Despite the occasional arrests and FTC fines for tech support scammers (TSS) and their henchmen, there are still plenty of cybercriminals active in this field. Scams range from unsolicited calls offering help with your “infected” computer to fully-fledged websites where you can purchase heavily over-priced versions of legitimate security software.
According to the FBI’s IC3 Report, in 2022 Tech and Customer Support fraudsters made 32,538 victims with total reported damages amassing $806,551,993 in the US alone.
Most people associate tech support scams with technicians sitting in a crowded and buzzing boiler room somewhere offshore, and they are not wrong. The scams primarily emanate from call centers in South Asia, mainly India. In response, the Department of Justice (DOJ) and the FBI are collaborating with law enforcement in India to combat cyber-enabled financial crimes and transnational call center fraud.
At the same time, the legal case against tech support scams originating in the US has proven to be difficult over the past few years, and prosecution has been limited. Courts are not tech-savvy enough to understand the latest scam tactics, making it very easy for scammers to get away with certain technical intricacies.
Malwarebytes researchers have been actively engaged in the fight against tech support scammers overseas but also in the US. With a commitment to helping protect consumers from all dangerous cyber threats, they are working hand in hand with the Federal Trade Commission to help provide technical evidence in support of shutting tech support scammers down while simultaneously educating Internet users on how to protect against the latest TSS tactics.
How to deal with tech support scams
As a security provider with a good reputation, we do get a lot of impersonators, like in the example below.
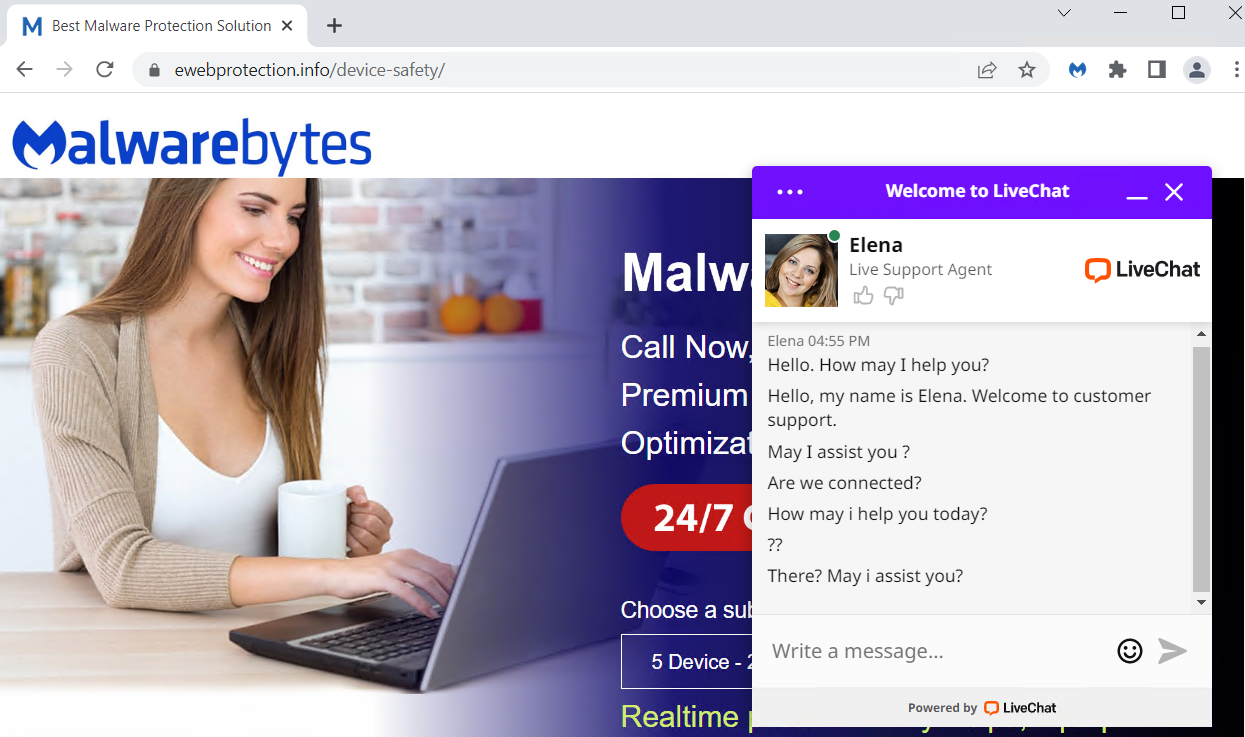
- The company gives you any name at all other than Malwarebytes. Malwarebytes does not outsource support. We have our own Support team. There are no third parties “authorized” to provide support. Nobody is “licensed” to use our name, logo, or any other intellectual property.
- The company can’t or won’t take your credit card the first time you ask. Reputable organizations don’t do this. Period. Malwarebytes has a credit card processor that takes payments for all transactions. Credit card processors do things like vet clients for risk, fraud, and abuse. So any company having trouble doing business with one, probably fits into one of those three categories. Credit cards also have reasonably robust consumer fraud protection, so if you’re being steered away from using one, that is also a red flag that the company is about to do something they probably shouldn’t.
- The company makes outbound support calls. Malwarebytes does not do this. Tech support companies that make outbound unsolicited calls tend to do so because they bought your personal information from a data broker who classified you as a vulnerable target. How would they know you have a problem with your computer? How would they even know you own a computer? Generally speaking, if someone calls you out of the blue claiming your computer has a problem, hang up.
There are some other methods that tech support scammers use to get access to your system. Here are a few of the basics to get you up to speed:
- Beware the lock up. If your browser or mobile device “locks up”, meaning you’re no longer able to navigate away from a virus warning, you’re likely part of a tech support scam. If something claims to show the files and folders from inside of your browser, this is another signal that you’re on a fake page. Close the browser if possible, or restart your device if this doesn’t work.
- Screenlocker issues. These are typically fake Windows Blue Screen of Death error pages, except they come with the tech support scammer’s phone number included. You may need one of our removal self-help guides to resolve this.
- Beware of someone wanting to connect to your computer remotely. One of the tech support scammer’s biggest weapons is their ability to connect remotely to their victims. If they do this, they essentially have total access to all of your files and folders.
Unfortunately for some people these warnings may have come too late. So what should you do if you have fallen victim to a tech support scam? Here are a few pointers:
- Did you already pay? Contact your credit card company or bank and let them know what’s happened. You may also need to file a complaint with the FTC, or contact your local law enforcement agency depending on your region.
- If you shared your password with a scammer, change it on every account that uses this password. Consider using a password manager and enable 2FA for important accounts.
- Scan your system. If scammers have had access to your system, they may have planted a backdoor so they can revisit whenever they feel like it. Malwarebytes can remove backdoors and other software left behind by scammers.
- Keep an eye out for unexpected payments. Be on the lookout for suspicious charges/payments on your credit cards and bank account(s) so you can revert and stop them.
- Be wary of suspicious emails. You have been marked as a target. By falling for one scam, scammers my try other methods to defraud you.
For a very detailed breakdown of tech support scams, how they operate, and more suggestions to keep yourself safe from harm, please check out our dedicated tech support scams page.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.











