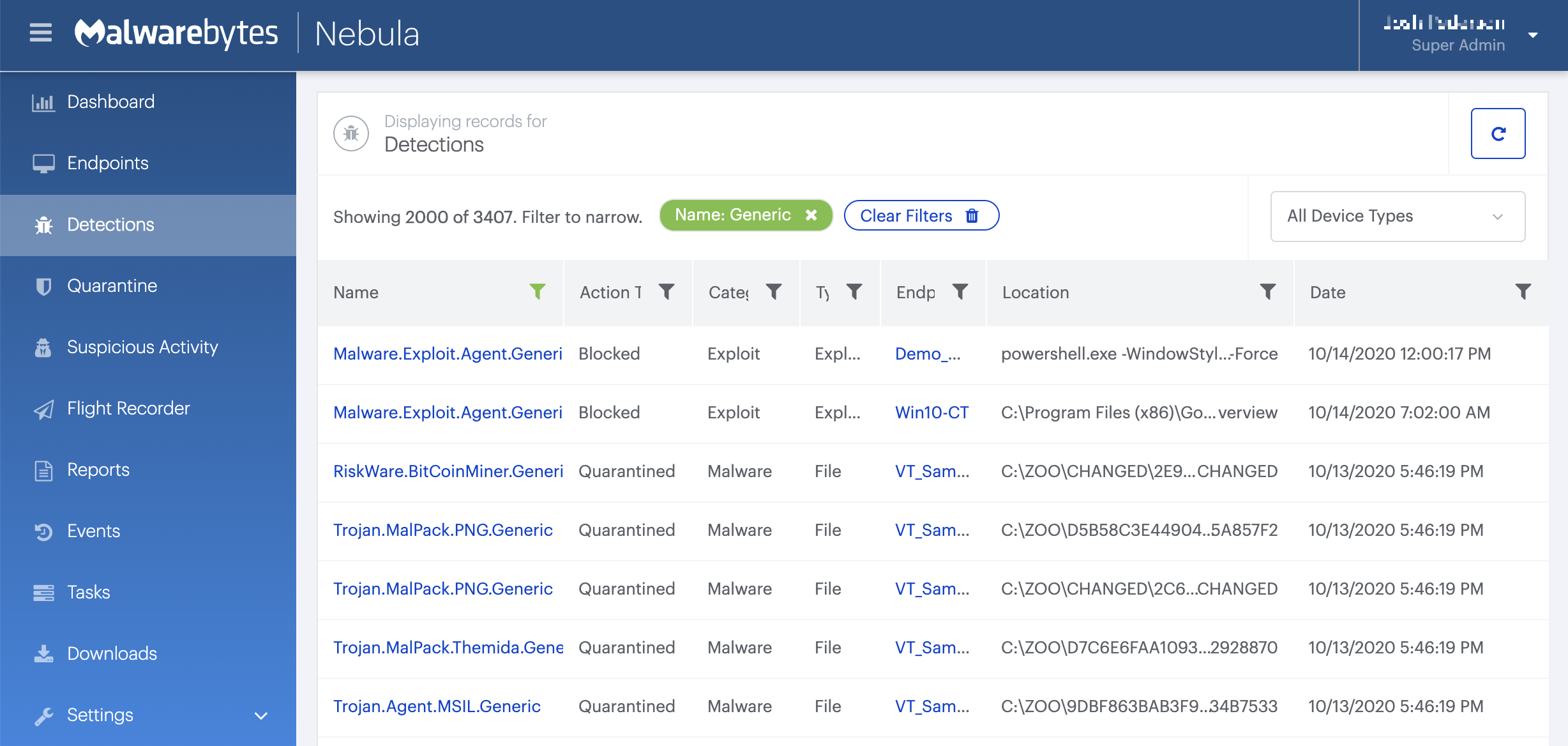
Nebula endpoint tasks menu
Choose the Scan + Quarantine option. Afterwards you can check the Detections pageto see which threats were found.
On the Quarantine pageyou can see which threats were quarantined and restore them if necessary.
Malwarebytes removal log
An example Malwarebytes log for a member of this family called Youndoo:
Malwarebyteswww.malwarebytes.com-Log Details-Scan Date:2/20/17Scan Time:2:10PMLogfile:mbamYoundoo.txtAdministrator:Yes-Software Information-Version:3.0.6.1469Components Version:1.0.50Update Package Version:1.0.1307License:Premium-System Information-OS:Windows 10CPU:x64File System:NTFSUser:{computername}\{username}-Scan Summary-Scan Type:Threat ScanResult:CompletedObjects Scanned:420585Time Elapsed:8min,58sec-Scan Options-Memory:EnabledStartup:EnabledFilesystem:EnabledArchives:EnabledRootkits:DisabledHeuristics:EnabledPUP:EnabledPUM:Enabled-Scan Details-Process:0(Nomalicious items detected)Module:0(Nomalicious items detected)Registry Key:4Adware.Elex.Generic,HKLM\SOFTWARE\CLASSES\CLSID\{5AD340E8-F445-11E6-B566-64006A5CFC23},Delete-on-Reboot,[2155],[356410],1.0.1307Adware.Elex.Generic,HKLM\SOFTWARE\CLASSES\CLSID\{5AD340E8-F445-11E6-B566-64006A5CFC23}\InprocServer32,Delete-on-Reboot,[2155],[356410],1.0.1307PUP.Optional.Youndoo,HKLM\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\UNINSTALL\{92C91B86-B20E-474B-A1D9-6B7D5AC229C4},Delete-on-Reboot,[767],[182916],1.0.1307PUP.Optional.Youndoo,HKLM\SOFTWARE\WOW6432NODE\youndooSoftware,Delete-on-Reboot,[767],[182849],1.0.1307Registry Value:4Adware.Elex.Generic,HKLM\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\SHELLEXECUTEHOOKS|{5AD340E8-F445-11E6-B566-64006A5CFC23},Delete-on-Reboot,[2155],[356410],1.0.1307Adware.Elex.SHHKRST,HKLM\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER|ENABLESHELLEXECUTEHOOKS,Delete-on-Reboot,[357],[-1],0.0.0Adware.Elex.SHHKRST,HKLM\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER|ENABLESHELLEXECUTEHOOKS,Delete-on-Reboot,[357],[-1],0.0.0PUP.Optional.Youndoo,HKLM\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\UNINSTALL\{92C91B86-B20E-474B-A1D9-6B7D5AC229C4}|DISPLAYNAME,Delete-on-Reboot,[767],[182916],1.0.1307Registry Data:0(Nomalicious items detected)Data Stream:0(Nomalicious items detected)Folder:3PUP.Optional.FakeFFProfile,C:\Users\{username}\AppData\Roaming\Mozilla\Firefox\naweriweentcofise\Profiles\mhc384j1.default,Delete-on-Reboot,[2786],[363173],1.0.1307PUP.Optional.FakeFFProfile,C:\Users\{username}\AppData\Roaming\Mozilla\Firefox\naweriweentcofise\Profiles,Delete-on-Reboot,[2786],[363173],1.0.1307PUP.Optional.FakeFFProfile,C:\USERS\{username}\APPDATA\ROAMING\Mozilla\Firefox\naweriweentcofise,Delete-on-Reboot,[2786],[363173],1.0.1307File:22PUP.Optional.FakeFFProfile,C:\Users\{username}\AppData\Roaming\Mozilla\Firefox\naweriweentcofise\Profiles\mhc384j1.default\prefs.js,Delete-on-Reboot,[2786],[363173],1.0.1307PUP.Optional.FakeFFProfile,C:\Users\{username}\AppData\Roaming\Mozilla\Firefox\naweriweentcofise\Profiles\mhc384j1.default\profiles.ini,Delete-on-Reboot,[2786],[363173],1.0.1307PUP.Optional.FakeFFProfile,C:\Users\{username}\AppData\Roaming\Mozilla\Firefox\naweriweentcofise\Profiles\mhc384j1.default\search-metadata.json,Delete-on-Reboot,[2786],[363173],1.0.1307PUP.Optional.FakeFFProfile,C:\Users\{username}\AppData\Roaming\Mozilla\Firefox\naweriweentcofise\Profiles\mhc384j1.default\search.json.mozlz4,Delete-on-Reboot,[2786],[363173],1.0.1307Adware.Elex.Generic,C:\PROGRAM FILES (X86)\THULUCH\REUQUTAIN.DLL,Delete-on-Reboot,[2155],[356410],1.0.1307PUP.Optional.Youndoo,C:\USERS\{username}\APPDATA\ROAMING\PROFILES\GHERLUWARDCOOZEIED.DEFAULT\PREFS.JS,Replaced,[767],[324487],1.0.1307PUP.Optional.Youndoo,C:\USERS\{username}\APPDATA\ROAMING\PROFILES\GHERLUWARDCOOZEIED.DEFAULT\PREFS.JS,Replaced,[767],[324487],1.0.1307PUP.Optional.Youndoo,C:\USERS\{username}\APPDATA\ROAMING\PROFILES\GHERLUWARDCOOZEIED.DEFAULT\PREFS.JS,Replaced,[767],[324487],1.0.1307PUP.Optional.Youndoo,C:\USERS\{username}\APPDATA\ROAMING\PROFILES\GHERLUWARDCOOZEIED.DEFAULT\PREFS.JS,Replaced,[767],[324487],1.0.1307PUP.Optional.Youndoo,C:\USERS\{username}\APPDATA\ROAMING\PROFILES\GHERLUWARDCOOZEIED.DEFAULT\PREFS.JS,Replaced,[767],[324487],1.0.1307PUP.Optional.Youndoo,C:\USERS\{username}\APPDATA\ROAMING\PROFILES\GHERLUWARDCOOZEIED.DEFAULT\PREFS.JS,Replaced,[767],[324487],1.0.1307PUP.Optional.Youndoo,C:\USERS\{username}\APPDATA\ROAMING\PROFILES\GHERLUWARDCOOZEIED.DEFAULT\PREFS.JS,Replaced,[767],[324487],1.0.1307PUP.Optional.Youndoo,C:\USERS\{username}\APPDATA\ROAMING\MOZILLA\FIREFOX\PROFILES\MHC384J1.DEFAULT\PREFS.JS,Replaced,[767],[302817],1.0.1307PUP.Optional.Youndoo,C:\USERS\{username}\APPDATA\ROAMING\MOZILLA\FIREFOX\PROFILES\MHC384J1.DEFAULT\PREFS.JS,Replaced,[767],[302817],1.0.1307PUP.Optional.Youndoo,C:\USERS\{username}\APPDATA\ROAMING\MOZILLA\FIREFOX\PROFILES\MHC384J1.DEFAULT\PREFS.JS,Replaced,[767],[302817],1.0.1307PUP.Optional.Youndoo,C:\USERS\{username}\APPDATA\ROAMING\MOZILLA\FIREFOX\PROFILES\MHC384J1.DEFAULT\PREFS.JS,Replaced,[767],[302817],1.0.1307PUP.Optional.Youndoo,C:\USERS\{username}\APPDATA\ROAMING\MOZILLA\FIREFOX\PROFILES\MHC384J1.DEFAULT\PREFS.JS,Replaced,[767],[302817],1.0.1307Adware.Elex,C:\USERS\{username}\DESKTOP\WAK_MY.EXE,Delete-on-Reboot,[305],[363419],1.0.1307PUP.Optional.Youndoo,C:\USERS\{username}\APPDATA\ROAMING\PROFILES\GHERLUWARDCOOZEIED.DEFAULT\SEARCHPLUGINS\JEBNKUVK.XML,Delete-on-Reboot,[767],[324489],1.0.1307Adware.Elex.SHHKRST,C:\PROGRAM FILES (X86)\THULUCH\CRASHREPORT.DLL,Delete-on-Reboot,[357],[372356],1.0.1307Adware.Elex.SHHKRST,C:\WINDOWS\SYSTEM32\TASKS\Gfakdutoing,Delete-on-Reboot,[357],[-1],0.0.0PUP.Optional.Youndoo,C:\USERS\{username}\APPDATA\ROAMING\MOZILLA\FIREFOX\PROFILES\MHC384J1.DEFAULT\SEARCHPLUGINS\JEBNKUVK.XML,Delete-on-Reboot,[767],[302734],1.0.1307Physical Sector:0(Nomalicious items detected)(end)
Traces/IOCs
Domains:istartpageing.comomiga-plus.comyoursites123.comoursearching.comyoursearchweb.comyoundoo.comvi-view.comtohotweb.comwebisawsome.infowebssearches.comv9.comtrotux.comswellsearch.infoso-v.comsearchqu.comsearchtotal.infoqvo6.comqone8.compur-esult.infoortalsepeti.com
Associated threats
- Adware.Elex.ShrtCln





