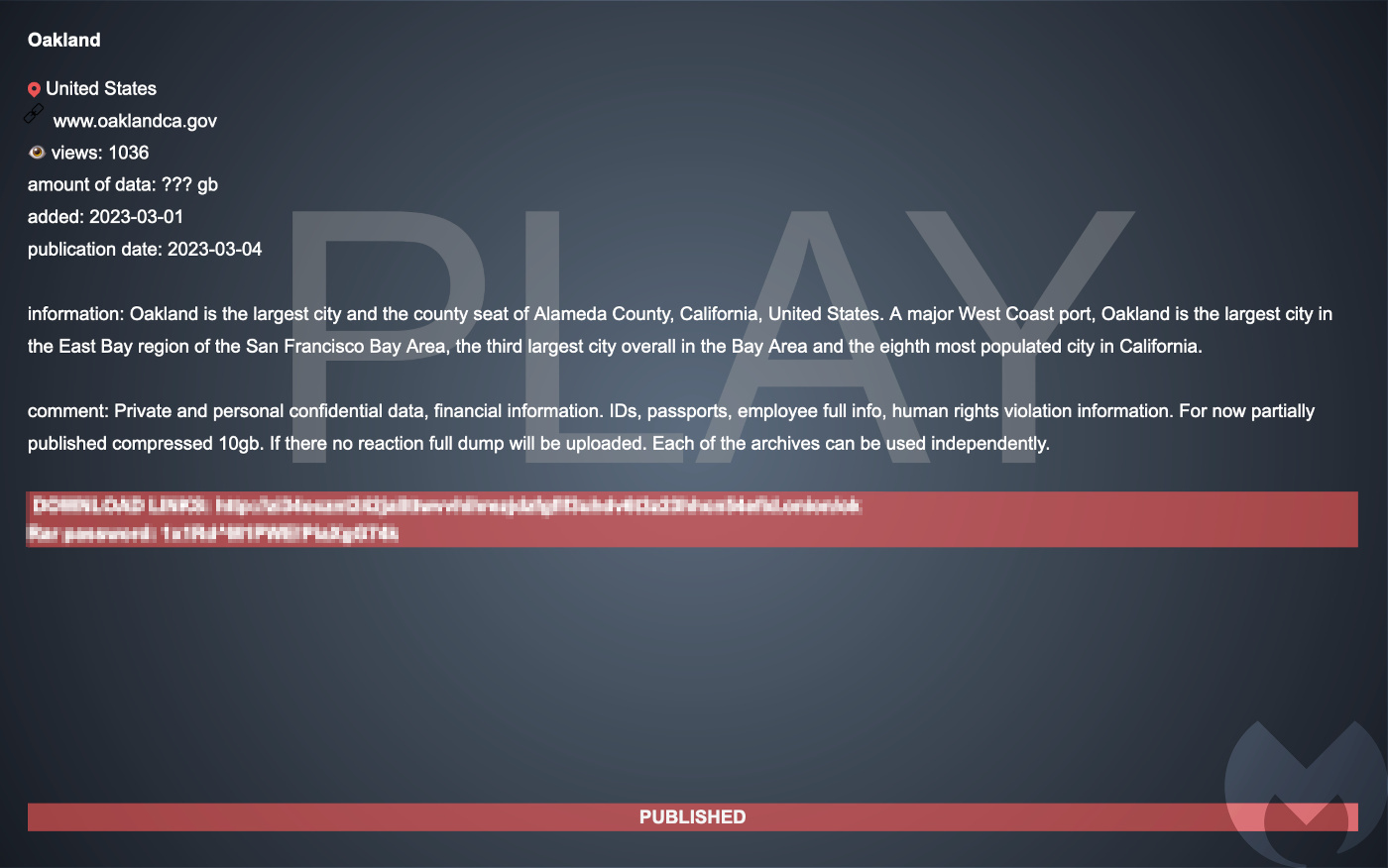
The Play ransomware gang has begun partially publishing data they stole from the City of Oakland, California. The data were in multiple archive files with a collective file size of 10GB. According to the ransomware gang, the files contain “[p]rivate and personal information data, financial information. IDs, passports, employee full info, human rights violation information.”
“If there is no reaction full dump will be uploaded,” the gang wrote in a comment on their leak site. They also hinted that each file could be used independently.
Following the release of the data, the City of Oakland said in an updated statement:
“While the investigation into the scope of the incident impacting the City of Oakland remains ongoing, we recently became aware that an unauthorized third party has acquired certain files from our network and intends to release the information publicly.
We are working with third-party specialists and law enforcement on this issue and are actively monitoring the unauthorized third party’s claims to investigate their validity.”
The City of Oakland, California was attacked four weeks ago, bringing several City services to a standstill. This pushed Interim City Administrator G. Harold Duffey to declare a state of emergency. The Play ransomware group claimed responsibility for the attack.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; disable or harden remote access like RDP and VPNs; use endpoint security software that can detect exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like Malwarebytes EDR that uses multiple different detection techniques to identify ransomware.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Write an incident response plan. The period after a ransomware attack can be chaotic. Make a plan that outlines how you’ll isolate an outbreak, communicate with stakeholders, and restore your systems.
Have a question or want to learn more about our cyberprotection? Get a free business trial below.










