We have recently written about malvertising campaigns that leverage Google paid advertisements to try and trick people into downloading malware instead of the software they were looking for. This malware then stole login credentials from the affected system.
Now, our researchers found that the malvertising campaigns via Google Ads are not just about software downloads and scams. They also include a much more direct way to get at your login credentials by phishing for users of popular password managers such as 1Password.
Below is a screenshot of what we found:
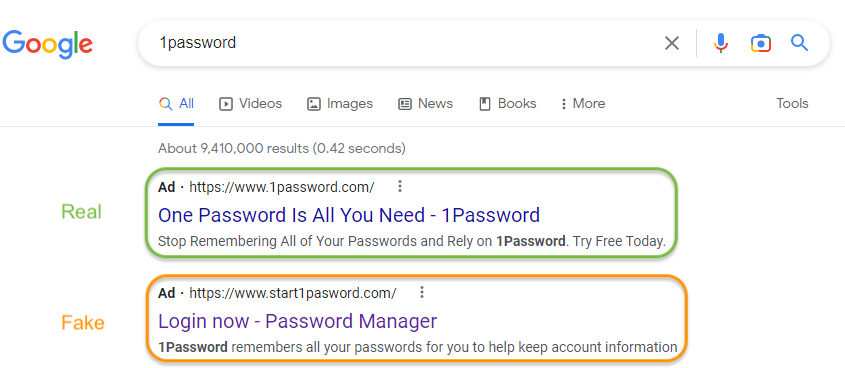
Searching for “1password” we noticed two different sponsored advertisements as the top results. The first one leads to the legitimate domain 1password[.]com, but the second one points to start1password[.]com. Both claim to be for 1Password and both are https sites. Which makes it very hard for someone who is unfamiliar with the brand to determine which one to follow.
The following order in the search results is based on a metric called “Ad Rank.”
Google says (emphasis by me):
“Ad Rank is a value that’s used to determine where ads are shown on a page relative to other ads, and whether your ads will show at all. Your Ad Rank is recalculated each time your ad is eligible to appear. It competes in an auction, which could result in it changing each time depending on your competition, the context of the person’s search, and your ad quality at that moment.”
Just to point out that going for the top result is not always a sure fire way to get to the right one.
Next phase
So where does the fake URL take us? To a very convincing phishing site. We have posted a comparison between the two login forms below.
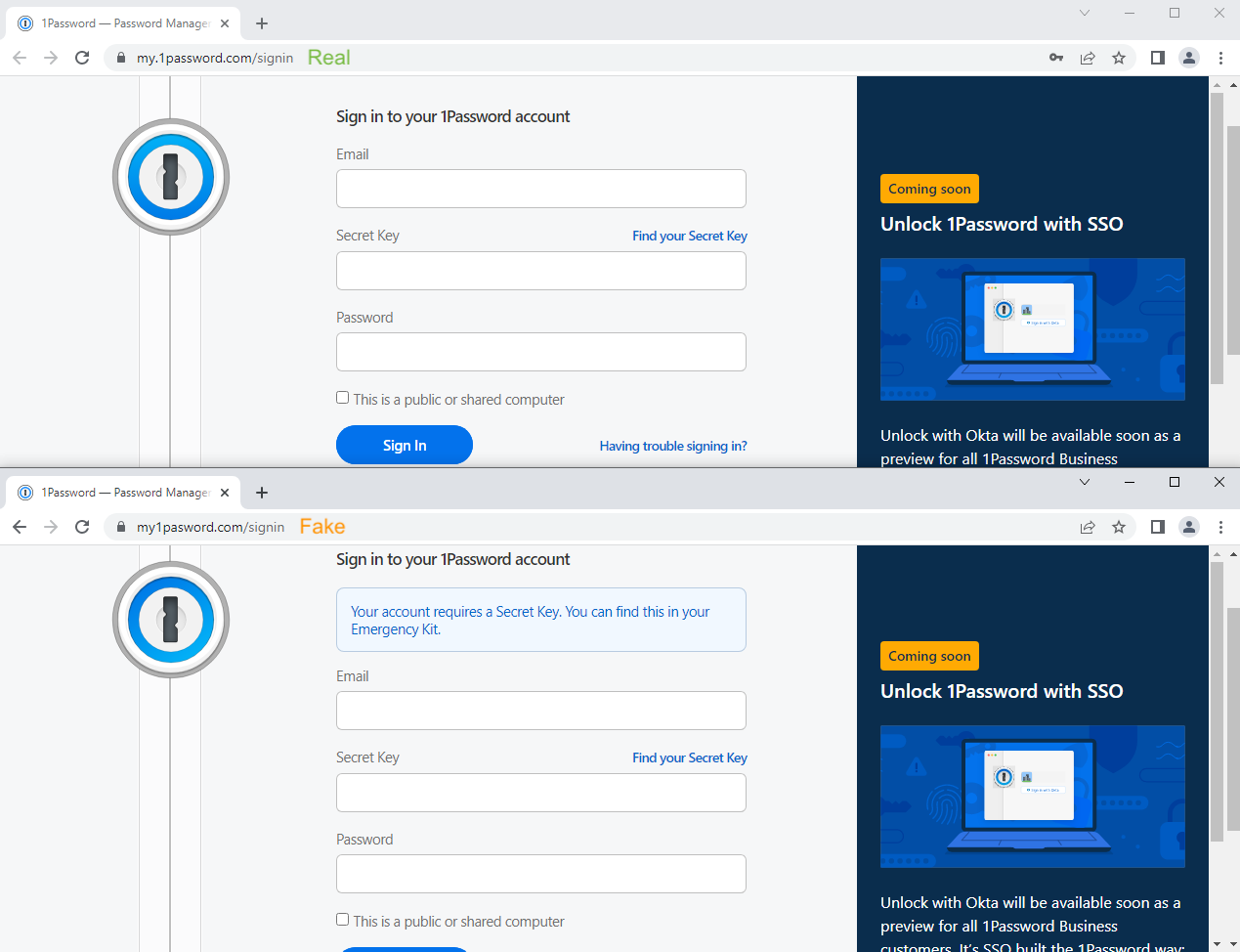
The differences are so subtle, most people will fall for it. The only real difference is that following the legitimate link will keep you in the same domain because it goes to my.1password[.]com and the phishing link will take you to my1password[.]com, where the missing dot is the only real difference in the URLs.
Secret key
The real difference is that phishing site will always have to ask for your secret key, because, well that’s what they are after. The legitimate 1Password will be able to retrieve it from your browser’s database and only ask for it if it has been deleted or if you are using 1Password on a new device or in a new browser. Deletion of the secret key can happen if you haven’t used the password manager for an extended period or if you have cleaned your browser’s cache. In which case you will have to retrieve it.
So, any attacker will not be satisfied with just your email address and password. They will need the secret key as well. But with that they would have access to all the login credentials in your vault.
While the sites used in this particular example have been taken offline, there is always the danger of new attempts, so be careful out there. Don’t give away the secret key to your password manager to any phishers.
Real URLs:
https://my[.]1password.com/signin
https://www[.]1password.com
Phishing URLs:
https://my1pasword[.]com/signin
https://www[.]start1password.com
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.











