Researchers have published details about a phishing campaign that uses QR codes to phish for Microsoft credentials.
A QR (Quick Response) code is a kind of two-dimensional barcode that holds encoded data in a graphical black-and-white pattern. The data that a QR code stores can include URLs, email addresses, network details, Wi-Fi passwords, serial numbers, etc.
While QR codes are generally safe, they can easily be manipulated by scammers because they all appear similar to the human eye. A malicious QR code may lead you to a spoofed website designed to drop different malware types or steal your sensitive data, like your password, credit card information, or money.
The use of QR codes in malicious campaigns is not new, and because they can provide contactless access to a product or service they grew in popularity during the pandemic. And because QR codes are images (sent as PNG or PDF attachments in the campaigns reported here) their content is more likely to make it past email filters.
The researchers have been monitoring a campaign since May of 2023 that, although it targeted users from a wide array of industries, seemed to focus on a major energy company based in the US. This undisclosed target received 29% of the over 1,000 emails containing malicious QR codes.
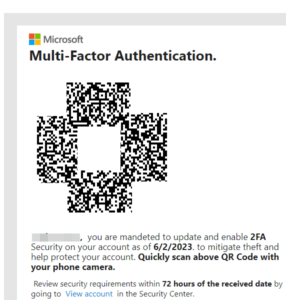
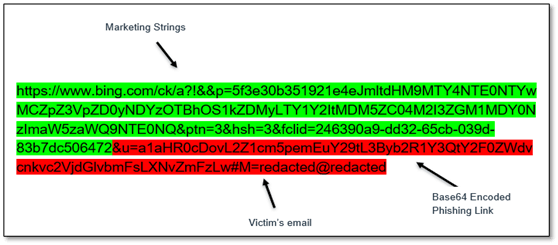
The links in the QR codes used open redirects from legitimate domains associated with Bing, Salesforce, and Cloudflare to send the targets to phishing sites that were after Microsoft credentials. Since the subject of the emails were often spoofed Microsoft security notifications the Bing URLs would not have looked out of place to any victims who noticed them.
The campaign has reportedly shown a significant growth since it was discovered with the volume increased by more than 2,400% since May 2023.
For cybercriminals, the use of QR codes usually has the disadvantage that they need to be scanned by a mobile device, which is more complex than simply giving targets a link to click on. But in a corporate environment this can also be an advantage as the mobile device might be outside of the protection of the enterprise environment.
The researchers showcase a Bing redirect URL which is likely to be seen as legitimate in light of the other Microsoft mimicry used in this campaign. Many search engines, social media, and other platforms use some form of open redirect, which cybercriminals use to make their links look legitimate.
Recommendations
When it comes to QR codes they are nearly impossible to recognize as malicious by humans, so it takes some extra attention. Some pointers:
- Treat QR codes like any other link in an unsolicited mail, or possibly even with more caution. If you receive a QR code either in the mail or sent to you by a friend, get in touch with them first and verify that they have indeed sent you the code.
- When scanning a QR code your device should display the site it will take you to. Pay close attention to that link. Be wary of legitimate domains that are known to use redirects and URL shorteners.
- Use the built-in scanner through your smartphone’s camera to scan for QR codes. There is no need to download another one from the app store since there are fake QR code scanners and ones that come bundled with unwanted extras.
Malwarebytes EDR and MDR removes all remnants of ransomware and prevents you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.











