Last quarter brought with it a maddening number of political ads, shocking and divisive news stories on climate change and gun laws, and mosquitoes. We hate mosquitoes. In related unpleasant news, it also apparently ushered in an era of banking Trojans that, as of this moment, shows no signs of slowing down.
First it was Emotet. But over the last couple months, Emotet has had some stiff competition. In fact, this already dangerous threat went quiet for a few weeks in October while its authors made tweaks to up the ante, adding a new module that exfiltrates email. Why? Because there’s a newer, more sophisticated banking Trojan in town attempting to penetrate business networks and giving Emotet a run for its money.
And its name is TrickBot.
TrickBot has now overtaken Emotet as our top-ranked threat for businesses, with an uptick in activity especially over the last 60 days. It’s hitting North America the hardest, with Europe, the Middle East, and Africa (EMEA) coming in a distant second. The latest surge in TrickBot activity has even prompted the National Cyber Security Centre in the UK to issue an advisory warning to organizations to prepare for attacks by immediately implementing mitigation protocols.
TrickBot features
The authors of TrickBot are agile and creative, regularly developing and rolling out new features, which is what makes this particular banking Trojan so dangerous. It’s likely why Emotet is locked in an arms race of sorts with TrickBot, competing for market share with increasingly sophisticated methods of attack and propagation.
So, what is TrickBot? Developed in 2016, TrickBot is one of the more recent banking Trojans on the market, with many of its original features inspired by Dyreza, another banking Trojan that acts as a data stealer. Besides targeting a wide array of international banks via webinjects, Trickbot can also harvest emails and credentials using the Mimikatz hack tool. Additional parlor tricks include the capability of stealing from Bitcoin wallets.
TrickBot comes in modules accompanied by a configuration file. Each module has a specific task, such as gaining persistence, propagation, stealing credentials, encryption, and so on. The C&Cs are set up on hacked wireless routers.
Infection vectors
TrickBot is typically spread via malicious spam (malspam) campaigns—for example, spear phishing emails disguised as unpaid invoices or requests to update account information.
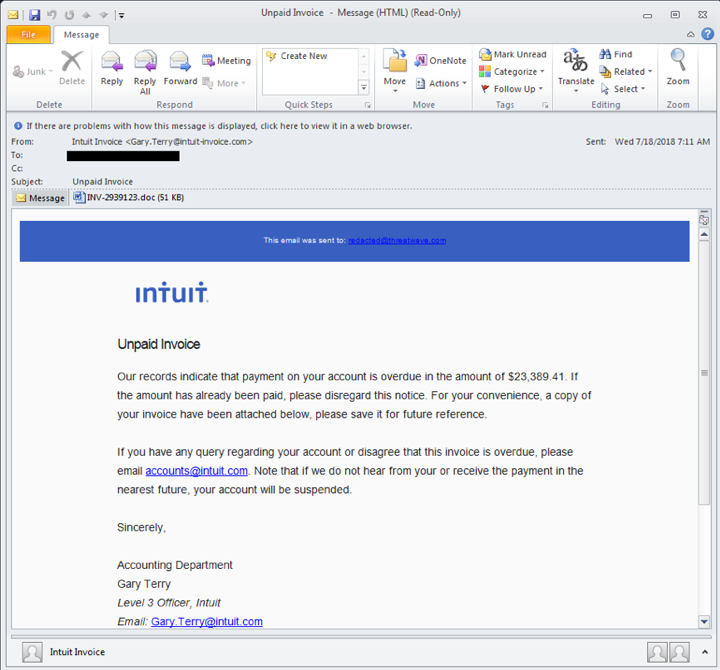
Other methods of propagation include embedded URLs and infected attachments, such as Microsoft Word documents with macros enabled. TrickBot is also seen as a secondary infection dropped by Emotet.
And, because those stolen NSA exploits keep proving their worth, once it has infected a single endpoint, TrickBot can then spread laterally through the network using the SMB vulnerability (MS17-010), which includes either the EternalBlue, EternalRomance, or EternalChampion exploit.
Clever girl.
Impact to businesses
The endpoint user will not notice any symptoms of a TrickBot infection. However, a network admin will likely see changes in traffic or attempts to reach out to blacklisted IPs and domains, as the malware will communicate with TrickBot’s command and control infrastructure to exfiltrate data and receive tasks.
TrickBot gains persistence by creating a Scheduled Task. And due to the way it uses the SMB vulnerability to spread through a company’s network, any infected machine on the network will re-infect machines that had been previously cleaned when they rejoin the network.
Therefore, IT teams need to isolate, patch, and remediate each infected system one-by-one. This can be a long and painstaking process that’s costly on time and resources. Much like with ransomware attacks, the best protection against a threat like TrickBot is to proactively prevent infection in the first place. However, that’s not always possible.
Prevention
According to a 2018 study conducted by Osterman Research on the true cost of cybercrime, 53 percent of US organizations have experienced a phishing attack in the last year. Another 23 percent have witnessed spear phishing attacks. There’s a reason why this attack vector is so popular: It’s still incredibly effective.
On average, four percent of the targets in any given phishing campaign will click on it. But here’s the kicker: the more phishing emails someone has clicked, the more likely they are do click on them again. And even worse—although most folks don’t click on phishing emails, only 27 percent actually report them. In a business environment, this is no bueno.
Think it’s time for organizations to educate their employees on how to spot phishing attempts? We sure do. One of the easiest ways to stop threats like TrickBot, which are initially spread via malspam/phishing campaigns, is to train users to spot that suspicious email from a mile away, even when it’s cloaked in reputable company logos. In addition, teaching users about the importance of immediately reporting a suspicious email to the correct teams will help to reduce the amount of time to detect and respond to phishing attacks.
But the training shouldn’t stop there. Work closely with individuals with access to the most sensitive data, since they will likely be targeted, and provide role-specific education. Show them how to spot a spear phish and emphasize the importance of healthy skepticism. They are the gatekeepers, and they must be on guard.
It’s not just end users who need a little (phish)boning up. Train the responders alongside them. Test their ability to detect a campaign, identify potentially infected hosts, determine which actions were taken on compromised machines, and confirm whether or not data exfiltration took place.
If you periodically drill your employees and response teams and provide follow-up seminars, especially for those who fail to identify or report phishes, your organization will be able to either successfully fend off a phishing attack or limit the impact of a successful phish.
Of course, increasing employee awareness isn’t the only prevention method. Patching for the SMB vulnerability can keep TrickBot and other threats that use these exploits from spreading laterally through the network. And using a comprehensive cybersecurity solution that blocks exploits can keep endpoints from getting infected.
Remediate
Malwarebytes can detect and remove TrickBot on business endpoints without further user interaction. But to be effective on networked machines, you must first follow these steps:
- Identify the infected machine(s). If you have unprotected endpoints/machines, you can run Farbar Recovery Scan Tool (FRST) to look for possible Indicators of Compromise (IOC). Besides verifying an infection, FRST can also be used to verify removal before bringing an endpoint/machine back into the network.
- Disconnect the infected machines from the network.
- Patch each endpoint for MS 17-010.
- Disable administrative shares. Windows Server by default installs hidden share folders specifically for administrative access to other machines. The Admin$ shares are used by TrickBot once it has brute forced the local administrator password. A file share server has an IPC$ share that TrickBot queries to get a list of all endpoints that connect to it. These AdminIP shares are normally protected via UAC, however, Windows will allow the local administrator through without a prompt.The most recent Trickbot variants use C$ with the Admin credentials to move around and re-infect all the other endpoints.It is recommended to disable these Admin$ shares via the registry, as discussed in this Microsoft support article. If you do not see this registry key, it can be added manually and set up to be disabled.
- Remove the TrickBot Trojan.
- Change account credentials. Repeated re-infections are an indication the worm was able to guess or brute force the administrator password successfully. Please change all local and domain administrator passwords.
A threat for the ages
TrickBot has proven itself to be a most tricky foe, but that doesn’t mean organizations should run screaming. Its modular structure, use of the SMB exploit, and simple, yet sophisticated attack vector (malspam/phishing campaigns) make it dangerous, yes, but we have proven methods for protecting against each of these traits. With dedicated employee training for phishing awareness, a cybersecurity solution that protects against exploits, and some good old-fashioned patching, you can not only keep individuals from losing out on productivity for the week—you can keep your whole network afloat.
And in the age of TrickBot, that’s no small fete.











