Payload seen: Kpot
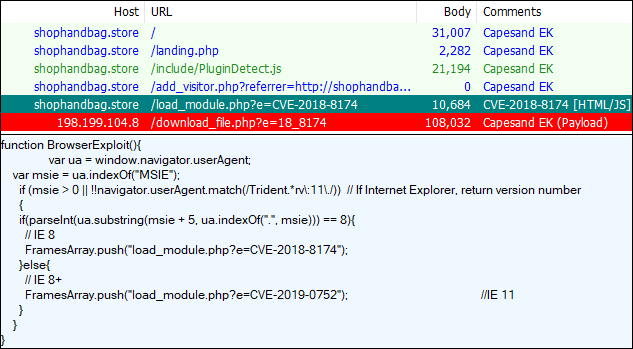
Capesand EK
Capesand EK is the latest exploit to have surfaced although it is based on code from an old EK called Demon Hunter. It was spotted on a particular malvertising campaign, perhaps suggesting the work of one malware author for his own distribution.
Payload seen: NjRAT
Maintaining a foothold
It’s interesting to see exploit kits alive and kicking, despite relying on aging vulnerabilities and a decrease in user base of both Internet Explorer and the Flash Player.
In the past quarter, we’ve observed sustained malvertising activity and a diversity of malware payloads served. We can probably expect this trend to continue and perhaps even see new frameworks pop up. Even if it remains remote, we can’t discard the possibility of an exploit kit targeting one of the newer browsers.
Consumer and enterprise users still running Internet Explorer are protected from these exploit kits with Malwarebytes.
Payload seen: Dupzom
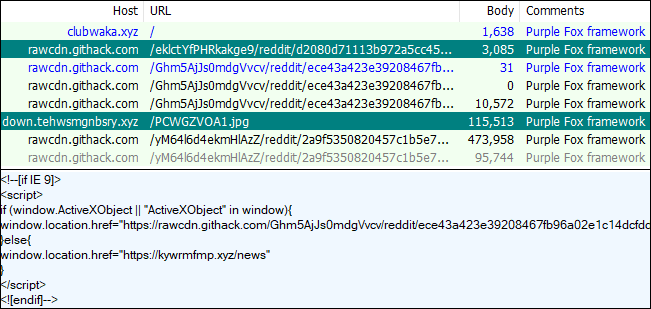
Purple Fox EK
Purple Fox was described previously by TrendMicro and is an interesting drive-by framework that loads fileless malware. While it was once loaded via RIG EK, it is now seen on its own. For this reason, we believe it can be called an exploit kit as well.

Payload seen: Kpot
Capesand EK
Capesand EK is the latest exploit to have surfaced although it is based on code from an old EK called Demon Hunter. It was spotted on a particular malvertising campaign, perhaps suggesting the work of one malware author for his own distribution.

Payload seen: NjRAT
Maintaining a foothold
It’s interesting to see exploit kits alive and kicking, despite relying on aging vulnerabilities and a decrease in user base of both Internet Explorer and the Flash Player.
In the past quarter, we’ve observed sustained malvertising activity and a diversity of malware payloads served. We can probably expect this trend to continue and perhaps even see new frameworks pop up. Even if it remains remote, we can’t discard the possibility of an exploit kit targeting one of the newer browsers.
Consumer and enterprise users still running Internet Explorer are protected from these exploit kits with Malwarebytes.
Payload seen: Hidden Bee
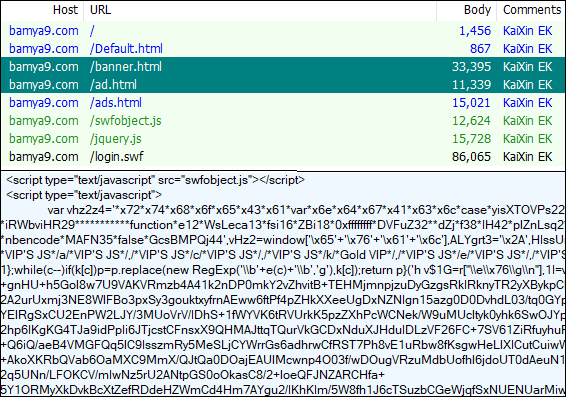
KaiXin EK
KaiXin EK is a more obscure exploit kit we seldom run into, perhaps because it seems to target the Asian market. However, it appears to still be around on the same infrastructure.

Payload seen: Dupzom
Purple Fox EK
Purple Fox was described previously by TrendMicro and is an interesting drive-by framework that loads fileless malware. While it was once loaded via RIG EK, it is now seen on its own. For this reason, we believe it can be called an exploit kit as well.

Payload seen: Kpot
Capesand EK
Capesand EK is the latest exploit to have surfaced although it is based on code from an old EK called Demon Hunter. It was spotted on a particular malvertising campaign, perhaps suggesting the work of one malware author for his own distribution.

Payload seen: NjRAT
Maintaining a foothold
It’s interesting to see exploit kits alive and kicking, despite relying on aging vulnerabilities and a decrease in user base of both Internet Explorer and the Flash Player.
In the past quarter, we’ve observed sustained malvertising activity and a diversity of malware payloads served. We can probably expect this trend to continue and perhaps even see new frameworks pop up. Even if it remains remote, we can’t discard the possibility of an exploit kit targeting one of the newer browsers.
Consumer and enterprise users still running Internet Explorer are protected from these exploit kits with Malwarebytes.
Payload seen: Ramnit
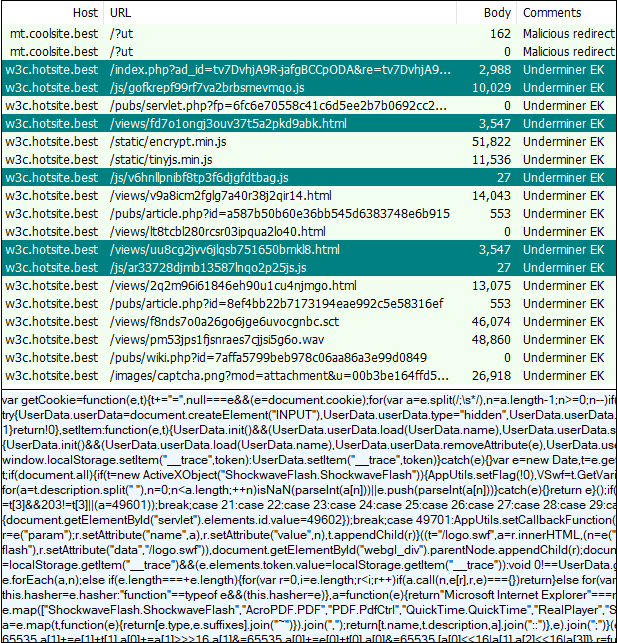
Underminer EK
Underminer EK is one of the more interesting exploit kits on the market, due to its unusual way of delivering its Hidden Bee payload. Not only is it fileless, but it is packed in a particular way that hints that the exploit kit and malware developer are one and the same.

Payload seen: Hidden Bee
KaiXin EK
KaiXin EK is a more obscure exploit kit we seldom run into, perhaps because it seems to target the Asian market. However, it appears to still be around on the same infrastructure.

Payload seen: Dupzom
Purple Fox EK
Purple Fox was described previously by TrendMicro and is an interesting drive-by framework that loads fileless malware. While it was once loaded via RIG EK, it is now seen on its own. For this reason, we believe it can be called an exploit kit as well.

Payload seen: Kpot
Capesand EK
Capesand EK is the latest exploit to have surfaced although it is based on code from an old EK called Demon Hunter. It was spotted on a particular malvertising campaign, perhaps suggesting the work of one malware author for his own distribution.

Payload seen: NjRAT
Maintaining a foothold
It’s interesting to see exploit kits alive and kicking, despite relying on aging vulnerabilities and a decrease in user base of both Internet Explorer and the Flash Player.
In the past quarter, we’ve observed sustained malvertising activity and a diversity of malware payloads served. We can probably expect this trend to continue and perhaps even see new frameworks pop up. Even if it remains remote, we can’t discard the possibility of an exploit kit targeting one of the newer browsers.
Consumer and enterprise users still running Internet Explorer are protected from these exploit kits with Malwarebytes.
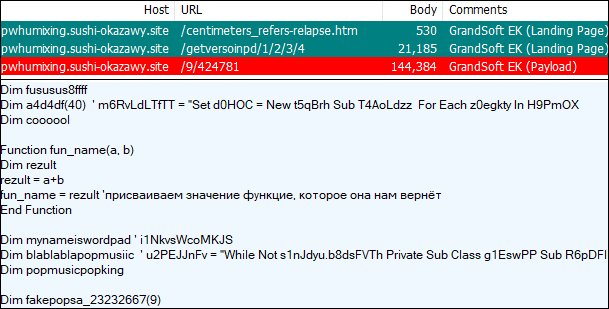
Payloads seen: Smoke Loader, Sodinokibi, Paradise, Antefrigus
GrandSoft EK
GrandSoft EK is not as commonly observed this fall, and appears to have limited payload distribution. It is known to focus on the distribution of the Ramnit Trojan.

Payload seen: Ramnit
Underminer EK
Underminer EK is one of the more interesting exploit kits on the market, due to its unusual way of delivering its Hidden Bee payload. Not only is it fileless, but it is packed in a particular way that hints that the exploit kit and malware developer are one and the same.

Payload seen: Hidden Bee
KaiXin EK
KaiXin EK is a more obscure exploit kit we seldom run into, perhaps because it seems to target the Asian market. However, it appears to still be around on the same infrastructure.

Payload seen: Dupzom
Purple Fox EK
Purple Fox was described previously by TrendMicro and is an interesting drive-by framework that loads fileless malware. While it was once loaded via RIG EK, it is now seen on its own. For this reason, we believe it can be called an exploit kit as well.

Payload seen: Kpot
Capesand EK
Capesand EK is the latest exploit to have surfaced although it is based on code from an old EK called Demon Hunter. It was spotted on a particular malvertising campaign, perhaps suggesting the work of one malware author for his own distribution.

Payload seen: NjRAT
Maintaining a foothold
It’s interesting to see exploit kits alive and kicking, despite relying on aging vulnerabilities and a decrease in user base of both Internet Explorer and the Flash Player.
In the past quarter, we’ve observed sustained malvertising activity and a diversity of malware payloads served. We can probably expect this trend to continue and perhaps even see new frameworks pop up. Even if it remains remote, we can’t discard the possibility of an exploit kit targeting one of the newer browsers.
Consumer and enterprise users still running Internet Explorer are protected from these exploit kits with Malwarebytes.
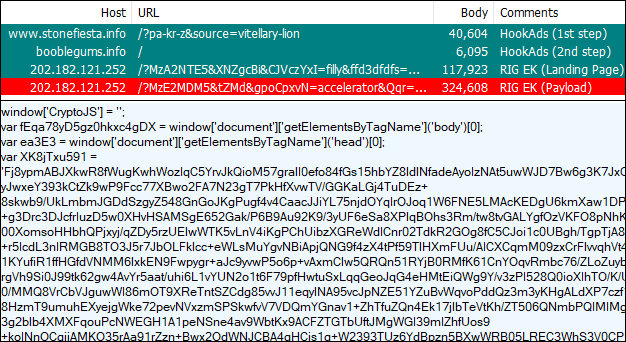
Payload seen: Magniber
RIG EK
Recently, RIG EK seems to have dropped its Flash Player exploit and instead relies solely on Internet Explorer. One active campaign is HookAds, which uses a fake gaming website to redirect to the exploit kit.

Payloads seen: Smoke Loader, Sodinokibi, Paradise, Antefrigus
GrandSoft EK
GrandSoft EK is not as commonly observed this fall, and appears to have limited payload distribution. It is known to focus on the distribution of the Ramnit Trojan.

Payload seen: Ramnit
Underminer EK
Underminer EK is one of the more interesting exploit kits on the market, due to its unusual way of delivering its Hidden Bee payload. Not only is it fileless, but it is packed in a particular way that hints that the exploit kit and malware developer are one and the same.

Payload seen: Hidden Bee
KaiXin EK
KaiXin EK is a more obscure exploit kit we seldom run into, perhaps because it seems to target the Asian market. However, it appears to still be around on the same infrastructure.

Payload seen: Dupzom
Purple Fox EK
Purple Fox was described previously by TrendMicro and is an interesting drive-by framework that loads fileless malware. While it was once loaded via RIG EK, it is now seen on its own. For this reason, we believe it can be called an exploit kit as well.

Payload seen: Kpot
Capesand EK
Capesand EK is the latest exploit to have surfaced although it is based on code from an old EK called Demon Hunter. It was spotted on a particular malvertising campaign, perhaps suggesting the work of one malware author for his own distribution.

Payload seen: NjRAT
Maintaining a foothold
It’s interesting to see exploit kits alive and kicking, despite relying on aging vulnerabilities and a decrease in user base of both Internet Explorer and the Flash Player.
In the past quarter, we’ve observed sustained malvertising activity and a diversity of malware payloads served. We can probably expect this trend to continue and perhaps even see new frameworks pop up. Even if it remains remote, we can’t discard the possibility of an exploit kit targeting one of the newer browsers.
Consumer and enterprise users still running Internet Explorer are protected from these exploit kits with Malwarebytes.
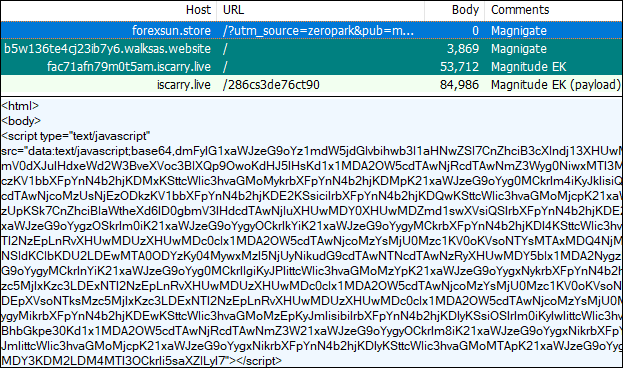
Payloads seen: Sodinokibi, AZORult, Kpot, Raccoon, Danabot
Magnitude EK
Magnitude EK hasn’t changed much in the past few months. The same Magnigate infrastructure is being used to redirect users to fake cryptocurrency domains. The payload remains Magniber ransomware delivered in fileless mode.

Payload seen: Magniber
RIG EK
Recently, RIG EK seems to have dropped its Flash Player exploit and instead relies solely on Internet Explorer. One active campaign is HookAds, which uses a fake gaming website to redirect to the exploit kit.

Payloads seen: Smoke Loader, Sodinokibi, Paradise, Antefrigus
GrandSoft EK
GrandSoft EK is not as commonly observed this fall, and appears to have limited payload distribution. It is known to focus on the distribution of the Ramnit Trojan.

Payload seen: Ramnit
Underminer EK
Underminer EK is one of the more interesting exploit kits on the market, due to its unusual way of delivering its Hidden Bee payload. Not only is it fileless, but it is packed in a particular way that hints that the exploit kit and malware developer are one and the same.

Payload seen: Hidden Bee
KaiXin EK
KaiXin EK is a more obscure exploit kit we seldom run into, perhaps because it seems to target the Asian market. However, it appears to still be around on the same infrastructure.

Payload seen: Dupzom
Purple Fox EK
Purple Fox was described previously by TrendMicro and is an interesting drive-by framework that loads fileless malware. While it was once loaded via RIG EK, it is now seen on its own. For this reason, we believe it can be called an exploit kit as well.

Payload seen: Kpot
Capesand EK
Capesand EK is the latest exploit to have surfaced although it is based on code from an old EK called Demon Hunter. It was spotted on a particular malvertising campaign, perhaps suggesting the work of one malware author for his own distribution.

Payload seen: NjRAT
Maintaining a foothold
It’s interesting to see exploit kits alive and kicking, despite relying on aging vulnerabilities and a decrease in user base of both Internet Explorer and the Flash Player.
In the past quarter, we’ve observed sustained malvertising activity and a diversity of malware payloads served. We can probably expect this trend to continue and perhaps even see new frameworks pop up. Even if it remains remote, we can’t discard the possibility of an exploit kit targeting one of the newer browsers.
Consumer and enterprise users still running Internet Explorer are protected from these exploit kits with Malwarebytes.
Despite a slim browser market share, Internet Explorer is still being exploited in fall 2019 in a number of drive-by download campaigns. Perhaps even more surprising, we’re seeing new exploit kits emerge.
Based on our telemetry, these drive-bys are happening worldwide (with the exception of a few that are geo-targeted) and are fueled by malvertising most often found on adult websites.
Even though the weaponized vulnerabilities remain fairly old, we’ve observed a growing number of exploit kits go for fileless attacks instead of the more traditional method of dropping a payload on disk. This is an interesting trend that makes sample sharing more difficult and possibly increases infection rates by evading some security products.
Fall 2019 overview
- Spelevo EK
- Fallout EK
- Magnitude EK
- RIG EK
- GrandSoft EK
- Underminer EK
- KaiXin EK
- Purplefox EK
- Capesand EK
Vulnerabilties
Internet Explorer’s CVE-2018-8174 and Flash Player’s CVE-2018-15982 are the most common vulnerabilities, while the older CVE-2018-4878 (Flash) is still used by some EKs. It’s worth noting we’re seeing some exploit kits no longer using Flash, while others are relying on much older vulnerabilities.
Spelevo EK
Spelevo EK is one of these newer exploit kits that we see on a regular basis via malvertising campaigns. There hasn’t been any major change since our last review and the threat actors still rely on the domain shadowing technique to generate new URLs.
Payloads seen: PsiXBot, Gootkit, Maze
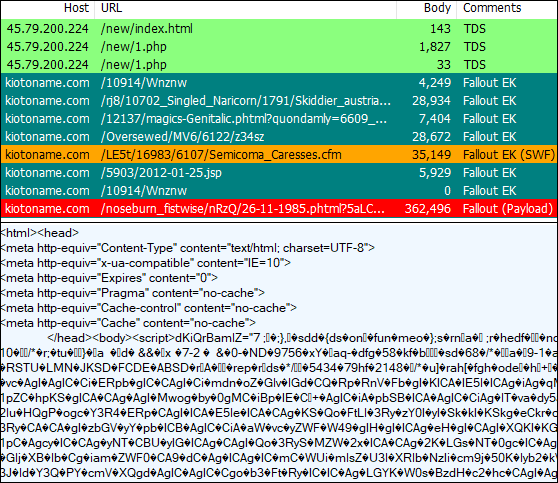
Fallout EK
Fallout EK stands apart from the rest with obfuscation techniques, as well various fingerprinting checks. It also implemented the Diffie-Hellman key exchange to prevent offline replays by security analysts.

Payloads seen: Sodinokibi, AZORult, Kpot, Raccoon, Danabot
Magnitude EK
Magnitude EK hasn’t changed much in the past few months. The same Magnigate infrastructure is being used to redirect users to fake cryptocurrency domains. The payload remains Magniber ransomware delivered in fileless mode.

Payload seen: Magniber
RIG EK
Recently, RIG EK seems to have dropped its Flash Player exploit and instead relies solely on Internet Explorer. One active campaign is HookAds, which uses a fake gaming website to redirect to the exploit kit.

Payloads seen: Smoke Loader, Sodinokibi, Paradise, Antefrigus
GrandSoft EK
GrandSoft EK is not as commonly observed this fall, and appears to have limited payload distribution. It is known to focus on the distribution of the Ramnit Trojan.

Payload seen: Ramnit
Underminer EK
Underminer EK is one of the more interesting exploit kits on the market, due to its unusual way of delivering its Hidden Bee payload. Not only is it fileless, but it is packed in a particular way that hints that the exploit kit and malware developer are one and the same.

Payload seen: Hidden Bee
KaiXin EK
KaiXin EK is a more obscure exploit kit we seldom run into, perhaps because it seems to target the Asian market. However, it appears to still be around on the same infrastructure.

Payload seen: Dupzom
Purple Fox EK
Purple Fox was described previously by TrendMicro and is an interesting drive-by framework that loads fileless malware. While it was once loaded via RIG EK, it is now seen on its own. For this reason, we believe it can be called an exploit kit as well.

Payload seen: Kpot
Capesand EK
Capesand EK is the latest exploit to have surfaced although it is based on code from an old EK called Demon Hunter. It was spotted on a particular malvertising campaign, perhaps suggesting the work of one malware author for his own distribution.

Payload seen: NjRAT
Maintaining a foothold
It’s interesting to see exploit kits alive and kicking, despite relying on aging vulnerabilities and a decrease in user base of both Internet Explorer and the Flash Player.
In the past quarter, we’ve observed sustained malvertising activity and a diversity of malware payloads served. We can probably expect this trend to continue and perhaps even see new frameworks pop up. Even if it remains remote, we can’t discard the possibility of an exploit kit targeting one of the newer browsers.
Consumer and enterprise users still running Internet Explorer are protected from these exploit kits with Malwarebytes.










