Correction, 5/22/19: Previously, we incorrectly stated that Emotet was using an EternalBlue vulnerability in order to spread laterally within a network. However, Emotet only attempts to enumerate network resources and write to share drives, as well as brute force user accounts.
Perhaps what led us (and other researchers) to this conclusion was the fact that TrickBot, a payload we frequently see being loaded by Emotet, makes use of the EternalBlue exploit to spread itself to a domain controller and other Windows clients on the network.
We strongly recommend anyone impacted by Emotet continue to patch for EternalBlue and other related SMB vulnerabilities in order to prevent such lateral malware propagations.
The threat landscape is changing once again, now that the ocean of cryptocurrency miners has shrunk to a small lake. Over the last couple months, we’ve seen cybercriminals lean back on tried and true methods of financial theft and extortion, with the rise of a familiar Banking Trojan: Emotet.
However, over the last few days, we’ve noticed a large increase in malicious spam spreading Emotet, as well as a higher number of detections from our customers. Looks like we’re in the middle of an active Emotet campaign.
What is Emotet?
For those who are unfamiliar, Emotet is a nasty piece of malware that has had numerous purposes over the years, including stealing data and eavesdropping on network traffic. For its latest trick, Emotet is spreading other banking Trojans, or malware that steals your financial information, bank logins, and in some cases, Bitcoin wallets.
Emotet has the ability to propagate through a network by using the popular EternalBlue vulnerability, first seen in use in the famous WannaCry ransomware outbreak. This functionality makes the malware even more dangerous to businesses, which have numerous endpoints linked together.
Once a system is infected, Emotet can then spread itself outside the network via built-in spam module. Imagine an Emotet-infected endpoint as a flower. Emotet’s spam module, then, would be the bees that spread pollen from flower to flower. The spam module sends new infections to other systems, which (if the users fall victim) creates even more new infections, which then blast spam to even more systems. And the process continues again.
Now, accelerate our metaphorical pollination process by at least 1000x, and you can begin to see how Emotet is quickly making a lot of…um, flowers…for businesses.
Spam campaign
Recently, the security community noticed an increase in malicious spam either spreading Emotet or coming from systems infected with Emotet. In addition to Emotet, this malspam campaign is also pushing Trickbot, a popular information-stealing malware that we spoke about last year when unused code was discovered using the same exploit as WannaCry.
We're seeing a large #Emotet spam campaign with maldocs, originally spewing malicious Word documents, but now sending out PDFs. At its peak, we blocked over 300k spam emails in 3 hrs. Detection name: TrojanDownloader:PDF/Domepidief.A https://t.co/pWja45EInR pic.twitter.com/8uAdQ6d7v3
— Microsoft Threat Intelligence (@MsftSecIntel) September 18, 2018
This spam campaign is pushing malicious documents to users: first Microsoft Word documents with malicious macro scripts and then PDFs with built-in malicious scripts. This method of attack (malspam), using these specific file types (malicious documents), has become the de-facto default method of spreading malware today.
Malicious spam emails that are spreading Emotet and Trickbot right now have similar subject lines. Below is a list of common subject lines for this campaign:
Sales Invoice Account September Invoice **** from **** Statement 20/09/2018 for customer **** Your Invoice: **** - Our Ref: **** Account Alert - Your recent Wellsfargo payment notice Activity Alert: Money transfer details Activity Alert: Your recent payment notification Payment details Your recent payment notice August Invoice **** Invoice **** from **** Invoice for August Invoice **** - **** Invoice No - **** Invoice number **** Invoice **** from **** for Order : **** Invoices from **** INV-**** **** Complete invoice **** **** report: Complete invoice Q7370 - 21 September 2018 OVERDUE INVOICE Re: Your recent invoice request for your account Sales invoice from **** **** Invoice Ready To View September Invoice INV-B58986 from **** SERVICE INVOICE **** Invoice/Credit **** Statements/Invoices Ready To View Your **** Invoice for billing period 08/2018Increase in stats
In addition to the increase of malspam spreading Emotet, we’ve also observed an increase in Emotet detections from our users. The chart below shows a five month period, from mid-April to mid-September 2018, broken down by the day. You can see a steady increase of Emotet through the end of the summer into September, with the largest spike in Emotet detections happening only a few days ago. While this is not a sign that it will rain Emotet, when you combine that spike with the known ability of Emotet to spread itself quickly and efficiently, we could be in for some nasty infections over the weekend.
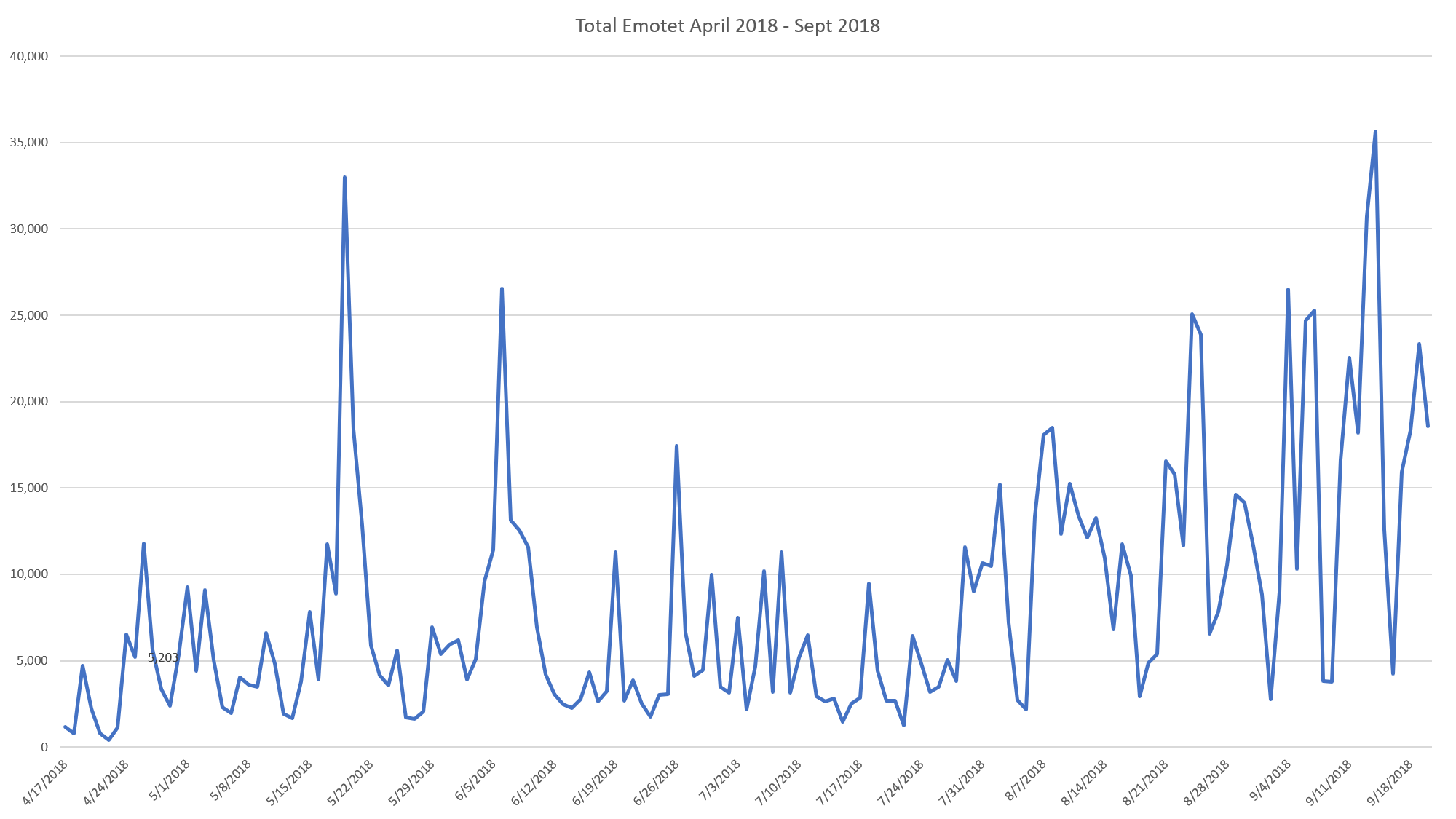
Despite its ups and downs—Emotet has not seen a continuous rise over the past year, though there was a similar massive Emotet and Trickbot campaign earlier in 2018—Emotet has been a bit of a thorn in the side of the security community for most of the year. That’s because when it is active, it has potential to do a lot of damage.
How much damage? Emotet is dangerous not only because of its capabilities to spread like wildfire and steal sensitive financial data, but also because it can download and install additional malware, which leaves the door open for anything coming through, from spyware to ransomware. Potential fallout could include:
- Theft of Personally Identifiable Information (PII), which could lead to identity theft
- Stolen financial information, which can later lead to extortion
- Stolen proprietary information, which can be held for ransom
- Credential theft, which means other accounts and passwords are vulnerable
- Theft of locally-stored cryptocurrency wallet
- Protracted remediation times for network admins
- Loss of productivity for workers whose endpoints must be taken off the network
Stay protected
Staying safe from the current Emotet campaign is not particularly difficult, since it is spread through malicious spam. However, users who don’t have a keen eye or little training in common phishing techniques might fall victim. One of the easiest ways to stay protected against Emotet is simply to keep a keen eye out for shady emails, especially if they have one of the subject lines mentioned above, include an Office document or PDF attachment, and come from unrecognizable email addresses. However, when it comes to social engineering, there is no guarantee someone won’t be fooled.
Thankfully, even if they open the email and download the document, Malwarebytes users (both those who purchased Malwarebytes Premium and business customers) will be safe from the malicious code within the document, as our anti-exploit technology identifies the malicious script and puts a stop to it.
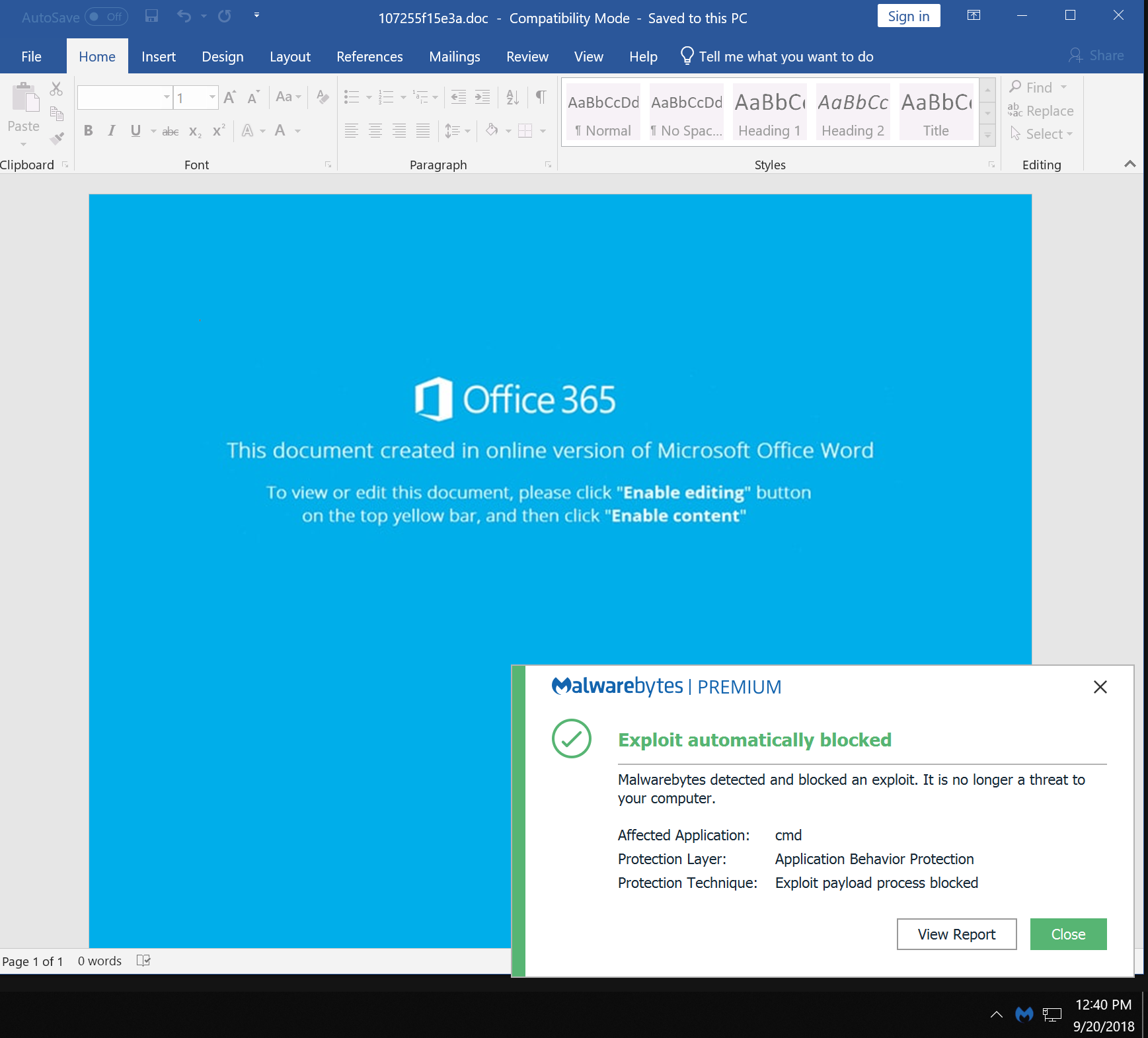
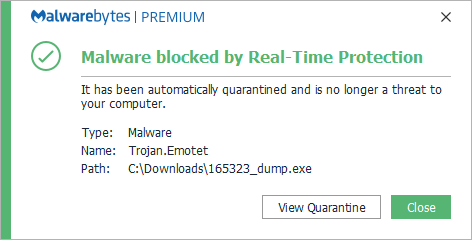
Also, users that have real-time protection enabled will have the malware itself blocked if it somehow manages to get through the anti-exploit defenses.
Another way to stay safe: Make sure systems are patched for the EternalBlue vulnerability, which is still exploitable—preferably before encountering this threat.
Malwarebytes has worked hard to keep an eye on this threat, and more importantly, how to stop it. Emotet is a mean adversary, and we expect to continue dealing with it through the rest of the year, as well as any future evolutions or copy cats.
That being said, making sure you, your family, and your employees know how to recognize emails attempting to deliver Emotet—or any other threat—is a key pillar in the fight against cybercrime, right alongside having a strong security solution and a “worst case scenario” plan to protect your data, users, and remediate your machines.
Thanks for reading, good luck out there, and safe surfing!











