This blog post was written based on research carried out by Jérôme Segura.
A campaign using sponsored search results is targeting home users and taking them to tech support scams.
Sponsored search results are the ones that are listed at the top of search results and are labelled “Sponsored”. They’re often ads that are taken out by brands who want to get people to click through to their website. In the case of malicious sponsored ads, scammers tend to outbid the brands in order to be listed as the first search result.
The criminals that buy the ads will go as far as displaying the official brand’s website within the ad snippet, making it hard for an unsuspecting visitor to notice a difference.
Who would, for example, be able to spot that the below ad for CNN is not legitimate. You’ll have to click on the three dots (in front of where we added malicious ad) and look at the advertiser information to see that it’s not the legitimate owner of the brand.
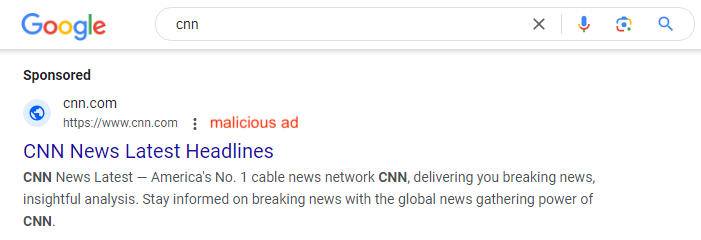
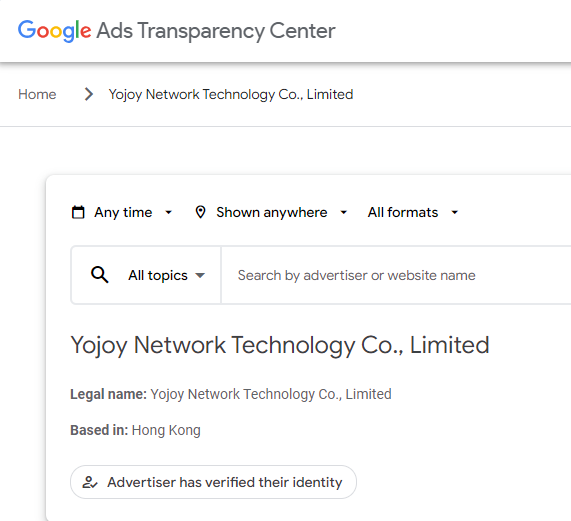
Only then it becomes apparent that the real advertiser is not CNN, but instead a company called Yojoy Network Technology Co., Limited.
Below, you can see another fake advertisement by the same advertiser, this time impersonating Amazon.
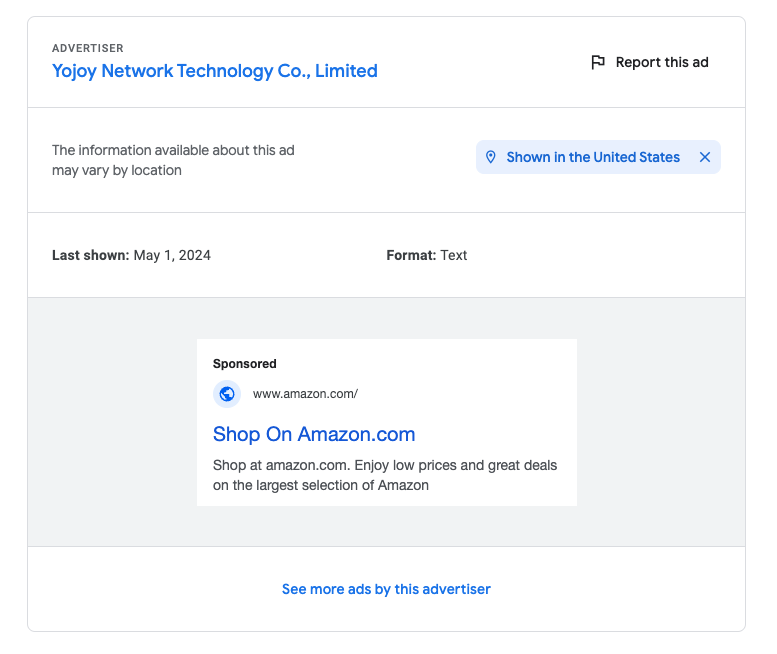
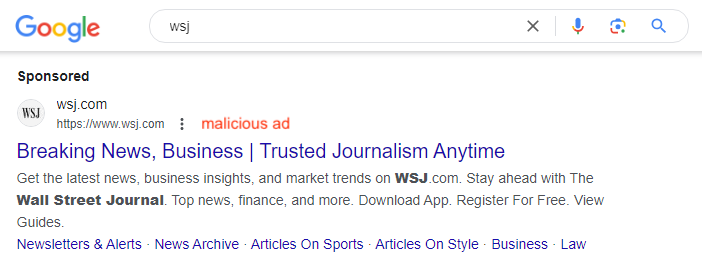
In our example, the scammers failed to use the correct CNN or Amazon icons, but in other cases (like another recent discovery by Jerome Segura), scammers have even used the correct icon.
The systems of the people that click one of these links are likely to assessed on what the most profitable follow-up is (using a method called fingerprinting). For systems running Windows, we found visitors are redirected to tech support scam websites such as this one.
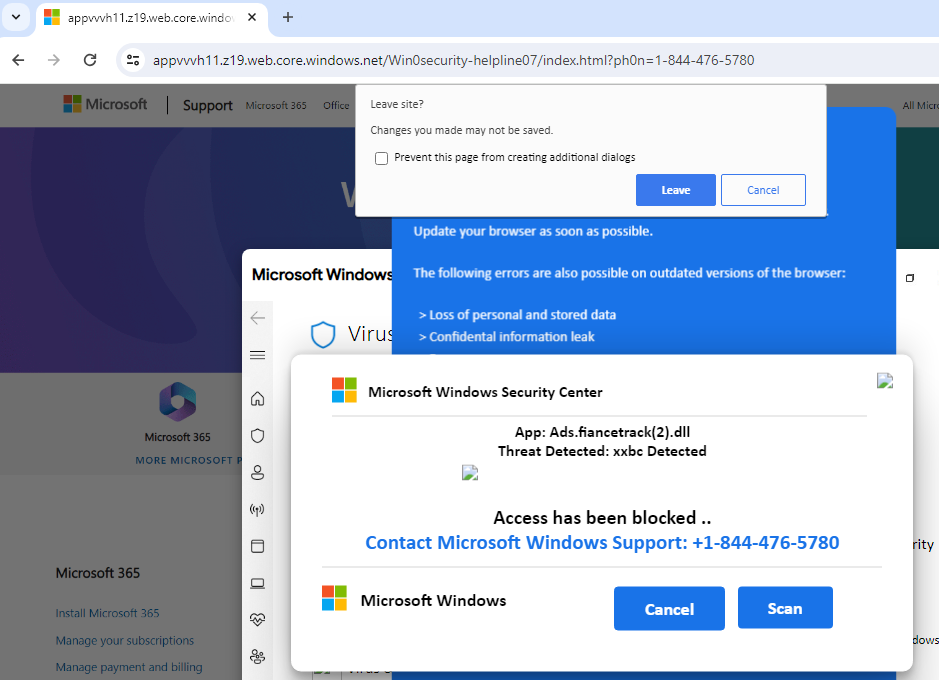
Tech Support Scam site telling the visitor to call 1-844-476-5780
You undoubtedly know the type. Endless pop-ups, soundbites, and prompts telling the visitor that they should urgently call the displayed number to free their system of alleged malware.
These tech support scammers will impersonate legitimate software companies (i.e. Microsoft) and charge their victims hundreds or even thousands of dollars for completely bogus malware removal.
Getting help if you have been scammed
Getting scammed is one of the worst feelings to experience. In many ways, you may feel like you have been violated and angry to have let your guard down. Perhaps you are even shocked and scared, and don’t really know what to do now. The following tips will hopefully provide you with some guidance.
If you’ve already let the scammers in
- Revoke any remote access the scammer has (if you are unsure, restart your computer). That should cut the remote session and kick them out of your computer.
- Scan your computer for malware. The miscreants may have installed password stealers or other Trojans to capture your keystrokes. Use a program such as Malwarebytes to quickly identify and remove threats.
- Change all your passwords. (Windows password, email, banking, etc.)
If you’ve already paid
- Contact your financial institution/credit card company to reverse the charges and keep an eye out for future unwanted charges.
- If you gave them personal information such as date of birth, Social Security Number, full address, name, and maiden name, you may want to look at some form of identity theft protection.
Reporting the scam
File a report
- In the US: File a complaint (FTC)
- In Canada: Contact law enforcement
- In the UK: Report fraud | Report a cold call
- In Australia: Report a scam
Shut down their remote software account
- Write down the TeamViewer ID (9-digit code) and send it to TeamViewer’s support. They can later use the information you provide to block people/companies.
- LogMeIn: Report abuse
Spread the word
You can raise awareness by letting your friends, family, and other acquaintances know what happened to you. Although sharing your experience of falling victim to these scams may be embarrassing, educating other people will help someone caught in a similar situation and deter further scam attempts.
We don’t just report on threats—we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your, and your family’s, personal information by using identity protection.











