There has been an interesting battle between two exploit kits in the past few months. Following the demise of the Angler exploit kit in June, Neutrino EK assumed the lead position by having the top malware and malvertising campaigns defaulted to it. But since then, there have been several shake ups, and an underdog in the name of RIG EK replaced Neutrino EK on several high volume attacks from compromised websites.
Today we spotted a malvertising incident on popular website answers.com (2 million visits daily) via the same pattern that was used by Angler EK and subsequently Neutrino EK via the ‘domain shadowing‘ practice and the use of the HTTPS open redirector from Rocket Fuel (rfihub.com). Contributing to its recent expansion, RIG EK was the go-to exploit kit for this campaign.
Some visitors that browsed the knowledge-based website were exposed to the fraudulent and malicious advert and could have been infected without even having to click on it.
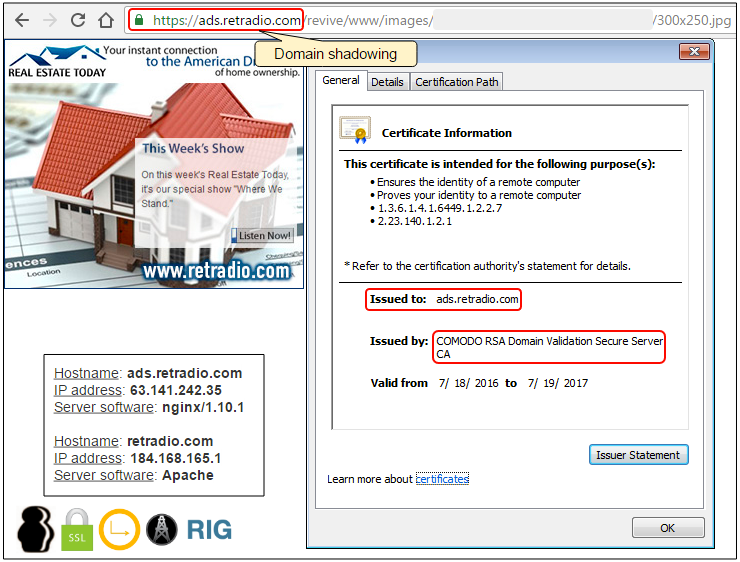
Domain shadowing:
- https://ads.retradio.com/www/delivery/afr.php?id=69151&target=_blank&click=http://r.turn.com/{redacted} -> Referer: http://www.answers.com/Q/What_is_Windows_7_loader
- https://p.rfihub.com/cm?forward=http://speerhaaien.eclouds.co.uk/?wXqBcrWeKB3PAoI=l3SKfPrfJxzFGMSUb-{redacted}
RIG EK, the new Neutrino?
In early September we noticed a change in how RIG drops its malware payload. Rather than using the iexplore.exe process, we spotted instances where wscript.exe was the parent process of the dropped binary.
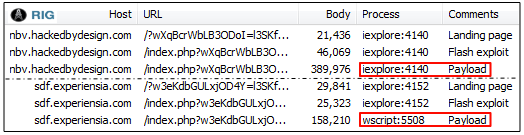
This may seem like a minor difference, but it has been Neutrino’s trademark for a long time and used as a way to bypass certain proxies. Below is a comparison of the script Neutrino EK and RIG EK leverage to download the encoded malware binary.

For the past weeks, RIG EK has been observed dropping the CrypMIC ransomware, a payload that Neutrino first served back in July.
More of the same fake advertisers
Threat actors are privileging RIG over its rival Neutrino as it can be seen from various malware campaigns. In the meantime, domain shadowing in the malvertising space is still an effective means of duping ad agencies via social engineering. While this practice is well known, it also remains a powerful method to bypass traditional defences at the gateway by wrapping the ad traffic (and malicious code) in an encrypted tunnel.
Since malvertising does not require any user interaction to infect your system, you should keep your computer fully up to date and uninstall unnecessary programs. Running an additional layer of protection, such as exploit mitigation software, ensures that drive-by download attacks leveraging zero-day vulnerabilities are also stopped.
Further reading:
Indicators of compromise:- ads.retradio.com
- 63.141.242.35










