The consequences of last year’s LastPass breach continue to be felt, with the latest insult to users coming in the form of a highly convincing phishing email.
Although the “unauthorized party” that compromised LastPass users’ data was able to steal password vaults, it’s likely that they are having a hard time cracking them open. LastPass’s own assessment was that “it would be extremely difficult to attempt to brute force guess master passwords for those customers who follow our password best practices.”
Brute force guessing techniques may be successful for some weak passwords, but it’s an approach that quickly runs out of steam. The frequency with which passwords are uncovered diminishes exponentially, and the cost per password increases in the same way. So while some passwords will be so strong they are effectively uncrackable, many weaker ones are likely to be safe simply because they’re too costly to uncover.
However, there is another, far easier way for criminals to get at LastPass users’ passwords, without cracking them: They can simply ask.
They can do this becasue alongside the password vaults that were stolen, criminals also made off with customers’ email addresses, as well as “basic customer account information”, company names, end-user names, billing addresses, telephone numbers, and IP addresses.
Armed with this data, attackers can send targeted phishing emails that attempt to steal the passwords needed to unlock the stolen password vaults.
The LastPass phishing email we received was convincing, familiar, and executed with high production values. However, as convincing as it was, the email could not avoid the two red flags that allow anyone to spot almost any scam: A demand for personal information and an attempt to hurry the victim.
The email lure tells users to verify their personal data or face losing deactivation of “certain features” on 26 September.
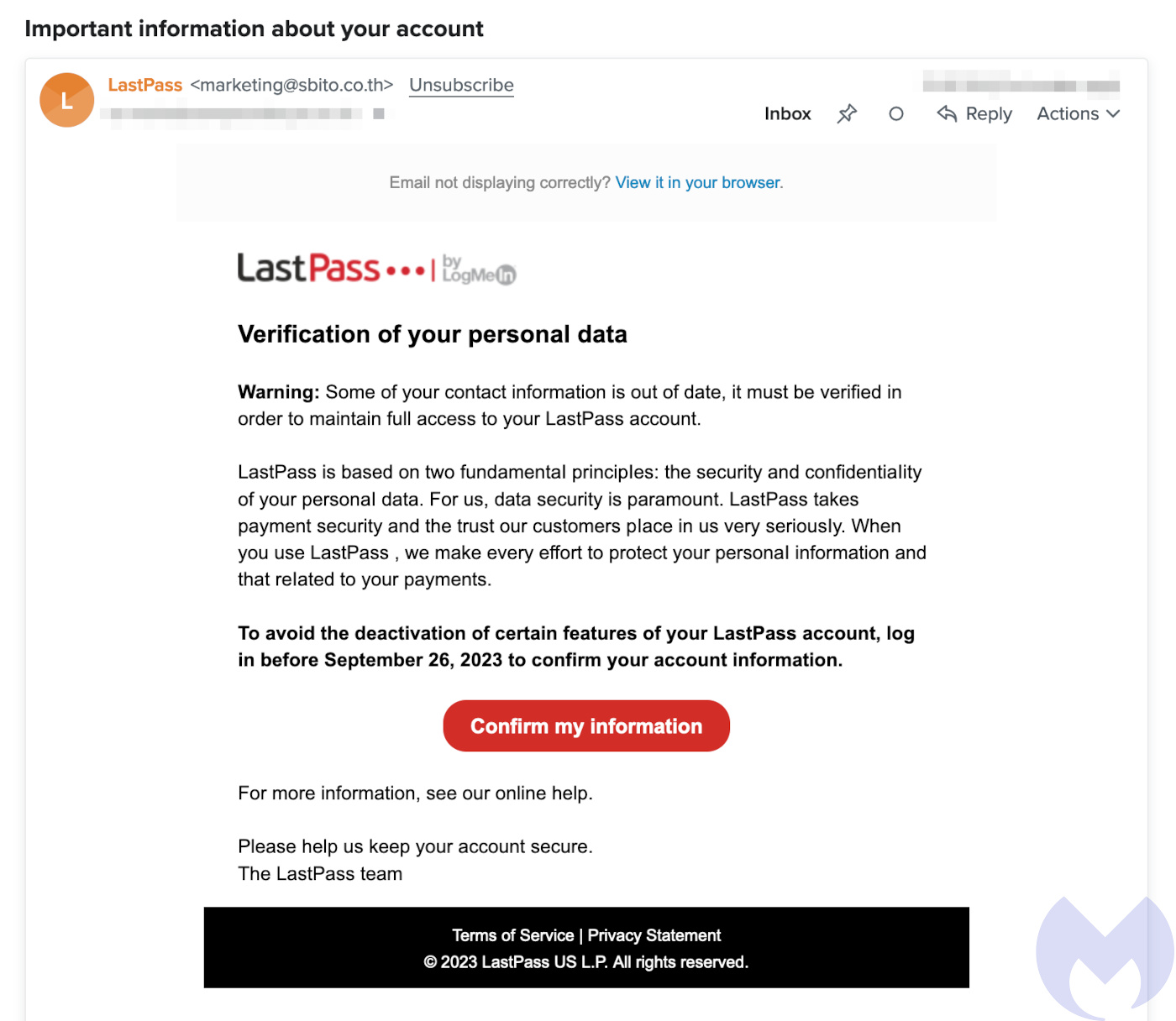
The full email reads:
Verification of your personal data
Warning: Some of your contact information is out of date, it must be verified in order to maintain full access to your LastPass account.
LastPass is based on two fundamentaI principIes: the security and confidentiaIity of your personaI data. For us, data security is paramount. LastPass takes payment security and the trust our customers pIace in us very seriousIy. When you use LastPass , we make every effort to protect your personaI information and that reIated to your payments.
To avoid the deactivation of certain features of your LastPass account, log in before September 26, 2023 to confirm your account information.
Although we spotted quickly that the “From” address of the email was registered in Thailand and didn’t appear to be related to LastPass, we suspect many won’t. Unfortunately, the old advice to watch out for strange addresses, complicated URLs, and to not click on links is being undermined by a vast army of legitimate companies using mailing systems that do all three.
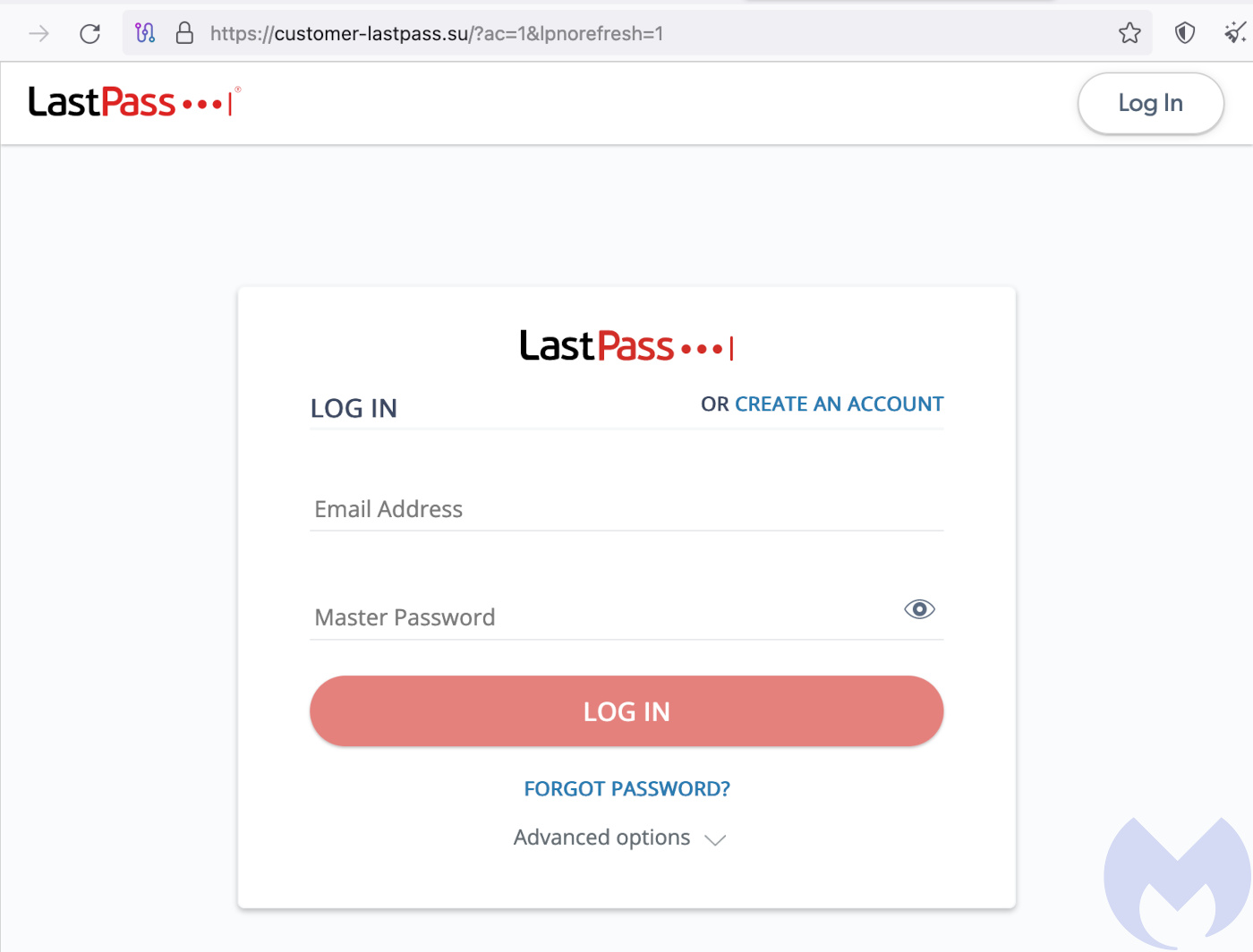
The email’s ‘Confirm my information’ link uses a complicated URL format that likely contains a unique ID, which redirects to the phishing site itself. Like the email, the site is an almost pixel-perfect copy of the real thing. (The only giveaways in the design were ‘Create an account’ and ‘Forgot password’ buttons that don’t do anything.)
Again, while some users might be put off by the Slovakian domain name, it looks neat enough and somewhat official.
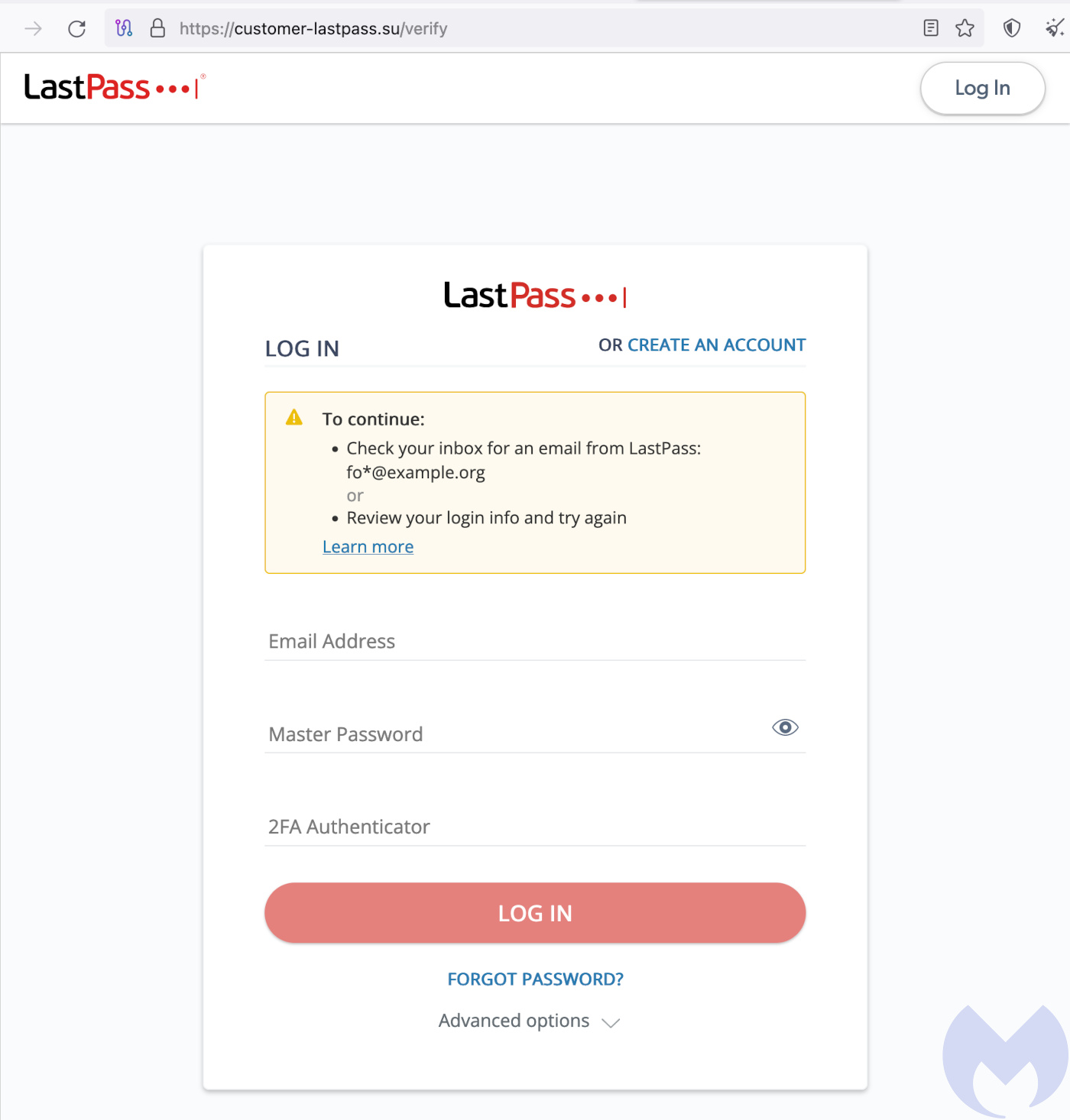
Filling in the username and password causes the page to reload, this time with a request for a two-factor authentication (2FA) code—allowing us to remind you once again that while code-based 2FA is a solid defence against all kinds of password attacks, it is no defence against phishing. (For that you need 2FA based on FIDO2, such as hardware keys.)
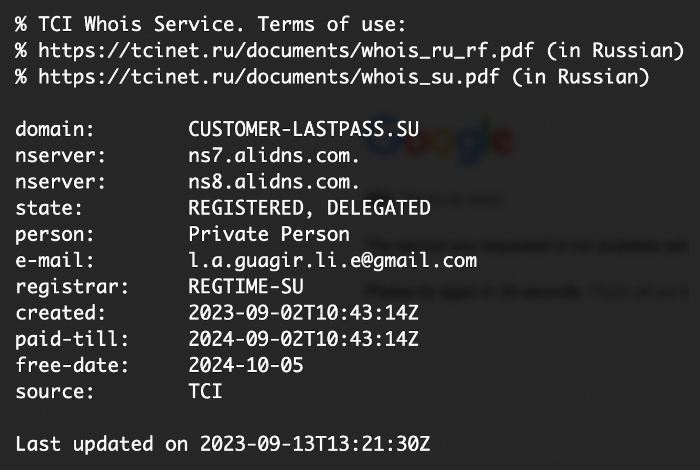
Having fed the criminals some useless information, we checked the site’s Slovakian domain name and discovered that it had been created just a few days before on September 2, 2023, via the Russian registrar webnames.ru—a veritable bunting of fluttering red flags.
Thankfully, while this phish was convincing and difficult to spot, our standard phishing advice still applies, and would have kept you safe:
- Block known bad websites. Malwarebytes DNS filtering blocks malicious websites used for phishing attacks, as well as websites used to spread or control malware.
- Don’t take things at face value. Phishing attacks often seem to come from people or brands you know, and use themes that require urgent attention, such as missed deliveries, account suspensions, and security alerts.
- Take action. If you receive a phishing attempt at work, report it to your IT or security team. If you fall for a phish, make your data useless: If you entered a password, change it, if you entered credit card details, cancel the card.
- Use a password manager. Password managers can create, remember, and fill in passwords for you. They protect you against phishing because they won’t enter your credentials into a fake site.
- Use a FIDO2 2FA device. Some forms of 2FA can be phished just as easily as a password. 2FA that relies on a FIDO2 device can’t be phished.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.










